Active Directory Self Service Password Reset Tool, cionsystems
It provides the feature of delegated web access administration, self-registration, self-service and password management. \/\/rb.gy\/1tjfv5
2 views • 2 slides
Digital Wellness and Password Security Lesson for Students
This lesson focuses on promoting digital wellness and teaching students about password security. It covers topics such as creating strong passwords, safeguarding personal information, and the importance of balancing online and offline interactions. Through activities and discussions, students learn
0 views • 13 slides
Unlocking Solutions: Addressing QuickBooks Company File Incorrect Password Issue
Unlocking Solutions: Addressing QuickBooks Company File Incorrect Password Issues\nQuickBooks, a vital tool for businesses, can encounter password-related hurdles, disrupting workflow. This guide explores causes and solutions to incorrect password issues. Forgotten passwords, user permission errors,
1 views • 5 slides
Cybersecurity Best Practices for Password Protection and Incident Response
Enhance your cybersecurity knowledge with insights on password management, cybercriminal tactics, creating strong passwords, and password complexity. Learn how to safeguard your data and prevent cyber threats by implementing strong password rules, multi-factor authentication, and incident response s
2 views • 24 slides
Device Settings and Strong Passwords for Digital Citizenship
This lesson focuses on understanding device settings and the importance of creating strong passwords for digital citizenship. It covers topics such as changing backgrounds, locking screens, creating strong passwords, common password mistakes to avoid, and tips for password safety. The lesson also in
2 views • 11 slides
Strengthen Your Digital Literacy with Strong Password Strategies
Enhance your digital literacy by learning about the importance of strong passwords, strategies for creating secure passwords, and the role of password managers. Explore various resources, videos, and tools to improve your password security and protect your online accounts effectively.
0 views • 5 slides
Promote Feature Adoption with Self-Service Password Reset Posters
Enhance feature adoption of self-service password reset among your employees with these ready-to-use posters. Simply customize and print them to encourage password security awareness in your workplace. Don't risk productivity downtime due to forgotten passwords – empower your team to reset their p
0 views • 13 slides
Evolution of Password Security in Modern Computing
Delve into the historical origins of passwords, their significance in cybersecurity, and the current methods employed to safeguard digital assets. Explore the challenges posed by fast computing systems and discover innovative solutions and tools like LastPass, Keeper, and Dashlane in the realm of pa
0 views • 15 slides
Reset Internet Banking Transaction Password Online Guide
Complete your internet banking transaction password reset online using your ATM card details and registered mobile number for OTP verification. Follow the step-by-step instructions provided with images for a successful reset process and confirmation.
0 views • 8 slides
Enhancing Security with Windows Hello for Business
Windows Hello for Business provides a more secure non-password credential for Windows 10/11 devices, implementing 2FA/MFA to combat password-related vulnerabilities. This article explores the benefits, security measures, and implementation steps of Windows Hello for Business, addressing the challeng
8 views • 24 slides
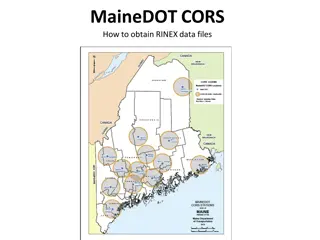
Obtaining RINEX Data Files from MaineDOT CORS
Obtain RINEX data files from MaineDOT CORS by following a few simple steps. Login and password are required, and guest login is no longer an option. The data is collected at one-second intervals and is available for Real-Time-Kinematic (RTK) users. To access the files, visit the provided link, selec
0 views • 17 slides
OAuth Service for Issuing Certificates to Science Gateways
This project aims to provide an OAuth service for issuing certificates to Science Gateways for TeraGrid users Jim Basney and Jeff Gaynor from the University of Illinois. The effort is supported by the National Science Foundation to enhance security, independent gateway access, and better resource ut
0 views • 14 slides
Recovering Console Password for Cisco ASR5000/5500 - Step-by-Step Guide
Learn how to recover the console password for Cisco ASR5000/5500 devices using a simple step-by-step process. Follow pre-requisites, problem reproduction steps, and the solution overview to regain access to your console interface.
