Pest control in Kolkata
Are you looking for professional pest control services in Kolkata? Socspl.com is here to provide the most reliable and efficient pest control services in Kolkata. We have extensive knowledge and experience in handling all kinds of pest infestations such as termite control, cockroach control, ant con
4 views • 8 slides
Personnel Safety Systems and Access Control at CERN Facilities
Personnel Safety Systems at CERN include ODH detection, fire safety measures, and access control to protect personnel from hazards. Various access control layers are implemented to regulate entry to different parts of the facility, ensuring only trained personnel access underground areas. Biometric
0 views • 19 slides
Pronoun Placement with Commands in English and Spanish
Understanding pronoun placement in commands is crucial in both English and Spanish. In English, pronouns are placed after the verb in both affirmative and negative commands. However, in Spanish, affirmatives attach pronouns while negatives place them in front of the verb. Examples and accent rules a
1 views • 5 slides
Android Debug Bridge (ADB) Commands
Android Debug Bridge (ADB) is a powerful command-line utility used to communicate with Android devices. It allows you to perform various tasks such as listing connected devices, installing apps, transferring files, taking screenshots, and more. Learn about ADB client-server architecture, connecting
3 views • 16 slides
Asian Pest Control - Professional Pest Management Services in Dhaka
Asian Pest Control offers top-quality pest control services in Dhaka, with a mission to be recognized as the best in the industry. Their highly trained professionals prioritize safety and environmental care while providing services like cockroach control, rodent control, snake repellent, lizard cont
1 views • 16 slides
Pronoun Placement Rules in Spanish Sentences
Clear up confusion around the placement of reflexive, direct object, and indirect object pronouns in Spanish sentences and commands. Learn the placement rules for different types of pronouns in statements and commands, including examples for single-verb and two-verb sentences. Understand the order o
2 views • 10 slides
CP and MV Commands in Unix/Linux
CP and MV commands in Unix/Linux are essential for copying and moving files or directories. CP is used to copy files with various options for different scenarios, while MV is used to move or rename files. Learn examples and practical usage of these commands to efficiently manage your files on the te
0 views • 5 slides
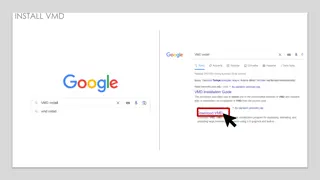
Step-by-Step Guide to Installing VMD Software and Using Linux Commands
Explore the comprehensive guide on installing Virtual Molecular Dynamics (VMD) software, along with insights into using Linux commands for data manipulation in Tk console. The tutorial covers registering, saving to desktop, and navigating through folders, concluding with loading data into VMD for vi
1 views • 9 slides
Introduction to Database Security and Countermeasures
Database security is essential to protect data integrity, availability, and confidentiality. Countermeasures such as access control, inference control, flow control, and encryption can safeguard databases against threats. Access control restricts user access, inference control manages statistical da
2 views • 26 slides
Database Security Measures and Controls
Database security is crucial to protect against threats like loss of integrity, availability, and confidentiality. Countermeasures such as access control, inference control, flow control, and encryption are important for safeguarding databases. Access control involves creating user accounts and pass
1 views • 35 slides
O3 Access Control Solution Overview
O3 Access Control Solution offers unique selling points like single-seat management software, role-based permissions, customizable user information, and more. The system includes a compact controller with multi-format reader support and BACnet Access objects. It integrates with other O3 modules for
0 views • 10 slides
Marketing Control and Its Importance in Business
Marketing control is a crucial process for firms to evaluate the impact of their marketing strategies and initiatives, making necessary adjustments for better outcomes. It involves various aspects such as annual plan control, profitability control, efficiency control, and strategic control. The proc
1 views • 20 slides
Comprehensive Overview of SQL Commands and Language Categories
In this detailed guide, you will learn about Structured Query Language (SQL) including its various commands such as Data Definition Language (DDL), Data Manipulation Language (DML), Data Control Language (DCL), and Transaction Control Language (TCL). Explore how SQL is used in Database Management Sy
0 views • 15 slides
HTCondor Submit Commands Overview
Comprehensive overview of HTCondor submit file commands, macros, and variables, emphasizing required commands, submit variables, execution point attributes, and containerization in high-throughput computing environments. Includes valuable insights and practical examples for better understanding.
