Introduction to Linux Command Line
The significance of the command line interface in computing, understand why it is preferred for efficient file management, and discover Linux as an alternative operating system widely utilized on servers and supercomputers. Learn how to access a Linux server via SSH for practical application.
1 views • 14 slides
UCC Research Support and Strategies Overview
UCC's Research Support, Policy & Strategy function, led by David O'Connell, PhD, provides comprehensive support for research activities at the university. The office manages research funding, monitors performance, and facilitates engagement with external stakeholders. UCC's involvement in Horizon Eu
3 views • 17 slides
Caterpillar Cat D7E TRACK-TYPE TRACTOR (Prefix SSH) Service Repair Manual Instant Download
Please open the website below to get the complete manual\n\n\/\/
0 views • 30 slides
Guide to MySQL Operations on Turing Server
This guide provides step-by-step instructions on working with MySQL on Turing server at turing.csce.uark.edu. It includes logging in via SSH, connecting to the server, changing MySQL passwords, and performing operations on tables. Learn how to create tables, change passwords, and more with detailed
2 views • 21 slides
Introduction to Unix-like Systems and Shell Interaction
Unix-like systems, such as Linux, Android, iOS, and macOS, are prevalent in various devices. The Unix shell acts as an intermediary between users and the operating system, allowing for program execution and process management. Secure Shell (SSH) and X Window System enable remote machine connections
4 views • 19 slides
Effective Proposal Writing for Health Research
Learn about the fundamentals of research proposals for health-related studies, including defining research, understanding the purposes of health research, and exploring motivation for undertaking research. Discover the difference between basic and applied research, examine types of research, and del
1 views • 70 slides
Tutorial: Installing Hadoop 3.3 on Windows 10 and Setting Up Linux Subsystem
Learn how to install Hadoop 3.3 on Windows 10 by enabling Windows Subsystem for Linux, downloading and configuring Java 8, downloading Hadoop, unzipping Hadoop binary, configuring SSH, and setting up Hadoop on your system.
1 views • 17 slides
Overview of Research Problem Identification and Formulation
Understanding the importance of defining a research problem, this content delves into the selection and formulation of research problems, the definition of a research problem, reasons for defining it, methods for identifying research problems, sources of research problems, and considerations in sele
1 views • 11 slides
Understanding Linux Services and Internals
Explore the components of a Linux system, including hardware controllers, the Linux kernel, operating system services, user applications, directory structure, shells, and essential Linux services. Learn how to list services in Linux by connecting via SSH and accessing them as a root user to manage c
1 views • 14 slides
Understanding the Essence of Research: A Comprehensive Overview
Research is a systematic pursuit of new knowledge, aiming to unveil hidden truths through data collection and analysis. This course outline delves into the fundamentals of research, covering topics such as types of research studies, importance of research, and distinctions between pure and applied r
3 views • 32 slides
Evolution of Cryptography: From Ancient Techniques to Modern Security Mechanisms
Explore the evolution of cryptography from ancient techniques like the Caesar Cipher to modern security mechanisms like SSL, SSH, and IPSec. Learn how cryptography plays a crucial role in ensuring confidentiality, integrity, authentication, non-repudiation, and availability in network security. Disc
1 views • 62 slides
Epic Tools for Clinical Research by Shara Power, RN, BSN, OCN
Explore Epic tools for clinical research developed by Shara Power, a skilled application developer specializing in EPIC Beacon Oncology at UIHC Healthcare Information Systems. Learn about managing research study records, investigational study medication orders, and the process for creating and using
0 views • 26 slides
Understanding Research Paradigms in Qualitative Medical Research
Delve into the world of research paradigms in qualitative medical research with a focus on the key differences between objective and subjective research, the meaning of research paradigms, components of research paradigms, types of research paradigms, and how paradigms guide the selection of researc
0 views • 42 slides
Guidelines for Selecting Research Project Topics in Environmental Health
