Efficient Key Recovery Attack on SIDH
Efficient key recovery attack on Supersingular Isogeny Diffie-Hellman (SIDH) protocol. It explores the vulnerability of the protocol and proposes a concrete solution. The attack leverages auxiliary points to solve the isogeny problem and reveals instances of the common secret key.
5 views • 22 slides
Fernandes Thriving in United's Resurgent Attack^J Euro 2024 Success
Fernandes Thriving in United's Resurgent Attack, Euro 2024 Success\n\nhttps:\/\/blog.worldwideticketsandhospitality.com\/2024\/02\/15\/fernandes-thriving-in-uniteds-resurgent-attack-euro-2024-success\/\n\nUEFA Euro 2024 fans from all over the world can book European Championship 2024 Tickets on our
2 views • 5 slides
Understanding Viral Vectors in Gene Delivery: Safety and Considerations
Exploring the mechanisms of gene delivery via viral vectors, this content delves into the basics of viral structure, infection, and replication. It discusses common viral vector systems like Adenoviral and Lentiviral vectors, highlighting safety considerations and the production processes involved.
1 views • 19 slides
Understanding Normed Vector Spaces for Nanotechnology Engineering
Introduction to normed vector spaces, focusing on defining norms for vectors in finite-dimensional spaces, exploring different ways to measure vector length, and understanding the concept of unit vectors and norm properties. This topic equips readers with the ability to calculate vector norms, norma
0 views • 9 slides
Introduction to Cartesian Components of Vectors in Two-Dimensional Space
Exploring Cartesian components of vectors in a two-dimensional coordinate frame using unit vectors i and j. Learn how to express vectors, add them using the triangle law, use column vector notation, and find resultant vectors. Understand position vectors in terms of coordinates. Examples and diagram
0 views • 16 slides
Understanding Recombinant DNA Technology and Cloning Vectors in Genetics Engineering
Exploring the fundamentals of recombinant DNA technology and gene cloning, this content delves into the key concepts and basic steps involved. It covers various cloning vectors such as plasmids, bacteriophages, and artificial chromosomes, highlighting their common features and applications in geneti
0 views • 12 slides
Understanding Amity School of Engineering & Technology Vectors in Java
Amity School of Engineering & Technology Vectors provide a flexible way to manage dynamic arrays in Java programming. With capabilities to store objects of any type and accommodate dynamic resizing, these vectors offer optimized storage management through capacity and capacity increment settings. Co
0 views • 18 slides
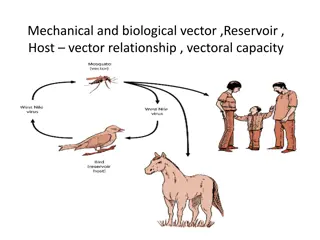
Vector Relationships and Pathogen Transmission
Understanding mechanical and biological vectors, reservoir hosts, and their role in disease transmission is crucial for effective disease control. Mechanical vectors like flies can transfer pathogens without getting infected, while biological vectors like mosquitoes carry pathogens that reproduce in
1 views • 5 slides
First Nations Attack on Fort Michilimackinac 1763: Causes, Tribes, and Aftermath
The First Nations' attack on Fort Michilimackinac in 1763 was triggered by British actions that disrupted their way of life. The Ojibwe, Odawa, Potawatomi, Ottawas, and Hurons were involved in the attack, led by Chief Pontiac. Following the attack, the British did not rebuild the fort but establishe
1 views • 7 slides
Understanding Vectors and Velocity in Physics and Game Programming
Exploring the concepts of vectors, velocity, and positional vectors in both physics and game programming. Learn about key properties, conversion formulas, and the application of velocity vectors to positional vectors using examples and visual representations.
1 views • 32 slides
Understanding Vectors and Motion Control Systems in Industrial Machinery
Vectors play a crucial role in machine control systems, particularly in programming and motion control. This article explores the concept of vectors, their application in two and three-dimensional machines, and their significance in physics. It also delves into the use of vectors for controlling mov
0 views • 6 slides
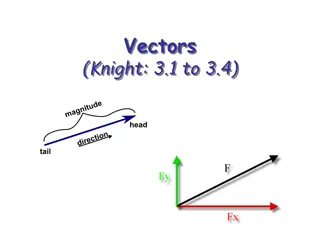
Exploring Vectors: Magnitude, Direction, and Operations
Delve into the world of vectors, understanding their properties, how to add and subtract them, and determining their components in different coordinate systems. Learn about scalar quantities, vector quantities, the tip-to-tail rule, and the role of unit vectors in calculations.
0 views • 19 slides
Enhancing Cybersecurity for Windows Infrastructure: A Practical Guide
In this informative session, Vladimir Stefanovi, a seasoned System Engineer and Technical Trainer, sheds light on the vulnerabilities of Windows servers and provides valuable insights on how to protect and fortify your infrastructure against cyber threats. From traditional to modern attack vectors,
0 views • 21 slides
Understanding Cloning Vectors and Recombinant DNA Technology
Genetics Engineering Lecture-2 delves into the concept and basic steps of recombinant DNA technology and gene cloning, highlighting different types of cloning vectors like plasmids, bacteriophages, bacterial artificial chromosomes, yeast artificial chromosomes, and mammalian artificial chromosomes.
