Automated Anomaly Detection Tool for Network Performance Optimization
Anomaly Detection Tool (ADT) aims to automate the detection of network degradation in a mobile communications network, reducing the time and effort required significantly. By utilizing statistical and machine learning models, ADT can generate anomaly reports efficiently across a large circle network
8 views • 7 slides
The Warning of Worldliness in Revelation
The images and verses from Revelation 17 highlight the dangers of worldliness, spiritual adultery, and the deception of the world system. The vivid descriptions of a woman on a scarlet beast, symbolizing worldly allure and opposition to God, serve as a cautionary tale against being ensnared by the a
0 views • 19 slides
Drone Detection Using mmWave Radar for Effective Surveillance
Utilizing mmWave radar technology for drone detection offers solutions to concerns such as surveillance, drug smuggling, hostile intent, and invasion of privacy. The compact and cost-effective mmWave radar systems enable efficient detection and classification of drones, including those with minimal
0 views • 8 slides
Understanding Voice Stress Analysis for Deception Detection
Voice Stress Analysis (VSA) employs technology to detect micro-tremors in the vocal muscles that indicate stress, potentially linked to deception. Developed based on Dr. Lippold's work, VSA systems measure changes in speech characteristics caused by mental stress, aiming to assess the truthfulness o
0 views • 11 slides
Machine Learning Techniques for Intrusion Detection Systems
An Intrusion Detection System (IDS) is crucial for defending computer systems against attacks, with machine learning playing a key role in anomaly and misuse detection approaches. The 1998/1999 DARPA Intrusion Set and Anomaly Detection Systems are explored, alongside popular machine learning classif
0 views • 36 slides
Unveiling the Evil Trinity and its Deception in Revelation
Dive into the intriguing world of the Evil Trinity as depicted in Revelation, where Satan mimics the Holy Trinity with the Red Dragon, the Beast from the Sea (Antichrist), and the Beast from the Earth (False Prophet). Explore the battles in heaven and on earth, and learn how believers can combat dec
0 views • 23 slides
Deception Game on Decoy Systems and Honeypots
Deception Game on Decoy Systems and Honeypots explores the use of deception technologies in computer security, focusing on decoy systems like honeypots. It delves into how attackers are lured into fake objects and the monitoring of their behavior to mitigate intrusion. The concept of fake honeypots,
4 views • 25 slides
NC22Plex STR Detection Kit: Advanced 5-Color Fluorescence Detection System
Explore the cutting-edge NC22Plex STR Detection Kit from Jiangsu Superbio Biomedical, offering a 5-color fluorescence detection system suitable for multiple applications. Enhance your research capabilities with this innovative product designed for precision and efficiency.
0 views • 20 slides
Automated Melanoma Detection Using Convolutional Neural Network
Melanoma, a type of skin cancer, can be life-threatening if not diagnosed early. This study presented at the IEEE EMBC conference focuses on using a convolutional neural network for automated detection of melanoma lesions in clinical images. The importance of early detection is highlighted, as exper
0 views • 34 slides
Colorimetric Detection of Hydrogen Peroxide Using Magnetic Rod-Based Metal-Organic Framework Composites
Nanomaterials, particularly magnetic rod-based metal-organic frameworks composites, are gaining attention for their exceptional properties and various applications in different fields. This study by Benjamin Edem Meteku focuses on using these composites for colorimetric detection of hydrogen peroxid
0 views • 16 slides
Insights into Ovid's Heroides: Love, Deception, and Feminine Voice
Ovid's Heroides explores love through mythological figures, showcasing a different approach from his other works. Inspired by Propertius, these fictional verse epistles incorporate emotional depth and deception. The dual readership and authorship dynamics, alongside the feminine voice employed, offe
0 views • 14 slides
Analysis of Don Pedro in "Much Ado About Nothing
Don Pedro in "Much Ado About Nothing" is depicted as a complex character who showcases qualities of kindness, judgmental behavior, loyalty, and deception. He is portrayed as kind and respectful towards Beatrice, loyal to his friends like Claudio, quick to judge at times, and strategic in his efforts
0 views • 21 slides
Deception and Humor in "The Rivals" by Sheridan
In "The Rivals" by Richard Brinsley Sheridan, a tale of deception unfolds as characters plot to deceive one another. Mrs. Malaprop unwittingly becomes part of a scheme to help Lydia elope with Ensign Beverley. Jack Absolute successfully gains the trust of both Lydia and Mrs. Malaprop through clever
0 views • 59 slides
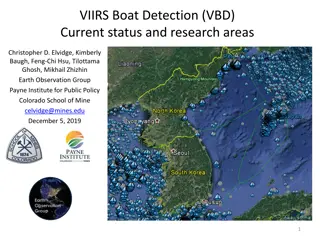
VIIRS Boat Detection (VBD) Research Overview
