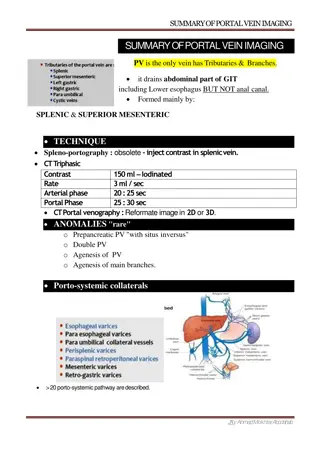
Enhancing Security with Two-Factor Authentication in Funding & Tenders Portal
Increase in cybersecurity threats necessitates the use of two-factor authentication in the Funding & Tenders Portal to safeguard valuable information. Users are encouraged to adopt this secure login method, which will soon become mandatory. Methods such as mobile devices, SMS, and security keys are recommended to strengthen user authentication and prevent unauthorized access.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
Funding & Tenders Portal Two-factor authentication Peter H rtwich European Commission DG R&I Business Processes RTD H3
2-factor authentication why? Threats to cybersecurity increase continuously, affecting all systems managing data and information that might be interesting for intruders The Funding & Tenders Portal hosts a wealth of interesting information that might be under threat if users do not take the necessary measures (commercially sensitive data in proposals, project reports, deliverables; personal data ) Simple user name and password provide only a minimum level of protection against intruders Strongly encouraged for all users to start using it now will become mandatory
Your EULogin account - basics One EULogin account = one user (natural person) Do not share your credentials (login,password) with others Inform the Commission immediately in case of theft or loss of your credentials F&T Portal Terms of Use
2-factor authentication how? Possible methods to use the 2-factor authentication: 1. Register a mobile device EU Login app 2. Register a mobile phone number 3. Register a security key / trusted platform 4. eID authentication Once enabled, each time you log in you will be prompted for username and password plus a second factor via your selected method See IT How To and video for detailed guidance
2-factor authentication two recommended options 1. Mobile device with EULogin app: Any device allowing the installation of an app (Android, iOS) and Internet access, no need for a mobile phone number/SIM card QR code scanning at each login 2. Mobile phone with SMS: simple mobile phone sufficient (no smartphone needed) Mobile phone number stored in your EULogin account is used exclusively for the two-factor authentication, will not be disclosed to anybody See IT How to and video for detailed guidance
2-factor authentication alternative options (if a user does not have or does not want to use a mobile device) USB security key Trusted platform on your computer eID (for users with national ID card providing such function)
USB security key A special USB device (to be purchased from a company offering such devices) This security key has to be registered with your EULogin account At each login, the key has to be plugged into your computer, providing the second factor
Register a Security Key You will see a pop-up window confirming that the security key will be used to authenticate for EU Login (with the email address of your EU Login account). You will be asked to allow ecas.ec.europa.eu (= the EU Login service) to access the manufacturing details of your key. If you have not inserted the key yet, insert it now before clicking OK. Click OK to confirm.
Register a Security Key Provide a PIN for your security key and click OK. Depending on the model, you will be requested to touch the key now. Your security key is now registered
Trusted platform An option in the operating system of your computer (most more recent computers/notebooks have the required hardware chip installed) Works with Windows and Mac Access to your computer/notebook must be secured itself (biometric or password) Device has to be registered with your EULogin account You can only log in to your EULogin account from this computer/notebook
Register a Trusted Platform Your trusted platform is now registered
4. eID authentication Use your national ID eCard as second factor (if equipped for this; currently only possible for 16 member states) The process to confirm the registration or login happens in the country- specific website or with the specific eID solution of your country. Please refer to your country eID support for guidance on the specific steps to follow. The option usually implies using additional hardware (i.e. a card reader). More information on eID: https://ec.europa.eu/digital-building- blocks/wikis/display/DIGITAL/eID
Switch on the two-factor authentication in the F&T Portal
Login when two-factor authentication is enabled
More information IT Support in FTOP: Two-factor authentication in the Funding & Tenders Portal - IT How To
Number of two-factor users 18000 16000 14000 12000 10000 8000 6000 4000 2000 0 Still less than 1% of all users!