Understanding the Evolution of Thin Clients
Explore the evolution and characteristics of thin clients, from their inception as interfaces for mainframe computers to modern ultra-thin clients with enhanced security and cost-effectiveness. Learn about the benefits, such as reduced energy consumption and improved manageability, as well as the tr
4 views • 35 slides
Introduction to Linux Command Line
The significance of the command line interface in computing, understand why it is preferred for efficient file management, and discover Linux as an alternative operating system widely utilized on servers and supercomputers. Learn how to access a Linux server via SSH for practical application.
1 views • 14 slides
Occupational Therapy and Mental Health: Supporting Clients' Return to Work
Explore the role of occupational therapists in supporting clients with mental health concerns to return to work. Understand the concept of occupational therapy, common assessments and interventions used in mental health OT, and how OTs help clients increase independent function. Discover what OTs do
1 views • 25 slides
Caterpillar Cat D7E TRACK-TYPE TRACTOR (Prefix SSH) Service Repair Manual Instant Download
Please open the website below to get the complete manual\n\n\/\/
0 views • 30 slides
Guide to MySQL Operations on Turing Server
This guide provides step-by-step instructions on working with MySQL on Turing server at turing.csce.uark.edu. It includes logging in via SSH, connecting to the server, changing MySQL passwords, and performing operations on tables. Learn how to create tables, change passwords, and more with detailed
2 views • 21 slides
Introduction to Unix-like Systems and Shell Interaction
Unix-like systems, such as Linux, Android, iOS, and macOS, are prevalent in various devices. The Unix shell acts as an intermediary between users and the operating system, allowing for program execution and process management. Secure Shell (SSH) and X Window System enable remote machine connections
4 views • 19 slides
Understanding Narrative Therapy with Latinos
Narrative therapy, developed by White and Epston in the 1980s, focuses on empowering clients by reshaping their stories. This approach emphasizes clients' perspectives and meanings, facilitating growth, and transforming narratives to uncover new possibilities. The therapist engages in deconstructing
1 views • 11 slides
Tutorial: Installing Hadoop 3.3 on Windows 10 and Setting Up Linux Subsystem
Learn how to install Hadoop 3.3 on Windows 10 by enabling Windows Subsystem for Linux, downloading and configuring Java 8, downloading Hadoop, unzipping Hadoop binary, configuring SSH, and setting up Hadoop on your system.
1 views • 17 slides
SHS Client Satisfaction Survey Results 2020 - Overview and Insights
The SHS Client Satisfaction Survey 2020 gathered feedback from clients in NSW regarding their demographics, reasons for seeking support, current situations, accommodations, and satisfaction with services. The survey revealed insights such as high overall satisfaction rates with services and accommod
0 views • 14 slides
Understanding Linux Services and Internals
Explore the components of a Linux system, including hardware controllers, the Linux kernel, operating system services, user applications, directory structure, shells, and essential Linux services. Learn how to list services in Linux by connecting via SSH and accessing them as a root user to manage c
1 views • 14 slides
Evolution of Cryptography: From Ancient Techniques to Modern Security Mechanisms
Explore the evolution of cryptography from ancient techniques like the Caesar Cipher to modern security mechanisms like SSL, SSH, and IPSec. Learn how cryptography plays a crucial role in ensuring confidentiality, integrity, authentication, non-repudiation, and availability in network security. Disc
1 views • 62 slides
Understanding Scanning in Thin Clients, RDP, and Citrix Environments
Learn about the difference between Fat Clients and Thin Clients, various types of Thin Clients, reasons for using Thin Clients, how programs are accessed on servers, and issues with scanning in RDP connections in this informative guide. Discover why Thin Clients are preferred for centralized softwar
1 views • 16 slides
Legal Rights and Options for Regional Center Clients in California
This document discusses the legal rights and options available for adult regional center clients in California, focusing on clarifying their rights, reviewing support systems, exploring alternatives to conservatorship, and explaining the conservatorship process. It also covers children's and adults'
1 views • 35 slides
Understanding Counsellor-Centered Counselling Approach
Counsellor-Centered Counselling, advocated by Dr. Nadeem Khan, focuses on the counselor taking a prominent role in guiding clients to replace emotional behavior with rational solutions. The approach, led by counselors like Williamson, is beneficial for educational and vocational issues by providing
0 views • 15 slides
Introduction to Linux System Administration
Explore the essentials of Linux system administration in this course material. Learn how to access Linux servers and virtual machines, utilize SSH for secure connections, and configure Kali Linux VM settings for efficient usage. Gain hands-on experience with graphical and command-line interfaces to
0 views • 45 slides