Research is crucial for addressing environmental health issues. Choosing a good research topic is the first step towards effective research. This paper discusses the meaning, characteristics, types of research, and the research process to help in selecting appropriate research topics. Understanding
0 views • 15 slides
Comprehensive Research Training Programme in Social Sciences
Delve into the Research Training Programme offered by the Graduate School of Social Sciences, led by Professor Mark Tranmer. Explore the importance of research methods training, course offerings under the Research Training Programme (RTP), the Certificate in Social Science Research Methods (CSSRM),
6 views • 11 slides
Introduction to Linux System Administration
Explore the essentials of Linux system administration in this course material. Learn how to access Linux servers and virtual machines, utilize SSH for secure connections, and configure Kali Linux VM settings for efficient usage. Gain hands-on experience with graphical and command-line interfaces to
0 views • 45 slides
Understanding SFTP Server Functionality with ACS 5.x by Mohammad Azharuddin AAA Team
SFTP (SSH File Transfer Protocol) is a secure network protocol for file access, transfer, and management over reliable data streams. It enhances security by extending the SSH protocol and can be implemented using a reliable 8-bit byte stream protocol. SFTP commands are sent as 4 ASCII letters follow
4 views • 23 slides
Comprehensive Remote Access Guide for Secure Resource Access Portal
This detailed guide provides step-by-step instructions for setting up remote access to SSH, RDP, web applications, and databases via secure authentication processes. It covers prerequisites, initial login setup with 2FA, and connecting to various resources securely. Follow the guide to ensure a smoo
0 views • 12 slides
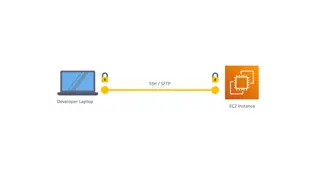
Development Process Using SSH, SFTP, EC2 Instances, and Autoscaling Groups
Exploring the development workflow involving SSH, SFTP, EC2 instances, and Autoscaling Groups for code merging, building, and releasing applications in the cloud environment using technologies like Amazon Elastic Container Service (ECS). The images provide insights into setting up developer laptops,
0 views • 5 slides
Comprehensive Overview of Git and GitHub for CS 4411 Spring 2020
This detailed content provides an in-depth exploration of Git and GitHub for the CS 4411 Spring 2020 semester. It covers Git basics, commands, dealing with conflicts and merges, understanding branches, recovering from errors, making commits, utilizing remote repositories, and collaborating via GitHu
0 views • 40 slides
Icelandic Research Fund 2015: Enhancing Scientific Research and Education
The Icelandic Research Fund (IRF) aims to enhance scientific research and education in Iceland by awarding funding to research projects led by individuals, teams, universities, research institutes, and companies. Principal investigators must have completed graduate studies and experience in running
0 views • 22 slides
Challenges in Self-Help Research in Germany
Exploring the landscape of self-help research in Germany reveals various challenges and obstacles faced by researchers in studying self-help initiatives. The research delves into different aspects such as research scope, involvement of various groups, and the entities conducting research in this dom
0 views • 14 slides
Memorial University Research Strategies Overview
Memorial University's research strategies focus on attracting, retaining, and supporting researchers, fostering an environment of research excellence, engaging with community partners, and supporting fundamental and applied research. The university's strategic priorities include synergy in applicati
0 views • 11 slides
Best Practices for Securing Linux Systems
This resource covers essential security practices for Linux systems, including the CIA Triad (Confidentiality, Integrity, Availability), recommended partitions, encryption at rest and in transit, SSH and user login configurations, and password best practices. Learn about securing user directories, p
0 views • 27 slides
Introduction to Linux System Administration
Explore the fundamentals of Linux system administration, including accessing Linux systems, using SSH for secure connections, setting up virtual machines, understanding the Unix system kernel and shell, and grasping the multi-user and multi-process aspects of Unix. Enhance your skills in managing Li
0 views • 42 slides
Understanding Unix: Fundamentals and Connections
Explore the basics of Unix operating systems, terminology, types of Linux installations, and connecting to remote Linux machines. Learn about key concepts such as local vs. remote connections, SSH connections using passwords and keys, and tools like PuTTY for remote access.
