Apache MINA: High-performance Network Applications Framework
Apache MINA is a robust framework for building high-performance network applications. With features like non-blocking I/O, event-driven architecture, and enhanced scalability, MINA provides a reliable platform for developing multipurpose infrastructure and networked applications. Its strengths lie i
3 views • 13 slides
Modeling and Generation of Realistic Network Activity Using Non-Negative Matrix Factorization
The GHOST project focuses on the challenges of modeling, analyzing, and generating patterns of network activity. By utilizing Non-Negative Matrix Factorization (NMF), realistic network activity patterns can be created and injected into live wireless networks. Understanding and predicting user behavi
4 views • 28 slides
Understanding Magnetic Disks and Disk Controllers in Computer Memory Hierarchy
Auxiliary memory in computer systems provides additional backup storage through technologies like magnetic disks and tapes. Magnetic disks, which consist of circular platters coated with magnetizable material, offer direct access storage and are controlled by read/write mechanisms and disk controlle
10 views • 42 slides
Exercise Evaluation Training
Controllers and Evaluators play crucial roles in exercise evaluation. Controllers ensure the exercise meets objectives while maintaining safety and focus. Evaluators organize evaluation, observe, and collect data to identify strengths and areas for improvement. Exercise Evaluation Guide (EEG) provid
1 views • 14 slides
Network Compression Techniques: Overview and Practical Issues
Various network compression techniques such as network pruning, knowledge distillation, and parameter quantization are discussed in this content. The importance of pruning redundant weights and neurons in over-parameterized networks is highlighted. Practical issues like weight pruning and neuron pru
0 views • 37 slides
Understanding Wireless Wide Area Networks (WWAN) and Cellular Network Principles
Wireless Wide Area Networks (WWAN) utilize cellular network technology like GSM to facilitate seamless communication for mobile users by creating cells in a geographic service area. Cellular networks are structured with backbone networks, base stations, and mobile stations, allowing for growth and c
2 views • 17 slides
Network Slicing with OAI 5G CN Workshop Overview
Overview of Network Slicing with OAI 5G CN workshop focusing on the crucial role of network slicing in realizing the service-oriented 5G vision. This workshop covers topics like multiple logical networks creation on shared infrastructure, different types of network slices, preparation and instantiat
1 views • 6 slides
Understanding PID Controllers in Control Systems
PID controllers, utilized in various industries, provide control feedback compensation through proportional, integral, and derivative components to modulate error and achieve desired system response. Different compensators like PI, PD, and PID offer varying characteristics impacting stability, overs
0 views • 11 slides
Understanding Flow Monitoring in OVS for Efficient Network Management
Learn how Flow Monitoring in Open vSwitch (OVS) allows controllers to track and manage changes to flow tables, enabling efficient network management. Explore topics such as Flow Mod programming, Flow Monitor messages, OVS support, monitoring vs. snoop, and practical examples of flow monitoring in ac
0 views • 9 slides
IEEE 802.11-19/1517r0 TDD Beamforming Configuration Overview
IEEE 802.11-19/1517r0 discusses TDD beamforming operations related to Beam Measurement in the standard. Before Draft 4.0, these operations were primarily initiated by SME, causing limitations due to proprietary network controllers. The document reviews gaps and improvements in TDD beamforming, aimin
0 views • 10 slides
Understanding Snort: An Open-Source Network Intrusion Detection System
Snort is an open-source Network Intrusion Detection System (NIDS) developed by Cisco, capable of analyzing network packets to identify suspicious activities. It can function as a packet sniffer, packet logger, or a full-fledged intrusion prevention system. By monitoring and matching network activity
0 views • 23 slides
Understanding Programmable Logic Controllers (PLC)
Programmable Logic Controllers (PLCs) are tiny computers used to control system functions with programmed logic. They receive inputs and provide operating instructions to automate processes in various industries. PLCs have replaced manual relay-based systems and are essential in industrial control t
0 views • 24 slides
Traffic Control and Coordination: Next Generation Signal Controller Overview
Explore the evolution of traffic signal controllers in Australia, from VC5 to VC6, along with the software integration and system overview. Learn about the hardware configurations and capabilities of the latest TSC/4 controllers, including signal group monitoring and conflict capabilities. The new g
4 views • 10 slides
A Comparative Analysis of Controllers and Followers in "Othello" and "A Streetcar Named Desire
The paper explores the dynamics of control and submission in "Othello" and "A Streetcar Named Desire," focusing on the characters' roles as controllers, followers, masters, and slaves. It delves into the methods of gaining control, such as through authority, language mastery, and sexual seduction, h
0 views • 37 slides
mass flow controllers
the increasing demand for mass flow controllers in pharmaceutical and medical devices industries and advancements in sensor technology are expected to offer growth opportunities for the players operating in this market.
