Enhance Your Wireless Range: 192.168.188.1 Wireless Extender Setup with Top Apps
Are you tired of weak Wi-Fi signals limiting your internet access? Fear not! With the 192.168.188.1 Wireless Extender Setup and some top-notch apps, you can extend your wireless range and enjoy seamless connectivity throughout your home or office.\n\nfor more info: https:\/\/1921681881.com\/192-168-
7 views • 2 slides
Scrolls:Rolling Flexible Surfaces for Wideband Wireless
Revolutionizing wireless communication, the Scrolls project introduces rolling flexible surfaces for wideband wireless applications. With the expectation of 30 billion wireless devices by 2025, the project emphasizes standards and frequencies such as Cellular, Wi-Fi, and IoT. By offering a standard-
3 views • 19 slides
Wireless Communication Networks by Dr. K. Gopi at SITAMS
Wireless Communication Networks (WCN) is a fundamental aspect of modern telecommunication, allowing information transfer without physical connections. Dr. K. Gopi, an Associate Professor at the Department of ECE at SITAMS, introduces concepts like multiple access techniques, traffic routing, and the
1 views • 13 slides
Class 2 Permit Modification Request
This Permit Modification Request (PMR) aims to transition audit scheduling for site recertification from an annual to a graded approach, incorporating DOE Orders and Quality Assurance program requirements. The PMR consolidates scheduling information, reduces redundancy, and clarifies subsequent audi
3 views • 22 slides
Utilizing Audits for Antimicrobial Stewardship in General Practice
The importance of audits in antimicrobial stewardship is highlighted in this informative content covering topics like why audit and feedback are crucial, sources of prescribing data, available audit tools, practical tips, and a case study showcasing the positive impact of audits in UTI management. T
10 views • 40 slides
Post-Election Risk-Limiting Audits in Indiana
Indiana's post-election audits, overseen by the Voting System Technical Oversight Program, utilize statistical methods to verify election outcomes, ensuring accuracy and reliability in the electoral process. The VSTOP team, led by experts in various fields, conducts audits based on Indiana Code IC 3
0 views • 12 slides
Role of Supreme Audit Institution of the Philippines in Employing Artificial Intelligence to Fight Corruption
The Supreme Audit Institution of the Philippines (SAI-PHL) is utilizing technology, including artificial intelligence, to enhance its audit processes and combat corruption effectively. Through initiatives like understanding IT systems and conducting computer-assisted audits, SAI-PHL is embracing dig
0 views • 12 slides
GMP Audits in Construction: Navigating Client Expectations
This presentation at the National Association of Construction Auditors' virtual conference focuses on helping clients grasp the key objectives and processes of Guaranteed Maximum Price (GMP) audits. Dave Potak, a seasoned professional, will share insights on managing client expectations, best practi
0 views • 18 slides
Rate Optimization in Wideband RIS-assisted Wireless Systems
This research focuses on rate optimization in wideband RIS-assisted wireless systems, specifically investigating MIMO RIS-assisted systems in sub-6 GHz mmWave settings. Pathloss and blockage modeling, along with LOS vs. spectral efficiency and RIS-UE distance vs. spectral efficiency analyses, are ke
0 views • 4 slides
Wireless Security Audits and Best Practices
Explore the world of security audits with a focus on wireless networks. Learn about the types of security audits, best practices, and the steps involved. Discover the importance of systematic evaluations, identifying vulnerabilities, establishing baselines, and compliance considerations. Dive into t
0 views • 14 slides
Departmental Audits in GST
Departmental audits in GST involve the examination of records, returns, and other documents to verify the correctness of turnover declared, taxes paid, refunds claimed, and input tax credit availed. This audit ensures compliance with the provisions of the CGST Act, 2017. Types of audits under GST in
7 views • 27 slides
Best Wireless Alarms in Leixlip
Are you looking for the Best Wireless Alarms in Leixlip? Then contact Covert Security. They offer comprehensive residential and commercial security services nationwide. They specialize in providing bespoke intruder wireless alarms and CCTV packages t
0 views • 6 slides
Guidelines for Social Audits under MGNREGA
The legal mandate for social audits under MGNREGA includes the requirement for conducting audits by Gram Sabhas, setting up independent Social Audit Units, and involving Village Social Audit Facilitators. The process involves collating records, conducting beneficiary and work verification, and prese
1 views • 19 slides
Worried About IRS Audits? Here’s How SAI CPA Services Can Help You Avoid Them!
