Addressing 5G Signaling Protocol Vulnerabilities
The 8th meeting of the Communications Security, Reliability, and Interoperability Council to discuss and address security vulnerabilities in the newly adopted 5G signaling protocol, HTTP/2. Learn about potential risks, recommended safeguards, and the prevention of these vulnerabilities in the upcomi
3 views • 85 slides
Functional Programming
Functional programming, a paradigm that emphasizes declarative programming, pure functions, and limited side effects. Explore the benefits and characteristics of functional programming languages.
0 views • 20 slides
Understanding Vulnerabilities of Individuals with Autism in Disciplinary Hearings and Employment Tribunals
People with autism may face vulnerabilities in disciplinary proceedings and employment tribunals due to impaired theory of mind, communication difficulties, insistence on sameness, stereotyped behaviors, and sensory sensitivities. These challenges can lead to misunderstandings, difficulties in copin
0 views • 10 slides
Decision Analysis and Operations Research in Management
This content delves into Management Decision Analysis and Operations Research techniques such as Linear Programming, Integer Linear Programming, Dynamic Programming, Nonlinear Programming, and Network Programming. It covers the phases of an Operations Research study, mathematical modeling for decisi
0 views • 36 slides
Module 2: PSEA and Safe Programming Training of Trainers (ToT) by CRS HRD
This Module 2 focuses on PSEA and Safe Programming, covering key sessions on understanding safe programming, identifying protection and SEA risks, and mitigating risks. It emphasizes the importance of safe programming in increasing safety, dignity, and access, with staff playing a crucial role. Part
2 views • 19 slides
Understanding Computer Programming: Basics and Beyond
In this chapter, we delve into the fundamental concepts of computer programming. We explore the definition of a program, the role of programming languages, types of programming languages, and generations of programming languages. Additionally, an assignment is provided to reinforce the key learnings
0 views • 25 slides
Understanding Object-Oriented Programming (OOP) in Python
Python is a versatile programming language that supports various programming approaches. Object-Oriented Programming (OOP) is a popular method in Python where objects are created to solve programming problems. OOP in Python focuses on creating reusable code, following the principle of DRY (Don't Rep
1 views • 35 slides
Introduction to Computers and C++ Programming Lecture 1 - Overview and Basics
This lecture covers the fundamental concepts in computer systems and programming using C++. Topics include the main components of a computer, bytes and addresses in memory, computer systems hardware and software, understanding programs, programming languages, compilers, preparing and running C++ pro
1 views • 21 slides
Understanding Buffer Overflow Vulnerabilities in Programming
Buffer overflow vulnerabilities pose serious security threats by allowing attackers to execute arbitrary code on victim machines. This issue arises from overwriting memory in a way that manipulates the program's behavior. Learn about the dangers of buffer overflow bugs, how they can be exploited, an
2 views • 33 slides
Software Security Principles and Practices: Enhancing Program Code Security
Understanding and addressing critical web application security flaws like unvalidated input, cross-site scripting, buffer overflow, injection flaws, and improper error handling is crucial in enhancing the security of program code. The NIST report NISTIR 8151 provides valuable recommendations to redu
2 views • 44 slides
Web Application Development and Programming CTE Program Overview
Viera High School offers a comprehensive CTE program in Web Application Development and Programming, taught by Mr. Dohmen. Students learn popular programming languages like Python, SQL, JavaScript, Java, C#, and C. The courses cover web programming, JavaScripting, and PHP programming, providing cert
1 views • 7 slides
Understanding Computer Security and Software Vulnerabilities
Computer security, also known as cybersecurity or IT security, encompasses the protection of information systems from theft and damage. This overview delves into software security, control-flow attacks, memory vulnerabilities, and the historical impact of events like the Morris Worm. Various aspects
0 views • 53 slides
Overview of Global Farmed Salmon and Organic Production
The data showcases the production figures for global farmed salmon across various countries, with Norway leading the production, followed by Chile, Scotland, and others. Additionally, insights into the growing organic salmon production, vulnerabilities in the sector, and details on organic mussels p
0 views • 9 slides
Introduction to Programming with RobotC in Robotics Education
