Understanding SFTP Server Functionality with ACS 5.x by Mohammad Azharuddin AAA Team
SFTP (SSH File Transfer Protocol) is a secure network protocol for file access, transfer, and management over reliable data streams. It enhances security by extending the SSH protocol and can be implemented using a reliable 8-bit byte stream protocol. SFTP commands are sent as 4 ASCII letters followed by arguments. Responses from the server consist of a response character and an ASCII message string. SFTP provides user access control, directory operations, and file manipulation functionalities.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author. Download presentation by click this link. If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
E N D
Presentation Transcript
Working of SFTP server with ACS 5.x By Mohammad Azharuddin AAA Team
About SFTP Simple File Transfer Protocol/SSH FTP/Secure FTP In computing, the SSH File Transfer is a network protocol that provides file access, file transfer, and file management functionalities over any reliable data stream. It was designed by the Internet Engineering Task Force (IETF) as an extension of the Secure Shell protocol (SSH) version 2.0 to provide secure file transfer capability, but is also intended to be usable with other protocols. The IETF of the Internet Draft states that even though this protocol is described in the context of the SSH-2 protocol, it could be used in a number of different applications, such as secure file transfer over Transport Layer Security (TLS) and transfer of management information in VPN applications. SFTP runs over TCP port 22. It fills the need of people wanting a protocol that is more useful than TFTP but easier to implement (and less powerful) than FTP. SFTP supports user access control, file transfers, directory listing, directory changing, file renaming and deleting. SFTP can be implemented with any reliable 8-bit byte stream oriented protocol, this document describes its TCP specification. SFTP uses only one TCP connection; whereas TFTP implements a connection over UDP, and FTP uses two TCP connections (one using the TELNET protocol).
SFTP commands sent to the remote server are always 4 ASCII letters (of any case) followed by a space, the argument(s), and a <NULL>. The argument can sometimes be null in which case the command is just 4 characters followed by <NULL>. Replies from the server are always a response character followed immediately by an ASCII message string terminated by a <NULL>. A reply can also be just a response character and a <NULL>. <command> : = <cmd> [<SPACE> <args>] <NULL> <cmd> : = USER ! ACCT ! PASS ! TYPE ! LIST ! CDIR KILL ! NAME ! DONE ! RETR ! STOR <response> : = <response-code> [<message>] <NULL> <response-code> : = + | - | | ! <message> can contain <CRLF> Commands that can be sent to the server are listed below. The server replies to each command with one of the possible response codes listed under each message. Along with the response, the server should optionally return a message explaining the error in more detail. Example message texts are listed but do not have to be followed. All characters used in messages are ASCII 7-bit with the high-order bit zero, in an 8 bit field. The response codes and their meanings: + Success. - Error. An error occurred while processing your command. Number. The number-sign is followed immediately by ASCII digits representing a decimal number. ! Logged in.
Example: An example file transfer. 'S' is the sender, the user process. 'R is the reply from the remote server. Remember all server replies are terminated with <NULL>. If the reply is more than one line each line ends with a <CRLF>. R: (listening for connection) S: (opens connection to R) R: +MIT-XX SFTP Service S: USER MKL R: +MKL ok, send password S: PASS foo R: ! MKL logged in S: LIST F PS: <MKL> R: +PS: <MKL> Small.File Large.File S: LIST V R: +PS: <MKL> Small.File 1 69(7) P775240 2-Aug-84 20:08 MKL Large.File 100 255999(8) P770000 9-Dec-84 06:04 MKL S: RETR SMALL.FILE R: 69 S: SEND R: This is a small file, the file is sent without a terminating null. S: DONE R: +MIT-XX closing connection
Comparison With SCP & FTP SCP Compared to the earlier SCP protocol, which allows only file transfers, the SFTP protocol allows for a range of operations on remote files it is more like a remote file system protocol. An SFTP client's extra capabilities compared to an SCP client include resuming interrupted transfers, directory listings, and remote file removal. SFTP attempts to be more platform-independent than SCP; for instance, with SCP, the expansion of wildcards specified by the client is up to the server, whereas SFTP's design avoids this problem. While SCP is most frequently implemented on Unix platforms, SFTP servers are commonly available on most platforms. FTP Sftp is a secure form of the ftp command. Whenever a user opens up a regular ftp session or most other TCP/IP connections, the entire transmission made between the host and the user is sent in plain text. Anyone who has the ability to snoop on the network packets can read the data, including the password information. If an unauthorized user can login, they have the opportunity to compromise the system. When using ssh's sftp instead of the ftp, the entire login session, including transmission of password, is encrypted. It is therefore much more difficult for an outsider to observe and collect passwords from a system using ssh/sftp sessions.