Understanding SFTP Server Functionality with ACS 5.x by Mohammad Azharuddin AAA Team
SFTP (SSH File Transfer Protocol) is a secure network protocol for file access, transfer, and management over reliable data streams. It enhances security by extending the SSH protocol and can be implemented using a reliable 8-bit byte stream protocol. SFTP commands are sent as 4 ASCII letters follow
4 views • 23 slides
Comprehensive Remote Access Guide for Secure Resource Access Portal
This detailed guide provides step-by-step instructions for setting up remote access to SSH, RDP, web applications, and databases via secure authentication processes. It covers prerequisites, initial login setup with 2FA, and connecting to various resources securely. Follow the guide to ensure a smoo
0 views • 12 slides
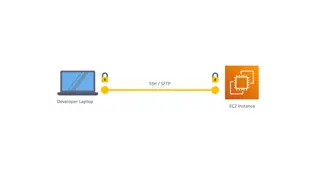
Development Process Using SSH, SFTP, EC2 Instances, and Autoscaling Groups
Exploring the development workflow involving SSH, SFTP, EC2 instances, and Autoscaling Groups for code merging, building, and releasing applications in the cloud environment using technologies like Amazon Elastic Container Service (ECS). The images provide insights into setting up developer laptops,
0 views • 5 slides
Comprehensive Overview of Git and GitHub for CS 4411 Spring 2020
This detailed content provides an in-depth exploration of Git and GitHub for the CS 4411 Spring 2020 semester. It covers Git basics, commands, dealing with conflicts and merges, understanding branches, recovering from errors, making commits, utilizing remote repositories, and collaborating via GitHu
0 views • 40 slides
Effective Sector Development Strategies for Client Intervention Programs
This webinar series delves into recording sector development activities, understanding the Data Exchange tool, and effectively managing cases, sessions, and clients for targeted intervention programs. Learn how to differentiate between individual clients and unidentified group clients, and optimize
0 views • 20 slides
Practical Techniques for Managing Fatigue in Clients with Neurological Conditions
This session by Dr. Nina McLoughlin, a Senior Clinical Psychologist/Neuropsychologist, focuses on practical fatigue management techniques for clients with brain injuries, strokes, and other neurological conditions. Emphasizing the importance of addressing sleep as the primary intervention point, the
0 views • 33 slides
Comprehensive Financial Solutions for Mortgage Protection, Life, Disability, and Retirement
Dedicated to providing mortgage protection, life insurance, disability coverage, and retirement solutions to clients, Chris Cook, a seasoned professional with a passion for assisting families, represents reputable companies like Mutual of Omaha and Americo. By understanding clients' needs and offeri
0 views • 11 slides
Best Practices for Securing Linux Systems
This resource covers essential security practices for Linux systems, including the CIA Triad (Confidentiality, Integrity, Availability), recommended partitions, encryption at rest and in transit, SSH and user login configurations, and password best practices. Learn about securing user directories, p
0 views • 27 slides
Introduction to Linux System Administration
Explore the fundamentals of Linux system administration, including accessing Linux systems, using SSH for secure connections, setting up virtual machines, understanding the Unix system kernel and shell, and grasping the multi-user and multi-process aspects of Unix. Enhance your skills in managing Li
0 views • 42 slides
Understanding Limited Scope Representation and Unbundling in Legal Practice
Limited Scope Representation, also known as unbundling, is an ethical and safe practice that allows lawyers to provide specific legal services to clients rather than full representation. It helps address issues of affordability and ensures clients receive the legal assistance they need for their cas
0 views • 19 slides
Understanding Façade Design Pattern in Structural Design Patterns
Façade design pattern simplifies the interface of a complex system by providing a unified and straightforward interface for clients to access the system's functionalities. It helps in isolating the clients from the complexities of underlying components, offering a more user-friendly experience. The
0 views • 48 slides
Analysis of Top 10,000 Clients' Social Sector Costs Presentation
Foundational work in the social sector focusing on shared clients and costs incurred from 1994 to 2014. The data reveals that each of the top 10,000 clients had costs of at least $400,000, with 920 clients surpassing $1 million. Health costs, particularly in disability services and mental health, ar
0 views • 13 slides
Evidence Gathering and Client Support Strategies in Clinics
This content delves into the importance of gathering evidence on how clients find out about clinics, the routes they take to reach the clinic, existing support or information sources, and the time taken for clients to receive help. It also explores evidence on when people seek help from the clinic,
0 views • 7 slides
Understanding Unix: Fundamentals and Connections
Explore the basics of Unix operating systems, terminology, types of Linux installations, and connecting to remote Linux machines. Learn about key concepts such as local vs. remote connections, SSH connections using passwords and keys, and tools like PuTTY for remote access.
