Visual Overview of Slide Presentations
This content showcases a series of visual slides with unique descriptions and image URLs. Each slide presents a different pattern or design, offering a diverse visual experience. Explore the array of images and descriptions in this collection.
1 views • 50 slides
Comprehensive Bug Hunting Toolkit for Cybersecurity Enthusiasts
Explore a detailed guide on bug hunting tools, techniques, and resources by expert bug hunter Orwa Atyat from Jordan. Learn valuable tips on finding high/critical bugs, conducting basic recon, subdomain enumerations, collecting URLs/endpoints, and searching for backup files. Enhance your cybersecuri
2 views • 14 slides
Step-by-Step Guide to Register and Login for WBG Edcast Grow Learn Connect Courses
Discover how to register and log in for Grow Learn Connect courses on the WBG Edcast platform. Follow detailed instructions from course access to account creation, including email verification and password setup. Access course URLs for learning in English and French. Start your learning journey toda
4 views • 7 slides
NCI Data Collections BARPA & BARRA2 Overview
NCI Data Collections BARPA & BARRA2 serve as critical enablers of big data science and analytics in Australia, offering a vast research collection of climate, weather, earth systems, environmental, satellite, and geophysics data. These collections include around 8PB of regional climate simulations a
6 views • 22 slides
Introduction to Web and HTTP Protocols in Data Communication Networks
Explore the fundamental concepts of the World Wide Web and Hypertext Transfer Protocol (HTTP) as integral parts of data communication networks. Delve into the history, structure, and key components of the web, including HTML, common tags, URLs, and HTTP. Understand how information is accessed, trans
1 views • 34 slides
Understanding Cora Analysis and Its Impact on SEO Practices
Cora analysis involves extracting information from URLs to enhance SEO visibility. By leveraging Spearman & Pearson correlation algorithms, one can identify ranking factors. This analysis compares competitor data to improve SEO strategies. Recommendations may include optimizing H1 tag usage for bett
0 views • 58 slides
Understanding Internet Tools and Terminology
The Internet is a global network of interconnected computers utilizing the TCP/IP communication method. It includes the World Wide Web, browsers for accessing content, servers for data transfer, websites with webpages displayed via web servers, URLs for addressing resources, and protocols like SMTP,
1 views • 6 slides
Efficient Malicious URL Detection with Bloom Filters
Google's Chrome team faces the challenge of detecting malicious URLs without heavy memory usage. Universal hashing and Bloom Filters are discussed as innovative solutions to address this issue efficiently and effectively, illustrating how K-independent hash functions can improve detection accuracy w
0 views • 19 slides
Understanding the Basics of the World Wide Web
The session presented by Dr. Ebenezer Ankrah provides an overview of the World Wide Web, covering topics such as web terminology, URLs, browsers, and search engines. Through this session, students will gain a fundamental understanding of web-related concepts and tools. The reading list includes reco
0 views • 36 slides
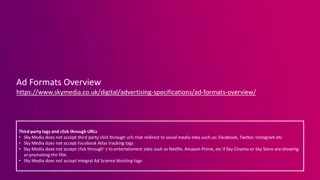
Sky Media Advertising Specifications Overview
Sky Media specifies ad formats and restrictions, including limitations on third-party tags, click-through URLs, and certain tracking tags. The overview covers website and app formats, loading requirements, file size guidelines, and creative considerations for successful advertising campaigns.
0 views • 19 slides
Creating QR Codes for Desktop Computers, Android, and iOS Devices
Learn how to create QR codes using Chrome on desktop computers as well as Android and iOS devices. Understand the importance of corrected age for premature babies and how it impacts developmental tracking. Discover tips and tricks for efficiently sharing URLs using QR codes across different platform
0 views • 26 slides
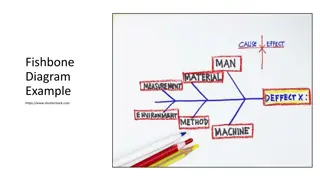
Examples of Fishbone, Mind Map, and Concept Map Diagrams
Visual examples of Fishbone Diagrams, Mind Maps, and Concept Maps are provided in the content. Each diagram is showcased with detailed descriptions and image URLs. Explore these examples to enhance your understanding of these diagram types.
