Effective Management of CDIS User Passwords and Account Lockouts
To ensure security in Child Development Information System (CDIS), it is crucial to regularly change passwords and handle account lockouts efficiently. This guide offers detailed steps for changing passwords, addressing locked accounts, and setting up local support messages. By following these proce
0 views • 19 slides
Secure Your Bet A Guide to Safe Online Casino Practices in Singapore
Football fans in Singapore are well aware of Singapore Pools, the official betting platform offering Singapore pools odds and fixtures for various matches. But with the rise of online casinos, the thrill of the game extends beyond the local pitch. While convenient, venturing into the online casino w
4 views • 4 slides
Get a Customised USB to Make Your Brand Look Stylish
At Wholesale USB, we understand the importance of data security and personalised solutions in today\u2019s fast-paced world. \n\nThat\u2019s why our customised USB flash drives, including the cutting-edge USB card with built-in 128-bit encryption software, are designed to ensure your important data
3 views • 5 slides
Digital Wellness and Password Security Lesson for Students
This lesson focuses on promoting digital wellness and teaching students about password security. It covers topics such as creating strong passwords, safeguarding personal information, and the importance of balancing online and offline interactions. Through activities and discussions, students learn
0 views • 13 slides
Guide to MySQL Operations on Turing Server
This guide provides step-by-step instructions on working with MySQL on Turing server at turing.csce.uark.edu. It includes logging in via SSH, connecting to the server, changing MySQL passwords, and performing operations on tables. Learn how to create tables, change passwords, and more with detailed
2 views • 21 slides
Comprehensive Guide to Setting Up Security Questions and Answers for Self-Service Accounts
This manual provides step-by-step instructions on setting up security questions and answers for self-service accounts, enabling users to easily reset passwords and enhance account security. The process includes logging in, selecting security questions, entering answers, and retrieving forgotten pass
0 views • 14 slides
Cybersecurity Best Practices for Password Protection and Incident Response
Enhance your cybersecurity knowledge with insights on password management, cybercriminal tactics, creating strong passwords, and password complexity. Learn how to safeguard your data and prevent cyber threats by implementing strong password rules, multi-factor authentication, and incident response s
2 views • 24 slides
Understanding Device Settings and Strong Passwords for Digital Citizenship
This lesson focuses on understanding device settings and the importance of creating strong passwords for digital citizenship. It covers topics such as changing backgrounds, locking screens, creating strong passwords, common password mistakes to avoid, and tips for password safety. The lesson also in
1 views • 11 slides
Protect Your Digital Identity: Cyber Hygiene Best Practices
Cyber hygiene involves following best practices to safeguard personal data in the digital realm. With the increasing value of personal data and evolving technology, individuals must take proactive steps such as using reputable antivirus software, network firewalls, updating software regularly, using
0 views • 25 slides
Understanding Strong and Weak Forms in English Pronunciation
Exploring the concept of strong and weak forms in English pronunciation, this content discusses the importance of using weak forms in speech, the rules of occurrence of strong forms, and how to recognize the position of weak forms. Examples and explanations illustrate how function words are weakened
1 views • 25 slides
Strengthen Your Digital Literacy with Strong Password Strategies
Enhance your digital literacy by learning about the importance of strong passwords, strategies for creating secure passwords, and the role of password managers. Explore various resources, videos, and tools to improve your password security and protect your online accounts effectively.
