Step-by-Step TCP/IP Configuration on Windows 10 Client
Detailed guide on configuring TCP/IP settings on a Windows 10 client, including preparation steps, configuration steps, and verification of settings. The guide provides clear instructions with accompanying images for each step.
1 views • 12 slides
WHONET Training Course: Laboratory Configuration and Setup
Understanding the laboratory configuration process in WHONET is crucial for effective data entry and analysis. This module guides users on setting up a new laboratory, entering country and lab details, defining antibiotics, sample locations, and data fields, creating microbiological alerts, and savi
3 views • 57 slides
Proposal for Location Configuration Information (LCI) in IEEE 802.11 Beacons and Probe Responses
This document proposes the inclusion of Location Configuration Information (LCI) data in a standard information element broadcast in Beacons and Probe Responses within IEEE 802.11 networks. By enhancing the accessibility of infrastructure location to non-AP STAs, this proposal aims to simplify locat
1 views • 5 slides
IEEE 802.11-20/0668r1: EHT BSS Configuration Proposal
The document discusses the configuration of a 320 MHz BSS in the context of 6 GHz regulations, focusing on EHT operation elements such as channel width indication, CCFS principles, and BSS advertisement settings. It proposes design principles for managing legacy and EHT STA operations, emphasizing s
0 views • 14 slides
Enhancing EPS Authorization and Configuration Options in 5G Networks
The proposal focuses on enhancing authorization and configuration options in EPS using protocol configuration options. It discusses the attach procedure, ePCO checking, and the importance of ePCO support in the network architecture. The solution presented emphasizes the role of MME, SGW, and PGW-C+S
0 views • 8 slides
Discussion on 5G NR CADC Configuration Handling in RAN5
The discussion revolves around the existing Tdocs and WIs focusing on how to handle 5G NR CADC configuration within RAN5. It includes proposals to streamline guidelines and checklists to effectively manage new configurations. Various operators and entities like CMCC, Huawei, Ericsson, China Unicom,
0 views • 9 slides
Discussion on Multi-PUSCH Configuration for UTO-UCI Content Moderator at Ericsson
This discussion encompasses the configuration and implications of the Multi-PUSCH setup based on agreed parameters within the UTO-UCI content moderation context at Ericsson. It delves into varying configurations, potential impacts, and considerations for effective utilization. The slides provide ins
0 views • 17 slides
5G Use Case Proposal for Dublin Ericsson
This proposal outlines the use of NETCONF for configuration management in 5G networks, focusing on Dublin. It covers topics like Configuration with NETCONF, NETCONF Overview, NETCONF Security, YANG Overview, and Proposed Use Cases and Requirements for Dublin. The proposal emphasizes the importance o
7 views • 20 slides
Focal Point Responsibilities in Data Management System
Detailed instructions on key responsibilities of a focal point including user creation, configuration backups, data export, maintenance, and configuration import in a data management system. Tasks involve creating and editing users, exporting configurations and data, and maintaining system integrity
0 views • 12 slides
Techno-Economic Analysis of Calcium Looping Processes for Low CO2 Emission Cement Plants
This study explores the application of Calcium Looping (CaL) processes in cement plants to reduce CO2 emissions. The process involves using CaO as a sorbent to capture CO2 from flue gas, with the potential for integration at different points in the cement production process. The Tail-end CaL configu
3 views • 14 slides
Managing Passive Host and Service Checks with Nagios Core
Learn how to enable passive host and service checks in Nagios Core via the configuration file, allowing for monitoring without actively polling the hosts and services. Understand the setup, configuration, and usage of passive checks in your monitoring system. Explore examples and best practices for
0 views • 30 slides
Comprehensive Setup and Configuration Guide for Office Management Software
Detailed setup and configuration instructions for your office management software, including customizing company information, tax rates, localization settings, barcode types, stock management, receipts, and invoices. Ensure a seamless setup process by following the step-by-step guidance provided in
0 views • 31 slides
Configuration Examples for IP SLA with Object Tracking
Learn how to configure and troubleshoot IP SLA with Object Tracking using detailed examples for Static Routing, HSRP, and Policy Based Routing. Find out where Object Tracking can be implemented and when not to use it in various network scenarios. Understand the configuration components, including de
2 views • 17 slides
Evolution of Configuration Management in Software Engineering
