OBSERVERS’ BRIEFING
Advanced encryption techniques, stringent manufacturing processes, and administrative safeguards are in place to ensure the security and integrity of electronic voting machines. Observers play a crucial role in overseeing EVM/VVPAT checks, commissioning processes, and ensuring transparency throughou
0 views • 16 slides
Supreme Court Rejects Petitions Against EVM Use In Elections
Supreme Court Rejects Petitions Against EVM Use In Elections\\nNew Delhi: \\nThe Supreme Court on Friday dismissed two writ petitions: namely, apprehensions over 19 lakhs missing EVMs and another petition to use ballot paper to conduct elections while reposing its faith in the EVMs.\\nAdjudicating t
1 views • 4 slides
Step-by-Step TCP/IP Configuration on Windows 10 Client
Detailed guide on configuring TCP/IP settings on a Windows 10 client, including preparation steps, configuration steps, and verification of settings. The guide provides clear instructions with accompanying images for each step.
1 views • 12 slides
WHONET Training Course: Laboratory Configuration and Setup
Understanding the laboratory configuration process in WHONET is crucial for effective data entry and analysis. This module guides users on setting up a new laboratory, entering country and lab details, defining antibiotics, sample locations, and data fields, creating microbiological alerts, and savi
3 views • 57 slides
Comprehensive Guide to District and Constituency Election Planning
This presentation delves into the intricate details of District and Constituency Election Management Plans (DEMP), focusing on various aspects such as district profiles, EVM management, security deployment, communication strategies, and training. It emphasizes the importance of interaction with poli
1 views • 64 slides
Proposal for Location Configuration Information (LCI) in IEEE 802.11 Beacons and Probe Responses
This document proposes the inclusion of Location Configuration Information (LCI) data in a standard information element broadcast in Beacons and Probe Responses within IEEE 802.11 networks. By enhancing the accessibility of infrastructure location to non-AP STAs, this proposal aims to simplify locat
1 views • 5 slides
IEEE 802.11-20/0668r1: EHT BSS Configuration Proposal
The document discusses the configuration of a 320 MHz BSS in the context of 6 GHz regulations, focusing on EHT operation elements such as channel width indication, CCFS principles, and BSS advertisement settings. It proposes design principles for managing legacy and EHT STA operations, emphasizing s
0 views • 14 slides
Guide to EVM and VVPAT Components, Connections, and Preparation for Poll
This comprehensive guide covers the components of Electronic Voting Machines (EVM) and Voter Verifiable Paper Audit Trail (VVPAT) systems, including protocols for setting up, connection processes for mock and actual polls, and instructions for masking/unmasking ballot buttons on the Balloting Unit (
0 views • 13 slides
EVM-VVPAT Administrative Procedures for Election Management
This document outlines the standard operating procedures (SoP) for Electronic Voting Machines (EVMs) and Voter Verifiable Paper Audit Trail (VVPAT) systems used in elections. It covers the components of EVMs, the process of voting, the roles of polling officers, and various sub-topics such as storag
1 views • 58 slides
Enhancing EPS Authorization and Configuration Options in 5G Networks
The proposal focuses on enhancing authorization and configuration options in EPS using protocol configuration options. It discusses the attach procedure, ePCO checking, and the importance of ePCO support in the network architecture. The solution presented emphasizes the role of MME, SGW, and PGW-C+S
0 views • 8 slides
Discussion on 5G NR CADC Configuration Handling in RAN5
The discussion revolves around the existing Tdocs and WIs focusing on how to handle 5G NR CADC configuration within RAN5. It includes proposals to streamline guidelines and checklists to effectively manage new configurations. Various operators and entities like CMCC, Huawei, Ericsson, China Unicom,
0 views • 9 slides
IEEE 802.11-20/0456r0: Transmission EVM Requirements for 4k QAM
The document discusses the tradeoff between error vector magnitude (EVM) and transmission power in the context of 4k QAM modulation. It explores the EVM requirements for 4k QAM and addresses issues such as channel estimation errors, modulation and coding scheme (MCS) parameters, and degradation with
0 views • 11 slides
Understanding Bipolar Transistor Configurations for Electronic Circuits
Explore the three common configurations - Common Base, Common Emitter, and Common Collector - for Bipolar Transistors in electronic circuits. Each configuration offers unique characteristics such as voltage gain, current gain, and impedance levels, impacting the signal processing and amplification c
0 views • 27 slides
Discussion on Multi-PUSCH Configuration for UTO-UCI Content Moderator at Ericsson
This discussion encompasses the configuration and implications of the Multi-PUSCH setup based on agreed parameters within the UTO-UCI content moderation context at Ericsson. It delves into varying configurations, potential impacts, and considerations for effective utilization. The slides provide ins
0 views • 17 slides
IEEE 802.11-21/0012r1 Considerations on Open Issues in PHY Requirements
In the January 2021 document IEEE 802.11-21/0012r1, discussions were held on open issues related to PHY requirements, including LO requirements for 320 MHz transmission, EVM requirements for 1024 QAM and BPSK-DCM-DUP, minimum sensitivity for 4K QAM and BPSK-DCM-DUP, and channel rejection levels. Sug
0 views • 12 slides
5G Use Case Proposal for Dublin Ericsson
This proposal outlines the use of NETCONF for configuration management in 5G networks, focusing on Dublin. It covers topics like Configuration with NETCONF, NETCONF Overview, NETCONF Security, YANG Overview, and Proposed Use Cases and Requirements for Dublin. The proposal emphasizes the importance o
7 views • 20 slides
Exploring the Impact of Wing Configuration on Paper Airplane Flight
Explore how changing the wing configuration of paper airplanes affects their flight distance. Learn about lift, drag, and aerodynamics, and conduct experiments to test hypotheses. The results provide insights into the role of wing design in flight performance.
