Creating a CollegeBoard Account
Learn why you should create a College Board account for access to AP, SAT, and PSAT scores, college lists, free score reports, and more. Follow the steps to create an account, providing necessary information like legal name, email, date of birth, and address. Remember your username and password, set
5 views • 6 slides
Boost Your Connectivity: Unleash the Power of WiFi Repeater 192.168.188.1 Setup
Boost your WiFi signal effortlessly with our user-friendly repeater that utilizes the 192.168.188.1 setup interface for quick and easy installation. No more frustrating dropped connections or slow internet speeds in certain areas. Our repeater extends your existing WiFi network, ensuring every corne
18 views • 9 slides
A Comprehensive Guide to 192.168.188.1: Login and Troubleshooting
192.168.188.1 serves as the default login gateway for numerous WiFi routers, offering access to various network configurations. In this guide, we will delve into the essential aspects of 192.168.188.1, encompassing both the login process and troubleshooting procedures.\n \nTo know more : https:\/\/1
8 views • 2 slides
H3C GB0-192 Certification: A Comprehensive Study Plan
Start Here--- https:\/\/bit.ly\/3HCewZV ---Get complete detail on GB0-192 exam guide to crack H3C Certified Network Engineer for Routing & Switching Plus (H3CNE-RS ). You can collect all information on GB0-192 tutorial, practice test, books, study material, exam questions, and syllabus. Firm your kn
5 views • 17 slides
Exploring the Benefits of 192.168.188.1 Admin Setup
Embrace the Benefits of 192.168.188.1 Admin Setup! Seamlessly manage your network settings, enhance connectivity, and elevate user experiences effortlessly.\n\nTo Know more: https:\/\/1921681881.com\/192-168-188-1-admin-setup-how-to-reset-netgear-wifi-range-extender\/
2 views • 2 slides
Enhance Your Wireless Range: 192.168.188.1 Wireless Extender Setup with Top Apps
Are you tired of weak Wi-Fi signals limiting your internet access? Fear not! With the 192.168.188.1 Wireless Extender Setup and some top-notch apps, you can extend your wireless range and enjoy seamless connectivity throughout your home or office.\n\nfor more info: https:\/\/1921681881.com\/192-168-
7 views • 2 slides
Troubleshooting 192.168.188.1 Not Working: Common Causes and Solutions
192.168.188.1 Not Working? Don\u2019t Panic, We\u2019ve Got This! This troubleshooting guide aims to explore the top reasons behind such errors and provide solutions to rectify them.\n\nFor a detailed guide: https:\/\/1921681881.com\/how-to-fix-1921681881-not-working\/
1 views • 2 slides
Troubleshooting Guide: Fixing the 192.168.188.1 Not Working Issue
Discover effective solutions to resolve the 192.168.188.1 not working issue with expert troubleshooting tips and guidance. Get your network back up and running smoothly with step-by-step instructions provided at 192168111.net.\n
14 views • 1 slides
Unlocking Solutions: Addressing QuickBooks Company File Incorrect Password Issue
Unlocking Solutions: Addressing QuickBooks Company File Incorrect Password Issues\nQuickBooks, a vital tool for businesses, can encounter password-related hurdles, disrupting workflow. This guide explores causes and solutions to incorrect password issues. Forgotten passwords, user permission errors,
1 views • 5 slides
Massey Ferguson MF 168 MKIII 168 F TRACTORS (FR) Parts Catalogue Manual Instant Download
Please open the website below to get the complete manual\n\n\/\/
0 views • 29 slides
Massey Ferguson MF 168 MKIII 168 S TRACTORS (FR) Parts Catalogue Manual Instant Download
Please open the website below to get the complete manual\n\n\/\/
0 views • 27 slides
Cleanroom Technology Market Projected to Reach $168.29 Billion by 2030
Explore $168.29 billion Cleanroom Technology Market: Get exclusive insights on key market trends, segments, geographical analysis, & competitive analysis!\n
1 views • 4 slides
The Benefits of Using a Newswire Service in US
Our infographic titled \"PR Newswire: Login for Existing Users in US\" is designed to guide users through the process of accessing their PR Newswire accounts with ease. This visual guide covers five essential elements to ensure a seamless login experience:\n\nAccessing the Login Page: Learn how to n
0 views • 11 slides
Cybersecurity Best Practices for Password Protection and Incident Response
Enhance your cybersecurity knowledge with insights on password management, cybercriminal tactics, creating strong passwords, and password complexity. Learn how to safeguard your data and prevent cyber threats by implementing strong password rules, multi-factor authentication, and incident response s
2 views • 24 slides
Device Settings and Strong Passwords for Digital Citizenship
This lesson focuses on understanding device settings and the importance of creating strong passwords for digital citizenship. It covers topics such as changing backgrounds, locking screens, creating strong passwords, common password mistakes to avoid, and tips for password safety. The lesson also in
2 views • 11 slides
Strengthen Your Digital Literacy with Strong Password Strategies
Enhance your digital literacy by learning about the importance of strong passwords, strategies for creating secure passwords, and the role of password managers. Explore various resources, videos, and tools to improve your password security and protect your online accounts effectively.