1 views • 13 slides
Duane Wolf Attack Simulation Study: Insights for Law Enforcement Officers
Duane Wolf conducted an attack simulation study to test the speed at which an un-handcuffed suspect sitting on a curb can launch an attack on officers. The study involved volunteers in different leg positions to mimic real-life scenarios. Findings emphasized the importance of officers staying alert
0 views • 9 slides
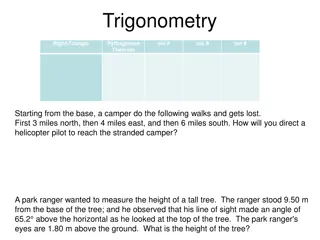
Trigonometry and Vector Illustrations in Physics
Explore applications of trigonometry and vectors in solving real-world problems such as directing a helicopter pilot to a stranded camper, measuring the height of a tree, analyzing displacement vectors, and adding vectors using graphical and component methods.
0 views • 10 slides
Understanding Acceleration Due to Gravity Vectors
Discover the direction of acceleration due to gravity vectors for various scenarios such as a pebble dropped from a bridge, a baseball tossed up in the air, a football thrown at a 45-degree angle, and more. Explore how vectors can be represented to show both magnitude and direction, helping in visua
0 views • 18 slides
Understanding Four-Vectors in 4D Space
Explore the concept of four-vectors in four-dimensional space, covering topics such as radius vectors, general 4-vectors, contravariant and covariant components, summation conventions, scalar products, and the components of a general 4-vector. Learn how these vectors transform under rotations and Lo
0 views • 42 slides
Understanding Blending Attacks on Mixes by Meng Tang
Explore the effectiveness of blending attacks on mixes, including steps of a blending attack, attack models, factors affecting the attack, defense strategies, and insights from the attacker's viewpoint.
0 views • 25 slides
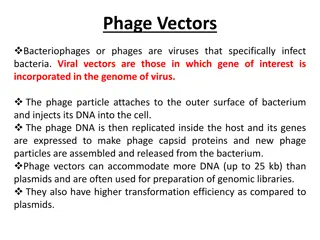
Understanding Phage Vectors in Genetic Engineering
Phage vectors, utilized in genetic engineering, are bacteriophages capable of incorporating genes of interest into their genome. They have a higher DNA capacity compared to plasmids, making them ideal for creating genomic libraries. Bacteriophages like Lambda and M13 are commonly used for cloning ve
0 views • 17 slides
Understanding Math Fundamentals: Matrices and Vectors in EECS 442
Delve into the world of matrices and vectors with a focus on floating-point math, IEEE standards, vector operations, and matrix manipulation in the context of EECS 442 lectures by Justin Johnson. Explore foundational concepts such as concatenation, transpose, cross product, dot product, and the nuan
0 views • 58 slides
Signature-Based IDS Schemes for Heavy Vehicles
This research focuses on developing signature-based Intrusion Detection System (IDS) schemes for heavy vehicles, particularly targeting the Controller Area Network (CAN) bus. The study delves into various attack vectors and payloads that have targeted commercial vehicles over the years, proposing th
0 views • 18 slides
Volleyball Referee Hand Signals for Common Violations
Learn the essential hand signals used by volleyball referees to indicate common violations during a game. Signals include illegal alignment, line violation, illegal hit, delay of service, over the net, net foul, legal back row attack, illegal attack of serve back row attack, and illegal block/screen
0 views • 26 slides
MATLAB Basics for Electrical Engineering Students
In this instructional content from the Government Polytechnic West Champaran Department of Electrical Engineering, students are introduced to the fundamentals of MATLAB. Topics covered include transposing matrices, concatenating matrices, matrix generators, arrays, entering matrices, and manipulatin
0 views • 48 slides
Understanding Word Vectors and Training with Gensim
Explore the differences between one-hot representation and word vectors, learn about virtual environments in Python for training word vectors, and dive into the process of evaluation, analogy, and word clustering. Discover tools like Anaconda and Virtualenv, popular libraries like Gensim, and the si
0 views • 16 slides
Mechanism of Br2 Attack on Trans-Cinnamic Acid
The detailed anti-attack and syn-attack mechanisms of Br2 on trans-cinnamic acid are presented, illustrating the intricate steps involved in preventing or facilitating the attack of bromine on the compound. The process involves initial attack, bridgehead formation, bond rupture, bond stabilization,
0 views • 11 slides
Understanding Recombinant DNA Technology and Plasmid Vectors
Explore the world of recombinant DNA technology through the utilization of plasmids as vectors for gene cloning. Learn about techniques like insertional inactivation and the characteristics of common plasmid vectors such as pBR322. Discover the intricacies of genetic manipulation in bacterial origin
0 views • 26 slides
Understanding Parasitic Helminths and Disease Vectors in Microbiology