IRS audits can be stressful, but with the right preparation, you can minimize your chances of being audited. Audits often stem from discrepancies or unusual patterns in tax returns. Common triggers include math errors, large deductions, unreported in
3 views • 2 slides
Tamper-Evident Pairing (TEP) Protocol for Secure Wireless Pairing Without Passwords
This article discusses the challenges of traditional secure wireless pairing methods that rely on password validation and proposes the Tamper-Evident Pairing (TEP) protocol as a secure in-band solution to protect against Man-in-the-Middle (MITM) attacks. TEP eliminates the need for out-of-band chann
1 views • 40 slides
Single Audits in Federal Grant Programs
Audits play a crucial role in ensuring accountability in Federal grant programs. Single Audits, being the most common type, combine financial and compliance audits into one report. Learn about threshold determinations, risk-based approaches, and key changes in the Uniform Guidance through this compr
0 views • 26 slides
Wireless LANs: Components and Security Issues
Wireless LANs use radio waves to connect users within a building or campus. This technology overview covers IEEE 802.11 standards, migration to WLANs, and connection to wired LANs through access points. Understanding the specialized protocols, security considerations, and performance differences is
0 views • 29 slides
Safety Management Overview and Audits Report
Explore a detailed report on safety management practices, audits findings, and actionable insights in the BSEE office. Learn about prior audits, SEMS evaluations, CAP verification, and more. Dive into SEMS subpart O audits and API RP 75 guidelines for a comprehensive understanding of safety protocol
0 views • 18 slides
Billing Documentation Guidelines for OSAP Programs
Audits are imminent for OSAP/BHSD programs, emphasizing the importance of proper documentation to ensure compliance and accuracy in billing. Providers must adhere to strict guidelines for submitting audits and desk audits annually, promptly informing OSAP of any staff changes. The documentation cove
0 views • 25 slides
Exploring Wireless Technologies and Mobile Commerce
Delve into the realm of wireless technologies, mobile computing, and mobile commerce with a focus on the advantages and disadvantages of wireless transmission media, business applications of short-range to long-range networks, m-commerce benefits for businesses, technologies in pervasive computing,
1 views • 36 slides
Powercor Industry Forum Audit Results and Trends Analysis
Audit results and trends analysis reveal that there were 256 audits completed, with 50 being re-audits. Additional resources were acquired to meet industry demand, but audit volumes in Q4 did not meet forecast. Turnaround times improved with the deployment of more auditor resources. Trends show issu
0 views • 8 slides
Wireless Network Essentials and Classification
Wireless networks play a vital role in our modern world, with mobile devices outnumbering wired connections. This overview covers wireless network fundamentals, including elements, characteristics of wireless links, ad hoc operations, and network classifications like mesh networks and MANET.
1 views • 45 slides
Wireless Networks: Types and Applications
Wireless networks utilize wireless data connections to connect network nodes and share resources. They include Wireless Personal Area Networks (WPAN), Wireless LAN, Wireless WAN, Wireless Broadband, and Wireless Cellular. Each type has specific characteristics and applications, such as linking perso
0 views • 29 slides
The Impact of Audits on Post-Audit Tax Compliance
Audits have direct and indirect effects on taxpayers, influencing compliance behaviors. While more audits generally lead to increased compliance, outcomes can be ambiguous, with some studies showing a decline in post-audit compliance. Behavioral responses to tax audits are driven by perceived risks
0 views • 15 slides
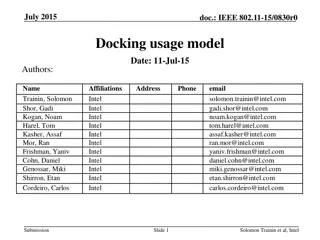
Wireless Office Docking Model for Multiple Devices
This document outlines a usage model for office docking involving wireless connections between mobile devices and various peripheral devices such as monitors, hard drives, printers, and more. It describes scenarios for single and multiple devices in both home and office settings, emphasizing the nee
0 views • 5 slides
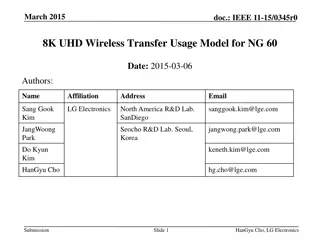
Evolution of 8K UHD Wireless Transfer Usage Model for Next Generation Displays
This IEEE document discusses the evolution of high-resolution displays and services, reviews wired interface solutions, and proposes a wireless transfer usage model for 8K UHD displays. It covers the advancements in display technology, including commercial 4K and 8K UHD offerings, broadcast services
1 views • 11 slides
Overview of External Wireless Communication System on International Space Station (ISS)
This presentation covers the overview and experience of implementing an external 802.11n wireless communication system on the International Space Station (ISS). It discusses the existing wireless system, committed users, system architecture, and future challenges. The system provides high data rate
