Addressing 5G Signaling Protocol Vulnerabilities
The 8th meeting of the Communications Security, Reliability, and Interoperability Council to discuss and address security vulnerabilities in the newly adopted 5G signaling protocol, HTTP/2. Learn about potential risks, recommended safeguards, and the prevention of these vulnerabilities in the upcomi
3 views • 85 slides
Apache MINA: High-performance Network Applications Framework
Apache MINA is a robust framework for building high-performance network applications. With features like non-blocking I/O, event-driven architecture, and enhanced scalability, MINA provides a reliable platform for developing multipurpose infrastructure and networked applications. Its strengths lie i
3 views • 13 slides
Modeling and Generation of Realistic Network Activity Using Non-Negative Matrix Factorization
The GHOST project focuses on the challenges of modeling, analyzing, and generating patterns of network activity. By utilizing Non-Negative Matrix Factorization (NMF), realistic network activity patterns can be created and injected into live wireless networks. Understanding and predicting user behavi
4 views • 28 slides
Automated Anomaly Detection Tool for Network Performance Optimization
Anomaly Detection Tool (ADT) aims to automate the detection of network degradation in a mobile communications network, reducing the time and effort required significantly. By utilizing statistical and machine learning models, ADT can generate anomaly reports efficiently across a large circle network
8 views • 7 slides
Understanding Vulnerabilities of Individuals with Autism in Disciplinary Hearings and Employment Tribunals
People with autism may face vulnerabilities in disciplinary proceedings and employment tribunals due to impaired theory of mind, communication difficulties, insistence on sameness, stereotyped behaviors, and sensory sensitivities. These challenges can lead to misunderstandings, difficulties in copin
0 views • 10 slides
Network Compression Techniques: Overview and Practical Issues
Various network compression techniques such as network pruning, knowledge distillation, and parameter quantization are discussed in this content. The importance of pruning redundant weights and neurons in over-parameterized networks is highlighted. Practical issues like weight pruning and neuron pru
0 views • 37 slides
Network Slicing with OAI 5G CN Workshop Overview
Overview of Network Slicing with OAI 5G CN workshop focusing on the crucial role of network slicing in realizing the service-oriented 5G vision. This workshop covers topics like multiple logical networks creation on shared infrastructure, different types of network slices, preparation and instantiat
1 views • 6 slides
Understanding Snort: An Open-Source Network Intrusion Detection System
Snort is an open-source Network Intrusion Detection System (NIDS) developed by Cisco, capable of analyzing network packets to identify suspicious activities. It can function as a packet sniffer, packet logger, or a full-fledged intrusion prevention system. By monitoring and matching network activity
0 views • 23 slides
Understanding Buffer Overflow Vulnerabilities in Programming
Buffer overflow vulnerabilities pose serious security threats by allowing attackers to execute arbitrary code on victim machines. This issue arises from overwriting memory in a way that manipulates the program's behavior. Learn about the dangers of buffer overflow bugs, how they can be exploited, an
2 views • 33 slides
Software Security Principles and Practices: Enhancing Program Code Security
Understanding and addressing critical web application security flaws like unvalidated input, cross-site scripting, buffer overflow, injection flaws, and improper error handling is crucial in enhancing the security of program code. The NIST report NISTIR 8151 provides valuable recommendations to redu
2 views • 44 slides
Understanding Computer Security and Software Vulnerabilities
Computer security, also known as cybersecurity or IT security, encompasses the protection of information systems from theft and damage. This overview delves into software security, control-flow attacks, memory vulnerabilities, and the historical impact of events like the Morris Worm. Various aspects
0 views • 53 slides
Overview of Global Farmed Salmon and Organic Production
The data showcases the production figures for global farmed salmon across various countries, with Norway leading the production, followed by Chile, Scotland, and others. Additionally, insights into the growing organic salmon production, vulnerabilities in the sector, and details on organic mussels p
0 views • 9 slides
Analysis of file:// Vulnerabilities in Android Browser Apps
The study delves into file:// vulnerabilities in Android browser apps, uncovering risks posed by the file:// URI scheme. It highlights how file:// requests can breach app data isolation, potentially compromising sensitive files. The research presents a unified attack model, FileCross automated testi
0 views • 22 slides
Transportation Network Modeling and Analysis with C.Coupled SE Platform