SFTP Servers There are many freeware software available on internet those can be used as SFTP servers. Here are some of them: - SolarWind - Silvershield - WinSSHD - Copssh - Core FTP Mini SFTP Server
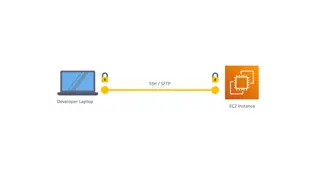
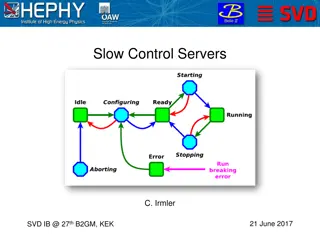
Working example of a SFTP server with ACS 5.3
Copssh (3.0.3) Installation and Configuration
Here is how we configure SFTP server on the ACS: Note: Syntax to configure the repository: acs/admin# conf t Enter configuration commands, one per line. End with CNTL/Z. acs/admin(config)# repository sftp acs/admin(config-Repository)# url sftp://<ip of the ftp server> acs51/admin(config-Repository)# user <username> password <password> plain acs51/admin(config-Repository)# host-key sync acs51/admin(config-Repository)# Exit The SFTP user should have all the permission of the repository folder. The SFTP server should be reachable from the ACS. The firewall should be disabled on the SFTP server for proper communication.
Generates RSA keys between the host and ACS machine when you configure SFTP repository. host-key sync: Debugs need to enabled on the the ACS CLI: debug transfer 7 debug copy 7 debug backup-restore all
To verify the repository created and permissions to access it, we use the following command on the ACS CLI: acs51/admin# show repository sftp Debugs: acs51/admin# sh repository sftp 7 [5570]: backup-restore:history: br_cli.c[136] [admin]: _cars_show_repository INVOKED 6 [5570]: transfer: cars_xfer.c[173] [admin]: sftp dir of repository sftp reques ted 6 [5570]: transfer: cars_xfer_util.c[1604] [admin]: resolved server to 192.168.26.120 7 [5570]: transfer: cars_xfer_util.c[1625] [admin]: authenticating using password 7 [5570]: transfer: cars_xfer_util.c[1633] [admin]: initializing sftp using ssh session 7 [5570]: transfer: cars_xfer_util.c[1654] [admin]: opening / on remote server 7 [5570]: transfer: cars_xfer_util.c[1672] [admin]: received filename . 7 [5570]: transfer: cars_xfer_util.c[1672] [admin]: received filename .. 7 [5570]: transfer: cars_xfer_util.c[1672] [admin]: received filename backup1-120717- 0332.tar.gpg 7 [5570]: transfer: cars_xfer_util.c[1672] [admin]: received filename bck1-120717-0337.tar.gpg 7 [5570]: transfer: cars_xfer_util.c[1672] [admin]: received filename bck1-120717-0338.tar.gpg 7 [5570]: transfer: cars_xfer_util.c[1672] [admin]: received filename bck2-120717-0347.tar.gpg 7 [5570]: transfer: cars_xfer_util.c[1672] [admin]: received filename Bin 7 [5570]: transfer: cars_xfer_util.c[1672] [admin]: received filename doc 7 [5570]: transfer: cars_xfer_util.c[1672] [admin]: received filename etc 7 [5570]: transfer: cars_xfer_util.c[1672] [admin]: received filename fstab.txt
7 [5570]: transfer: cars_xfer_util.c[1672] [admin]: received filename home 7 [5570]: transfer: cars_xfer_util.c[1672] [admin]: received filename LICENSE.COPSSH.TXT 7 [5570]: transfer: cars_xfer_util.c[1672] [admin]: received filename LICENSE.CYGWIN.TXT 7 [5570]: transfer: cars_xfer_util.c[1672] [admin]: received filename LICENSE.OPENSSH.TXT 7 [5570]: transfer: cars_xfer_util.c[1672] [admin]: received filename myhome 7 [5570]: transfer: cars_xfer_util.c[1672] [admin]: received filename myhome.lnk 7 [5570]: transfer: cars_xfer_util.c[1672] [admin]: received filename README.TXT 7 [5570]: transfer: cars_xfer_util.c[1672] [admin]: received filename sftp 7 [5570]: transfer: cars_xfer_util.c[1672] [admin]: received filename sshd-stderr.log 7 [5570]: transfer: cars_xfer_util.c[1672] [admin]: received filename sshd-stdout.log 7 [5570]: transfer: cars_xfer_util.c[1672] [admin]: received filename tmp 7 [5570]: transfer: cars_xfer_util.c[1672] [admin]: received filename uninstall_Copssh.exe 7 [5570]: transfer: cars_xfer_util.c[1672] [admin]: received filename uninstall_ICW_Base.exe 7 [5570]: transfer: cars_xfer_util.c[1672] [admin]: received filename uninstall_ICW_OpenSSHServer.exe 7 [5570]: transfer: cars_xfer_util.c[1672] [admin]: received filename var 7 [5570]: transfer: cars_xfer_util.c[1672] [admin]: received filename proc 7 [5570]: transfer: cars_xfer_util.c[1672] [admin]: received filename cygdrive 7 [5570]: transfer: cars_xfer_util.c[1705] [admin]: shutting down sftp & ssh after successful dir xfer 7 [5570]: transfer: cars_xfer.c[209] [admin]: freed file list