0 views • 12 slides
Focal Point Responsibilities in Data Management System
Detailed instructions on key responsibilities of a focal point including user creation, configuration backups, data export, maintenance, and configuration import in a data management system. Tasks involve creating and editing users, exporting configurations and data, and maintaining system integrity
0 views • 12 slides
Techno-Economic Analysis of Calcium Looping Processes for Low CO2 Emission Cement Plants
This study explores the application of Calcium Looping (CaL) processes in cement plants to reduce CO2 emissions. The process involves using CaO as a sorbent to capture CO2 from flue gas, with the potential for integration at different points in the cement production process. The Tail-end CaL configu
3 views • 14 slides
Understanding Native VLAN 1 in Mesh Ethernet Bridging
Mesh Ethernet bridging utilizes native VLAN 1 for the initial configuration, ensuring the RAP connects to the native VLAN ID 1 on a switch. This setup affects the communication between the RAP and the Map devices, as well as their connection to the controller. Misconfigurations related to VLAN taggi
0 views • 9 slides
Managing Passive Host and Service Checks with Nagios Core
Learn how to enable passive host and service checks in Nagios Core via the configuration file, allowing for monitoring without actively polling the hosts and services. Understand the setup, configuration, and usage of passive checks in your monitoring system. Explore examples and best practices for
0 views • 30 slides
Understanding BIND DNS Security Vulnerabilities and Configuration
Dive into the world of BIND DNS with a focus on security vulnerabilities, zone transfer restrictions, rate limiting, and essential configuration options. Explore key topics such as ISC mailing lists, CVE announcements, and best practices for setting up BIND DNS servers.
1 views • 16 slides
Procedures for Closing and Declaring Polls in an Election
Learn the steps involved in closing and declaring polls during an election, including distributing slips, closing the control unit, recording votes, sealing election papers, and delivering materials to the collection center. Follow guidelines for distributing numbered slips to voters present at clos
0 views • 38 slides
Comprehensive Setup and Configuration Guide for Office Management Software
Detailed setup and configuration instructions for your office management software, including customizing company information, tax rates, localization settings, barcode types, stock management, receipts, and invoices. Ensure a seamless setup process by following the step-by-step guidance provided in
0 views • 31 slides
Configuration Examples for IP SLA with Object Tracking
Learn how to configure and troubleshoot IP SLA with Object Tracking using detailed examples for Static Routing, HSRP, and Policy Based Routing. Find out where Object Tracking can be implemented and when not to use it in various network scenarios. Understand the configuration components, including de
2 views • 17 slides
Evolution of Configuration Management in Software Engineering
Explore the evolution of configuration management in software engineering, highlighting key practices like cloud-based IDE, shared repositories, and unobtrusive configuration management. Understand the importance of modern best practices in software development, traditional vs. optimistic approaches
0 views • 20 slides
UITF MPS System Requirements and Protection Details
Combining hardware configuration and CEBAF-style FSD protection, the UITF MPS system ensures laser safety, vacuum control, and GUN HV stability. It protects against beam loss, maintains UHV, safeguards viewers, magnets, RF components, and more through a series of interlocks and comparator systems. T
0 views • 7 slides
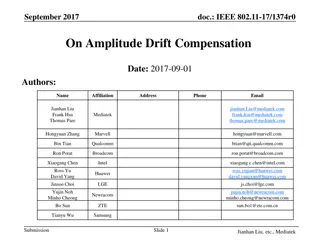
Amplitude Drift Compensation in IEEE 802.11-17/1374r0 Document
The document discusses Amplitude Drift Compensation in the context of EVM tests for IEEE 802.11 devices. It highlights the challenges posed by amplitude drift, the impact on EVM degradation, and the need for compensation mechanisms. Various authors from different affiliations contribute insights on
0 views • 6 slides
U-Boot Debug Using CCSv5 - Fundamentals and Examples
This session covers the essentials of using CCSv5 and a JTAG to debug a TI SDK-based U-Boot on an EVM platform. It includes pre-work checklist, agenda, background information, components of Sitara Linux SDK, where to get the SDK, CCS installation details, and example development environment for AM33
0 views • 34 slides
Conducting a BLDC Gate Driver Schematic Review and Debug Process
Exploring how to effectively review and debug a Brushless-DC (BLDC) motor driver schematic, focusing on locating EVM hardware files, understanding schematic recommendations, detecting errors, and providing valuable feedback. The process involves utilizing available resources to create, review, and d
0 views • 30 slides
LArDPS to eFEX Test Configuration for FOX Demonstrator
Configuration details and diagrams for testing the direct path from the LArDPS to eFEX in the FOX Demonstrator, including optical insertion loss measurements, offset calibration using different setups, and diagrams without splitters. The setup matches the planned configuration for the test.
