Introduction to Linux Command Line
The significance of the command line interface in computing, understand why it is preferred for efficient file management, and discover Linux as an alternative operating system widely utilized on servers and supercomputers. Learn how to access a Linux server via SSH for practical application.
1 views • 14 slides
Stack Based Attacks in Linux (an intro)
Explore the world of stack-based attacks in Linux through an introductory session presented by Bryce L. Meyer at the Saint Louis Linux Users Group. Covering topics from weaknesses to exploits, shellcode, and mitigations like stack canaries and address space randomization, this overview delves into c
7 views • 60 slides
Understanding TCP/IP Networking Tools in Linux Administration
The iproute2 software suite in Linux provides utilities for network control and monitoring, replacing legacy tools like ifconfig, netstat, route, and arp. This lesson delves into displaying information about network interfaces, network addresses (IP addresses), routing tables, assigned DNS servers,
2 views • 22 slides
Introduction to Linux Shell for CSE 374 Course
Explore the Linux shell basics in CSE 374 course, covering topics like using Bash shell, executing commands, connecting to remote Linux servers, and interaction basics such as navigating command history. Get ready to dive into text-based interfaces and command-line operations in a Unix environment.
0 views • 14 slides
Linux Training Course in Noida
At APTRON Solutions, we prioritize practical learning with real-world scenarios, ensuring you develop the confidence to tackle complex challenges in Linux Training Course in Noida environments. Whether you're aiming to become a Linux administrator or
2 views • 9 slides
Linux Course Overview and Content for Digital Library Training
Explore the world of Linux operating systems in the context of digital library training, covering topics such as Linux distributions, system administration, text manipulation, file systems, and network configuration. The course provides a comprehensive overview and detailed content modules to develo
1 views • 11 slides
Understanding CP and MV Commands in Unix/Linux
CP and MV commands in Unix/Linux are essential for copying and moving files or directories. CP is used to copy files with various options for different scenarios, while MV is used to move or rename files. Learn examples and practical usage of these commands to efficiently manage your files on the te
0 views • 5 slides
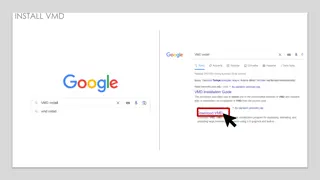
Step-by-Step Guide to Installing VMD Software and Using Linux Commands
Explore the comprehensive guide on installing Virtual Molecular Dynamics (VMD) software, along with insights into using Linux commands for data manipulation in Tk console. The tutorial covers registering, saving to desktop, and navigating through folders, concluding with loading data into VMD for vi
1 views • 9 slides
Understanding Linux Services and Internals
Explore the components of a Linux system, including hardware controllers, the Linux kernel, operating system services, user applications, directory structure, shells, and essential Linux services. Learn how to list services in Linux by connecting via SSH and accessing them as a root user to manage c
1 views • 14 slides
Introduction to Linux Shell Scripting
Dive into the world of Linux shell scripting with a focus on the bash shell. Explore the basics of programming versus scripting, different shells available in Linux, common scripting errors, and the essential elements of writing shell scripts in Linux.
0 views • 26 slides
Introduction to Linux System Administration
Explore the essentials of Linux system administration in this course material. Learn how to access Linux servers and virtual machines, utilize SSH for secure connections, and configure Kali Linux VM settings for efficient usage. Gain hands-on experience with graphical and command-line interfaces to
0 views • 45 slides
On the Shoulders of Giants: Harnessing Powerful Commands in Stata for Efficient Coding
Stata users can enhance their coding efficiency by utilizing powerful commands that are often overlooked. This presentation showcases examples of commands that can streamline coding work, ranging from interactive use to supporting long programs. By leveraging these commands, users can avoid reinvent
0 views • 51 slides
Linux Administration Essentials: A Comprehensive Training Program
Join the Cooper Union Retraining Program at CAMBA for an intensive course on Linux (Unix) Administration instructed by Dr. Tavaris J. Thomas. Learn core objectives spanning from file system management to network configuration without diving into hacking or programming. Explore the history of Linux,
0 views • 35 slides
Understanding Linux Processes and Controlling Them
This content provides insights into Linux processes, including parent-child relationships, process management commands like ps and top, background jobs, bringing processes to the foreground, and terminating processes. It also covers killing processes using kill and killall commands.