The Visible Infrared Imaging Radiometer Suite (VIIRS) program, a joint effort between NASA and NOAA, focuses on weather prediction and boat detection using low light imaging data collected at night. The VIIRS system provides global coverage with sensitive instruments and efficient data flow processe
1 views • 13 slides
Multibeam Data Analysis for Seabed Characterization at Deception Island, Antarctic
This work explores the morphological and sedimentary characterization of the seabed at Deception Island, Antarctic, through the analysis of multibeam bathymetric data and geological samples. The study identifies ravines, depressions, and volcanic structures as key features, revealing a seabed predom
0 views • 7 slides
Real-Time Cough and Sneeze Detection Project Overview
This project focuses on real-time cough and sneeze detection for assessing disease likelihood and individual well-being. Deep learning, particularly CNN and CRNN models, is utilized for efficient detection and classification. The team conducted a literature survey on keyword spotting techniques and
1 views • 15 slides
Stop Hidden Water Damage: Your Ultimate Guide to Leak Detection in San Diego
Learn how San Diego leak detection services can help protect your home from water damage. Discover the signs of leaks, advanced detection technologies, and tips to prevent costly repairs. Stay ahead with proactive slab leak detection and expert solut
0 views • 6 slides
GOES-R ABI Aerosol Detection Product Validation Summary
The GOES-R ABI Aerosol Detection Product (ADP) Validation was conducted by Shobha Kondragunta and Pubu Ciren at the NOAA/NESDIS/STAR workshop in January 2014. The validation process involved testing and validating the ADP product using proxy data at various resolutions for detecting smoke, dust, and
1 views • 21 slides
Real-Time Cough and Sneeze Detection Using Deep Learning Models
Detection of coughs and sneezes plays a crucial role in assessing an individual's health condition. This project by Group 71 focuses on real-time detection using deep learning techniques to analyze audio data from various datasets. The use of deep learning models like CNN and CRNN showcases improved
0 views • 15 slides
Development of Satellite Passive Microwave Snowfall Detection Algorithm
This study focuses on the development of a satellite passive microwave snowfall detection algorithm, highlighting the challenges in accurately determining snowfall using satellite instruments. The algorithm uses data from AMSU/MHS, ATMS, and SSMIS sensors to generate snowfall rate estimates, overcom
0 views • 20 slides
Methods and Devices for Detection of Deception
Various methods and devices are used for the detection of deception, including physiological responses recording, drug usage, hypnotism, observation, scientific interrogation, and confession. Deceptive behaviors manifest in verbal responses, posture changes, gestures, movements, and facial expressio
0 views • 20 slides
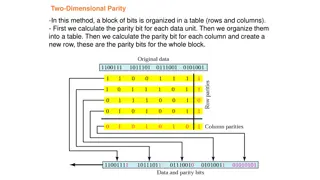
Data Error Detection Techniques Overview
Two-dimensional parity and Cyclic Redundancy Check (CRC) are data error detection methods used to ensure data integrity during transmission. Two-dimensional parity involves organizing bits in a table to calculate parity bits for data units and columns, while CRC appends a string of zeros to the data
0 views • 20 slides
Understanding Fraud and Forensic Accounting
Fraud is defined as deception to gain an unlawful advantage. Various legal definitions of fraud under Indian law are discussed, including those under the Indian Penal Code, Indian Contract Act, and Companies Act. The concept of forensic accounting in detecting and investigating fraud is also introdu
0 views • 15 slides
Overview of GRANDproto Project Workshop on Autonomous Radio Detection
GRANDproto project workshop held in May 2017 focused on improving autonomous radio detection efficiency for the detection of extensive air showers (EAS). Issues such as detector stability and background rates were discussed, with the goal of establishing radio detection as a reliable method for EAS
1 views • 14 slides
Analysis of Deception and Betrayal in Shakespeare's "Much Ado About Nothing
Explore the themes of deception and betrayal in Shakespeare's "Much Ado About Nothing" through the cunning actions of Don John, his cohort Borachio, and the jealousy-driven motives that lead to turmoil and heartache in the play. Witness the complexities of character dynamics and the consequences of
0 views • 21 slides
Timely Leak Detection San Diego | Professional Leak Detection Services
Protect your home with expert leak detection services in San Diego. Avoid costly water damage and health risks with timely detection of hidden leaks. Schedule today!\n\nKnow more: \/\/ \/san-diego-slab-leak-detection\/
0 views • 7 slides
How Professional Leak Detection Can Save Your San Diego Home | Leak Detection Sa
Protect your home from costly damage with professional leak detection in San Diego. Learn about expert services like slab leak detection, non-invasive testing, and more. Save money and prevent water damage with top San Diego leak detection services.\