1 views • 4 slides
Transportation Network Modeling and Analysis with C.Coupled SE Platform
This content outlines the features and functionalities of the C.Coupled SE Platform (CSET Platform) developed by the Connetics Transportation Group. It covers aspects such as interface design, inputs merging, purposes, platform development using Cube, TAZs merging, and network attributes. The platfo
0 views • 11 slides
Understanding Apple iOS MVC Architecture
This introduction to Apple mobile technologies explores iOS Model-View-Controller (MVC) architecture, highlighting the division of programs into logical units and emphasizing communication management between controllers, models, and views. Discover how controllers interact with models and views, and
0 views • 18 slides
Android Bluetooth Game Controllers Support and Setup Guide
This guide explores the built-in support for game controllers in Android devices, detailing how to process joystick movements and key events. It covers KeyEvent and MotionEvent objects, checking for connected game controllers, and understanding different source types like SOURCE_GAMEPAD and SOURCE_J
0 views • 13 slides
Understanding OpenFlow Switch Limitations
OpenFlow architecture presents limitations in flow table entries, matching fields, and asynchronous network events between switches and controllers. The background covers current applications, switch design, and network events related to OpenFlow technology.
0 views • 42 slides
Understanding NFV and SDN Controllers in Networking Architecture
This content discusses the architecture and components for designing NFV solutions, including roles of ETSI, OPNFV, ODL, and forwarding in the network. It highlights the coordination needed in deploying NFV in data centers and smaller facilities, emphasizing the use of NFV and SDN controllers to wor
0 views • 16 slides
Step-by-Step Guide to Configuring APACS & AAN Controllers
This detailed guide outlines the steps to configure APACS & AAN Controllers, including connecting power, network setup, checking operation, programming IP addresses, reader interfaces, software installation, and system configuration. Follow these instructions methodically to successfully set up and
0 views • 20 slides
Effective Fuzz Testing for Programmable Logic Controllers - Research for Nuclear Safety
This paper discusses the significance of fuzz testing for Programmable Logic Controllers (PLCs) to ensure nuclear safety, citing incidents like the Stuxnet worm attack. It delves into the methodology, zero-day vulnerability findings, and results of the research conducted by authors in February 2020,
1 views • 11 slides
Financial Reporting Tools Overview for FSU Controllers Office
Detailed overview of the financial reporting tools available for the FSU Controllers Office, including OMNI/BI Departmental Ledger review, other BI reports and queries, OMNI Financials, and daily updates for monthly department financial activity. These tools provide essential information for monitor
0 views • 19 slides
Efficient Dynamic Skinning with Low-Rank Helper Bone Controllers
This research explores efficient dynamic skinning methods using low-rank helper bone controllers to achieve robust, simple, and high-performance skin deformation in computer graphics. By investigating linear blend skinning techniques and helper bone rigs, the study aims to address the wishlist of ga
0 views • 29 slides
Meridian: An SDN Platform for Cloud Network Services
Meridian is an SDN platform developed by Mohammad Banikazemi, David Olshefski, Anees Shaikh, John Tracey, and GuohuiWang at IBM T. J. Watson Research Center. The platform focuses on providing cloud network services efficiently. It encompasses an architecture that enables faster and more convenient n
0 views • 21 slides
Understanding Kubernetes Controllers: Managing State and Reacting to Changes
Kubernetes controllers play a crucial role in managing the state of resources within a Kubernetes cluster by watching for changes in the API server and ensuring the desired state matches the current state. They take actions to bring the system into alignment, helping to maintain stability and effici
0 views • 15 slides
Comprehensive Overview of GDPR and Information Law Updates
This content delves into the implications and obligations introduced by the General Data Protection Regulation (GDPR) and Information Law updates, emphasizing the increased responsibilities for data controllers, fines for non-compliance, and the criticality of data protection compliance in organizat
0 views • 13 slides
Design and Verification of Autonomous System Controllers
Explore the challenges of designing autonomous system controllers under timing uncertainties, focusing on quantitative safety measures to ensure the robot maneuvers safely despite deadline misses. The study delves into implementing controllers, analyzing trajectory deviations under different scenari