Explore the world of parasitic helminths and disease vectors in microbiology. Learn about the classification of parasites, the life cycle of Ascaris lumbricoides, and the role of arthropods as agents and vectors of diseases in humans. Discover the characteristics of the three main groups of parasiti
0 views • 18 slides
Understanding Vectors in AP Physics C: Mechanics
Explore the fundamental concepts of vectors in AP Physics C: Mechanics, including scalar vs. vector quantities, vector operations, and vector multiplication. Discover the significance of vectors in explaining and predicting physical phenomena through graphical methods and mathematical equations. Div
0 views • 28 slides
Understanding Vectors, Matrices, and Rotations in Euclidean Space
Explore the fundamentals of vectors, matrices, rotations, and coordinate transformations in Euclidean space. Learn about points, tensors, and the significance of vectors in representing physical quantities. Discover the Parallelogram Law and Coordinate Frames for effective visualization and computat
0 views • 46 slides
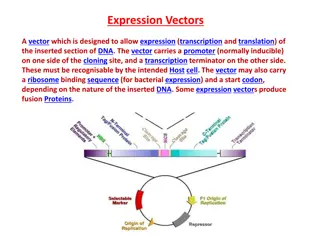
Understanding Expression Vectors in Molecular Biology
Expression vectors are essential tools for gene expression studies, allowing for transcription and translation of specific DNA sections in host cells. These vectors contain key elements like promoters, terminators, and ribosome binding sequences for efficient protein production. Different promoters
0 views • 15 slides
Understanding Forces and Vectors in Statics with Air Balloon Models
Explore the world of forces and vectors in statics through the model of a hot air balloon. Learn about vectors of negative magnitude, zero, addition, subtraction, parallel and perpendicular components, and multiplying by a scalar. Discover how to find components and the resultant force of multiple f
0 views • 17 slides
Understanding Vectors in C++: A Comprehensive Overview
Dive into the world of vectors in C++ with this detailed lecture overview, covering topics like overloading operators, enumeration, and dynamic memory allocation. Explore the principles of least privilege and learn about access specifiers for class functions. Discover the flexibility and convenience
0 views • 51 slides
Vector Mathematics for Geometric Problem Solving
Learn how to use vectors to solve geometric problems, including finding position vectors of points dividing line segments in given ratios. Explore concepts such as position vectors, ratios, trigonometry, and Pythagoras' theorem to determine angles and side lengths in triangles using vector methods.
0 views • 9 slides
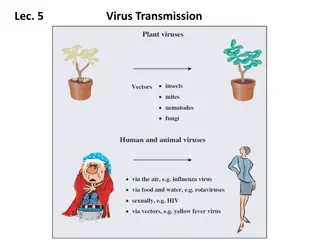
Understanding Virus Transmission via Vectors
Viruses must be transmitted to new hosts for their survival. This transmission occurs through vectors like arthropods, which acquire and transmit viruses during feeding. The mechanism involves viruses attaching to the vectors' mouthparts or entering their circulatory system to reach salivary glands
0 views • 14 slides
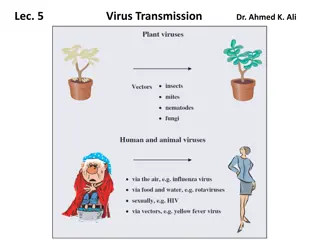
Understanding Virus Transmission via Vectors in Hosts
Viruses must be propagated and transmitted to new hosts for survival. They can be spread via vectors like arthropods, which acquire and transmit viruses during feeding. This transmission can occur quickly through the vector's mouthparts or more slowly via circulation in the vector's body. Plant viru
0 views • 14 slides
Understanding Malaria Vectors and Their Habitats
Explore the complex relationships between malaria vectors and parasites, highlighting the biology and life cycles of Anopheline mosquitoes. Discover the diverse species within the Culicidae family and their preferences in habitat, influenced by human activities. Gain insights into the genus Anophele
0 views • 47 slides
Social Engineering Attack Framework (SEAF) - Understanding the Process
Social Engineering Attack Framework (SEAF) provides a structured approach to executing social engineering attacks. It defines the attack framework, assists in planning and execution, and helps in verifying the success of the attack. The process involves identifying the attack goal, assessing potenti
0 views • 16 slides
Understanding Vectors: Concepts, Operations, and Applications
Vectors are quantities defined by magnitude and direction, essential in various fields like physics and mathematics. Learn about vector properties, examples, operations like addition and multiplication, as well as applications such as understanding displacement, velocity, and acceleration. Dive into
0 views • 20 slides
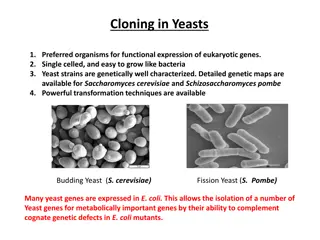
Understanding Cloning in Yeasts: Vectors and Selectable Markers
Yeasts like Saccharomyces cerevisiae and Schizosaccharomyces pombe are valuable organisms for eukaryotic gene expression. They offer easy growth like bacteria and are genetically well-characterized. Yeast selectable markers and vectors enable efficient cloning and expression of genes. The use of shu
0 views • 16 slides