Traffic Analysis and Forensic Investigation Puzzle
In this scenario, Anarchy-R-Us suspects that their employee Ann is a secret agent leaking the company's secret recipe. By analyzing network traffic using Wireshark, specific questions are posed regarding Ann's activities, such as identifying her IM buddy and the contents of transferred files. The in
0 views • 21 slides
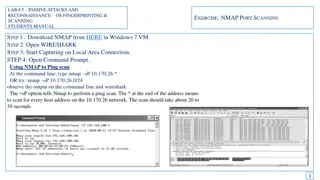
Passive Attacks and Reconnaissance using NMAP for Network Scanning
Learn how to use NMAP for passive attacks and reconnaissance through port scanning techniques like ping scan, TCP port scan, and stealth scan. Understand how to analyze the output in Wireshark to identify open ports and version numbers on target systems.
2 views • 7 slides
Network Traffic Analysis with Wireshark: Examples and Techniques
Explore the world of network traffic analysis using Wireshark through examples and practical techniques. Learn how tools like Nmap and Wireshark can be used for network scanning and detecting suspicious activities. Dive into real examples, including identifying attackers through HTTP web traffic ana
1 views • 10 slides
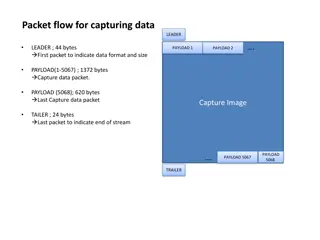
Wireshark Data Capture and UDP Analysis
Capturing data flow through packets in Wireshark reveals a series of fragmented payloads, starting with a leader packet of 44 bytes and ending with a trailer of 24 bytes. The UDP data payloads range from 44 to 1372 bytes, with specific lengths for different payloads and packets. Analysis includes UD
0 views • 4 slides
Network Monitoring Workshop - Incident Response Overview
This workshop covers various aspects of incident response, including tools and techniques such as network taps, protocol analysis with Wireshark, data summarization with Bro/Zeek, alerting with Snort/Suricata, and more. Sessions delve into topics like TLS inspection, wireless network monitoring, and
0 views • 17 slides
Network Sniffing and Protocol Analysis Overview
Learn about network sniffing, a process of capturing and interpreting network traffic, its analogies like wiretapping, environmental considerations, and protocol analysis. Understand the risks, authorization requirements, and tools like Wireshark. Explore examples of Nmap Port Scans and monitoring w
0 views • 30 slides
Understanding REST in Delphi: A Comprehensive Overview
Representational State Transfer (REST) is an architectural style for interacting with web services, providing a stateless connection between transactions. No official standard exists, but it is commonly used as an alternative to SOAP. RESTful services utilize HTTP verbs like GET, POST, PUT, DELETE,
0 views • 22 slides
Understanding Wireshark Filters for Efficient Packet Analysis
Learn how to leverage Wireshark capture filters to customize packet analysis, enhance traffic visibility, and optimize network monitoring. Capture only the data you need, create custom filters, and streamline intrusion detection analysis with Berkeley Packet Filters (BPF). Discover the power of disp
0 views • 17 slides
Wireshark Network Traffic Analysis Basics
Explore the fundamentals of Wireshark for capturing and analyzing network data. Learn about its powerful capabilities, basic functions, installation on various operating systems, and device classification methods. Discover insights into IPv4, network structures, and key concepts in cybersecurity.
0 views • 28 slides