Enhancing Mobile PIN Security Using Passwords
Explore the integration of passwords to enhance mobile PIN security, addressing challenges like authentication difficulty, limited battery life, and poor voice quality. Learn about common PIN patterns, love/hate towards PINs, user mapping examples, and opportunities for efficient key derivation and storage techniques.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
Bootstrapping Mobile PINs Using Passwords Markus Jakobsson Debin Liu Information Risk Management PayPal
A Bit about Authentication Difficulty authenticating Small screen size Lack of coverage Short battery life 1 2 3 4 5 Slow Web connection Difficulty customizing settings Poor voice quality 2
Commercial Four-Letter Word Friction
A Bit About Human Memory Not so amazing
Common PIN Your spouse s birthday
Love/Hate PINs
Example User Mapping Blu2thRules 2582
Opportunistic Derivation Access; Truncate; Map; Store
Special Characters ~1.5% Can be reduced
Special Phones Need numeric pad
Strong password, weak PIN 1234Brew$g , 1begHELP
Password change? Dual Universes
Measuring Security Raided Dropboxes
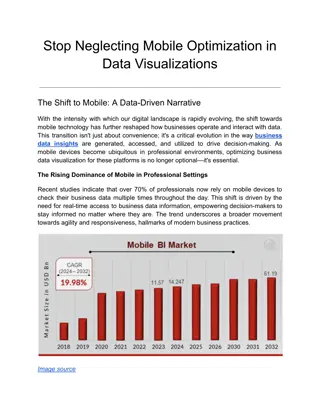
Entropy of Derived PINs 14 pwd4 Entropy PIN Entropy Information Loss by Mapping 12 12 10.9 10.5 10 Information Entropies 9.7 10 9.2 8 6 4 2 1.1 0.5 0.5 0 FSP (8359) SNP (2873) Data Sources (Size) Malware (16192)
Special Characters Percentage of Passwords using Upper Case Letters 35.00% 32.16% 30.00% 26.96% Percentage of Passwords using Special Characters 25.00% Percentage 20.00% 15.00% 11.14% 10.00% 6.16% 5.00% 1.95% 1.44% 0.00% FSP (8359) SNP (2873) Data Sources (Size) Malware (16192)
Imagine PIN Theft 20 18 16 14 12 10 8 6 4 2 0 Password Entropy Entropy of Derived PINs Conditional Password Entropy
Experiment What is Joe s PIN? Joe uses a PIN to access his PayPal account from his phone. But he does not want to have to remember another number, and he does not want to reuse his banking PIN. So he uses PayPal s new password to PIN feature so that he only has to remember his password. Joe s password is Blu2thrules . Look at the screen-shot below and let us know what PIN he should enter.
Usability of Derived PINs 25-subject Qualitative study Successful but Slow 24% Successful and Fast 64% Failed 12%
Usability of Derived PINs 100-subject Quantitative study Likely Successful 22% Failed 10% Successful 68%
Other things I pitch Address web/app spoofing: www.SpoofKiller.com Mobile-friendly passwords: www.fastword.me Mobile malware detection: www.fatskunk.com Etc: www.markus-jakobsson.com