Experimental Analysis of Vulnerabilities in MLC NAND Flash Memory Programming
This session at HPCA explores the experimental analysis, exploits, and mitigation techniques related to vulnerabilities in MLC NAND flash memory programming. The presentation delves into the risks associated with NAND flash memory, such as data corruption and errors during read operations. It discusses potential exploits and ways to address these security concerns. Various techniques for enhancing the integrity and reliability of NAND flash memory are highlighted, emphasizing the importance of understanding and mitigating vulnerabilities in programming practices.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
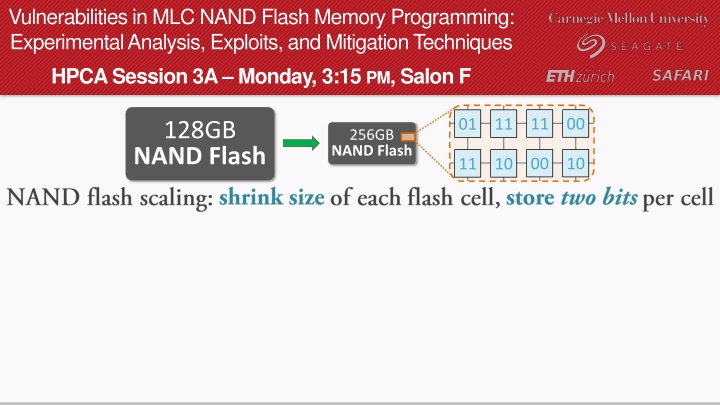
Vulnerabilities in MLC NAND Flash Memory Programming: Experimental Analysis, Exploits, and Mitigation Techniques HPCA Session 3A Monday, 3:15 PM, Salon F 11 00 01 11 128GB NAND Flash 256GB NAND Flash 00 10 11 10
Vulnerabilities in MLC NAND Flash Memory Programming: Experimental Analysis, Exploits, and Mitigation Techniques HPCA Session 3A Monday, 3:15 PM, Salon F 11 00 01 11 128GB NAND Flash 256GB NAND Flash 00 10 11 10 10 11 Program 00 ?? 10 10
Vulnerabilities in MLC NAND Flash Memory Programming: Experimental Analysis, Exploits, and Mitigation Techniques HPCA Session 3A Monday, 3:15 PM, Salon F 11 00 01 11 128GB NAND Flash 256GB NAND Flash 00 10 11 10 10 11 Program 00 ?? 00 ?0 ?? Step 2 Step 1 10 10
Vulnerabilities in MLC NAND Flash Memory Programming: Experimental Analysis, Exploits, and Mitigation Techniques HPCA Session 3A Monday, 3:15 PM, Salon F
Vulnerabilities in MLC NAND Flash Memory Programming: Experimental Analysis, Exploits, and Mitigation Techniques HPCA Session 3A Monday, 3:15 PM, Salon F Controller Flash Memory MSB . . . MSB data LSB Read With Errors . . . . . . MSB 1 MSB n MSB 0 Read Without Errors LSB n LSB 0 LSB 1
Vulnerabilities in MLC NAND Flash Memory Programming: Experimental Analysis, Exploits, and Mitigation Techniques HPCA Session 3A Monday, 3:15 PM, Salon F Controller Flash Memory MSB . . . MSB data LSB Read With Errors . . . . . . MSB 1 MSB n MSB 0 Read Without Errors LSB n LSB 0 LSB 1 ECC Limit Error Rate Lifetime
Vulnerabilities in MLC NAND Flash Memory Programming: Experimental Analysis, Exploits, and Mitigation Techniques HPCA Session 3A Monday, 3:15 PM, Salon F
Vulnerabilities in MLC NAND Flash Memory Programming: Experimental Analysis, Exploits, and Mitigation Techniques HPCA Session 3A Monday, 3:15 PM, Salon F
Vulnerabilities in MLC NAND Flash Memory Programming: Experimental Analysis, Exploits, and Mitigation Techniques HPCA Session 3A Monday, 3:15 PM, Salon F Lifetime (P/E Cycles) 8K Solution #3 16% Baseline 6K 4K 2K 0 10K 20K 30K 40K Read Disturb Count
Vulnerabilities in MLC NAND Flash Memory Programming: Experimental Analysis, Exploits, and Mitigation Techniques HPCA Session 3A Monday, 3:15 PM, Salon F Lifetime (P/E Cycles) 8K Solution #3 16% Baseline 6K 4K 2K 0 10K 20K 30K 40K Read Disturb Count