Machine learning applied to mobile phone data for public statistics prediction
Researchers from multiple institutions are utilizing mobile phone data in Senegal to predict public statistics, leveraging machine learning techniques. Projects like GUISSTANN aim to forecast indicators from census data using telephone and mobile money data. The analysis includes call/text informati
4 views • 10 slides
Enhancing Access to Medicines and Health Products through Innovative Approaches
Global Health Centre experts discuss how building access into innovation can ensure better access to medicines, vaccines, and health products. Key ideas include planting seeds for access early in innovation, exploring alternative innovation models, and rethinking the relationship between innovation
4 views • 20 slides
2022 Thales Access Management Index
Thales Access Management Index highlights the current landscape of access security, revealing insights on multi-factor authentication adoption, remote and privileged user access management, VPN usage trends, challenges faced, and preferences towards third-party access management. The report emphasiz
2 views • 9 slides
Guidelines for Expanded Access to Investigational Drugs and Devices
Providing guidance on types of Expanded Access for drugs, biologics, and devices, this content explains the concept of Expanded Access and the criteria that must be met. It covers different types of Expanded Access for drugs and devices, emphasizing the importance of patient safety and benefit. The
0 views • 10 slides
Personnel Safety Systems and Access Control at CERN Facilities
Personnel Safety Systems at CERN include ODH detection, fire safety measures, and access control to protect personnel from hazards. Various access control layers are implemented to regulate entry to different parts of the facility, ensuring only trained personnel access underground areas. Biometric
0 views • 19 slides
Effective Telephone Conversations: Tips and Techniques
Enhance your telephone communication skills with tips, expressions, and examples for both informal and formal conversations. Learn how to handle phone calls professionally, spell names accurately, and use the phonetic alphabet effectively. Improve your telephone etiquette and make a positive impress
2 views • 15 slides
Port of Stockton Restricted Area Access Control and ID Card Policy
Access to restricted areas at the Port of Stockton facilities requires possession of a TWIC (Transportation Worker Identification Credential). Only authorized personnel, such as employees, contractors, and those with regular access, may receive a Port Access Card after approval by the Facility Secur
0 views • 6 slides
Introduction to Database Security and Countermeasures
Database security is essential to protect data integrity, availability, and confidentiality. Countermeasures such as access control, inference control, flow control, and encryption can safeguard databases against threats. Access control restricts user access, inference control manages statistical da
0 views • 26 slides
O3 Access Control Solution Overview
O3 Access Control Solution offers unique selling points like single-seat management software, role-based permissions, customizable user information, and more. The system includes a compact controller with multi-format reader support and BACnet Access objects. It integrates with other O3 modules for
0 views • 10 slides
Employee Assistance Program at Fermilab
Fermilab's Employee/Users Assistance Program offers comprehensive online, telephone, and virtual services for employees, household members, and users at the lab. Services include counseling, legal and financial consultations, work/life referrals, and new offerings like life coaching and personal ass
0 views • 5 slides
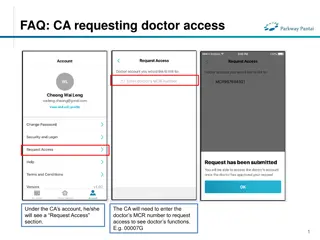
FAQs for Doctor and Clinical Assistant (CA) Account Access Management
Learn how CAs can request access to doctors' functions by entering the MCR number, how doctors can grant or remove CA access, and how CAs can manage access to multiple doctors. The process includes requesting, approving, and unlinking accounts, ensuring efficient and secure access management in a cl
0 views • 4 slides
Mastering Telephone Communication Skills Workshop Series
Enhance your telephone communication skills with a comprehensive workshop series covering teaching methods, group work strategies, and modules focusing on introduction, assessment tools, and role plays. Explore key considerations for planning, engaging with various learner groups, and optimizing lea
2 views • 66 slides
Mastering Telephone Skills in Healthcare
Develop your telephone skills in healthcare by following guidelines for answering calls, identifying purposes, handling various types of calls, addressing clinical issues, and implementing effective telephone tips. Proper documentation of calls is essential for legal protection and may be a part of
1 views • 12 slides
Enhancing Secure Telephone Identity and Caller Authentication