0 views • 34 slides
Updates on iKAGRA Installation and Configuration Changes
The report discusses changes in the iKAGRA configuration from Fabry-Perot Michelson Interferometer to Michelson Interferometer due to schedule constraints and budget limitations. The document outlines the revised schedule for installation tasks, shift applications, and the impact on the KAGRA projec
0 views • 16 slides
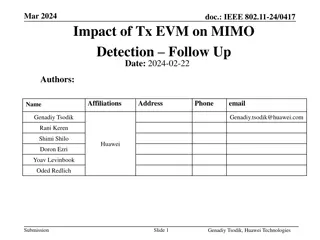
Impact of Tx EVM on MIMO Detection Follow-Up
This document discusses the impact of Tx EVM on MIMO detection, highlighting that improving Tx EVM can achieve theoretical gains in nonlinear detection. It addresses questions raised during discussions and presents an optimal detector scenario in the presence of colored noise from Tx EVM. Simulation
0 views • 14 slides
3GPP TSG-RAN WG4 Meeting #100-e Electronic Meeting Summary
The 3GPP TSG-RAN WG4 Meeting #100-e held discussions on defining EVM limits, modulation schemes, repeater requirements, and IMD requirements. Emphasis was placed on linking EVM levels to modulation schemes and declaring supported levels for repeaters. The meeting also addressed NF equivalent RF requ
0 views • 7 slides
Insights into Operating Experience and Configuration Management in Nuclear Power Plants
Explore the significance of Operating Experience (OE) in refining machine and human performance, reinforcing desired behaviors, solving problems timely, and sharing industry-wide knowledge in nuclear power. Learn from examples highlighting the importance of configuration management in mature nuclear
0 views • 11 slides
Advanced Neutronics Parameters for Fusion Chamber Configuration with Magnetic Intervention
Detailed analysis and design considerations for a fusion chamber configuration utilizing magnetic intervention to optimize neutronics parameters. The discussion includes blanket configuration, neutron wall loading distribution, blanket design options, nuclear design requirements, and dimensions meet
0 views • 12 slides
Recap of eZeeKonfigurator Notice Configuration and Zeek Week Oct 2019
A summary of events involving a talk at Zeek Week, issues with notice configuration, experiences with Zeek/Bro, and the introduction of eZeeKonfigurator for configuring Zeek clusters. The content includes descriptions of individuals involved, challenges faced, support for cluster configurations, and
0 views • 20 slides
Efficient Skyline Batch Workflow Tool for Processing Multiple Files
Utilize Skyline Batch, a user-friendly tool developed by Ali Marsh, to run simple Skyline workflows on multiple files efficiently. This tool is ideal for overnight processing, reprocessing data easily, and sharing workflows across different computers. Quickly transform Skyline templates into report
0 views • 4 slides
Removal of FILS IP Address Configuration in IEEE 802.11-14/0093r2
This document details the rationale behind the proposal to remove FILS IP Address Configuration in IEEE 802.11-14/0093r2. The author, Hitoshi Morioka, explains that the need for this configuration is redundant due to the HLP encapsulation's ability to support all required functions. By eliminating c
0 views • 18 slides
Development of NSF Process for Validation and Acceptance of EVMS: Insights and Recommendations
NSF is enhancing guidelines for Earned Value Management Systems (EVMS) to evaluate construction project status. Insights suggest obtaining certification and validation for maintaining acceptable EVM systems, important for project oversight. Recommendations highlight the need for decisive action to e
0 views • 16 slides