Active Directory Self Service Password Reset Tool, cionsystems
It provides the feature of delegated web access administration, self-registration, self-service and password management. \/\/rb.gy\/1tjfv5
2 views • 2 slides
Digital Wellness and Password Security Lesson for Students
This lesson focuses on promoting digital wellness and teaching students about password security. It covers topics such as creating strong passwords, safeguarding personal information, and the importance of balancing online and offline interactions. Through activities and discussions, students learn
0 views • 13 slides
Unlocking Solutions: Addressing QuickBooks Company File Incorrect Password Issue
Unlocking Solutions: Addressing QuickBooks Company File Incorrect Password Issues\nQuickBooks, a vital tool for businesses, can encounter password-related hurdles, disrupting workflow. This guide explores causes and solutions to incorrect password issues. Forgotten passwords, user permission errors,
1 views • 5 slides
Cybersecurity Best Practices for Password Protection and Incident Response
Enhance your cybersecurity knowledge with insights on password management, cybercriminal tactics, creating strong passwords, and password complexity. Learn how to safeguard your data and prevent cyber threats by implementing strong password rules, multi-factor authentication, and incident response s
2 views • 24 slides
Device Settings and Strong Passwords for Digital Citizenship
This lesson focuses on understanding device settings and the importance of creating strong passwords for digital citizenship. It covers topics such as changing backgrounds, locking screens, creating strong passwords, common password mistakes to avoid, and tips for password safety. The lesson also in
2 views • 11 slides
Strengthen Your Digital Literacy with Strong Password Strategies
Enhance your digital literacy by learning about the importance of strong passwords, strategies for creating secure passwords, and the role of password managers. Explore various resources, videos, and tools to improve your password security and protect your online accounts effectively.
0 views • 5 slides
Promote Feature Adoption with Self-Service Password Reset Posters
Enhance feature adoption of self-service password reset among your employees with these ready-to-use posters. Simply customize and print them to encourage password security awareness in your workplace. Don't risk productivity downtime due to forgotten passwords – empower your team to reset their p
0 views • 13 slides
Evolution of Password Security in Modern Computing
Delve into the historical origins of passwords, their significance in cybersecurity, and the current methods employed to safeguard digital assets. Explore the challenges posed by fast computing systems and discover innovative solutions and tools like LastPass, Keeper, and Dashlane in the realm of pa
0 views • 15 slides
Reset Internet Banking Transaction Password Online Guide
Complete your internet banking transaction password reset online using your ATM card details and registered mobile number for OTP verification. Follow the step-by-step instructions provided with images for a successful reset process and confirmation.
0 views • 8 slides
Enhancing Security with Windows Hello for Business
Windows Hello for Business provides a more secure non-password credential for Windows 10/11 devices, implementing 2FA/MFA to combat password-related vulnerabilities. This article explores the benefits, security measures, and implementation steps of Windows Hello for Business, addressing the challeng
8 views • 24 slides
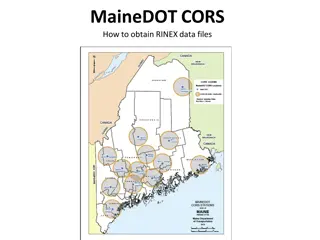
Obtaining RINEX Data Files from MaineDOT CORS
Obtain RINEX data files from MaineDOT CORS by following a few simple steps. Login and password are required, and guest login is no longer an option. The data is collected at one-second intervals and is available for Real-Time-Kinematic (RTK) users. To access the files, visit the provided link, selec
0 views • 17 slides
Integration: Geometrical Interpretation, Properties, and Methods
Integration is the inverse process of differentiation, where we find a function whose differential is given. This process involves basic formulae, methods like integration by parts, and geometrical interpretation. Properties of indefinite integrals and techniques such as integration by substitutions
6 views • 28 slides
Assessment of Progress on Regional Integration in Africa: Key Messages and Recommendations
Regional integration in Africa remains vital for economic transformation, with progress and challenges highlighted in a technical report. The African Continental Free Trade Area (AfCFTA) is a significant milestone for boosting trade and market integration on the continent. Efforts are needed to addr
0 views • 5 slides
Progress Report on Regional Integration in Africa
The document presents an assessment of progress on regional integration in Africa, highlighting challenges and achievements in advancing integration agendas. It emphasizes the importance of regional integration, particularly in the context of the AfCFTA, to foster economic transformation and resilie
1 views • 6 slides
Promoting Integration Through Public Discourse: International Conference Insights
Public discourse plays a crucial role in shaping societal perceptions of diversity and integration. The Integration Foundation International Conference delved into communicative practices that both promote and hinder integration, emphasizing the responsibility of public communicators in constructing
6 views • 15 slides
Recovering Console Password for Cisco ASR5000/5500 - Step-by-Step Guide
Learn how to recover the console password for Cisco ASR5000/5500 devices using a simple step-by-step process. Follow pre-requisites, problem reproduction steps, and the solution overview to regain access to your console interface.