0 views • 5 slides
Promote Feature Adoption with Self-Service Password Reset Posters
Enhance feature adoption of self-service password reset among your employees with these ready-to-use posters. Simply customize and print them to encourage password security awareness in your workplace. Don't risk productivity downtime due to forgotten passwords – empower your team to reset their p
0 views • 13 slides
Obtaining RINEX Data Files from MaineDOT CORS
Obtain RINEX data files from MaineDOT CORS by following a few simple steps. Login and password are required, and guest login is no longer an option. The data is collected at one-second intervals and is available for Real-Time-Kinematic (RTK) users. To access the files, visit the provided link, selec
0 views • 17 slides
Guide to Accessing and Sharing Your HEAR with Gradintelligence
Learn how to access and share your Higher Education Achievement Report (HEAR) through Gradintelligence. Follow the registration process, choose your username and password, log in to Gradintel.com, view official documents, share your HEAR electronically, view co-curricular activities, and access info
0 views • 12 slides
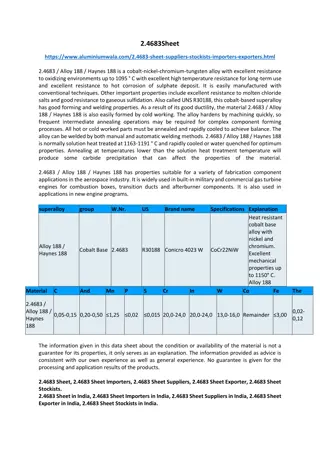
2.4683 Sheet Suppliers in Mumbai
2.4683 \/ Alloy 188 \/ Haynes 188 is a cobalt-nickel-chromium-tungsten alloy with excellent resistance to oxidizing environments up to 1095 \u00b0 C with excellent high temperature resistance for long-term use and excellent resistance to hot corrosion of sulphate deposit. It is easily manufactured w
3 views • 2 slides
Independent School District 192 Employee Handbook Overview
This employee handbook provides essential information for casual employees of Independent School District 192. It includes details on pay rates, school policies, substitute teacher qualifications, workplace injury protocols, and more. The handbook serves as a valuable resource to guide casual employ
0 views • 17 slides
Basic Switch Configuration Guide for Setting Up VLANs
Configuring switches from basic settings to creating 3 VLANs using subnet 192.168.100.0/24. Follow the commands provided for setting up VLANs, trunk links, and default gateways on switches for efficient network communication.
0 views • 10 slides
Safely Logging Password-Derived Measurements for Web Login Systems
Design a secure measurement framework called Gossamer to assess risks associated with password-based measurements for web login systems. Explore ways to differentiate between benign and malicious traffic, and consider adding instrumentation to enhance security. Learn how attackers exploit password-d
0 views • 12 slides
How to Login to BridgeIT & Create MAPFRE Password
Learn how to login to BridgeIT on August 6th at bridgeit.mapfre.com:4430 and create or reset your MAPFRE password. Follow the step-by-step instructions provided using your MAPFRE username. A dedicated support helpline is available for any login difficulties.
0 views • 5 slides
Guide to Logging in to SIRA UW with MAPFRE Credentials
Learn how to access SIRA UW platform using your MAPFRE credentials starting August 6th. Follow the steps for creating and resetting your password, ensuring a smooth login process. Utilize your MAPFRE username and be prepared to wait 10 minutes post password reset. Reach out to the dedicated support
0 views • 5 slides
Guide to Logging in and Setting Up Core-CT for the First Time
Accessing Core-CT for the first time involves using your State of Connecticut Employee ID and temporary password. Follow the steps to log in, set up a new password, and establish a forgotten password help feature. This guide provides clear instructions and visuals for each step.