The STIR Working Group aims to address the issues surrounding the reliability of caller identities in telecommunication networks. By specifying internet-based mechanisms for verifying the authorization of calling parties, STIR seeks to combat threats like caller ID spoofing and unauthorized use of t
0 views • 11 slides
Online Payment Guide: Electricity and Telephone Bills
Conveniently pay your electricity and telephone bills online with step-by-step instructions for using the Paytm app for electricity bills and visiting the respective mobile operator's website for telephone bills. Complete your payments using various methods like Debit Card, Credit Card, Net Banking,
0 views • 12 slides
Understanding Audio-COT in Medical Training
The Audio-COT is a valuable tool used in medical training to assess telephone consultation skills, complementing Workplace Based Assessment (WPBA). Supervisors review trainees' telephone consultations, provide feedback, and complete Audio-COT assessments, which count towards training requirements. T
0 views • 24 slides
Evolution of Electrical and Electromagnetic Telecommunication Technologies
Explore the evolution of electrical and electromagnetic telecommunication technologies such as the telegraph, telephone, teleprinter, networks, radio, microwave transmission, fiber optics, communications satellites, and the Internet. Learn about the innovation and development of telecommunication de
0 views • 11 slides
Importance of Telephone Etiquette in Business Communication
Telephone etiquette is crucial in business communication as it reflects professionalism, creates a positive impression, builds loyalty and trust, and ensures customer satisfaction. Proper telephone manners demonstrate respect, enhance the customer experience, and contribute to a lasting positive imp
0 views • 17 slides
Mastering Telephone Consultations: Tips and Key Skills for Effective Remote Communication
Explore the world of telephone consultations with insights on benefits, pitfalls, and essential skills. Discover strategies for successful remote communication, understanding patient needs, and ensuring confidentiality. Enhance your ability to connect, explain clearly, and problem-solve in various s
0 views • 20 slides
Enhancing Telephone Skills for Insurance and Financial Services Professionals
Improve your communication abilities over the phone with insights on key skills, communication dynamics, and strategies for confident interactions. Explore advantages and disadvantages of telephone and email communication, emphasizing the power of voice for conveying emotions effectively. Learn abou
0 views • 16 slides
Provision, Installation, and Support of PIC Data and Telephone Line Services
Appointment of a qualified service provider for the provision, installation, and support of PIC data and telephone line services for a five-year period. Details include background, evaluation criteria, RFP advertisement, submission guidelines, and minimum requirements for bidders. The evaluation pro
0 views • 10 slides
Telecommunication Services Overview: Telephone Services in South Africa
This content provides an overview of telephone services in South Africa, focusing on Telkom as a key provider. It covers different aspects such as cellular phones, their functions, features, advantages, and cell phone etiquette. The information highlights how telephone services play a crucial role i
0 views • 45 slides
Exploration of Race and Identity in Telephone Conversation
The poem "Telephone Conversation" by Wole Soyinka delves into the themes of race, identity, and societal prejudices through a phone dialogue between a man and a landlady. The man's experience of discrimination based on his skin color unfolds in a conversation filled with subtle and overt racism, hig
0 views • 10 slides
Care Concierge: Supporting You Through Later Life Care Journey
Care Concierge provides confidential telephone guidance to help you find the right care for your loved one in later life. From creating tailored care plans to exploring funding options, our experts offer comprehensive support under one roof. Employees can access this service for emotional and practi
1 views • 7 slides
EventsHQ Virtual Event Registration: User Access and Setup Guide
This comprehensive guide provides step-by-step instructions on setting up virtual event registration using EventsHQ. It covers how users can access event details, join the event, and includes best practices for sharing access links. Learn how to utilize the Virtual Event Details feature, send remind
1 views • 19 slides
Impact of Streamlined HIV Care on Economic Burden among Infected Adults
Streamlined HIV care models aim to reduce the economic burden faced by HIV-infected adults by minimizing healthcare costs and improving access to care. The SEARCH trial in Kenya and Uganda implemented population-based testing and supported linkage to antiretroviral therapy (ART) regardless of CD4 co
2 views • 22 slides
Accessible Voting System for Californians with Disabilities
Learn about the Remote Accessible Vote-by-Mail System in California, designed to empower voters with disabilities to securely access, mark, and return their ballots from any computer with internet access. Find out who is eligible to use the system, how to access and return the ballot, and the steps