0 views • 5 slides
Promote Feature Adoption with Self-Service Password Reset Posters
Enhance feature adoption of self-service password reset among your employees with these ready-to-use posters. Simply customize and print them to encourage password security awareness in your workplace. Don't risk productivity downtime due to forgotten passwords – empower your team to reset their p
0 views • 13 slides
Importance of Secure Passwords in Internet Safety
Passwords play a crucial role in protecting personal information online. Using easily guessable passwords like '123456' poses a significant risk. It's essential to choose complex and secure passwords to safeguard your identity and information from cyber threats. This includes using a combination of
0 views • 6 slides
Online Safety Guidelines and Best Practices
Learn how to stay safe online by following rules for online etiquette, using and creating passwords wisely, understanding the importance of VPNs, ensuring safety on platforms like Discord and online games, creating secure passwords, keeping personal information private, handling inappropriate messag
0 views • 13 slides
Strong vocational interest blank
Strong Vocational Interest Blank, introduced in 1927 by Edward Kellog Strong Jr., assesses individuals' career preferences based on their likes and dislikes across various dimensions. The Strong-Campbell Interest Inventory, a revised version, includes 124 occupational scales and 23 Basic Interest Sc
0 views • 12 slides
Developing Strong Belief and Trust in Allah for Success in Life
Explore the teachings of Prophet Muhammad in Hadith, emphasizing the importance of strong faith and trust in Allah. Learn how to become a strong believer, seek forgiveness, and put trust in Allah for guidance and success. Encourage charity, constant learning, and good behavior to strengthen your rel
0 views • 11 slides
Tamper-Evident Pairing (TEP) Protocol for Secure Wireless Pairing Without Passwords
This article discusses the challenges of traditional secure wireless pairing methods that rely on password validation and proposes the Tamper-Evident Pairing (TEP) protocol as a secure in-band solution to protect against Man-in-the-Middle (MITM) attacks. TEP eliminates the need for out-of-band chann
1 views • 40 slides
The Vital Role of Encryption in Safeguarding the Digital Economy
Encryption plays a crucial role in protecting the digital economy by providing secure communication channels. Professor Peter Swire from Ohio State University emphasizes the need for strong encryption over weak cybersecurity measures. He discusses the history of wiretaps, the shift to strong cryptog
0 views • 15 slides
Start Strong Fall 2022 Administration District Test Coordinator Training
Delve into the comprehensive training agenda for the Start Strong Fall 2022 Administration, focusing on key aspects such as testing requirements, technology setup, reporting groups, accessibility features, and more. Understand the differences between Start Strong and NJSLA assessments, key dates, an
0 views • 58 slides
Essential Information for New Student Orientation at Brunswick Community College
New student orientation at Brunswick Community College provides important details on technology access, user IDs and passwords, Dolphin Alert notifications, and access to courses via Moodle. Students are guided on setting, resetting, and managing passwords, registering for Dolphin Alert notification
0 views • 10 slides
Strong List Coloring and the Polynomial Method in Graph Theory
Exploring the Polynomial Method in the context of Strong List Coloring, Group Connectivity, and Algebraic tools. This method involves proper coloring of graphs based on polynomial assignments, highlighting the significance of Strong Choosability and the Co-graphic case. The applications and proofs a
0 views • 34 slides
Effective Strategies for Creating Strong and Memorable Passwords
Enhance your online security by understanding the importance of strong passwords and learn various techniques to create secure yet easy-to-remember passwords. From guidelines to online tools, explore methods like Bruce Schneier's sentence-based approach and the PAO method for better password managem
0 views • 8 slides
Mastering Strong Passwords: A Practical Guide
Understanding how passwords work is crucial for online security. Passwords act like combination locks, preventing unauthorized access to your accounts. Creating a strong password involves using random words and characters, as well as combining three random words for added security. Learn how to craf
0 views • 5 slides
Interactive Password Security Activity for Children
This presentation recaps the importance of strong passwords, techniques for creating them, and the significance of two-factor authentication. The lesson notes guide discussions on creating secure passwords using the "three random words" method and avoiding personal details. The interactive game "Gue
0 views • 4 slides
Understanding Strong and Weak Links in Team Talent Distributions
Talent distributions within sports teams can vary greatly, affecting team performance. The concepts of strong and weak links in team dynamics are explored through examples in hockey, shedding light on how having the best player or avoiding the worst player can impact outcomes. The correlation betwee
0 views • 13 slides
Understanding Strong Consistency and CAP Theorem in Distributed Systems