0 views • 19 slides
Step-by-Step Guide to Creating a Wikipedia Account
Follow these detailed steps to create your own Wikipedia account easily, including selecting a language, inputting a username and password, and entering your email address. Ensure a secure and unique username and password for a successful account setup.
0 views • 13 slides
Step-by-Step Guide for Connect & Canvas Student Registration
Step 1: Enter your Canvas username and password, then click Login to start the registration process. Step 2: Navigate to Courses and select a course name. Step 3: Access Assignments from the course home page. Step 4: Click on the Connect assignment. Step 5: Begin the assignment. Step 6: Register as
2 views • 13 slides
Rental Housing Advisory Board - Act 188 Overview
The Rental Housing Advisory Board established under Act 188 in Vermont focuses on improving rental housing conditions through various initiatives such as composition of the board, ongoing charges, recommendations for system improvement, and more. The board aims to provide guidance, support landlords
1 views • 11 slides
Accessing NC Fast Subsidized Child Care Data in Data Warehouse
Learn how to log in and access NC Fast Subsidized Child Care data through the Data Warehouse portal. Access to the data warehouse requires a login and password, which can be obtained by contacting your LME or Institution Security Officer. The metadata available includes descriptions, table names, pr
0 views • 15 slides
Interactive Password Security Activity for Children
This presentation recaps the importance of strong passwords, techniques for creating them, and the significance of two-factor authentication. The lesson notes guide discussions on creating secure passwords using the "three random words" method and avoiding personal details. The interactive game "Gue
0 views • 4 slides
Best Practices for Secure Password Storage - OWASP Foundation Guidelines
Learn about secure password storage techniques recommended by OWASP Foundation, including adding salt, slowing down hashing functions, using HMAC isolation, and imposing difficult verification processes on attackers. Remember to use proper encoding, avoid limiting password types or lengths unreasona
0 views • 10 slides
Techniques and Tools for Offline Password Cracking
Explore the world of offline password cracking techniques using tools like John the Ripper. Learn about the motivation behind cracking user account passwords, gaining root privilege, and compromising vulnerable systems to obtain password hashes for further exploitation. Enhance your understanding of
0 views • 15 slides
Fine-Grained Password Policies in Active Directory
Explore the intricacies of Fine-Grained Password Policies (FGPP) in Active Directory, covering topics such as domain account policies, policy recovery methods, interpreting pwdProperties attribute, and implementing PSOs for granular password settings. Delve into the nuances of password complexity, h
0 views • 11 slides
Password Security: Techniques and Best Practices
Delve into the world of password security with this comprehensive guide, covering topics such as password gathering, cracking strategies, tools, types of passwords, hashes, salting, better hashes, and hash identification. Learn how to enhance security measures and protect against malicious attacks.
0 views • 20 slides
Protecting Password Identifiers in IEEE 802.11-21
This submission addresses the need for safeguarding password identifiers in SAE to ensure privacy and prevent attackers from constructing personally identifiable information. The document presents two potential solutions, ultimately recommending the use of symmetric cryptography for efficient protec
0 views • 11 slides
Password Guessability Metrics in Real-World Security
Delve into the realm of password guessability metrics to enhance password security. Explore how measuring guessability aids in eliminating weak passwords, aiding users in creating stronger ones, and assessing security against various cracking algorithms. Uncover the significance of statistical and p
0 views • 27 slides
Self-Service Password Reset Instructions for Staff Members
Staff members can easily reset or change their password through self-service options using Multi-Factor Authentication. They can visit the provided links, verify their identity through email and phone number, and reset their password securely. Follow the step-by-step guide for a hassle-free password
0 views • 4 slides
Guide to Logging into Your Chromebook
This step-by-step guide provides instructions on how to log into your Chromebook using either your student ID and password or a QR code. Simply open the lid, press the power button, select "Next," and then proceed to log in with your credentials. For password login, enter your student ID and the def
0 views • 6 slides
Enhancing Wi-Fi Security with User-Friendly WPA3 Passwords
Proposal to enhance Wi-Fi security by incorporating password and password identifier hashes in the SAE commit exchange, enabling devices to hint to access points which password will be used. This approach aims to improve network efficiency and user experience while addressing privacy concerns associ
0 views • 8 slides