Enhancing Access to Medicines and Health Products through Innovative Approaches
Global Health Centre experts discuss how building access into innovation can ensure better access to medicines, vaccines, and health products. Key ideas include planting seeds for access early in innovation, exploring alternative innovation models, and rethinking the relationship between innovation
4 views • 20 slides
2022 Thales Access Management Index
Thales Access Management Index highlights the current landscape of access security, revealing insights on multi-factor authentication adoption, remote and privileged user access management, VPN usage trends, challenges faced, and preferences towards third-party access management. The report emphasiz
2 views • 9 slides
Guidelines for Expanded Access to Investigational Drugs and Devices
Providing guidance on types of Expanded Access for drugs, biologics, and devices, this content explains the concept of Expanded Access and the criteria that must be met. It covers different types of Expanded Access for drugs and devices, emphasizing the importance of patient safety and benefit. The
0 views • 10 slides
Personnel Safety Systems and Access Control at CERN Facilities
Personnel Safety Systems at CERN include ODH detection, fire safety measures, and access control to protect personnel from hazards. Various access control layers are implemented to regulate entry to different parts of the facility, ensuring only trained personnel access underground areas. Biometric
0 views • 19 slides
Port of Stockton Restricted Area Access Control and ID Card Policy
Access to restricted areas at the Port of Stockton facilities requires possession of a TWIC (Transportation Worker Identification Credential). Only authorized personnel, such as employees, contractors, and those with regular access, may receive a Port Access Card after approval by the Facility Secur
0 views • 6 slides
ConCORD: Exploiting Memory Content Redundancy Through Content-aware Services
Memory content-sharing detection and tracking are crucial aspects that should be built as separate services. ConCORD, a distributed system, efficiently tracks memory content across entities like VMs and processes, reducing memory footprint size and enhancing performance. The implementation involves
0 views • 56 slides
Understanding Content Management Systems
Content Management Systems (CMS) are computer applications that enable easy publishing, editing, and management of content on websites. They help in organizing, maintaining, and updating content efficiently from a centralized interface. With features like web-based publishing, revision control, and
4 views • 10 slides
Introduction to Database Security and Countermeasures
Database security is essential to protect data integrity, availability, and confidentiality. Countermeasures such as access control, inference control, flow control, and encryption can safeguard databases against threats. Access control restricts user access, inference control manages statistical da
0 views • 26 slides
O3 Access Control Solution Overview
O3 Access Control Solution offers unique selling points like single-seat management software, role-based permissions, customizable user information, and more. The system includes a compact controller with multi-format reader support and BACnet Access objects. It integrates with other O3 modules for
0 views • 10 slides
Open Access Publishing and EIS Programme at Pázmány University: Empowering Research and Scholarly Communication
Discover the advantages of Open Access (OA) publishing and how researchers benefit from immediate accessibility, increased discoverability, and global readership. Learn about the EIS Programme at Pázmány University, a member institution dedicated to providing essential electronic resources for hig
0 views • 12 slides
Green Open Access in Finland: Why, What, and How?
