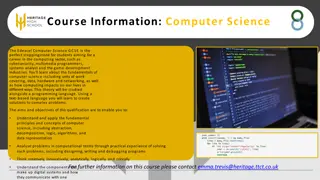
Explore Edexcel Computer Science GCSE Course Information
The Edexcel Computer Science GCSE is an ideal pathway for students interested in a computing career, covering fundamental computer science principles, practical problem-solving using a programming language, and understanding digital systems. The course focuses on developing creativity, analytical th
1 views • 4 slides
Herbalife
Herbalife provides guidelines for Independent Distributors on creating effective business materials that communicate the brand with clarity and consistency. The guide covers the brand's purpose, vision, values, and slogan, along with dos and don'ts for using the logo and slogan. Distributors are enc
4 views • 17 slides
Montar a caballo en Andorra
Hay dos reacciones m\u00e1s frecuentes al aprender a montar a caballo: la incertidumbre y la expectativa de que ser\u00e1 f\u00e1cil. La realidad, como ocurre con muchas cosas en la vida, se encuentra en alg\u00fan lugar entre las dos respuestas. Debe ser consciente tanto del posible riesgo como del
2 views • 6 slides
Texting Etiquette and Emoji Usage: Tips and Examples
Explore the dos and don'ts of texting etiquette, understand when to use emojis, learn about pet peeves in texting, and delve into real-life examples of embarrassing text moments. Gain insights on appropriate texting behavior and how to navigate communication in the digital age.
1 views • 9 slides
Overview of Distributed Operating Systems
Distributed Operating Systems (DOS) manage computer resources and provide users with convenient interfaces. Unlike centralized systems, DOS runs on multiple independent CPUs and prioritizes software over hardware. It ensures transparency and fault tolerance, with a focus on software error handling.
1 views • 36 slides
DoS Detection for IoT Networks Using Machine Learning: Study Overview
As the number of IoT devices grows rapidly, the need for securing these devices from cyber threats like DoS attacks becomes crucial. This study aims to evaluate the effectiveness of machine learning algorithms such as Gaussian Naive Bayes, K-Nearest Neighbors, Support Vector Machine, and Neural Netw
1 views • 13 slides
How to have a good organising conversation
Explore the importance and structure of organizing conversations with Rohan Kon and Stuart McMillan, focusing on strategies to handle objections, ask impactful questions, and build a vision for collective action like the Sheffield Needs A Pay Rise campaign. Learn the dos and don'ts, the structure of
0 views • 11 slides
Understanding Mess Ethics and Membership Guidelines in Organizations
The content explores the importance of ethics in organizational behavior, focusing on the rules governing personnel conduct to maintain order. It outlines objectives for officers, including defining a mess, classifying members, and understanding dos and don'ts. Additionally, it details membership cl
0 views • 117 slides
Comprehensive Guide to Crafting a Winning University Application and Personal Statement
Universities evaluate applications based on various criteria like past and predicted performance, focus, motivation, reasoning ability, and more. Personal statements play a crucial role in showcasing independence, critical thinking, enthusiasm, and self-awareness. Admissions tutors seek qualities su
1 views • 15 slides
Early Arrival at CSE 417 Winter '21 Lecture - Grab Your Copy!
Welcome to CSE 417 Winter '21 Lecture 1! Get ready for an informative session with insightful staff details, classroom logistics, and important to-dos. Ensure you're prepared by downloading slides and handouts from the webpage. Stay updated with syllabus and additional textbook resources. Engage in
0 views • 33 slides
2022 Guide to Sport Clubs Budget Presentations Dos & Don'ts
Visual representation of a workbook for presenting the estimated budget for the 2022-2023 school year, emphasizing income, expenses, needs, and reasons. Tips include being timed at 12 minutes, professional presentation skills, and ensuring accuracy with the workbook data. Submission involves an esti
1 views • 20 slides
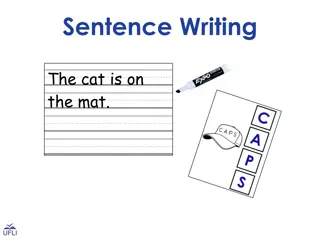
Learn Sentence Writing with Proper Capitalization, Punctuation, and Spelling
Enhance your writing skills with this interactive lesson on sentence construction, capitalization, punctuation, and spelling. Through engaging examples like "The cat is on the mat" and "The dog runs," you'll understand the importance of correct grammar in creating clear and effective sentences. Expl
1 views • 5 slides
Guide to Written Estimates and Claim Checks for Service Dealers
This comprehensive guide covers essential topics such as written estimates, claim checks, invoices, diagnostic fees, and service calls for service dealers. It outlines legal requirements, dos and don'ts, examples, and important references to ensure compliance and transparency in service transactions
0 views • 31 slides
Suspicious Activity Reporting & Beneficial Ownership System Guidelines
Learn about the dos and don'ts of reporting suspicious activities and transactions, understanding beneficial ownership, and the importance of secure search systems. Discover insights on submitting reports, maintaining integrity, and transitioning from reactive to proactive reporting in various secto
0 views • 15 slides
Unlocking the Power of Keywords and AI in Resumes
Harness the potential of keywords and artificial intelligence in crafting effective resumes for enhancing your job search success. Discover the dos and don'ts, understand the role of applicant tracking systems, and optimize your resume with targeted keywords. Gain insights into how ATS/keywords impa
1 views • 5 slides
Use Blog.lri.com.br para aprender sobre a força e a confiabilidade dos
Use Blog.lri.com.br para aprender sobre a for\u00e7a e a confiabilidade dos computadores industriais. Aumente sua vantagem competitiva com tecnologia de ponta e aconselhamento profissional.