Explore the evolution of configuration management in software engineering, highlighting key practices like cloud-based IDE, shared repositories, and unobtrusive configuration management. Understand the importance of modern best practices in software development, traditional vs. optimistic approaches
0 views • 20 slides
UITF MPS System Requirements and Protection Details
Combining hardware configuration and CEBAF-style FSD protection, the UITF MPS system ensures laser safety, vacuum control, and GUN HV stability. It protects against beam loss, maintains UHV, safeguards viewers, magnets, RF components, and more through a series of interlocks and comparator systems. T
0 views • 7 slides
BOR-60 Reactor Operating Experience and Design Configuration
The BOR-60 reactor, a key component of sustainable clean energy, has a rich history since its construction in the USSR. Its design configuration includes various components such as coolant inlet nozzles, control rod mechanisms, and fuel loading ducts. The core arrangement consists of control rods an
0 views • 12 slides
Overview of Computational Complexity Theory: Savitch's Theorem, PSPACE, and NL-Completeness
This lecture delves into Savitch's theorem, the complexity classes PSPACE and NL, and their completeness. It explores the relationship between time and space complexity, configuration graphs of Turing machines, and how non-deterministic space relates to deterministic time. The concept of configurati
0 views • 67 slides
3GPP TSG-RAN-WG4 Meeting #95e - CSI-RS Configuration and Measurement Definitions
This document outlines the discussions and decisions made at the 3GPP TSG-RAN-WG4 Meeting #95e held electronically from 25th May to 5th June 2020. The focus was on defining CSI-RS configuration and intra/inter-frequency measurements for CSI-RS based L3 measurements, with detailed requirements and sc
0 views • 5 slides
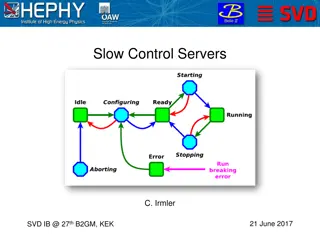
Slow Control Servers and Network Configuration for SVD Management
The documentation discusses the setup and requirements for slow control servers, network configuration, FADC server status, ENV server status, and general SC server status for SVD management. It outlines the need for backup servers, minimum server requirements, server specifications, procurement det
0 views • 11 slides
LArDPS to eFEX Test Configuration for FOX Demonstrator
Configuration details and diagrams for testing the direct path from the LArDPS to eFEX in the FOX Demonstrator, including optical insertion loss measurements, offset calibration using different setups, and diagrams without splitters. The setup matches the planned configuration for the test.
0 views • 34 slides
Data Testing Methodology and Analysis Guidelines for Mobile Networks - A Case Study
Presentation outlining a data test measurement system for mobile networks, focusing on methodology, hardware components, measurement profiles, configuration, and analysis guidelines. The case study of Ghana's Ashanti Region is discussed, highlighting the test methodology and configuration specificat
0 views • 22 slides
Engineering-To-Order Product/System Configuration Strategies
Strategies for dealing with engineering-to-order product/system configuration including assemble-to-order, make-to-order, configure-to-order, and engineer-to-order approaches. Highlights different levels of diversity, challenges, and solutions in personalized system configurations.
0 views • 10 slides
Overview of Package Management in Software Configuration
Understanding package management is vital for software installation and configuration. It involves making installation atomic, ensuring dependencies, and utilizing tools like RPM and deb. High-level tools like yum and APT further simplify package management by handling internet-based package searche
0 views • 21 slides
Software Quality and Source Code Management Best Practices
Effective source code management is crucial for software quality assurance. This involves locking down code, baselining milestones, managing code variants, and ensuring traceability. Software Configuration Management (SCM) is key, encompassing configuration items and core concepts like creating base
0 views • 34 slides
Enhancing Visit Settings and Configuration for 2024 Annual Redrock Conference
Explore the comprehensive features of visit settings and configuration for the upcoming 2024 Annual Redrock Conference. From allowing staff and students to provide booking reasons to customizing kiosks and enhancing satisfaction feedback mechanisms, these settings offer a tailored and efficient visi
0 views • 12 slides
Updates on iKAGRA Installation and Configuration Changes
The report discusses changes in the iKAGRA configuration from Fabry-Perot Michelson Interferometer to Michelson Interferometer due to schedule constraints and budget limitations. The document outlines the revised schedule for installation tasks, shift applications, and the impact on the KAGRA projec
0 views • 16 slides
Overview of Hydrogen: Properties, Isotopes, and Characteristics
Hydrogen, a colorless gas with atomic number 1 and mass 1.008 amu, exhibits electropositive and electronegative characteristics due to its electron configuration. It has three isotopes - protium, deuterium, and tritium - with varying reaction rates. Protium is the most abundant isotope. This element
