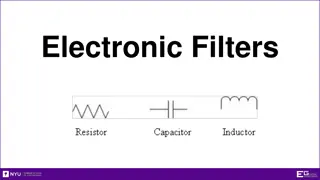
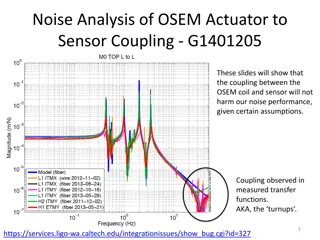
Understanding Wireshark Filters for Efficient Packet Analysis
Learn how to leverage Wireshark capture filters to customize packet analysis, enhance traffic visibility, and optimize network monitoring. Capture only the data you need, create custom filters, and streamline intrusion detection analysis with Berkeley Packet Filters (BPF). Discover the power of display filters for convenient packet viewing and analysis customization.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author. Download presentation by click this link. If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
E N D
Presentation Transcript
Contents An introduction to capture filters Why and how to use capture filters Lab up capture filters An introduction to display filters Why and how to use display filters Lab up display filters Colorizing traffic Creating a new Wireshark profile(s) Lab up profiles
Capture Filters Before Capturing. Filters enhance the flexibility of packet analysis, where a certain user is given the privilege of seeing what he/she wants to see to capture what they want to capture.
Capture Filters Wireshark offers some interesting options to configure an interface, that will be capturing traffic that meets only a certain expression, and this is achievable through the Capture Options window. Capture: Input Output Option
Berkeley packet filters Berkeley Packet Filters (BPF) provide a powerful tool for intrusion detection analysis. Use BPF filtering to quickly reduce large packet captures to a reduced set of results by filtering based on a specific type of traffic. Both admin and non-admin users can create BPF filters. https://www.ibm.com/docs/en/qsip/7.4?topic=queries-berkeley- packet-filters
Why use capture filters Capturing only traffic that meets your requirements is useful when you have a large volume of packets flowing around. Creating your custom capture filters can come in handy while you analyze a production environment.
How to use capture filters Identifiers: This is the value that you are looking for in your packets. Qualifiers: These are categorized into three different sections: Type Direction Proto
Filter Examples Bing ..
Display filters Display filters do not discard any packets; instead, the packets are hidden to make viewing convenient. Analyze Display Filter Expression
Comparison Operators The following table lists the comparison operators used to create display filters:
Logical Operators The logical operators that are used to combine different conditions together. The following table lists all of them:
Retaining filters for later use Sometimes, you will have a requirement where having access to previously created filters would make your work easy and fast enough. Wireshark gives you the facility where you can retain your display filters through their saved names and use them at a later point of time whenever required
Retaining filters for later use Go to Analyze | Display filters; this will give you a window like the one shown in the following screenshot: Now, let's try applying the filter we just created. Navigate to Analyze | Display Filter | (Scroll and select ) Display Filter | Apply.
Searching for packets using the Find dialog You can access the Find utility by navigating to Edit | Find packets or using the shortcut Ctrl + F. Some more configurable options in it: The display filter The Hex value String Search In String Options Direction
Colorize Traffic Coloring a specific set of traffic with a different rule other than the default one will be like finding a needle in a haystack. View | Edit coloring rules or clicking on the Edit coloring rules button from the main toolbar to open a window as shown in the following screenshot. Foreground Color Background Color
Practice Questions Create a display filter to show packets originating only from your IP. ip.src == 192.168.1.21 Create a display filter to see packets that are only related to the protocol Secure Socket layer. sll Create a display filter to see only the ICMP destination host's unreachable packets. icmp[0:1]=3 Create a display filter to see only TCP packets with FIN and ACK flags set. tcp[13]==18 Create a display filter to show TCP packets with a header length greater than 40. tcp.len>40 Change the coloring scheme for all the DNS query Type A packets to the color of your choice. Change Color Change the coloring scheme of all HTTP error messages to the color of your choice. Change Color Create a profile with the name DNS using a default profile, and create a capture filter in this profile that will capture DNS traffic. Then, change the coloring scheme of all DNS response packets to the color of your choice.