3 views • 1 slides
Understanding Denial-of-Service Attacks and Defense Strategies
Denial-of-Service attacks pose a serious threat where attackers flood networks with traffic, leading to system crashes and slowdowns. Explore the impact, expected results, and various categories of DoS attacks such as bandwidth attacks, protocol exceptions, and logic attacks. Learn how to defend aga
0 views • 61 slides
Understanding Network Denial of Service (DoS) Attacks
Network Denial of Service (DoS) attacks aim to disrupt services by overwhelming them with traffic. These attacks can occur at various layers of the network stack and exploit weaknesses to achieve their goal. Amplification attacks, such as the Smurf attack and DNS Amplification attack, can significan
2 views • 52 slides
EnCE EnCase Forensic Boot Disks and Acquiring Digital Evidence
Learn about creating EnCase forensic boot disks, utilizing them to acquire digital evidence, and understanding invisible HPA and DCO data. Discover the steps involved in DOS booting and drive-to-drive DOS acquisition in computer forensics.
0 views • 30 slides
Mastering Group Discussions for Effective Communication and Decision-Making
Explore the world of group discussions with this comprehensive guide. Learn about the importance of group discussions in problem-solving and decision-making. Understand the process involved in conducting successful group discussions, from seating arrangements to evaluation criteria. Gain insights in
0 views • 11 slides
Dos and Don'ts for Stucco Walls in Construction
Stucco walls offer durability and aesthetic appeal, but proper installation is crucial. This guide outlines dos and don'ts for stucco wall construction, emphasizing the importance of drainage plane, synthetic stone materials, and integration of weather-resistive barriers. Proper sequencing and use o
1 views • 8 slides
Cultural Diversity and Journalism Practices
Cultural diversity in journalism is essential for recognizing, respecting, and valuing different cultural expressions. It promotes empowerment, contribution from diverse groups, and celebrates differences. The importance of cultural diversity in journalism lies in acknowledging the variety of cultur
0 views • 9 slides
Protecting Your Computer and Laptop: Tips for Maintenance and Security
In this presentation, learn how to safeguard your computer and laptop with simple precautions to prevent physical damage, viruses, hacking, and more. Discover dos and don'ts for handling serious computer issues and ensuring your devices stay in optimal condition. Remember these key steps for maintai
0 views • 5 slides
Implementing Smoke and Tobacco-Free Policies on College Campuses
Explore the growing momentum of implementing smoke and tobacco-free policies on college campuses across the country, with examples from leading health organizations and steps to form and enforce these policies effectively. Learn about the dos and key considerations in adopting such policies and acce
1 views • 33 slides
Understanding Low-Intensity DoS Attacks on BGP Infrastructure
Low-intensity Denial of Service (DoS) attacks present a new challenge in cyber warfare, blending in with regular traffic to target communication channels like HTTP, SMTP, and DNS. These attacks require multiple participating hosts to flood the target with useless packets, gradually overloading serve
0 views • 25 slides
Job Interview Preparation Tips: Dos and Dont's for Success
Prepare effectively for your job interview with dos and don'ts to remember, from dressing professionally to arriving on time, maintaining good posture, and researching the company. Learn how to answer questions, greet the interviewer, and present yourself professionally before, during, and after the
0 views • 26 slides
Challenges and Design Issues in MS-DOS Development
Windows faced difficulties in enabling multitasking while integrating with non-multitasking MS-DOS and device drivers. MS-DOS lacked multiprocessor synchronization capabilities, limiting shared resource access. Security features like unalterable password identifiers and command-based usage reduced v
0 views • 159 slides
LTU+TTCex System Status and Installation Overview
Detailed status updates, notes, and images regarding the LTU+TTCex system setup, clock distribution, final partitions, hardware installation, firmware and software updates, and DIM servers running on VME processors. The content covers the system's functionality, issues, to-dos, and upgrades as of Se