This presentation discusses the importance of Green Open Access in Finland, exploring the reasons behind its adoption, different access models like Gold OA and self-archiving, and the role of university libraries in supporting and centralizing Green OA practices. It also touches upon the European Un
2 views • 17 slides
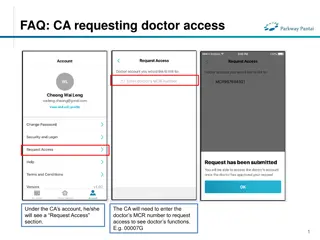
FAQs for Doctor and Clinical Assistant (CA) Account Access Management
Learn how CAs can request access to doctors' functions by entering the MCR number, how doctors can grant or remove CA access, and how CAs can manage access to multiple doctors. The process includes requesting, approving, and unlinking accounts, ensuring efficient and secure access management in a cl
0 views • 4 slides
EventsHQ Virtual Event Registration: User Access and Setup Guide
This comprehensive guide provides step-by-step instructions on setting up virtual event registration using EventsHQ. It covers how users can access event details, join the event, and includes best practices for sharing access links. Learn how to utilize the Virtual Event Details feature, send remind
1 views • 19 slides
Putting Content First for Effective User Experiences
Content is king in creating meaningful user experiences. Emphasizing content over design and incorporating change management can lead to smoother processes and better user satisfaction. Experts highlight the importance of focusing on content before design, debunking assumptions about content's role,
0 views • 46 slides
Television Content Regulation in Australia
Television content regulation in Australia is overseen by industry-developed codes of practice and specific licence conditions under the Broadcasting Services Act 1992. TV stations hold the primary responsibility to ensure that programs reflect community standards. Regulations cover areas such as to
0 views • 12 slides
Open Access in Action Conference Overview
The Conference Open Access in Action on October 19, 2020, highlights the Open Science Programme, National Open Access Strategy, and Action Plan 2018-2024. It covers topics like Open Research Data, the future Strategy & Action Plan, and the drive towards free access to publicly funded research public
1 views • 29 slides
Accessible Voting System for Californians with Disabilities
Learn about the Remote Accessible Vote-by-Mail System in California, designed to empower voters with disabilities to securely access, mark, and return their ballots from any computer with internet access. Find out who is eligible to use the system, how to access and return the ballot, and the steps
0 views • 23 slides
Dell Networking Solutions for BYOD and Guest Access Projects
Dell offers end-to-end solutions for Bring-Your-Own-Device (BYOD) and guest access projects, enabling secure employee access and controlled connectivity for visitors. The framework includes mobility business models, device security, network protection, and scalability. Dell supports customers in imp
0 views • 11 slides
The Significance of B2B Content Marketing Transformation
In the evolving B2B marketing landscape, content has become crucial. By 2020, customers will engage with enterprises largely through digital means. B2B companies must embrace a content-centric approach to keep up with changing buyer behaviors. Utilizing content calendars, managing websites and blogs
0 views • 18 slides
Open Access Books and Library Membership: Enhancing Global Research Accessibility
Explore how Open Book Publishers (OBP) and EIFL collaborate to provide free access to scholarly resources for libraries in non-OECD countries, promoting global research accessibility. Discover the benefits of OBP's Library Membership Programme, offering discounts and comprehensive ebook access, revo
0 views • 20 slides
Overview of MPDI Training Session: Access, Security, and Reporting
The provided content gives an in-depth look at the MPDI Training session, covering topics such as the objective of the training, background of the change from ACS to MPDI, system access and security, data collection timeframes, dashboard setup, and new Employee FTE module. It details the reasons beh
0 views • 18 slides
Role-based Access Control Policies and Security Properties Overview
This content provides an overview of Role-based Access Control (RBAC) policies, Administrative RBAC (ARBAC) systems, and security properties in the context of access control in large organizations. It discusses the implementation of RBAC in various software systems, the assignment and revocation of
0 views • 18 slides
Open Access at Charles University: Opportunities and Challenges
Charles University is navigating the landscape of open access following the implementation of the Czech National Open Access Strategy. The university is working towards making all research articles and proceeding papers open access, monitoring article processing charges, and promoting open access as
0 views • 24 slides
Understanding Filesystem Security Principles and Access Control
Learn about filesystem security, general principles, discretionary access control (DAC), closed vs. open policy, closed policy with negative authorizations, and access control entries and lists. Discover how files and folders are managed, the role of access control lists (ACLs), and the different le
1 views • 56 slides
Understanding Ethernet and Multiple Access Protocols in Computer Networks
Exploring the fundamentals of Ethernet and multiple access protocols in computer networks, this content discusses the two primary categories of multiple access protocols - contention access and controlled access. It delves into topics such as CSMA/CD, LANs, performance of multiple access schemes, ad
0 views • 7 slides