0 views • 78 slides
Internal Dispute Resolution - Helping Clients Navigate Debt Issues
Explore the process of internal dispute resolution (IDR) to assist clients in resolving problem debts efficiently. Learn how to identify, gather information, determine issues, assess urgency, and negotiate resolutions. Discover the importance of IDR, its benefits, and who offers IDR procedures. Gain
0 views • 71 slides
Understanding Client-Server Computing in Distributed Systems
Client-server interaction forms the foundation of distributed computing, where clients rely on servers to perform operations. Clients can be various applications like browsers, email clients, and office software, while servers manage network resources and serve specific functions such as file storag
0 views • 17 slides
Understanding File Transfer Protocols: FTP, SSH, SFTP, and Email Systems
This content delves into the intricacies of file transfer protocols such as FTP, SSH, and SFTP, along with components of email systems. It explains how FTP works, its security implications, and the evolution towards more secure protocols like SFTP. Additionally, it provides insights into FTP impleme
0 views • 40 slides
Understanding Client/Server Computing Architecture
Client/Server Computing architecture separates clients and servers over a network, allowing for file sharing, resource allocation, and service requests. Clients initiate services from servers, with transparent server locations and message-passing transactions. Systems with C/S architecture include f
0 views • 18 slides
Strategies for Finding and Keeping Clients in Business
Discover effective strategies to attract and retain clients in your business. Learn how to package, price, and promote your services to optimize your schedule and revenue. Understand the importance of targeting specific client groups and pricing your services appropriately to position yourself in th
0 views • 24 slides
Understanding the Key Dimensions of SSH Research Societal Impact
Exploring pathways to societal impact through SSH research, this presentation delves into the mechanisms and processes that lead to impactful interactions with society. It challenges the focus on physical outputs and emphasizes the importance of studying the ways in which SSH researchers engage with
0 views • 20 slides
Understanding Limited Legal Services for Access to Justice
Limited legal services involve providing clients with specific legal assistance rather than handling all aspects of a case. This approach aims to make legal services more affordable and accessible, particularly for low- and middle-income individuals. By unbundling services, clients can choose and pa
0 views • 29 slides
Customizable CRM Scheduler with Appointment Calendar for Clients
Implement a customizable CRM scheduler with a user-friendly appointment calendar for clients and customers. Allow easy scheduling, cost estimates, demographic data collection, and communication features. Enhance the scheduler with new event types, break time configuration, appointment types, and not
0 views • 9 slides
Setting Up Ignite-UX Server and Client with NFSv4 and SSH Tunnel on HP-UX 11iv3
Learn how to configure an Ignite-UX server and client on HP-UX 11iv3 using NFSv4 with an SSH tunnel for a secure environment. This presentation covers the setup process, equipment requirements, and the benefits of using NFSv4 in disaster recovery scenarios.
0 views • 28 slides
Understanding Electron-Phonon Interaction and Peierls Instability in Polyacetylene using SSH Model
Explore the concepts of electron-phonon interaction, Peierls instability, and the SSH model in the context of Polyacetylene. Dive into the Born-Oppenheimer approximation, electron band properties, and density of states, unraveling the fascinating world of molecular dynamics and energy calculations.
0 views • 16 slides
Introduction to UNIX System and Homework Assignment in CS 240
Learn about connecting to the CS department's UNIX system, setting up accounts, using SSH clients on Windows, Mac, and Linux, navigating the filesystem, and performing commands in the command line interface. Get started with your CS 240 assignments effectively.
0 views • 19 slides