Programming in robotics involves giving specific directions to a robot using software like RobotC. This introduction covers the basics of programming, software organization, and how to get started with RobotC through creating flow charts and programming tasks. Learn about setting up RobotC, creating
0 views • 8 slides
Introduction to Programming and Computer Instructions
Programming is the process of creating instructions for computers to follow and accomplish tasks. It involves turning human language instructions into detailed binary machine language. Before learning programming, individuals may have different levels of experience, ranging from no experience to pro
0 views • 16 slides
Analysis of file:// Vulnerabilities in Android Browser Apps
The study delves into file:// vulnerabilities in Android browser apps, uncovering risks posed by the file:// URI scheme. It highlights how file:// requests can breach app data isolation, potentially compromising sensitive files. The research presents a unified attack model, FileCross automated testi
0 views • 22 slides
Development of Attosecond Theory for Nobel Prize through Verilog Programming
Attosecond generation is a crucial technique for creating attosecond pulses by manipulating radiation waves. This research paper focuses on developing the Attosecond generation equation through Verilog programming and validating it using test programming techniques. The interface between equations,
0 views • 15 slides
Automated Detection of SSL Vulnerabilities in Applications
This research introduces SSLint, a systematic approach and automated tool for detecting incorrect SSL API usage vulnerabilities in applications. By analyzing millions of lines of code, the tool discovered previously unknown SSL/TLS vulnerable apps. The study addresses the motivation, problem stateme
0 views • 29 slides
Server-Side Technologies and Security Vulnerabilities in Mobile Services
This content delves into server-side technologies such as SQL, SOAP, JSON, and ReST used in mobile services, highlighting vulnerabilities that expose sensitive data. It emphasizes the importance of general web service security guidelines and discusses attacks against XML-based web services, outlinin
0 views • 52 slides
Understanding Blockchain Vulnerabilities to Quantum Attacks
Explore the vulnerabilities of blockchains to quantum attacks and the potential impact of quantum devices on blockchain technologies. Learn about key concepts such as blockchain basics, proof-of-work, quantum computing, quantum computing algorithms, and vulnerabilities like ECDSA and peer-to-peer ne
0 views • 23 slides
Understanding Security Threats and Vulnerabilities in Computer Systems
In computer security, threats exploit vulnerabilities to breach security and cause harm. Vulnerabilities arise from system weaknesses, attacker access, and capability. Threats include spoofing, data tampering, repudiation, information disclosure, denial of service, and elevation of privilege. Catego
0 views • 13 slides
CS252 Systems Programming Course Overview
This course overview covers topics such as C programming review, Unix basics, Unix systems programming, and grading details. The course includes labs on C/C++ programming, Unix shell scripting, and writing your own shell. Communication is emphasized through Piazza for questions/answers and Blackboar
0 views • 41 slides
Introduction to Programming Languages and Functional Programming with OCaml
Welcome to Lecture 1 of CSEP505 on Programming Languages focusing on OCaml and functional programming. Professor Dan Grossman introduces the course, discusses the importance of studying programming languages, and shares insights on course mechanics and content. Topics include staff introductions, co
0 views • 84 slides
Understanding ITM352 and Its Role in MIS
Welcome to ITM352, a course focusing on acquiring basic programming skills in a business context. This course emphasizes hands-on experience in developing relevant software applications, addressing real technology problems, and fostering rapid self-learning of IS/IT technologies. Misconceptions arou
0 views • 36 slides
Understanding the Importance of OWASP Dependency-Check Project
Explore the significance of OWASP Dependency-Check in managing software dependencies and mitigating known vulnerabilities in applications. Learn about the risks associated with using components with vulnerabilities and the challenges of patching programs. Discover how OWASP Dependency-Check provides
1 views • 26 slides
Data Disaggregation Taskforce: Assessment and Recommendations on Vulnerabilities
The Data Disaggregation Taskforce is conducting an assessment of current practices across sectors, assessing 10 sectors/clusters, 15 categories of affected populations, and identifying vulnerabilities in 17 categories. The Taskforce is working on harmonizing categories and finalizing recommendations
0 views • 6 slides
Understanding Spectre and Meltdown Security Vulnerabilities
Spectre and Meltdown are two critical security vulnerabilities that exploit microarchitectural features to gain unauthorized access to memory. These vulnerabilities enable attackers to read memory that should be inaccessible, targeting branch prediction and exception handling mechanisms. Side channe