0 views • 7 slides
Basic Linux Commands Overview for Embedded Programming and Robotics
Embedded Programming and Robotics Lesson 13 provides an introduction to basic Linux commands such as man, ls, cd, cp, and more. Understanding these commands is essential for interacting with the operating system on devices like Raspberry Pi. The lesson also covers important concepts like superuser p
0 views • 17 slides
Understanding Sudo and User Privileges Management in Linux
Enhance your knowledge on controlling access to sudo in Linux, allowing users to execute commands with root privileges securely. Explore the significance of logging sudo commands, managing sudo access through sudoers file, and utilizing the Wheel group for root access control.
0 views • 8 slides
Overview of the Linux Boot Process
Exploring the six stages of the Linux boot process, starting from the BIOS and Master Boot Record (MBR) to the Grand Unified Bootloader (GRUB) and kernel initialization. Understand the essential components involved in booting up a Linux system, from system integrity checks to mounting the root file
0 views • 18 slides
Introduction to Linux System Administration
Explore the fundamentals of Linux system administration, including accessing Linux systems, using SSH for secure connections, setting up virtual machines, understanding the Unix system kernel and shell, and grasping the multi-user and multi-process aspects of Unix. Enhance your skills in managing Li
0 views • 42 slides
Introduction to Linux and Commands - Overview and Benefits
Linux is a powerful operating system with roots in UNIX, offering a wide array of functionalities for users. The program goals include presenting the Linux OS basics, introducing fundamental command-line operations, and showcasing the utilization of bioinformatics software. The content explores the
0 views • 79 slides
Introduction to the Command Line: Basic Commands and Unix Systems
This material provides an overview of fundamental commands in Unix systems, applicable to both Unix and Linux operating systems. It covers topics like directory structure, text file manipulation, file permissions, redirections, pipes, wildcards, and more. Learn about the nature of Unix systems, how
0 views • 43 slides
Guide to Giving Negative Commands in Spanish
Learn how to effectively communicate what not to do in Spanish with negative commands. Understand the different forms of negative commands for -AR, -ER/-IR verbs, irregular verbs, direct object pronouns, stem-changing verbs, and verb forms ending in -CAR, -GAR, -ZAR. Master the rules and exceptions
0 views • 12 slides
Understanding the Imperative Mood in Language
The imperative mood focuses on giving commands without reference to different time frames. It entails direct statements with the understood recipient mainly being 'you.' Commands in the singular, informal form involve dropping the 's' from the second person singular verb, both in affirmative and neg
0 views • 19 slides
Understanding Negative -T Commands in Spanish
Negative -T commands in Spanish are used to tell someone what not to do. These commands are often directed at friends or familiar individuals. Forming negative -T commands involves starting with the YO form in the present tense, dropping the O for -ER/-IR verbs, adding -ES for -AR verbs, and includi
0 views • 50 slides
Introduction to Linux: Course Overview and Objectives
This introduction to Linux course provides a comprehensive overview of operating systems, including the history, variations, user interface, and essential commands. The course is designed with lectures, labs, and exercises to help participants gain a better understanding of Linux and its practical a
0 views • 77 slides
Linux Printing Technologies Overview
Delve into the world of Linux printing with insights on open printing plenary sessions, Linux distribution market shares, driverless printing support, CUPS filters development, and future trends. Explore the growing popularity of Linux in various sectors and witness the advancements in driverless pr
0 views • 13 slides
Introduction to Shell Programming in Linux/Unix with Vim and Control Flow Commands
Explore the basics of shell programming in Linux/Unix, including Vim commands for editing files, control flow commands like if-then statements, and examples of executing commands with built-in utilities. Learn how to handle arguments, read input, and implement conditional logic in scripts.
0 views • 47 slides
In-Vehicle Infotainment System Evolution at DENSO: A Linux Experience
Explore Kazuo Tsubouchi's journey at DENSO, from software engineer to General Manager of ICT Division, focusing on Linux-based IVI systems. Witness DENSO's transition to Linux in car navigation, joining Linux Foundation and GENIVI, contributing to AGL, and shaping the future of in-vehicle technology
0 views • 20 slides
Introduction to MATLAB Commands for Data Analysis in Geophysics
Learn how UNIX commands work in MATLAB, differentiate between MATLAB and UNIX commands, utilize MATLAB's help function, explore topics available for help, access help on individual commands, and create constant matrices in MATLAB for data analysis in geophysics.