Strong consistency and the CAP theorem play a crucial role in the design and implementation of distributed systems. This content explores different consistency models such as 2PC, consensus, eventual consistency, Paxos, and Raft, highlighting the importance of maintaining ordering and fault-toleranc
0 views • 29 slides
Understanding Strong Consistency and CAP Theorem
Explore the concepts of strong consistency, CAP theorem, and various consistency models such as 2PC, consensus, eventual consistency, Paxos, Raft, and Dynamo. Learn about fault-tolerance, durability, and the importance of correct consistency models in distributed systems. Understand how Paxos and Ra
0 views • 29 slides
Best Practices for Protecting Sensitive Data
Learn about password and credit card data security, storing passwords securely, data in transit vs. data at rest, and the importance of using salts to protect password hashes from offline attacks. Discover how to securely store passwords using encryption, hashing, and more to minimize exposure of se
0 views • 30 slides
Understanding Cybercrime: Types, Signs, and Prevention
Cybercrime involves various criminal activities targeting computers and networks, aiming to generate profit or cause harm. Types include website spoofing, ransomware, malware, IoT hacking, identity theft, and online scams. Signs of identity theft can manifest in credit, tax, child, medical, and crim
0 views • 6 slides
Windows Security Overview and Best Practices
Windows operating system security overview focusing on preventing unauthorized access, privilege escalation, and password vulnerabilities. Includes countermeasures such as setting proper permissions, implementing strong passwords, and detecting vulnerabilities. Covering topics like remote password g
0 views • 6 slides
Essential Tips for Computer Security
Protecting your computer is crucial in today's digital world. Follow these steps to enhance your computer's security: 1. Utilize a firewall to block hackers. 2. Install and update anti-malware software. 3. Create strong, unique passwords. By implementing these measures, you can safeguard your system
0 views • 4 slides
Enhancing Mobile PIN Security Using Passwords
Explore the integration of passwords to enhance mobile PIN security, addressing challenges like authentication difficulty, limited battery life, and poor voice quality. Learn about common PIN patterns, love/hate towards PINs, user mapping examples, and opportunities for efficient key derivation and
0 views • 21 slides
Understanding Molar Conductivity of Strong Electrolytes
Strong electrolytes are materials highly dissociated in water, leading to conducting solutions with high molar conductivity. This article delves into the concept, calculation methods, and experimental procedures for determining the molar conductivity of strong electrolytes using examples of NaCl, KC
0 views • 5 slides
Understanding Acids and Bases in Chemistry: Key Concepts and Terminology
This chapter delves into the fundamental concepts of acids and bases in chemistry, covering Arrhenius, Bronsted-Lowry, and Lewis definitions. It discusses conjugate acids and bases, acid dissociation, dissociation of strong and weak acids, and the differences between strong and weak acids/bases. The
0 views • 41 slides
Strong Workforce Program Task Force Membership Overview
Strong Workforce Program Task Force is comprised of diverse members from various educational and workforce development backgrounds. The Task Force plays a vital role in steering the program's initiatives and ensuring a strong focus on workforce development, innovation, and student support services a
0 views • 14 slides
Best Practices for Password Security and User Authentication
Password security is crucial for protecting sensitive information. Passwords should not be shared and should be changed regularly to prevent unauthorized access. Implementing strong passwords, two-factor authentication, and biometric security measures can greatly enhance security. Additionally, main
0 views • 16 slides
Enhancing Wi-Fi Security with User-Friendly WPA3 Passwords
Proposal to enhance Wi-Fi security by incorporating password and password identifier hashes in the SAE commit exchange, enabling devices to hint to access points which password will be used. This approach aims to improve network efficiency and user experience while addressing privacy concerns associ
0 views • 8 slides
Secure Email Practices and Guidelines for SWOSU Accounts
Enhance your online security with these guidelines for managing your SWOSU email accounts effectively. Learn how to create strong passwords, avoid potential security risks, and protect your personal information from phishing scams. Take proactive steps to safeguard your digital communications and ma
0 views • 13 slides
Login Instructions for Coresuite, The Portal, THEREFORE, and PET
Detailed instructions on how to login to Coresuite, The Portal, THEREFORE, and PET after September 2nd. Includes information on using different usernames and passwords for MAPFRE accounts, saving login credentials, resetting passwords, and accessing support helpline.
0 views • 8 slides
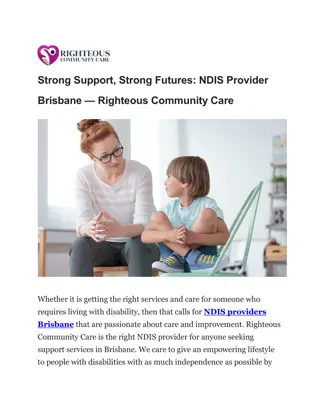
Strong Support, Strong Futures NDIS Provider Brisbane Righteous Community Care
Strong Support, Strong Futures NDIS Provider Brisbane Righteous Community Care
0 views • 6 slides