0 views • 19 slides
Understanding Functional Programming Paradigm
Functional programming emphasizes well-structured software that is easy to write and debug, with reusable modules to reduce future programming costs. It introduces higher-order functions and first-class function values, fostering declarative programming for tasks like symbolic data manipulation and
0 views • 21 slides
Essential Principles of Teaching Programming Languages
Foundational concepts in programming form the core of computing. This encompasses understanding programming fundamentals, teaching language aspects effectively, statistical programming for data analysis, and guiding students unfamiliar with programming environments towards grasping the logic and sim
0 views • 23 slides
Exploring Computer Programming Principles
Dive into the world of computer programming, covering high-level and machine languages, compilers, interpreters, writing programs, top-down design, and the array of programming languages available. Understand the essentials of building code to control computers, the diversity of programming language
0 views • 23 slides
Understanding Cloud Security Threats and Vulnerabilities
Explore the world of cloud security through the eyes of Dr. Liang Zhao, focusing on mobile security, WLAN security, and cloud threats. Learn about threat modeling, mitigating cloud vulnerabilities, and common threats such as data leakage, insecure interfaces, and more. Discover practical threat anal
0 views • 18 slides
Transitioning from Scratch to Python: A Practical Approach for Learning Textual Programming
Explore the transition from visual programming in Scratch to textual programming in Python using Turtle Graphics. Engage in practical exercises, clarify key concepts, and reflect on the challenges and progress in learning core programming concepts. Utilize resources from TeachingLondon Computing to
0 views • 21 slides
Understanding Network Security Vulnerabilities and Attacks
Explore the world of network security vulnerabilities and attacks, including Denial-of-Service (DoS) and Distributed-Denial-of-Service (D-DoS), security flaws in the TCP/IP protocol suite, ICMP attacks, routing attacks, and TCP attacks. Learn about common security vulnerabilities such as address spo
0 views • 36 slides
Understanding Web Application Vulnerabilities in Information Warfare
Web application vulnerabilities such as Cross-Site Scripting, SQL Injection, and Broken Authentication pose significant risks in information warfare. Current solutions include Black-Box Security Testing and XSS Analyzers, but they have limitations like static verification and dependence on security
0 views • 21 slides
Understanding Programming Language Vulnerabilities and ISO/IEC/SC22/WG23
Explore the history and evolution of ISO/IEC/SC22/WG23 focusing on programming language vulnerabilities, led by Stephen Michell. Learn about the formation in 2006, publications, identified vulnerabilities, and the upcoming Edition 3 outlook with language-specific annexes. Discover comparisons with A
0 views • 15 slides
Basic Web Security Model for Secure Electronic Commerce
This presentation covers the basic web security model for secure electronic commerce, focusing on vulnerabilities such as XSS and SQL injection. It discusses the decline in web vulnerabilities since 2009 and explores reported web vulnerabilities. The course theme includes topics like web application
0 views • 38 slides
CS 288-102 Intensive Programming in Linux Spring 2017 Course Details
Learn Linux programming, C language proficiency, Bash scripting, and more in this intensive course taught by Instructor C.F. Yurkoski. The course covers programming in Linux environment, command line interface, C language, client/server programming, and essential programming concepts like pointers,
0 views • 31 slides
Understanding Spectre and Meltdown Security Flaws
Recent security vulnerabilities named Spectre and Meltdown have surfaced in the realm of computer architecture and hardware implementation. These flaws allow attackers to access sensitive data through covert channels utilizing speculative execution mechanisms. The vulnerabilities exploit the perform
0 views • 12 slides
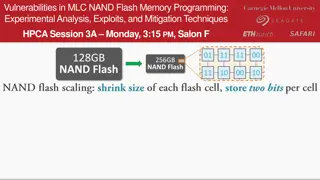
Experimental Analysis of Vulnerabilities in MLC NAND Flash Memory Programming
This session at HPCA explores the experimental analysis, exploits, and mitigation techniques related to vulnerabilities in MLC NAND flash memory programming. The presentation delves into the risks associated with NAND flash memory, such as data corruption and errors during read operations. It discus
0 views • 10 slides
Functional Programming Concepts for COMPSCI 220 Programming Methodology
In this tutorial, we explore functional programming concepts in the context of COMPSCI 220 Programming Methodology. We delve into writing functions using `reduce` and discuss examples and implementations of various functions like sum, product, and string length calculation. We also analyze the diffe
1 views • 47 slides