0 views • 28 slides
Intermediate Linux Workshop Overview
This intermediate Linux workshop covers various topics including input, output, pipes, processes, compiling Unix software packages, symbolic and hard links, environment variables, security, and ECC policies. It also explains CougarNet authentication for accessing engineering Linux systems, setting u
0 views • 34 slides
CS288 Intensive Programming in Linux - Course Updates and Homework Review
In CS288 Intensive Programming in Linux, Professor C.F. Yurkoski shared announcements regarding TA contact info, a sneak peek at upcoming quizzes, and file editing tips. The course also covered evaluation quiz results and practical exercises using tools like vi and tr. Homework assignments focused o
0 views • 35 slides
Introduction to Linux Workshop and History: A Brief Overview
Delve into the world of Linux with an introduction to its basics, operating system functionalities, and a quick history lesson from the Unix roots to the release of Linux. Explore the significance of Linux as an operating system and the evolution of computing. Get insights into key milestones like U
0 views • 98 slides
Overview of Windows Subsystem for Linux 2 (WSL2)
Windows Subsystem for Linux 2 (WSL2) is a new feature in Windows 10 that enables users, especially developers, to run native Linux command-line tools directly on Windows alongside traditional desktop applications. WSL provides a way to use Bash, common Linux tools, and Linux-first tools on Windows,
0 views • 11 slides
Introduction to Linux: Key Aspects and Application in Robotics
Discover the significance of Linux in the world of robotics and beyond. Learn about its widespread usage, versatility under the GNU GPL license, robust security features, and practical application through executing bash scripts on a Linux system. Dive into the fundamentals of Linux Shell interaction
0 views • 21 slides
Exploring Linux System and Bash Shell Functionality at Cornell CS4414
During the lecture, Professor Ken Birman discussed the inner workings of the Linux system and the Bash shell, focusing on processes, daemons, useful commands, and features. The session covered parallelism benefits, background processes, and the concept of daemon programs. Attendees were also shown h
0 views • 66 slides
Introduction to Linux at the Command Line with Don Johnson
Dive into the world of Linux with Don Johnson from BU IS&T. Learn about Linux's origins, common OS used by researchers, GNU utilities, essential commands, file systems, network tools, and more. Discover the importance of xterm emulation software and Mac OS X Terminal in this comprehensive guide to m
0 views • 30 slides
Comprehensive Guide on Linux Intermediate Text and File Processing
Explore a detailed course on Linux intermediate text and file processing, covering essential commands, tools, topics, and logistics for post-processing data files. Delve into topics like stdout, stdin, stderr, piping, and redirection. Enhance your skills with practical lab exercises and advance your
0 views • 67 slides
Overview of Windows Subsystem for Linux 2 (WSL)
Windows Subsystem for Linux 2 (WSL) is a new feature in Windows 10 that allows users to run native Linux command-line tools directly on Windows alongside traditional desktop and store apps. It is primarily geared towards developers, especially web developers and those working with open-source projec
0 views • 14 slides
Understanding Linux and Its Importance in Computing
Linux, a Unix clone developed by Linus Torvalds in 1991, is a widely used operating system powering servers, mobile phones, and other devices. It emphasizes the collaborative nature of software development and the synergies between different programs. This overview delves into key aspects of Linux,
0 views • 49 slides
Enhancing Cybersecurity in Modern Linux Systems
Explore the evolving landscape of cybersecurity in Linux systems as discussed in Professor Ken Birman's CS4414 lecture series at Cornell University. The focus is on protection features, defense strategies, code reviews, and continuous efforts to secure Linux platforms against exploits and vulnerabil
0 views • 55 slides
Understanding Authentication in Networking Environments
Authentication is a crucial process in computer networks where clients prove their identity to servers. This article covers the concept of authentication, its importance, and specific guidance on network authentication, particularly focusing on Windows and Linux VMs. Key topics include the use of pa
0 views • 30 slides