2 views • 14 slides
Laptop Roll-Out Information and Schedule for Students at HPK
Information and guidelines for the upcoming laptop roll-out event at HPK including distributing password cards, password training, roll-out locations, times by grade, and instructions on global protection software. Students must follow the specified steps to receive their laptops successfully.
0 views • 14 slides
Step-by-Step Guide to Password Recovery and Account Activation
Detailed instructions on how to recover your password, activate your account, and securely log in for the first time following the system upgrade. Follow each step carefully to ensure a smooth transition into the upgraded system.
0 views • 9 slides
Safely Logging Password-Derived Measurements for Web Login Systems
Design a secure measurement framework called Gossamer to assess risks associated with password-based measurements for web login systems. Explore ways to differentiate between benign and malicious traffic, and consider adding instrumentation to enhance security. Learn how attackers exploit password-d
0 views • 12 slides
How to Login to BridgeIT & Create MAPFRE Password
Learn how to login to BridgeIT on August 6th at bridgeit.mapfre.com:4430 and create or reset your MAPFRE password. Follow the step-by-step instructions provided using your MAPFRE username. A dedicated support helpline is available for any login difficulties.
0 views • 5 slides
Guide to Logging in to SIRA UW with MAPFRE Credentials
Learn how to access SIRA UW platform using your MAPFRE credentials starting August 6th. Follow the steps for creating and resetting your password, ensuring a smooth login process. Utilize your MAPFRE username and be prepared to wait 10 minutes post password reset. Reach out to the dedicated support
0 views • 5 slides
Guide to Logging in and Setting Up Core-CT for the First Time
Accessing Core-CT for the first time involves using your State of Connecticut Employee ID and temporary password. Follow the steps to log in, set up a new password, and establish a forgotten password help feature. This guide provides clear instructions and visuals for each step.
0 views • 19 slides
Step-by-Step Guide to Creating a Wikipedia Account
Follow these detailed steps to create your own Wikipedia account easily, including selecting a language, inputting a username and password, and entering your email address. Ensure a secure and unique username and password for a successful account setup.
0 views • 13 slides
Password Cracking Techniques and Remote Desktop Access Setup
Explore various password cracking methods such as offline and online techniques using tools like Hydra, alongside setting up remote desktop access on Windows VMs to gain remote control over services. Learn about preparing Windows VMs, disabling firewalls, and enabling remote desktop assistance for e
0 views • 12 slides
Best Practices for Securing Linux Systems
This resource covers essential security practices for Linux systems, including the CIA Triad (Confidentiality, Integrity, Availability), recommended partitions, encryption at rest and in transit, SSH and user login configurations, and password best practices. Learn about securing user directories, p
0 views • 27 slides
Mastering Strong Passwords: A Practical Guide
Understanding how passwords work is crucial for online security. Passwords act like combination locks, preventing unauthorized access to your accounts. Creating a strong password involves using random words and characters, as well as combining three random words for added security. Learn how to craf
0 views • 5 slides
Accessing NC Fast Subsidized Child Care Data in Data Warehouse
Learn how to log in and access NC Fast Subsidized Child Care data through the Data Warehouse portal. Access to the data warehouse requires a login and password, which can be obtained by contacting your LME or Institution Security Officer. The metadata available includes descriptions, table names, pr
0 views • 15 slides
Interactive Password Security Activity for Children
This presentation recaps the importance of strong passwords, techniques for creating them, and the significance of two-factor authentication. The lesson notes guide discussions on creating secure passwords using the "three random words" method and avoiding personal details. The interactive game "Gue
0 views • 4 slides
Best Practices for Secure Password Storage - OWASP Foundation Guidelines
Learn about secure password storage techniques recommended by OWASP Foundation, including adding salt, slowing down hashing functions, using HMAC isolation, and imposing difficult verification processes on attackers. Remember to use proper encoding, avoid limiting password types or lengths unreasona
0 views • 10 slides
Techniques and Tools for Offline Password Cracking
Explore the world of offline password cracking techniques using tools like John the Ripper. Learn about the motivation behind cracking user account passwords, gaining root privilege, and compromising vulnerable systems to obtain password hashes for further exploitation. Enhance your understanding of