This content outlines the features and functionalities of the C.Coupled SE Platform (CSET Platform) developed by the Connetics Transportation Group. It covers aspects such as interface design, inputs merging, purposes, platform development using Cube, TAZs merging, and network attributes. The platfo
0 views • 11 slides
Understanding Wireless Network Threats and Vulnerabilities
Explore the various threats and vulnerabilities present in wireless networks, including different types of attackers, weaknesses in WLAN security standards, such as WEP, and the risks associated with Bluetooth and Ad Hoc networks. Learn about the profiles of cyber attackers and the importance of imp
2 views • 20 slides
Understanding BGP and DNS Worms in Network Security
Border Gateway Protocol (BGP) is crucial for network communication, allowing autonomous systems to exchange routing information. BGP works by announcing network ownership and directing traffic efficiently. However, BGP Blackhole attacks pose a threat, where malicious entities reroute traffic to disr
0 views • 37 slides
Automated Detection of SSL Vulnerabilities in Applications
This research introduces SSLint, a systematic approach and automated tool for detecting incorrect SSL API usage vulnerabilities in applications. By analyzing millions of lines of code, the tool discovered previously unknown SSL/TLS vulnerable apps. The study addresses the motivation, problem stateme
0 views • 29 slides
Analysis of Network Coordinate Systems and Security Vulnerabilities
This presentation explores the concept of network coordinate systems, their limitations, efficient measurement of distance between nodes, and existing systems like Vivaldi and Pyxida. It delves into embedding errors in network coordinates, updates to reduce errors, secure mechanisms like Mahalanobis
0 views • 23 slides
Server-Side Technologies and Security Vulnerabilities in Mobile Services
This content delves into server-side technologies such as SQL, SOAP, JSON, and ReST used in mobile services, highlighting vulnerabilities that expose sensitive data. It emphasizes the importance of general web service security guidelines and discusses attacks against XML-based web services, outlinin
0 views • 52 slides
Understanding Blockchain Vulnerabilities to Quantum Attacks
Explore the vulnerabilities of blockchains to quantum attacks and the potential impact of quantum devices on blockchain technologies. Learn about key concepts such as blockchain basics, proof-of-work, quantum computing, quantum computing algorithms, and vulnerabilities like ECDSA and peer-to-peer ne
0 views • 23 slides
Meridian: An SDN Platform for Cloud Network Services
Meridian is an SDN platform developed by Mohammad Banikazemi, David Olshefski, Anees Shaikh, John Tracey, and GuohuiWang at IBM T. J. Watson Research Center. The platform focuses on providing cloud network services efficiently. It encompasses an architecture that enables faster and more convenient n
0 views • 21 slides
Understanding Security Threats and Vulnerabilities in Computer Systems
In computer security, threats exploit vulnerabilities to breach security and cause harm. Vulnerabilities arise from system weaknesses, attacker access, and capability. Threats include spoofing, data tampering, repudiation, information disclosure, denial of service, and elevation of privilege. Catego
0 views • 13 slides
Understanding the Importance of OWASP Dependency-Check Project
Explore the significance of OWASP Dependency-Check in managing software dependencies and mitigating known vulnerabilities in applications. Learn about the risks associated with using components with vulnerabilities and the challenges of patching programs. Discover how OWASP Dependency-Check provides
1 views • 26 slides
Data Disaggregation Taskforce: Assessment and Recommendations on Vulnerabilities
The Data Disaggregation Taskforce is conducting an assessment of current practices across sectors, assessing 10 sectors/clusters, 15 categories of affected populations, and identifying vulnerabilities in 17 categories. The Taskforce is working on harmonizing categories and finalizing recommendations
0 views • 6 slides
Understanding Spectre and Meltdown Security Vulnerabilities
Spectre and Meltdown are two critical security vulnerabilities that exploit microarchitectural features to gain unauthorized access to memory. These vulnerabilities enable attackers to read memory that should be inaccessible, targeting branch prediction and exception handling mechanisms. Side channe
0 views • 19 slides
Understanding Cloud Security Threats and Vulnerabilities
Explore the world of cloud security through the eyes of Dr. Liang Zhao, focusing on mobile security, WLAN security, and cloud threats. Learn about threat modeling, mitigating cloud vulnerabilities, and common threats such as data leakage, insecure interfaces, and more. Discover practical threat anal
0 views • 18 slides
Understanding Network Analysis: Whole Networks vs. Ego Networks
Explore the differences between Whole Networks and Ego Networks in social network analysis. Whole Networks provide comprehensive information about all nodes and links, enabling the computation of network-level statistics. On the other hand, Ego Networks focus on a sample of nodes, limiting the abili