2 views • 14 slides
Laptop Roll-Out Information and Schedule for Students at HPK
Information and guidelines for the upcoming laptop roll-out event at HPK including distributing password cards, password training, roll-out locations, times by grade, and instructions on global protection software. Students must follow the specified steps to receive their laptops successfully.
0 views • 14 slides
Step-by-Step Guide to Password Recovery and Account Activation
Detailed instructions on how to recover your password, activate your account, and securely log in for the first time following the system upgrade. Follow each step carefully to ensure a smooth transition into the upgraded system.
0 views • 9 slides
Safely Logging Password-Derived Measurements for Web Login Systems
Design a secure measurement framework called Gossamer to assess risks associated with password-based measurements for web login systems. Explore ways to differentiate between benign and malicious traffic, and consider adding instrumentation to enhance security. Learn how attackers exploit password-d
0 views • 12 slides
How to Login to BridgeIT & Create MAPFRE Password
Learn how to login to BridgeIT on August 6th at bridgeit.mapfre.com:4430 and create or reset your MAPFRE password. Follow the step-by-step instructions provided using your MAPFRE username. A dedicated support helpline is available for any login difficulties.
0 views • 5 slides
Guide to Logging in to SIRA UW with MAPFRE Credentials
Learn how to access SIRA UW platform using your MAPFRE credentials starting August 6th. Follow the steps for creating and resetting your password, ensuring a smooth login process. Utilize your MAPFRE username and be prepared to wait 10 minutes post password reset. Reach out to the dedicated support
0 views • 5 slides
Guide to Logging in and Setting Up Core-CT for the First Time
Accessing Core-CT for the first time involves using your State of Connecticut Employee ID and temporary password. Follow the steps to log in, set up a new password, and establish a forgotten password help feature. This guide provides clear instructions and visuals for each step.
0 views • 19 slides
Step-by-Step Guide to Creating a Wikipedia Account
Follow these detailed steps to create your own Wikipedia account easily, including selecting a language, inputting a username and password, and entering your email address. Ensure a secure and unique username and password for a successful account setup.
0 views • 13 slides
Transportation and Handling of Endcap C for Integration at CERN
Utilizing expertise in transporting SCT Endcap C, the project involves designing cradles for secure transportation minimizing integration work at CERN. Input required from CERN Integration team for tooling design. Detailed inspection before departure crucial. Tasks include reception, testing, connec
1 views • 10 slides
Interactive Password Security Activity for Children
This presentation recaps the importance of strong passwords, techniques for creating them, and the significance of two-factor authentication. The lesson notes guide discussions on creating secure passwords using the "three random words" method and avoiding personal details. The interactive game "Gue
0 views • 4 slides
Integration: From Marginal Utility to Definite Numeric Solutions
Integration plays a crucial role in mathematics, connecting concepts such as marginal utility and total utility functions, differential coefficients, rules for indefinite integration, and the process of definite integration. Learn about notation, rules, and examples to grasp the fundamentals and app
2 views • 23 slides
Best Practices for Secure Password Storage - OWASP Foundation Guidelines
Learn about secure password storage techniques recommended by OWASP Foundation, including adding salt, slowing down hashing functions, using HMAC isolation, and imposing difficult verification processes on attackers. Remember to use proper encoding, avoid limiting password types or lengths unreasona
0 views • 10 slides
Techniques and Tools for Offline Password Cracking
Explore the world of offline password cracking techniques using tools like John the Ripper. Learn about the motivation behind cracking user account passwords, gaining root privilege, and compromising vulnerable systems to obtain password hashes for further exploitation. Enhance your understanding of
0 views • 15 slides
Fine-Grained Password Policies in Active Directory