0 views • 15 slides
Fine-Grained Password Policies in Active Directory
Explore the intricacies of Fine-Grained Password Policies (FGPP) in Active Directory, covering topics such as domain account policies, policy recovery methods, interpreting pwdProperties attribute, and implementing PSOs for granular password settings. Delve into the nuances of password complexity, h
0 views • 11 slides
Best Practices for Protecting Sensitive Data
Learn about password and credit card data security, storing passwords securely, data in transit vs. data at rest, and the importance of using salts to protect password hashes from offline attacks. Discover how to securely store passwords using encryption, hashing, and more to minimize exposure of se
0 views • 30 slides
Windows Security Overview and Best Practices
Windows operating system security overview focusing on preventing unauthorized access, privilege escalation, and password vulnerabilities. Includes countermeasures such as setting proper permissions, implementing strong passwords, and detecting vulnerabilities. Covering topics like remote password g
0 views • 6 slides
Enhancing Web Security with U2F Authentication
Explore the innovative FIDO U2F technology, a robust authentication solution for the web that addresses common password vulnerabilities. Learn how U2F works, its benefits for users, service providers, and device vendors, and its user-friendly implementation across various devices. Discover why U2F o
0 views • 18 slides
Distance CME Greenville County EMS Training Programs
Distance CME offered by Greenville County EMS aims to enhance outcomes through education, training, and research. Access the training site by copying and pasting the provided link. Follow the instructions to log in using your work email and default password. Learn how to change your password, explor
0 views • 17 slides
Enhancing WiFi Security and Password Protection for IoT Devices
Explore the importance of securing WiFi networks and IoT devices to mitigate privacy and security risks. Learn about encryption, hashing, salting, and ways to strengthen passwords to prevent unauthorized access. Discover common password attack methods and how to safeguard against them.
0 views • 13 slides
Password Security: Techniques and Best Practices
Delve into the world of password security with this comprehensive guide, covering topics such as password gathering, cracking strategies, tools, types of passwords, hashes, salting, better hashes, and hash identification. Learn how to enhance security measures and protect against malicious attacks.
0 views • 20 slides
Tools and Techniques for Extracting Password Hashes and Credentials from Windows Systems
Explore various tools and scripts such as ESEDBXTRACT, GPPPFinder, and PowerShell scripts for extracting password hashes and credentials from Windows systems, including NTDS.dit and SYSTEM files, Group Policy Preferences, and more. Learn how to handle different Windows versions and access encrypted
1 views • 19 slides
Protecting Password Identifiers in IEEE 802.11-21
This submission addresses the need for safeguarding password identifiers in SAE to ensure privacy and prevent attackers from constructing personally identifiable information. The document presents two potential solutions, ultimately recommending the use of symmetric cryptography for efficient protec
0 views • 11 slides
Password Guessability Metrics in Real-World Security
Delve into the realm of password guessability metrics to enhance password security. Explore how measuring guessability aids in eliminating weak passwords, aiding users in creating stronger ones, and assessing security against various cracking algorithms. Uncover the significance of statistical and p
0 views • 27 slides
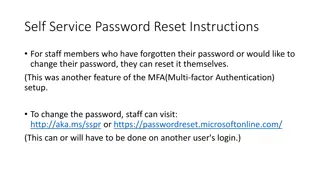
Self-Service Password Reset Instructions for Staff Members
Staff members can easily reset or change their password through self-service options using Multi-Factor Authentication. They can visit the provided links, verify their identity through email and phone number, and reset their password securely. Follow the step-by-step guide for a hassle-free password
0 views • 4 slides
Guide to Logging into Your Chromebook
This step-by-step guide provides instructions on how to log into your Chromebook using either your student ID and password or a QR code. Simply open the lid, press the power button, select "Next," and then proceed to log in with your credentials. For password login, enter your student ID and the def
0 views • 6 slides
Enhancing Wi-Fi Security with User-Friendly WPA3 Passwords
Proposal to enhance Wi-Fi security by incorporating password and password identifier hashes in the SAE commit exchange, enabling devices to hint to access points which password will be used. This approach aims to improve network efficiency and user experience while addressing privacy concerns associ
0 views • 8 slides