We can also check the repository configured under in the running- config of the ACS CLI:
ACS configuration backup with debugs: acs51/admin# acs backup back3 repository sftp 7 [5583]: backup-restore:backup: br_backup.c[427] [admin]: initiating application component backup back3-120717-0421 to repos sftp 7 [5583]: backup-restore:backup: br_backup.c[450] [admin]: no staging url defined, using local space 7 [5583]: backup-restore:backup: br_backup.c[41] [admin]: flushing the staging area 7 [5583]: backup-restore:backup: br_backup.c[473] [admin]: creating /opt/backup/backup-back3-120717-0421-1342479066 7 [5583]: backup-restore:backup: br_backup.c[488] [admin]: creating backup subdir: /opt/backup/backup-back3-120717- 0421-1342479066/backup/appcomponent 7 [5583]: backup-restore:backup: br_backup.c[492] [admin]: Calling appComponent backup with command: /opt/CSCOacs/bin/backup.sh /opt/backup/backup-back3-120717-0421-1342479066/backup/appcomponent 6 [5583]: transfer: cars_xfer.c[120] [admin]: sftp copy out of /opt/backup/backup-back3-120717-0421-1342479066/back3- 120717-0421.tar.gpg requested 6 [5583]: transfer: cars_xfer_util.c[343] [admin]: resolved server to 192.168.26.120 7 [5583]: transfer: cars_xfer_util.c[359] [admin]: copying file to remote server: 192.168.26.120 with full path /back3- 120717-0421.tar.gpg 7 [5714]: transfer: sftp_copy.c[78] [daemon]: Executing SFTP command: /usr/bin/scp /opt/backup/backup-back3-120717- 0421-1342479066/back3-120717-0421.tar.gpg Administrator@192.168.26.120:/back3-120717-0421.tar.gpg 7 [5583]: transfer: cars_xfer_util.c[367] [admin]: sftp xfer succeeded 7 [5583]: backup-restore:backup: br_backup.c[41] [admin]: flushing the staging area 6 [5583]: backup-restore:backup: br_backup.c[537] [admin]: application component backup back3-120717-0421.tar.gpg to repository sftp: success 7 [5583]: backup-restore:history: br_history.c[252] [admin]: running date 7 [5583]: backup-restore:history: br_history.c[76] [admin]: obtained backup history lock 7 [5583]: backup-restore:history: br_history.c[160] [admin]: loaded history file /var/log/backup.log 7 [5583]: backup-restore:history: br_history.c[118] [admin]: stored backup history file 7 [5583]: backup-restore:history: br_history.c[118] [admin]: stored backup history file 7 [5583]: backup-restore:history: br_history.c[90] [admin]: released backup history lock 7 [5583]: backup-restore:history: br_history.c[310] [admin]: added record to history ACS backup file 'back3-120717-0421.tar.gpg' successfully copied to repository 'sftp'
Defects/Feature Requests With ACS 5.x CSCts42754: Feature request to show SCP instead of SFTP, as it uses SCP in the background. State: New CSCtq07534: ACS 5 does not verify the RSA key set for SFTP repositories. It automatically accepts any set of RSA keys.Such a behavior could be subject to man-in-the-middle attacks, where ACS will just send the SCP login credentials without ever verifying (or prompting the end user to verify) the RSA key set. State: Verified Status: Fixed in ACS 5.3. CSCtn78315: Backup fails using sftp if not transferred within 60 secs. State: Verified. Status: Fixed in ACS 5.3.
References Request for Comments: 913 Reference Link: http://en.wikipedia.org/wiki/SSH_File_Transfer_Protocol#References