1 views • 18 slides
Challenges and Solutions in Wired-Wireless TSN Configuration
This document discusses the challenges faced in configuring and managing wired-wireless TSN domains, focusing on the unique aspects of wireless networks such as fading, variable delays, and shared medium access. It presents models for physical and logical integration of wired and wireless TSN, empha
0 views • 13 slides
Impact of Audits on Tax Compliance: Insights from Research Studies
Studies conducted by researchers such as Erich Kirchler have explored the impact of audits on tax compliance. While audits generally have a positive effect on compliance, there are cases where they can backfire, leading to unintended consequences. High auditing levels may not always deter tax evasio
0 views • 14 slides
The Interaction Between Criminal Investigations and Civil Tax Audits in Sweden
The relationship between criminal investigations and civil tax audits in Sweden is explored, highlighting how tax audits and criminal proceedings run concurrently. The mens rea requirement for criminal sanctions and tax surcharge, as well as the integration between criminal sanctions and tax surchar
0 views • 13 slides
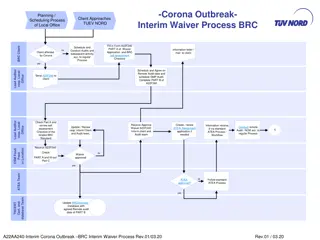
Interim Waiver Process for BRC Audits During Corona Outbreak
This content outlines the interim waiver process and scheduling procedures for local office client audits during the Corona outbreak. It includes steps for completing waiver applications, conducting remote audits, and handling certification extensions. The document also provides guidelines for remot
0 views • 11 slides
Game Theory Applications in Wireless Communication Networks
Explore the application of game theory in wireless communication networks through lectures covering various game theory concepts such as non-cooperative games, Bayesian games, and cooperative games. The focus is on Zero-Determinant Strategy, a method used for resource sharing and power control in wi
2 views • 36 slides
Wireless Programming for Hardware Dummies: Simplifying Wireless Research in the Industry
Explore the world of wireless programming for hardware beginners with a comprehensive guide on software-defined radios, FPGA usage, and modern wireless research challenges. Discover the importance of innovative PHY/MAC designs, new protocols like 5G and IoT, and the need for high-rate DSP in wireles
1 views • 76 slides
Exploring Wireless Technologies for Datacenters
This presentation delves into the feasibility and advantages of completely wireless datacenters, focusing on alternative switching technologies, goals, conventional setups, opportunities, 60GHz wireless technology, antenna models, design challenges, and the motivation behind moving towards wireless
0 views • 28 slides
Advanced Strategies for Wireless Communication Networks
Explore advanced strategies for wireless communication networks, including aggressive synchronous transmissions with in-network processing, goals beyond capture-based processing, concurrent wireless transmissions, and innovative concepts for efficient data transfer and network reliability. Dive deep
1 views • 11 slides
Supporting SAIs in Auditing SDGs: Reflections and Plans
SAIs play a crucial role in auditing SDGs to ensure high-quality audits of partnerships. Various SAIs and funding partners are actively involved in supporting this initiative. The story so far includes audits of preparedness and implementation of SDGs, with performance audits supporting 73 SAIs and
0 views • 14 slides
Wireless Communication Frequencies and Regulations
Explore the world of wireless communication frequencies, signals, and regulations explained by Prof. Dr.-Ing. Jochen H. Schiller from Freie Universität Berlin, Germany. Discover the various frequency ranges from VLF to EHF, examples for mobile communication frequencies, and regulations in Europe, U
0 views • 44 slides
Enhancing Bandwidth of Channel State Information (CSI) for Wireless Sensing Applications
This submission delves into the necessity of expanding the bandwidth of Channel State Information (CSI) in wireless environments to cater to the demands of time-sensitive wireless sensing applications. It explores the implications of high-bandwidth CSI on enhancing wireless channel understanding, ac
0 views • 12 slides
Food Industry Perspective on 3rd Party Audits and Regulatory Inspections
Overview of regulatory inspections and 3rd party audits in the food industry from the perspective of Tim Ahn, Global Director of Quality & Food Safety at Mars Chocolate. The content covers the importance of inspections, differences between inspections and audits, and the role of audits in driving qu
0 views • 12 slides
Overview of Wireless Industry: Competition and Financialization Impact on Workers
The wireless communications industry is rapidly evolving, with increasing data traffic, market penetration, and a shift towards wireless-only households. Major companies like AT&T, Verizon, Google, and Netflix are shaping the industry with a focus on network infrastructure and services. Despite the
0 views • 18 slides