Incomplete Registrations
Learn the criteria for incomplete voter registration applications, including missing applicant details and signatures. Discover what actions are needed to rectify incomplete applications for successful voter registration.
0 views • 11 slides
KINDLE Autograph Book 2023: Vacation Trips with Children Family & Friends . Cele
\"http:\/\/softebook.net\/B0BMSKNP9V\/Autograph Book 2023: Vacation Trips with Children Family & Friends . Celebrities Signatures Keep all Album Fun For Kids, Girls & Boy.pdf\n\"\n
1 views • 1 slides
Information Security – Theory vs. Reality
Exploring the concept of fault attacks in hardware security, this lecture delves into the various techniques used to compromise systems through non-nominal and nominal channels, as well as the potential risks introduced by trojan horses in the IT supply chain. The discussion includes differential fa
1 views • 37 slides
Adversarial Machine Learning in Cybersecurity: Challenges and Defenses
Adversarial Machine Learning (AML) plays a crucial role in cybersecurity as security analysts combat continually evolving attack strategies by malicious adversaries. ML models are increasingly utilized to address the complexity of cyber threats, yet they are susceptible to adversarial attacks. Inves
1 views • 46 slides
Ensuring Integrity: Signature Verification in Mail-In Voting
Kane County Clerk's Office employs certified forensic document examiners for manual verification of signatures on mail-in ballot envelopes, emphasizing the challenges and importance of ensuring authenticity in the voting process. Learn about the technology and processes involved in signature authent
3 views • 28 slides
Multivariate Analysis
Explore the key concepts of marginal, conditional, and joint probability in multivariate analysis, as well as the notion of independence and Bayes' Theorem. Learn how these probabilities relate to each other and the importance of handling differences in joint and marginal probabilities.
5 views • 43 slides
Understanding Multidimensional Scaling and Unsupervised Learning Methods
Multidimensional scaling (MDS) aims to represent similarity or dissimilarity measurements between objects as distances in a lower-dimensional space. Principal Coordinates Analysis (PCoA) and other unsupervised learning methods like PCA are used to preserve distances between observations in multivari
0 views • 21 slides
Compact Ring Signatures from LWE - CRYPTO 2021 Research
Research presented at CRYPTO 2021 introduces a compact ring signature scheme using components instantiated from LWE. The scheme allows each signer to sign on behalf of a ring of users, offering properties of unforgeability, anonymity, and compactness. The work explores the possibility of building co
0 views • 25 slides
Understanding Multivariate Binary Logistic Regression Models: A Practical Example
Exploring the application of multivariate binary logistic regression through an example on factors associated with receiving assistance during childbirth in Ghana. The analysis includes variables such as wealth quintile, number of children, residence, and education level. Results from the regression
0 views • 19 slides
Parallel Implementation of Multivariate Empirical Mode Decomposition on GPU
Empirical Mode Decomposition (EMD) is a signal processing technique used for separating different oscillation modes in a time series signal. This paper explores the parallel implementation of Multivariate Empirical Mode Decomposition (MEMD) on GPU, discussing numerical steps, implementation details,
1 views • 15 slides
Understanding MANOVA: Multivariate Analysis of Variance
MANOVA, an extension of ANOVA, deals with multiple dependent variables simultaneously to test mean differences across groups. Types of MANOVA include one-way between/within subjects and mixed MANOVA. An example explores the effects of coffee consumption on anxiety and fatigue levels. SPSS data files
1 views • 33 slides
Understanding DocuSign Legal Binding Authority for INDOT LPA Programs
This document explains the process of using DocuSign for electronically signing INDOT LPA Contracts and Local Roads and Bridges Matching Grant Agreements. It covers the definition of Legal Binding Authority, requirements for legal signatures per contract, instructions for providing signer informatio
0 views • 18 slides
Understanding Multivariate Normal Distribution and Simulation in PROC SIMNORM
Explore the concepts of multivariate normal distribution, linear combinations, subsets, and variance-covariance in statistical analysis. Learn to simulate data using PROC SIMNORM and analyze variance-covariance from existing datasets to gain insights into multivariate distributions. Visualize data t
0 views • 16 slides
Performance of Post-Quantum Signatures: Analysis and Comparison
Explore the performance and characteristics of various post-quantum signature schemes including Lattice-based Dilithium, QTesla, Falcon, Symmetric Sphincs+, Picnic, Multivariate GEMSS, Rainbow, and more. Understand the implications of using these schemes in TLS, code signing, firmware updates, signe