Explore the intricacies of Fine-Grained Password Policies (FGPP) in Active Directory, covering topics such as domain account policies, policy recovery methods, interpreting pwdProperties attribute, and implementing PSOs for granular password settings. Delve into the nuances of password complexity, h
0 views • 11 slides
Africa Regional Integration Index Report 2019 Summary
The Africa Regional Integration Index Report 2019 presented at the Conference of Ministers in Marrakech, Morocco, highlights the framework, dimensions, indicators, and progress on regional integration in Africa. It focuses on aspects such as free movement of people, trade integration, infrastructura
1 views • 10 slides
Integration Landscape at Microsoft: Journey to Azure Logic Apps
Mayank Sharma and Divya Swarnkar, Senior Program Managers at Microsoft, discuss the current integration landscape at Microsoft, highlighting the transition to Azure Logic Apps. They emphasize the modernization of integration through metadata-driven flows and patterns for enhanced business agility an
0 views • 13 slides
Microsoft Integration Day - Cloud Automation and Platform Functionality
Explore the Microsoft Integration Day event held on September 10, 2016 in Bengaluru, focusing on cloud-based application integration, Azure services, Logic Apps for business process automation, various connectors, and upcoming integration capabilities. Discover the power of automating business proce
0 views • 20 slides
Password Security: Techniques and Best Practices
Delve into the world of password security with this comprehensive guide, covering topics such as password gathering, cracking strategies, tools, types of passwords, hashes, salting, better hashes, and hash identification. Learn how to enhance security measures and protect against malicious attacks.
0 views • 20 slides
Official Bilingualism and Monolingual Integration Policies in Finland
Official bilingualism in Finland between Finnish and Swedish is a crucial aspect of the country's integration policies. The challenges faced by monolingual integration and the importance of proficiency in the national languages for asylum seekers are highlighted. The role of language in integration,
0 views • 14 slides
CampusCE Integration Overview and Milestones
This collection provides an in-depth look at the integration of CampusCE with ctcLink PeopleSoft, detailing the phases of integration, creation of pages, set up of admin units and subjects, and milestones achieved by various colleges. The process involves building courses, adding fees, student enrol
0 views • 30 slides
Protecting Password Identifiers in IEEE 802.11-21
This submission addresses the need for safeguarding password identifiers in SAE to ensure privacy and prevent attackers from constructing personally identifiable information. The document presents two potential solutions, ultimately recommending the use of symmetric cryptography for efficient protec
0 views • 11 slides
Password Guessability Metrics in Real-World Security
Delve into the realm of password guessability metrics to enhance password security. Explore how measuring guessability aids in eliminating weak passwords, aiding users in creating stronger ones, and assessing security against various cracking algorithms. Uncover the significance of statistical and p
0 views • 27 slides
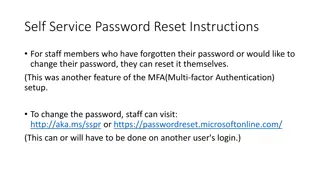
Self-Service Password Reset Instructions for Staff Members
Staff members can easily reset or change their password through self-service options using Multi-Factor Authentication. They can visit the provided links, verify their identity through email and phone number, and reset their password securely. Follow the step-by-step guide for a hassle-free password
0 views • 4 slides
Guide to Logging into Your Chromebook
This step-by-step guide provides instructions on how to log into your Chromebook using either your student ID and password or a QR code. Simply open the lid, press the power button, select "Next," and then proceed to log in with your credentials. For password login, enter your student ID and the def
0 views • 6 slides
Enhancing Wi-Fi Security with User-Friendly WPA3 Passwords
Proposal to enhance Wi-Fi security by incorporating password and password identifier hashes in the SAE commit exchange, enabling devices to hint to access points which password will be used. This approach aims to improve network efficiency and user experience while addressing privacy concerns associ
0 views • 8 slides