0 views • 23 slides
Dell Networking Solutions for BYOD and Guest Access Projects
Dell offers end-to-end solutions for Bring-Your-Own-Device (BYOD) and guest access projects, enabling secure employee access and controlled connectivity for visitors. The framework includes mobility business models, device security, network protection, and scalability. Dell supports customers in imp
0 views • 11 slides
Open Access at Charles University: Opportunities and Challenges
Charles University is navigating the landscape of open access following the implementation of the Czech National Open Access Strategy. The university is working towards making all research articles and proceeding papers open access, monitoring article processing charges, and promoting open access as
0 views • 24 slides
The Evolution of the Telephone: From First Invention to Modern Communication
In the mid-19th century, the first phone was invented by a German teacher named Philip Reys in 1861, followed by the famous Scottish scientist Alexander Graham Bell who patented his device. Over time, telephones underwent significant improvements, introducing features like call chains and dual tubes
0 views • 4 slides
Understanding Ethernet and Multiple Access Protocols in Computer Networks
Exploring the fundamentals of Ethernet and multiple access protocols in computer networks, this content discusses the two primary categories of multiple access protocols - contention access and controlled access. It delves into topics such as CSMA/CD, LANs, performance of multiple access schemes, ad
0 views • 7 slides
Challenges in RDD Telephone Surveys for Young Adults: Item Nonresponse and Coverage Implications
This research study conducted in Quebec, Canada, in 2011 focused on the challenges faced in RDD telephone surveys, specifically targeting young adults. It discussed issues such as decreasing coverage due to wireless-only households, nonresponse rates, and the impact of emerging trends on survey meth
0 views • 20 slides
Harvard Chan School 2021 Yearly Access Review Process
The Harvard Chan School conducts its annual Yearly Access Review (YAR) process to review user access to various financial systems. The process involves assessing permissions, levels of access, and organizational details for each team member. Instructions are provided on reviewing worksheets, adding
0 views • 19 slides
Understanding Security Access in PeopleSoft Finance
Explore the various levels of security access in PeopleSoft Finance, from basic entry access to transaction entry, approvals, and procurement processes. Learn how to request individual and department security access and find relevant forms on the financial services website. Discover the different ty
0 views • 11 slides
Immediate Jeopardy Control Panel Access
Quickly navigate your control panel, access audio features, and think like a surveyor with the immediate jeopardy function integrated into the system. Utilize audio PIN for telephone access and adapt panel visibility to suit your needs.
0 views • 149 slides
Comprehensive Rehabilitation Services for Cancer Late Effects and Brachial Plexus Injuries
The complex cancer late effects rehabilitation service (CCLERS) and breast radiation injury rehabilitation service (BRIRS) offer specialized care for individuals experiencing chronic pain, reduced limb function, and psychological distress following cancer treatment. BRIRS provides support for brachi
0 views • 11 slides
Workplace English Conversations Staff Training Session Overview
This training session covers basic telephone etiquette, including answering calls, transferring calls, putting calls on hold, giving negative information, and ending calls. Participants will engage in practical exercises and watch instructional videos to enhance their communication skills. Additiona
0 views • 16 slides
E-R Diagram and Normalization Analysis for Online Telephone Sales System
This content provides detailed information on the creation of an information system for tracking orders in an online telephone sales company. It includes system requirements, entity identification, attribute listing, relationship identification, and normalization analysis for second and third normal
0 views • 10 slides
Befrienders Highland: Combating Isolation for Mental Health in Highland & Argyll
Befrienders Highland offers vital support services to individuals with mental health challenges in Highland and Argyll. Established in 1993, they provide companionship through face-to-face, distance, and telephone befriending. Notably, their Distance Befriending program has proven successful in enha
0 views • 14 slides
Understanding Transit Survey Methods for Data Collection
Explore the various types of surveys used in transit systems, including longitudinal, cross-sectional, and single-point surveys. Learn about different survey modes such as on-board/intercept, telephone, mail, web-based, and smartphones. Understand the advantages and limitations of each survey method
0 views • 32 slides