0 views • 6 slides
Streamlined Process for 1098t System Access
Simplify your 1098t document management with the new streamlined process, including easy upload options, student connectivity, and document access instructions. Utilize the dedicated URLs for clients and students, facilitate bulk imports, and ensure accurate data placement with updated field definit
0 views • 10 slides
MySafety WHS Hazard and Incident Management Overview
MySafety WHS hazard and incident management system provides a comprehensive platform for Health and Safety Representatives to access, lodge, investigate, and review records related to workplace incidents. Workers, emergency services volunteers, and non-employees working for participating agencies in
1 views • 11 slides
Collection of 20 Image Objects
A collection featuring 20 ImageObjects with descriptions, each showcasing a unique image with a width of 900px. The images are part of a series identified as 1.of.20, 2.of.20, and so on up to 20.of.20, accessible via content URLs from data1.slideorbit.com.
0 views • 20 slides
Unleash Cutting-Edge Research Access at One Infinite Hub
Elevate your research endeavors with unparalleled access to a wealth of multidisciplinary content brought together conveniently in one comprehensive platform. Stay ahead in your field by leveraging the vast resources available, while seamlessly integrating custom URLs for a tailored experience. Expl
0 views • 4 slides
NSU Editorial Style Quick Tips and Guidelines
Learn valuable NSU editorial style quick tips on punctuation, capitalization, grammar, numbers, and more to enhance the clarity and professionalism of your writing. Get insights on when to use the serial/Oxford comma, em dashes, and proper capitalization rules. Understand the correct usage of facult
0 views • 7 slides
Effective Strategies for Upstream Growth Optimization
Improve your keyword match types to enhance cost-effectiveness and conversions. Target specific positions for keywords to maximize conversion rates. Utilize relevant variations of keywords for better traffic and conversions. Harness the power of converting URLs for enhanced ad group performance and
0 views • 7 slides
Understanding Reliable and Unreliable Sources for Research
Recognize reliable and unreliable sources for research. Reliable sources, such as books and peer-reviewed journals, are authored by experts in the field. Unreliable sources like Wikipedia and blogs can be altered by anyone. Learn how to evaluate the credibility of online sites based on their URLs an
0 views • 10 slides
Case Study on Web-Scale Natural Language Processing for URL Word Breaking
Explore how web-scale NLP techniques are applied to break down URLs into words effectively. Various models and evaluations are discussed to address the challenges of handling diverse language styles and the need for matched data to ensure accuracy in different languages. The study emphasizes the imp
0 views • 21 slides
Potential Applications of GEONETCast at NMSB, Belize
The National Meteorological Service of Belize heavily relies on the internet for forecasting and diagnostic products, making GEONETCast a valuable alternative during internet failures. Various crucial operational products, such as upper-air sounding profiles, high-resolution satellite imagery, globa
0 views • 8 slides
Understanding Linked Data: Basics to Publishing and Beyond
Delve into the world of Linked Data with topics ranging from its fundamental principles like URIs, RDF, and Triples to practical aspects like publishing data using standard web technologies such as HTTP. Explore the essence of RDF graphs, the significance of naming things with URLs, and ways to prov
0 views • 26 slides
Understanding How Browser Engines Work
Browser engines play a crucial role in how web browsers retrieve, present, and traverse information resources on the World Wide Web. This process involves fetching a page, interpreting URLs, rendering content with layout engines, and utilizing components like the host application. Popular layout eng
0 views • 10 slides
PHP File I/O Functions and Query Strings Explained
This content covers PHP file input/output functions such as file reading, writing, and manipulation, along with an explanation of query strings and parameters in URLs. It delves into how PHP can interact with user-provided parameters to customize output, as well as practical examples and common idio
0 views • 14 slides
ICE Clear Credit Disaster Recovery Test Information
ICE Clear Credit will participate in the FIA Disaster Recovery Test on October 14th. The test timings, applications available, and precautions for participants are detailed. Participants must verify connection to CDS clearing applications via provided URLs. Various functionalities such as Managed Fi
0 views • 8 slides
Understanding HTTP Basics and Common Status Codes
Delve into the world of Hypertext Transfer Protocol (HTTP). Learn about HTTP methods, response status codes, interesting headers, HTTP proxies, maintaining URLs, and form submission in web development. Explore the fundamentals of client-server communication over the web.