0 views • 9 slides
Understanding UNIX Operating System
UNIX is a versatile operating system that enables multi-user access, multitasking, and portability across various computing environments. It serves as the foundation for many modern operating systems and has influenced concepts incorporated in Microsoft Windows and DOS. The UNIX system comprises dis
0 views • 51 slides
Mastering Presentation Skills: Tips and Techniques for Effective Public Speaking
Overcome the fear of public speaking with these practical tips and techniques for delivering engaging presentations. Learn how to plan your talk effectively, structure your content in threes, utilize presentation techniques, and make the most of aids like PowerPoint. Discover dos and don'ts to enhan
0 views • 14 slides
Introduction to Linux: Course Overview and Objectives
This introduction to Linux course provides a comprehensive overview of operating systems, including the history, variations, user interface, and essential commands. The course is designed with lectures, labs, and exercises to help participants gain a better understanding of Linux and its practical a
0 views • 77 slides
All You Need to Know About Elections and Voting Procedures
Learn about different types of elections, obligations for local and regional elections, election dos and don'ts, what constitutes a valid ballot, and the importance of voter transparency and integrity in the election process.
0 views • 13 slides
Understanding Web Security: Risks, Threats, and Safeguards
In the realm of web security, it is crucial to shift our mindset to anticipate malicious intent and potential vulnerabilities. Attackers can aim to access private data, manipulate information, disrupt services, or tarnish reputations. Familiarize yourself with common attacker goals, tools used, and
0 views • 18 slides
Understanding Network Security Vulnerabilities and Attacks
Explore the world of network security vulnerabilities and attacks, including Denial-of-Service (DoS) and Distributed-Denial-of-Service (D-DoS), security flaws in the TCP/IP protocol suite, ICMP attacks, routing attacks, and TCP attacks. Learn about common security vulnerabilities such as address spo
0 views • 36 slides
Evolved Addressing and Forwarding in Information-Centric Networks
The content discusses Evolved Addressing and Forwarding in Information-Centric Networks, focusing on an accountable Internet protocol (AIP) that addresses vulnerabilities at the IP level, such as source spoofing, DoS attacks, and route hijacking. AIP utilizes a hierarchy of self-certifying addresses
0 views • 16 slides
Best Practices for Maternal and Newborn Health (MNH) - Essential Guidelines
Comprehensive guidelines for maternal and newborn health practices include dos and don'ts, such as perineal shaving, delayed cord clamping, exclusive breastfeeding, and more. Key measures like controlled cord traction (CCT) in a relaxed uterus and delaying the baby's first bath play crucial roles in
0 views • 11 slides
Insight into British Culture and Society
Discover various aspects of British culture such as the cost of living, dos and don'ts, population demographics, religions, trade and industries, as well as natural resources. From the diverse population to the main industries and trade exports and imports, delve into the unique characteristics of E
0 views • 9 slides
Mastering Views: An Essential Guide for Efficient Web Data Display
Dive into the world of Views with expert trainers Dawain Faison, Lois Nilsen, Marla Laubisch, and Amy Perry. Learn the basics, layout diagrams, hands-on exercises, and best practices to create and manage Views effectively. Discover the power of Views in compiling and arranging data for webpage displ
0 views • 8 slides
Dos and Don'ts of Toilet Construction Guide
Proper toilet construction involves positioning the squatting pan centrally, aligning it with the floor level, ensuring proper aeration and lighting, and maintaining neat finishing. Avoid common mistakes like poor piping, misalignment, lack of external lighting, and substandard materials to achieve
0 views • 17 slides
Overview of DoS and DDoS Attacks in Cybersecurity
This content provides an in-depth overview of Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks in cybersecurity. It covers the types of attacks, including volumetric, reflected, and stealthy, along with detailed explanations and examples. Additionally, it discusses how DoS at
0 views • 8 slides