0 views • 18 slides
Bulgarian National Control System in the Danube Region Programme
The Bulgarian national control system for the Danube Region Programme involves a centralized approach from 2021-2027. The Ministry of Regional Development and Public Works oversees the system, with controllers appointed at the national level. The system includes a National Control Unit with quality
0 views • 10 slides
Neural Network Control for Seismometer Temperature Stabilization
Utilizing neural networks, this project aims to enhance seismometer temperature stabilization by implementing nonlinear control to address system nonlinearities. The goal is to improve control performance, decrease overshoot, and allow adaptability to unpredictable parameters. The implementation of
0 views • 24 slides
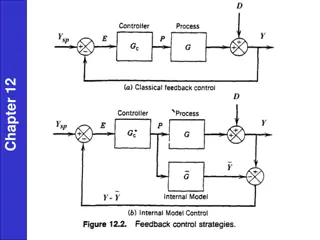
Control System Synthesis and Compensation Techniques
Explore various chapters discussing topics like direct synthesis, closed-loop transfer functions, PI controllers, time delay compensation, and Smith predictor approach in control systems. Learn about modeling feedback controllers, closed-loop performance, and response specifications.
0 views • 9 slides
Understanding Network Analysis: Whole Networks vs. Ego Networks
Explore the differences between Whole Networks and Ego Networks in social network analysis. Whole Networks provide comprehensive information about all nodes and links, enabling the computation of network-level statistics. On the other hand, Ego Networks focus on a sample of nodes, limiting the abili
0 views • 31 slides
Broadband Access Points & Programmable Logic Controllers Replacement Phase 1 Project Overview
This project overview provides details of the Broadband Access Points & Programmable Logic Controllers Replacement Phase 1 Project led by Jeff Ray, EIT Project Engineer at Treatment & Recycle Engineering. It includes information on the pre-submittal conference, RFQ schedule, evaluation criteria, and
0 views • 13 slides
Introduction to Spring MVC with Template Engine
Spring MVC is a framework for building web applications in Java that follows a model-view-controller architecture. Controllers handle logic, process HTTP requests, and inject data into views using template engines like Thymeleaf. Views contain HTML pages with dynamic content injected from controller
0 views • 26 slides
Control System Overview for ATLAS Superconducting Accelerator
The ATLAS Control System Group manages control systems from ion sources to specified areas, utilizing hardware such as AlphaServer and various controllers. Software tools from Vista Control Systems offer real-time control functionalities for OpenVMS, Linux, and Windows. Data management includes CAMA
0 views • 17 slides
Network Function Virtualization (NFV) Overview
Network Function Virtualization (NFV) focuses on virtualizing network functions to improve efficiency and reduce costs in network infrastructure. The lecture discusses key readings, devices that compose a network, specialization of devices, benefits of one-device-does-anything approach, and the goal
0 views • 21 slides
Enhancing Network Stability with Network Monitoring Systems
Network monitoring is crucial for efficient management and proactive issue detection in a network environment. Factors influencing an effective network system include choosing the best OEM, SLA agreements, and selecting a reliable System Integrator. Reactive monitoring can lead to financial losses a
0 views • 12 slides
Genetic Programming Tree Implementation for Pac-Man Controllers
Implementation of genetic programming tree for Pac-Man controllers involves methods like random search through parse tree space, full genetic programming recombination, mutation, and competitive co-evolution. The setup includes defining the problem formulation, scoring function represented as a tree
0 views • 26 slides
Introduction to ASP.NET MVC: Understanding Controllers, Views, and Models
Explore the fundamentals of ASP.NET MVC with Dhananjay Kumar in this informative webinar. Delve into the concepts of Controllers, Views, and Models, learn about ViewBag, ViewData, and TempData, and discover the benefits of using client-side libraries like jQuery and Ignite UI. Gain insights into str
0 views • 31 slides
Understanding Programmable Logic Controllers (PLCs) in Robotic Cell Operations
Programmable Logic Controllers (PLCs) are versatile devices used in various industries for automation and control processes. This article explores the functionality and applications of PLCs in supporting robotic cell operations, emphasizing their role in conveyor control, multi-robot workstations, a
0 views • 15 slides