0 views • 8 slides
EPA Compliance Basics: Tank Leak Detection and Monitoring Methods
Learn about EPA requirements for tank leak detection, release detection methods, and compliance methods for monitoring tank systems. Understand the importance of implementing effective leak detection systems to prevent contamination and comply with federal regulations, including Automatic Tank Gaugi
0 views • 18 slides
Research on Polygraph and Deception Detection
The research focuses on the use of polygraph tests for deception detection, highlighting concerns about accuracy when facing major security threats. It discusses the impact of countermeasures on polygraph screening effectiveness, emphasizing the value of research in detecting deception despite chall
0 views • 13 slides
Deception in Risk Analysis and Military Scenarios
Deception plays a crucial role in risk analysis, particularly in military scenarios where adversaries employ strategies to mislead and confuse. This involves reasoning under uncertainty, employing tactics like feint attacks, counter-recce activities, dummy airfields, and more. Understanding the use
0 views • 31 slides
Gas Detection of Hydrogen/Natural Gas Blends in the Gas Industry
Gas detection instruments play a crucial role in assessing the presence of hazardous atmospheres in the gas industry. This study focuses on the impact of adding hydrogen up to 20% in natural gas blends on gas detection instruments. The aim is to understand any potential inaccuracies in readings and
0 views • 30 slides
Timely San Diego Leak Detection | Protect Your Home from Water Damage
Discover the importance of timely leak detection in San Diego. Prevent costly water damage, reduce bills, and protect your home with professional leak detection services. Learn more about slab leak detection and prevention today!\n\nKnow more: \/\/m
0 views • 9 slides
Understanding Intrusion Detection Systems (IDS) and Snort in Network Security
Intrusion Detection Systems (IDS) play a crucial role in network security by analyzing traffic patterns and detecting anomalous behavior to send alerts. This summary covers the basics of IDS, differences between IDS and IPS, types of IDS (host-based and network-based), and the capabilities of Snort,
0 views • 34 slides
The Deception of Loving and Believing a Lie: Insights from Scripture
Explore the intricate web of deception woven through our human tendencies to love and believe in lies, as illuminated through various passages from Scripture. Delve into the reasons behind our affinity for falsehoods and the consequences of such choices in our lives.
0 views • 23 slides
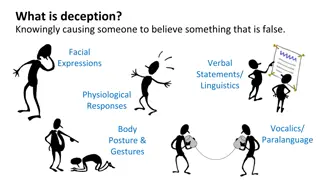
Understanding Deception and Financial Crime
Deception involves causing someone to believe false information through various means like facial expressions, verbal statements, and body language. In the realm of financial crime, money laundering is a significant concern where illegal proceeds are disguised to appear legal. Detection of deception
0 views • 4 slides
Understanding Anomaly Detection in Data Mining
Anomaly detection is a crucial aspect of data mining, involving the identification of data points significantly different from the rest. This process is essential in various fields, as anomalies can indicate important insights or errors in the data. The content covers the characteristics of anomaly
0 views • 50 slides
Enhancing OIG Audit Methodology for Improved Fraud Detection
The importance of improving methodologies for Office of Inspector General (OIG) auditors to enhance detection and proof of fraud cases, including civil and criminal offenses. Emphasizing on methods like forcing deception from suspects and diligently seeking answers from top management to strengthen
0 views • 31 slides
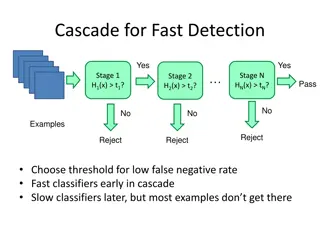
Object Detection Techniques Overview
Object detection techniques employ cascades, Haar-like features, integral images, feature selection with Adaboost, and statistical modeling for efficient and accurate detection. The Viola-Jones algorithm, Dalal-Triggs method, deformable models, and deep learning approaches are prominent in this fiel
0 views • 21 slides
Deception and Truth in Biblical Context
Pharisees try to entangle Jesus with their questioning, warning of false Christs and prophets. The urgency of seeking God in the midst of confusion and deception is emphasized, with references to the famine for God's Word and the choices between God's Holy Spirit and the devil's spirit. A tale of Th
0 views • 27 slides
Understanding Seducing Spirits and Tools of Deception
The passage explores the dangers of seducing spirits and doctrines of devils leading individuals astray from faith. Tools of deception, such as manipulation and isolation, are highlighted with biblical references to provide insight into recognizing and resisting these influences. Stay vigilant again
0 views • 14 slides