0 views • 29 slides
Optimization Methods: Understanding Gradient Descent and Second Order Techniques
This content delves into the concepts of gradient descent and second-order methods in optimization. Gradient descent is a first-order method utilizing the first-order Taylor expansion, while second-order methods consider the first three terms of the multivariate Taylor series. Second-order methods l
0 views • 44 slides
Understanding MANOVA: Mechanics and Applications
MANOVA is a multivariate generalization of ANOVA, examining the relationship between multiple dependent variables and factors simultaneously. It involves complex statistical computations, matrix operations, and hypothesis testing to analyze the effects of independent variables on linear combinations
0 views • 16 slides
Determinants of Growth in Micro & Small Enterprises: Empirical Evidence from Jordan
Jordanian micro and small enterprises (MSEs) play a significant role in the economy but face challenges in accessing markets and obtaining finance. A research study was conducted in Jordan to analyze the factors influencing the growth of MSEs, including formality, education level of owners, technolo
0 views • 8 slides
Rainbow Signatures Overview and New Attacks
Rainbow signatures, introduced in 2005, offer good performance with small signatures but raise concerns due to large key sizes. This article explores the history of Rainbow, its vulnerabilities, new attacks, and the challenges posed by multivariate trapdoors. The overview delves into practical impli
0 views • 20 slides
Machine Learning for Molten Salt Reactor Safeguards
Molten salt reactors face challenges in material accounting due to liquid fuel which precludes traditional safeguards. This project proposes a two-step approach involving the development of measurement signatures created by material diversion, and a machine learning model to distinguish normal react
1 views • 18 slides
Comprehensive Malware Analysis Techniques
This detailed guide covers basic static techniques, malware analysis in virtual machines, and basic dynamic analysis. It includes information on static analysis, such as examining payloads without execution, file signatures, and signatures generated via analysis. Additionally, it delves into counter
0 views • 17 slides
Statistical and Quantitative Genetics of Disease
This session covers single locus analysis in statistical and quantitative genetics, focusing on design, analysis, logistic regression, covariates, and multivariate analysis. It discusses approaches for analyzing DNA on cases and controls, modeling, and adjusting for covariates. The association analy
0 views • 36 slides
Understanding Multivariate Statistics: Regression, Correlation, and Prediction Models
Explore the differences between regression and correlation, learn about compensatory prediction models, understand the role of suppressor and moderator variables, and delve into non-compensatory models based on cutoffs in multivariate statistics.
0 views • 9 slides
Understanding Homomorphic Signatures and Fully Homomorphic Encryption
Explore the concepts of homomorphic signatures, fully homomorphic encryption, and their unified construction as they relate to security and authenticity in data processing. Learn about commitments, extractable commitments, and equivocal commitments in the context of encryption and signatures.
0 views • 26 slides
Limits on the Efficiency of Ring LWE-based Key Exchange
This study explores the limitations of Ring LWE-based key exchange protocols and their impact on non-interactive key exchange mechanisms. It discusses the LWE assumption, noise distribution, and the practical implications of small moduli q and noise-to-modulus ratio r. Additionally, it delves into P
0 views • 71 slides
Digital Signatures in Legislation: Estonia's Electronic Process
Estonia's legislative process embraces digital signatures, starting with coordination by various institutions and concluding with the enactment of laws electronically. The process involves e-consultation, government systems, digital signing of draft legislation, and ID-card authentication. The final
0 views • 10 slides
Distinctive Signatures of Climate on Land Form
Climate can leave unique imprints on land forms, both at fine and large scales. Examples include relict topography shaped by past climates and the influence of climate zonation on the Andes' shape. Erosional processes and glacial activities also play significant roles in shaping Earth's surface feat
0 views • 40 slides
Lower Bounds for Small Depth Arithmetic Circuits
This work explores lower bounds for small-depth arithmetic circuits, jointly conducted by researchers from MSRI, IITB, and experts in the field. They investigate the complexity of multivariate polynomials in arithmetic circuits, discussing circuit depth, size, and the quest for an explicit family of
0 views • 114 slides
Automated Signature Extraction for High Volume Attacks in Cybersecurity