Understanding Shared Memory, Distributed Memory, and Hybrid Distributed-Shared Memory
Shared memory systems allow multiple processors to access the same memory resources, with changes made by one processor visible to all others. This concept is categorized into Uniform Memory Access (UMA) and Non-Uniform Memory Access (NUMA) architectures. UMA provides equal access times to memory, w
0 views • 22 slides
Resources for SharePoint Designers: Enhancing Web Content
Explore valuable resources for SharePoint designers to improve web content creation, including SharePoint Help site, SharePoint Work Zone, writing tips for the web, and guidelines for user-friendly content. Gain insights on effective web writing practices and access training environments for practic
0 views • 12 slides
Understanding Access Changes and Community Relations at Fermilab
Access to Fermilab has become more complicated due to changing DOE guidance and security posture. Efforts are being made to streamline access while addressing security gaps. Public access to outdoor areas of the Fermilab campus is still encouraged, but communication regarding access changes needs im
0 views • 12 slides
Understanding Computer System Protection and Security
Mechanisms like protection and security ensure controlled access to a computer system's resources and prevent malicious activities. Protection involves defining access control levels through models, policies, and mechanisms. Security focuses on user authentication to safeguard stored information. Di
0 views • 25 slides
Understanding Access to ITU Information and Documents
Exploring the concept of access in the work of a dedicated group, this content delves into the types of information that could or should be made available to the public, along with considerations on when access should be provided. It highlights the varying stages of information dissemination, discus
0 views • 8 slides
Harvard Chan School 2021 Yearly Access Review Process
The Harvard Chan School conducts its annual Yearly Access Review (YAR) process to review user access to various financial systems. The process involves assessing permissions, levels of access, and organizational details for each team member. Instructions are provided on reviewing worksheets, adding
0 views • 19 slides
Understanding Security Access in PeopleSoft Finance
Explore the various levels of security access in PeopleSoft Finance, from basic entry access to transaction entry, approvals, and procurement processes. Learn how to request individual and department security access and find relevant forms on the financial services website. Discover the different ty
0 views • 11 slides
Proxy Access to Medications Implementation Stages
This document outlines the implementation stages for proxy access to medications. It covers agreements with healthcare providers, prerequisites including compliance and data sharing agreements, and systems configuration for access to medical records. The stages include setting up access for care pro
0 views • 7 slides
CSUEB Academic Access Enhancement and Excellence Fee Proposal
The CSUEB Academic Access Enhancement and Excellence Fee Proposal aims to enhance the academic environment, reduce student costs, and provide equal access to educational materials. Components include an Academic Access Enhancement fund, e-textbooks program, and provision of tablets/netbooks to all i
0 views • 23 slides
Publishing Requirements and Challenges in Horizon Europe
The publication landscape under Horizon Europe presents challenges regarding compliance with publishing fee eligibility for hybrid journals and embargoes for open access. Hybrid journals feature subscription-based and open access parts, while open access journals require authors to pay open access f
0 views • 6 slides
Enhancing Born-Digital Content Access
Explore methods and policies for accessing born-digital content, including pre-accession documentation, security measures, and tools for rendering file formats. Learn about the OAIS model, levels of access, and collaboration with third-party platforms like Europeana. Enhance researcher support and d
0 views • 12 slides
Insights from LYRASIS Leadership Forum 2016
Delve into discussions from the LYRASIS Leadership Forum 2016 covering topics such as content creation, open access, library roles, commercial content hosting, and open source software trends. Key questions raised include shifts in organizational priorities, support for open access content, interdep
0 views • 28 slides
Best Practices for Transradial Angiography and Intervention
This update highlights best practices for transradial angiography and intervention, including topics such as ultrasound guidance for transradial access, ulnar artery access recommendations, and future study opportunities. The importance of developing proficiency with ultrasound guidance, utilizing r
0 views • 15 slides
Challenges and Importance of Government Access to Personal Data in Cross-Border Intelligence Oversight
Reflecting on the significance of the OECD Declaration on Government Access to Personal Data held by Private Sector Entities, this content delves into the drivers necessitating an OECD-type process, such as law enforcement needs, globalization of criminal evidence, and convergence of civilian commun
0 views • 8 slides
Evolution of Access Management in the 21st Century: RA21 Initiative
RA21, a joint initiative of STM Publishers and NISO, addresses the challenges of IP-based access management in the digital age. It aims to enhance user experience by optimizing access protocols across different stakeholder groups. The evolution from print to digital formats has led to the need for n
0 views • 12 slides