0 views • 78 slides
Understanding File Transfer Protocols: FTP, SSH, SFTP, and Email Systems
This content delves into the intricacies of file transfer protocols such as FTP, SSH, and SFTP, along with components of email systems. It explains how FTP works, its security implications, and the evolution towards more secure protocols like SFTP. Additionally, it provides insights into FTP impleme
0 views • 40 slides
Secure Out-of-Band Remote Management Using Encrypted Virtual Serial Consoles in IaaS Clouds
IaaS clouds provide virtual machines for users to manage through SSH. In scenarios where in-band remote management is not feasible, out-of-band remote management using Virtual Serial Consoles (VSC) offers a secure solution. However, challenges such as untrusted admins and potential attacks exist, wh
0 views • 22 slides
MATLAB Remote Access Instructions for Off-Campus and BU Network Users
Access MATLAB remotely using VPN for off-campus and BU network users. Establish a VPN connection, control it via tray icon, and set up X-Win32 for SSH access. Download and install necessary software following step-by-step instructions provided. By following these steps, users can easily access MATLA
0 views • 11 slides
Enhancing Interactive Job Efficiency in DLWorkspace Cloud Computing
Explore how to optimize interactive job experiences for researchers in DLWorkspace by bridging the gap between cloud and local environments, offering pre-defined job templates, and implementing efficient networking solutions such as Flannel and Kubernetes. This includes facilitating interactive job
0 views • 15 slides
Understanding the Key Dimensions of SSH Research Societal Impact
Exploring pathways to societal impact through SSH research, this presentation delves into the mechanisms and processes that lead to impactful interactions with society. It challenges the focus on physical outputs and emphasizes the importance of studying the ways in which SSH researchers engage with
0 views • 20 slides
Research Assessment Trends in RSA and Lesotho: Issues, Challenges, and Forward Strategies
Research assessment in RSA and Lesotho involves evaluating research quality, measuring inputs, outputs, and impacts using both qualitative and quantitative methodologies. The prevailing practices include assessing research productivity for progression and utilizing various assessment mechanisms to e
0 views • 7 slides
Troubleshooting WSL Issues on Inria Windows PC
WSL (Windows Subsystem for Linux) on Inria Windows PC can face issues with apt install, npm install, and Git clone due to Kaspersky Endpoint Security blocking TLS/SSL communications. A workaround involving tunneling through SSH and using proxychains4 can help resolve these problems. This guide provi
0 views • 6 slides
Networking and Distributed Computing Systems Lab Setup Guide
Set up your lab environment for networking and distributed computing systems using Unix, Bash, and Emacs. Learn to access lab machines via SSH, use PuTTY and Terminal for communication, simulate Linux environment on Windows with Cygwin, run different OS on VMware Player, download and install Linux o
0 views • 14 slides
Weak Keys Detection in Network Devices
TLS and SSH rely on RSA and DSA for security, but weaknesses in random number generation can lead to widespread weak keys among hosts on the Internet. This paper uncovers the prevalence of repeated keys and easily inferred private keys, emphasizing the importance of entropy pools in key generation.
0 views • 28 slides
Setting Up Ignite-UX Server and Client with NFSv4 and SSH Tunnel on HP-UX 11iv3
Learn how to configure an Ignite-UX server and client on HP-UX 11iv3 using NFSv4 with an SSH tunnel for a secure environment. This presentation covers the setup process, equipment requirements, and the benefits of using NFSv4 in disaster recovery scenarios.
0 views • 28 slides
Understanding Electron-Phonon Interaction and Peierls Instability in Polyacetylene using SSH Model
Explore the concepts of electron-phonon interaction, Peierls instability, and the SSH model in the context of Polyacetylene. Dive into the Born-Oppenheimer approximation, electron band properties, and density of states, unraveling the fascinating world of molecular dynamics and energy calculations.
0 views • 16 slides
Exploring Research Design and Funding Priorities in Northern Ireland
Dive into the world of research at the upcoming Application and Research Design Workshop scheduled for Friday, 28th May 2021. Discover the strategic priorities driving impactful research initiatives, learn about current research projects, funding processes, and collaborations. Explore the rich histo
0 views • 37 slides
Terrestrial File Transfer Concept: Design Goals and Protocols
This document discusses the concept of terrestrial file transfer as presented in a series of slides from an ESA event in Noordwijkerhout, The Netherlands. It covers the purpose, design goals, protocols, and transport protocols involved in exchanging files between agencies for mission design, operati
0 views • 20 slides
Introduction to UNIX System and Homework Assignment in CS 240
Learn about connecting to the CS department's UNIX system, setting up accounts, using SSH clients on Windows, Mac, and Linux, navigating the filesystem, and performing commands in the command line interface. Get started with your CS 240 assignments effectively.
0 views • 19 slides