This research delves into automated signature extraction for high-volume attacks in cybersecurity, specifically focusing on defending against Distributed Denial of Service (DDoS) attacks. The study discusses the challenges posed by sophisticated attackers using botnets and zero-day attacks, emphasiz
0 views • 37 slides
Canine CSF Proteomic Profiling for Non-Infectious Meningoencephalitis Biomarker Discovery
This study focuses on using mass spectrometry to analyze cerebrospinal fluid (CSF) proteomics in dogs with non-infectious meningoencephalitis, aiming to identify unique peptide signatures for improved diagnosis and monitoring. The research addresses the diagnostic and therapeutic limitations of this
0 views • 16 slides
Comprehensive Guide to Task Briefing Sheets in Construction
A Task Briefing Sheet (TBS) is an essential document for frontline workers in construction, outlining the work to be done, available resources, health and safety measures, and emergency arrangements. Updated requirements include reflecting changes in CDM 2015, using specific plan templates, and issu
0 views • 20 slides
Proposal for Enhancing S-63 Cybersecurity Management
This proposal suggests amendments to S-63 to address cybersecurity issues in maritime navigation systems. It discusses the current digital signature encoding, importance of trusted digital signatures, and mechanisms for supporting digital signing in exchange sets. The document outlines the use of en
0 views • 13 slides
PySAT Point Spectra Tool: Spectral Analysis and Regression Software
PySAT is a Python-based spectral analysis tool designed for point spectra processing and regression tasks. It offers various features such as preprocessing, data manipulation, multivariate regression, K-fold cross-validation, plotting capabilities, and more. The tool's modular interface allows users
0 views • 6 slides
Understanding DNSSEC: Adding Digital Signatures to DNS Responses
DNSSEC (Domain Name System Security Extensions) allows for the addition of digital signatures to DNS responses, ensuring the authenticity, completeness, and currentness of the data received by a client. By validating the digital signature, clients can trust the response received is genuine and unalt
0 views • 27 slides
Optical Signatures of Climate Change Impacts on Phytoplankton
Explore the optical signatures of climate change impacts on phytoplankton through images showing differences in primary production, reflectance ratios, community changes, and trends in various oceanic regions. The data visualizations provide insights into the effects of climate change on phytoplankt
0 views • 10 slides
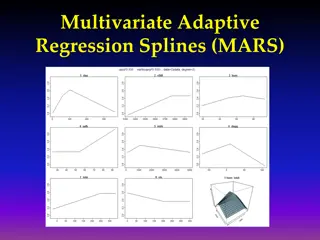
Understanding Multivariate Adaptive Regression Splines (MARS)
Multivariate Adaptive Regression Splines (MARS) is a flexible modeling technique that constructs complex relationships using a set of basis functions chosen from a library. The basis functions are selected through a combination of forward selection and backward elimination processes to build a smoot
0 views • 13 slides
Quasi-Interpolation for Scattered Data in High Dimensions: Methods and Applications
This research explores the use of quasi-interpolation techniques to approximate functions from scattered data points in high dimensions. It discusses the interpretation of Moving Least Squares (MLS) for direct pointwise approximation of differential operators, handling singularities, and improving a
0 views • 9 slides
Advanced Techniques in Multivariate Approximation for Improved Function Approximation
Explore characteristics and properties of good approximation operators, such as quasi-interpolation and Moving Least-Squares (MLS), for approximating functions with singularities and near boundaries. Learn about direct approximation of local functionals and high-order approximation methods for non-s
0 views • 9 slides
Multivariate Adaptive Regression Splines (MARS) in Machine Learning
Multivariate Adaptive Regression Splines (MARS) offer a flexible approach in machine learning by combining features of linear regression, non-linear regression, and basis expansions. Unlike traditional models, MARS makes no assumptions about the underlying functional relationship, leading to improve
0 views • 42 slides
Analyzing Improved Cryptanalysis of UOV and Rainbow Signature Algorithms
In this detailed study, the cryptanalysis of UOV and Rainbow signature algorithms by Ward Beullens is explored, focusing on key recovery attacks and the trapdoor structures of Oil & Vinegar and Rainbow schemes. The research highlights the complexities involved in deciphering these multivariate quadr
0 views • 11 slides
Understanding Multivariate Cryptography Schemes
Multivariate cryptography involves systems of polynomial equations, with public keys based on polynomial functions. GeMSS and Rainbow are discussed, highlighting their design features and vulnerabilities. The Butterfly Construction method in multivariate schemes constructs public keys using easily i
0 views • 33 slides