0 views • 8 slides
Trigger Data Analysis in Physics: ATLAS Software Tutorial
This content provides detailed information on trigger data analysis for physics, focusing on ATLAS software tutorials conducted by Ricardo Gonçalo at Royal Holloway in April 2009. It covers features extraction algorithms, trigger configuration and data management, trigger-aware analysis, and the Tr
0 views • 26 slides
OSCAR Project Proposal for OPNFV
The OSCAR Project is a proposed initiative for OPNFV by Stuart Mackie, focusing on system configuration and reporting deployment for OPNFV platform and virtual infrastructure. The project aims to create templates for building different OPNFV stacks, preload required VNFs, and enable rapid deployment
0 views • 14 slides
Specific Parameters for DL Interruptions in 5G Network Testing
Detailed discussion and guidelines for verifying symbol-level DL interruptions in 5G network testing scenarios such as switching between LTE and NR carriers, inter-band ENDC TDD configuration, and FDD-TDD CA (SA) TDD configuration. The document covers specific parameters, test options, and symbol ve
0 views • 6 slides
S32K3 Real-Time Development Training Overview
Explore the S32K3 Real-Time Development (RTD) training for Logic Control Unit (LCU) in automotive applications. Learn about LCU configuration, main API functions, example codes, Look-Up Table (LUT) setup, and tips for optimal usage. Discover how LCU interacts with combinatorial logic, latches, and a
0 views • 22 slides
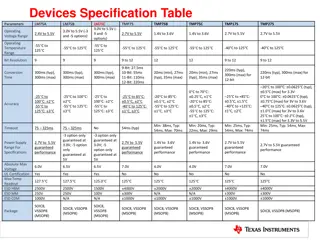
- "Temperature Sensor Devices Specifications and Register Configuration
- This comprehensive content provides detailed specifications and register mappings for various temperature sensor devices, including LM75A, LM75B, LM75C, TMP75, TMP75B, TMP75C, TMP175, and TMP275. It covers parameters such as operating voltage range, resolution, accuracy, operating temperature rang
0 views • 6 slides
Insights into Operating Experience and Configuration Management in Nuclear Power Plants
Explore the significance of Operating Experience (OE) in refining machine and human performance, reinforcing desired behaviors, solving problems timely, and sharing industry-wide knowledge in nuclear power. Learn from examples highlighting the importance of configuration management in mature nuclear
0 views • 11 slides
PeopleSoft Campus Solutions Configuration Changes
This content showcases upcoming changes in PeopleSoft Campus Solutions configuration, including disabling the Campus_ID field and hiding the View/Download Sample Data File link. It also details 19 different navigation paths within the system for various campus community and student-related tasks. Ad
0 views • 8 slides
ChannelFinder Setup and Deployment Diagrams with RecSync Components
Includes setup and deployment diagrams for ChannelFinder on vclx4, along with details about RecSync components for EPICS module communication. Also covers RecCaster configuration and registration of support components. The documentation further discusses RecReceiver setup, Python integration with Tw
0 views • 8 slides
Advanced Neutronics Parameters for Fusion Chamber Configuration with Magnetic Intervention
Detailed analysis and design considerations for a fusion chamber configuration utilizing magnetic intervention to optimize neutronics parameters. The discussion includes blanket configuration, neutron wall loading distribution, blanket design options, nuclear design requirements, and dimensions meet
0 views • 12 slides
Recap of eZeeKonfigurator Notice Configuration and Zeek Week Oct 2019
A summary of events involving a talk at Zeek Week, issues with notice configuration, experiences with Zeek/Bro, and the introduction of eZeeKonfigurator for configuring Zeek clusters. The content includes descriptions of individuals involved, challenges faced, support for cluster configurations, and
0 views • 20 slides
Efficient Skyline Batch Workflow Tool for Processing Multiple Files
Utilize Skyline Batch, a user-friendly tool developed by Ali Marsh, to run simple Skyline workflows on multiple files efficiently. This tool is ideal for overnight processing, reprocessing data easily, and sharing workflows across different computers. Quickly transform Skyline templates into report
0 views • 4 slides
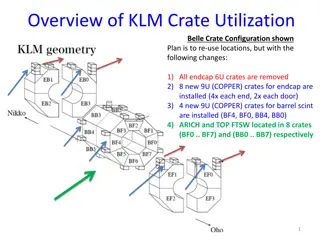
KLM Crate Utilization Belle Crate Configuration Overview
The KLM Crate Utilization Belle Crate Configuration involves reusing locations with specific changes: removal of endcap 6U crates, installation of new 9U (COPPER) crates for endcap and barrel scintillators, and relocation of ARICH and TOP FTSW to 8 crates each. Check out the detailed changes and con
0 views • 5 slides
Removal of FILS IP Address Configuration in IEEE 802.11-14/0093r2
This document details the rationale behind the proposal to remove FILS IP Address Configuration in IEEE 802.11-14/0093r2. The author, Hitoshi Morioka, explains that the need for this configuration is redundant due to the HLP encapsulation's ability to support all required functions. By eliminating c
0 views • 18 slides