0 views • 11 slides
Hunting Cross-Site Scripting Attacks in the Network
Detect suspicious URLs and prevent XSS attacks with xHunter, a tool by Elias Athanasopoulos and team at FORTH-ICS, Greece. Explore the motivation, current status, targets, and orchestration of XSS incidents. Learn about the anatomy of XSS exploits and the operation of xHunter in identifying JavaScri
0 views • 48 slides
PHP File Handling Functions Overview
The PHP file handling functions discussed in the content include mkdir, rmdir, unlink, reading contents from remote files, file_get_contents, rename, strtotime, and gmdate. Each function serves a specific purpose in file manipulation, such as creating directories, removing files, reading contents fr
0 views • 11 slides
Analysis of Unique URLs Retrieval Patterns in Web Logs
This analysis delves into the retrieval patterns of unique URLs from web logs, revealing that a significant percentage of URLs are re-presented from different client IP addresses. The study identifies top repeaters and examines instances of potential proxy device usage based on AS locations.
0 views • 15 slides
Analyzing Android Applications for Malware Detection
Android applications have become a prime target for cybercriminals, leading to an increase in Android malware. The authors introduce a mobile sandbox for automated analysis of Android apps, combining both static and dynamic methods. Static analysis inspects downloaded apps and their source code, whi
0 views • 20 slides
Upcoming Changes to IPEX Fault Reporting Journey
This pack explains the upcoming changes to the IPEX fault reporting journey for customers. A new BT Wholesale Voice Products Ordering and Support System will be introduced in March 2017. Customers will need to transition to the new online IPEX fault reporting journey via the BTWholesale.com web port
0 views • 6 slides
MLA 8th Edition Changes: Basics and Examples
The MLA 8th edition brings changes to formatting entries, emphasizing uniform double-spacing, using quotation marks for articles, and italicizing titles. This guide provides examples for formatting various sources like websites, web magazines, and scholarly journals, including details on citing auth
0 views • 9 slides
Understanding Session Management Challenges in Web Applications
Session management is crucial in web applications to maintain user authentication and authorization. This presentation delves into the evolution of session management, highlighting issues with HTTP authentication, the use of session tokens, and challenges in storing and securing session data. Variou
0 views • 18 slides
Understanding the Architecture of the World Wide Web
The World Wide Web (WWW) is a vast repository of information accessible through a distributed client-server system. Users interact with web pages hosted on servers through browsers, utilizing URLs to navigate between different sites. This system consists of clients (browsers) and servers, where clie
0 views • 44 slides
Insider's Guide to Accessing NLM Data EDirect for PubMed
Learn how to access PubMed data efficiently using EDirect, delve into extracting and formatting data, understand the power of APIs like E-utilities, and discover the ease of using URLs as database queries. Maximize your research capabilities with tips and insights shared in this comprehensive guide.
0 views • 42 slides
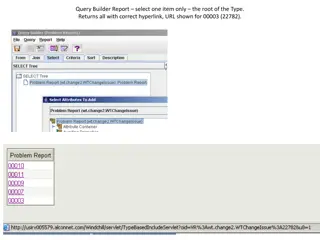
Troubleshooting Hyperlink Issues for Query Builder Report
Learn how to troubleshoot hyperlink issues in a Query Builder report, including creating correct hyperlink URLs, passing reports to Cognos, and understanding syntax errors with URL encoding.
0 views • 5 slides
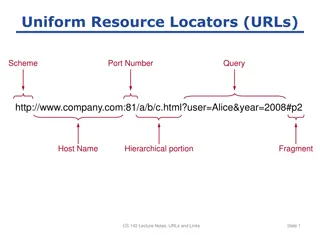
Understanding URLs and Links in Web Development
This content delves into the intricacies of Uniform Resource Locators (URLs) and their significance in web development. It covers topics such as URL structure, port numbers, query parameters, and fragments. Examples of absolute and relative URLs, along with anchor definitions and other uses of URLs
0 views • 4 slides
Understanding the Threat of Unintended URLs in Social Media
Characterising the potential threat posed by unintended URLs in social media, this study identifies the risk stemming from automatic rendering of clickable links. The research delves into the background of Top Level Domains (TLDs), the issue of unintended URLs caused by forgotten spaces, and propose
0 views • 21 slides
Understanding FMP URLs for FileMaker Systems
Delve into the comprehensive guide on FMP URLs for FileMaker systems, exploring their structure, potential, and practical applications. Learn how to leverage FMP URLs effectively to enhance your FileMaker solutions and maximize their capabilities. Discover the nuances of FMP URLs with detailed expla
0 views • 29 slides
Annual Air Monitoring Data Certification Process Overview
In the annual air monitoring data certification process, the State or local agency must certify data collected by various monitors at specified sites. The certification letter and summary reports are due by specific dates each year to the EPA Regional Administrator. Additionally, precision and accur
0 views • 23 slides