0 views • 33 slides
Control Plans in Process Management
A Control Plan is vital in controlling risks identified in the FMEA process, focusing on process and product characteristics, customer requirements, and establishing reaction plans for out-of-control conditions. It serves as a central document for communicating control methods and includes key infor
2 views • 20 slides
On the Shoulders of Giants: Harnessing Powerful Commands in Stata for Efficient Coding
Stata users can enhance their coding efficiency by utilizing powerful commands that are often overlooked. This presentation showcases examples of commands that can streamline coding work, ranging from interactive use to supporting long programs. By leveraging these commands, users can avoid reinvent
1 views • 51 slides
Designing a Network-Controlled Railway System with Human Monitoring
Our project aims to design a network-controlled railway system that allows for human intervention and monitoring. The system consists of a main control station, multiple trains, and a communication and power infrastructure. The main control station includes a main microcontroller connecting to a PC,
2 views • 29 slides
File Transfer Protocols in Networking
Explore the fundamental concepts of File Transfer Protocol (FTP) in networking, covering its architecture, operation, commands, security considerations, and a comparison with Secure File Transfer Protocol (SFTP). Gain insights into how FTP enables the transfer of files between client and server, inc
0 views • 33 slides
Basic Linux Commands Overview for Embedded Programming and Robotics
Embedded Programming and Robotics Lesson 13 provides an introduction to basic Linux commands such as man, ls, cd, cp, and more. Understanding these commands is essential for interacting with the operating system on devices like Raspberry Pi. The lesson also covers important concepts like superuser p
0 views • 17 slides
Sudo and User Privileges Management in Linux
Enhance your knowledge on controlling access to sudo in Linux, allowing users to execute commands with root privileges securely. Explore the significance of logging sudo commands, managing sudo access through sudoers file, and utilizing the Wheel group for root access control.
0 views • 8 slides
Role-based Access Control Policies and Security Properties Overview
This content provides an overview of Role-based Access Control (RBAC) policies, Administrative RBAC (ARBAC) systems, and security properties in the context of access control in large organizations. It discusses the implementation of RBAC in various software systems, the assignment and revocation of
0 views • 18 slides
User Permissions in Database Management Systems
Database Management Systems (DBMS) offer security measures to control user accesses and permissions. Users can be assigned specific access rights and commands. This guide explains concepts like creating users, granting privileges, managing roles, and using GRANT commands effectively in DBMS.
0 views • 12 slides
BMC IPMI LED Control Commands
This content provides detailed commands for controlling LEDs using BMC IPMI for RS700A-E11-RS12U server systems. It includes instructions for LED commands, disabling sensor scans, setting GPIO status, and more, along with specific configurations for drive control status and LED blinking patterns for
0 views • 5 slides
Introduction to the Command Line: Basic Commands and Unix Systems
This material provides an overview of fundamental commands in Unix systems, applicable to both Unix and Linux operating systems. It covers topics like directory structure, text file manipulation, file permissions, redirections, pipes, wildcards, and more. Learn about the nature of Unix systems, how
0 views • 43 slides
Filesystem Security Principles and Access Control
Learn about filesystem security, general principles, discretionary access control (DAC), closed vs. open policy, closed policy with negative authorizations, and access control entries and lists. Discover how files and folders are managed, the role of access control lists (ACLs), and the different le
2 views • 56 slides
Spanish Commands Review and Tips for Test Success
Prepare for your test on Spanish commands by reviewing the formation of affirmative, negative, and stem-changing verbs. Learn how to form Ud., Uds., and negative commands, and understand the nuances of -car/gar/zar verbs. Master the use of el, la, los, and las pronouns for effective communication in
0 views • 16 slides
Guide to Giving Negative Commands in Spanish
Learn how to effectively communicate what not to do in Spanish with negative commands. Understand the different forms of negative commands for -AR, -ER/-IR verbs, irregular verbs, direct object pronouns, stem-changing verbs, and verb forms ending in -CAR, -GAR, -ZAR. Master the rules and exceptions