0 views • 31 slides
Proactive Network Protection Through DNS Security Insights
Exploring proactive network protection methods using DNS, security challenges, botnet threats, firewall management, malware controls, and DNS-based malware control. Discussions on DNS security vulnerabilities, DNSSEC, threat intelligence, machine learning, and best practices like RPZ for DNS protect
0 views • 29 slides
Understanding Network Security Vulnerabilities and Attacks
Explore the world of network security vulnerabilities and attacks, including Denial-of-Service (DoS) and Distributed-Denial-of-Service (D-DoS), security flaws in the TCP/IP protocol suite, ICMP attacks, routing attacks, and TCP attacks. Learn about common security vulnerabilities such as address spo
0 views • 36 slides
Understanding Web Application Vulnerabilities in Information Warfare
Web application vulnerabilities such as Cross-Site Scripting, SQL Injection, and Broken Authentication pose significant risks in information warfare. Current solutions include Black-Box Security Testing and XSS Analyzers, but they have limitations like static verification and dependence on security
0 views • 21 slides
Understanding Programming Language Vulnerabilities and ISO/IEC/SC22/WG23
Explore the history and evolution of ISO/IEC/SC22/WG23 focusing on programming language vulnerabilities, led by Stephen Michell. Learn about the formation in 2006, publications, identified vulnerabilities, and the upcoming Edition 3 outlook with language-specific annexes. Discover comparisons with A
0 views • 15 slides
Basic Web Security Model for Secure Electronic Commerce
This presentation covers the basic web security model for secure electronic commerce, focusing on vulnerabilities such as XSS and SQL injection. It discusses the decline in web vulnerabilities since 2009 and explores reported web vulnerabilities. The course theme includes topics like web application
0 views • 38 slides
Enhancing Tor Network Security and Performance with Tunable Path Selection
This presentation discusses the improvement of security and performance within the Tor network through tunable path selection. It covers Tor's design, proposed methods for bandwidth measurement, router selection algorithms, and the evaluation of different strategies to enhance the network's efficien
0 views • 29 slides
Network Function Virtualization (NFV) Overview
Network Function Virtualization (NFV) focuses on virtualizing network functions to improve efficiency and reduce costs in network infrastructure. The lecture discusses key readings, devices that compose a network, specialization of devices, benefits of one-device-does-anything approach, and the goal
0 views • 21 slides
Enhancing Network Stability with Network Monitoring Systems
Network monitoring is crucial for efficient management and proactive issue detection in a network environment. Factors influencing an effective network system include choosing the best OEM, SLA agreements, and selecting a reliable System Integrator. Reactive monitoring can lead to financial losses a
0 views • 12 slides
Understanding Network Security Part 2: Link Layer and ARP
Exploring the vulnerabilities in simple network topologies with hubs and the need for examining the link layer to prevent eavesdropping. Dive into MAC addresses, ARP (Address Resolution Protocol), and how machines translate IP addresses to physical Ethernet addresses. Learn about ARP tables, the tra
0 views • 61 slides
Understanding Spectre and Meltdown Security Flaws
Recent security vulnerabilities named Spectre and Meltdown have surfaced in the realm of computer architecture and hardware implementation. These flaws allow attackers to access sensitive data through covert channels utilizing speculative execution mechanisms. The vulnerabilities exploit the perform
0 views • 12 slides
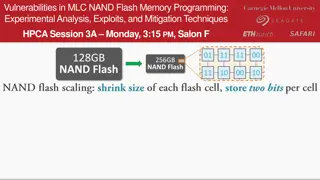
Experimental Analysis of Vulnerabilities in MLC NAND Flash Memory Programming
This session at HPCA explores the experimental analysis, exploits, and mitigation techniques related to vulnerabilities in MLC NAND flash memory programming. The presentation delves into the risks associated with NAND flash memory, such as data corruption and errors during read operations. It discus
0 views • 10 slides
Accelerating Systemic Change Network Inaugural Workshop Summary
The Accelerating Systemic Change Network held its inaugural workshop at Howard Hughes Medical Institute in July 2016 to address the lack of coordination in improving higher education. With a vision to become a professional hub for change researchers in STEM education, the network aims to enhance ind
0 views • 5 slides
University Network Section Overview July 2015 - March 2016
The presentation covers the network team structure, team members, objectives, goals, report outline, network statistics, accomplishments, and future plans of the university network section from July 2015 to March 2016. It highlights efforts to provide stable internet and intranet services, restructu
0 views • 16 slides