0 views • 12 slides
The Imperative Mood in Language
The imperative mood focuses on giving commands without reference to different time frames. It entails direct statements with the understood recipient mainly being 'you.' Commands in the singular, informal form involve dropping the 's' from the second person singular verb, both in affirmative and neg
0 views • 19 slides
Mastering T Commands in Spanish
Learn how to form affirmative and negative T commands in Spanish, including irregular forms and reflexive verbs. Understand the rules and exceptions for creating commands to communicate effectively in Spanish. Improve your command of the language with practical examples and tips for each type of com
0 views • 8 slides
Negative -T Commands in Spanish
Negative -T commands in Spanish are used to tell someone what not to do. These commands are often directed at friends or familiar individuals. Forming negative -T commands involves starting with the YO form in the present tense, dropping the O for -ER/-IR verbs, adding -ES for -AR verbs, and includi
0 views • 50 slides
Computer System Protection and Security
Mechanisms like protection and security ensure controlled access to a computer system's resources and prevent malicious activities. Protection involves defining access control levels through models, policies, and mechanisms. Security focuses on user authentication to safeguard stored information. Di
0 views • 25 slides
Introduction to Shell Programming in Linux/Unix with Vim and Control Flow Commands
Explore the basics of shell programming in Linux/Unix, including Vim commands for editing files, control flow commands like if-then statements, and examples of executing commands with built-in utilities. Learn how to handle arguments, read input, and implement conditional logic in scripts.
0 views • 47 slides
Microsoft Office Ribbon and its Features
Microsoft Office Ribbon organizes commands into tabs for easy access, allowing users to minimize, display, and restore the Ribbon as needed. Keyboard shortcuts via Key Tips provide quick access, while contextual tabs and Galleries offer specific commands and clear result options. Live Preview techno
0 views • 12 slides
Mastering AutoCAD Basics: Commands, Navigation, and Tools
Explore the fundamentals of AutoCAD with a focus on commands, navigation using mouse or digitizing tablet, and essential tools like Pan and Zoom. Learn how to efficiently type commands, utilize pointing devices, and shift views in this comprehensive guide.
0 views • 54 slides
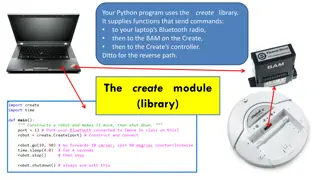
Python Create Library Overview
This Python program uses the Create library to send commands, enabling communication between your laptop's Bluetooth radio, the BAM on the Create robot, and the Create's controller. The library facilitates non-blocking commands for controlling the robot's movements and sensors, with specific instruc
0 views • 9 slides
Introduction to MATLAB Commands for Data Analysis in Geophysics
Learn how UNIX commands work in MATLAB, differentiate between MATLAB and UNIX commands, utilize MATLAB's help function, explore topics available for help, access help on individual commands, and create constant matrices in MATLAB for data analysis in geophysics.
0 views • 28 slides
Detailed Guide on BMC IPMI LED Control for RS500A-E11-RS12U
This detailed guide provides instructions on how to control BMC IPMI LEDs for RS500A-E11-RS12U server systems, including disabling BMC sensor scans, switching to manual mode, setting LED control commands, and more. Learn how to manipulate LED statuses, address settings, and light behaviors through I
0 views • 6 slides
Database Access Control & Privacy: A Common Ground Explored
Exploring the intersection of database access control and data privacy, this paper delves into the implications of data privacy concerns on Database Management Systems (DBMS). It discusses the need for more than just access control mechanisms and highlights the evolving landscape of data publishing,
0 views • 29 slides
Introduction to Basic UNIX Usage and Network Programming
In this course, you will learn the fundamentals of UNIX usage and network programming. Topics covered include basic UNIX commands, file system structure, UNIX shell functionalities, command line structure, and essential commands like passwd, ls, more, logout, date, and man. Understanding the hierarc
0 views • 31 slides
Control Plans in Process Management
Control plans are essential tools for managing process risks and ensuring quality control. They focus on controlling process and product characteristics, meeting customer requirements, and having reaction plans in place. A control plan contains key information such as control factors, specifications
1 views • 20 slides