Events Training 2023/24 Information Session Details
This document contains details about the Events Training Session for the year 2023/24 at Essex University. It includes information on session formats, how to host events on and off-campus, accessing event toolkits, and contacting relevant departments. Attendees are encouraged to take notes and ask q
1 views • 38 slides
Empower Your Organization with Ex-McKinsey, Deloitte & BCG Management Consulting Toolkits
Leveraging the expertise of ex-McKinsey, Deloitte & BCG Management Consultants has never been easier with the comprehensive toolkits offered by Domont Consulting. These toolkits cover a range of areas such as corporate strategy, digital transformation, talent management, and more, enabling executive
5 views • 30 slides
Enhancing Access to Medicines and Health Products through Innovative Approaches
Global Health Centre experts discuss how building access into innovation can ensure better access to medicines, vaccines, and health products. Key ideas include planting seeds for access early in innovation, exploring alternative innovation models, and rethinking the relationship between innovation
4 views • 20 slides
Comprehensive Guide to Accessing and Utilizing Indicator Toolkits
This detailed guide covers various aspects of using Indicator Toolkits, including locating toolkits, completing required activities, uploading documentation, accessing dates to remember, and utilizing compliance monitoring dashboards. Learn how to efficiently navigate through the toolkits for compli
5 views • 26 slides
Vanderbilt Staff Learning Opportunities and Resources
Explore a variety of learning opportunities at Vanderbilt to enhance your knowledge, skills, and understanding. From digital libraries to online training seminars, discover resources like Strategic Planning Toolkits, Microsoft 365 tutorials, and specialized courses in Excel, PowerPoint, and Project
1 views • 20 slides
2022 Thales Access Management Index
Thales Access Management Index highlights the current landscape of access security, revealing insights on multi-factor authentication adoption, remote and privileged user access management, VPN usage trends, challenges faced, and preferences towards third-party access management. The report emphasiz
2 views • 9 slides
Guidelines for Expanded Access to Investigational Drugs and Devices
Providing guidance on types of Expanded Access for drugs, biologics, and devices, this content explains the concept of Expanded Access and the criteria that must be met. It covers different types of Expanded Access for drugs and devices, emphasizing the importance of patient safety and benefit. The
0 views • 10 slides
Personnel Safety Systems and Access Control at CERN Facilities
Personnel Safety Systems at CERN include ODH detection, fire safety measures, and access control to protect personnel from hazards. Various access control layers are implemented to regulate entry to different parts of the facility, ensuring only trained personnel access underground areas. Biometric
0 views • 19 slides
Port of Stockton Restricted Area Access Control and ID Card Policy
Access to restricted areas at the Port of Stockton facilities requires possession of a TWIC (Transportation Worker Identification Credential). Only authorized personnel, such as employees, contractors, and those with regular access, may receive a Port Access Card after approval by the Facility Secur
0 views • 6 slides
Introduction to Database Security and Countermeasures
Database security is essential to protect data integrity, availability, and confidentiality. Countermeasures such as access control, inference control, flow control, and encryption can safeguard databases against threats. Access control restricts user access, inference control manages statistical da
0 views • 26 slides
Comprehensive Resources for Economic Recovery and Resilience Planning
Explore a wealth of resources on economic recovery and resilience planning, including webinars, case studies, toolkits, and thought leadership. Discover best practices, research reports, and insights to help communities navigate disasters and build resilience. Access free materials from organization
0 views • 12 slides
O3 Access Control Solution Overview
O3 Access Control Solution offers unique selling points like single-seat management software, role-based permissions, customizable user information, and more. The system includes a compact controller with multi-format reader support and BACnet Access objects. It integrates with other O3 modules for
0 views • 10 slides
Asset Management Resources and Funding in Yukon Community of Practice
Explore asset management resources and funding opportunities in Yukon through the Community of Practice. Learn about asset management in Canada, FCM, CNAM, NAMS Canada, and more. Discover networks, associations, and toolkits to enhance infrastructure planning and operations in the region.
0 views • 12 slides
Understanding Antimicrobial Stewardship in Healthcare
Exploring the critical aspects of antimicrobial stewardship, including the reasons for antibiotic resistance, considerations for prescribing antibiotics, stewardship checklists, and the role of toolkits in promoting responsible antibiotic use to combat resistance. The importance of monitoring, docum
0 views • 20 slides
Enhancing Collaboration for Climate Change Action
The CPDAE Action Plan aims to foster knowledge exchange and peer support among national implementing entities involved in climate change finance. The proposal includes the development of an online platform for sharing experiences, an online hub for toolkits, and capacity-building programs to strengt
3 views • 11 slides
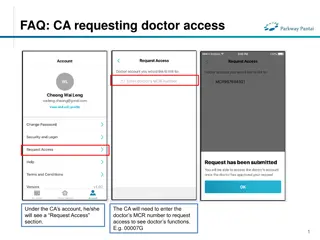
FAQs for Doctor and Clinical Assistant (CA) Account Access Management
Learn how CAs can request access to doctors' functions by entering the MCR number, how doctors can grant or remove CA access, and how CAs can manage access to multiple doctors. The process includes requesting, approving, and unlinking accounts, ensuring efficient and secure access management in a cl
0 views • 4 slides
EventsHQ Virtual Event Registration: User Access and Setup Guide
This comprehensive guide provides step-by-step instructions on setting up virtual event registration using EventsHQ. It covers how users can access event details, join the event, and includes best practices for sharing access links. Learn how to utilize the Virtual Event Details feature, send remind
1 views • 19 slides
Understanding Disabilities in Native Communities
Indigenous communities have diverse views on disabilities, with some lacking specific terms. Stories of compassion and inclusion exist, like the Navajo tale of Early Dawn Boy and the Hopi Cross-Legged Kachina. However, challenges such as underfunding, limited services, and cultural sensitivity gaps
0 views • 12 slides
Scrap Tire Generator Education and Outreach Campaign Progress Report
Update on the education and outreach campaign for scrap tire generators, detailing initiatives such as the Scrap Tire Summit, development of toolkits, and regional improvements in scrap tire management infrastructure. The campaign aims to engage stakeholders, enhance compliance with scrap tire laws,
0 views • 30 slides
Accessible Voting System for Californians with Disabilities
Learn about the Remote Accessible Vote-by-Mail System in California, designed to empower voters with disabilities to securely access, mark, and return their ballots from any computer with internet access. Find out who is eligible to use the system, how to access and return the ballot, and the steps
0 views • 23 slides
Dell Networking Solutions for BYOD and Guest Access Projects
Dell offers end-to-end solutions for Bring-Your-Own-Device (BYOD) and guest access projects, enabling secure employee access and controlled connectivity for visitors. The framework includes mobility business models, device security, network protection, and scalability. Dell supports customers in imp
0 views • 11 slides
Strategies for Reducing Vehicle Miles Traveled (VMT) in North Carolina
Explore the initiatives undertaken by NCDOT to reduce VMT in North Carolina through studies, toolkits, task forces, and collaboration with various stakeholders. Discover the importance of VMT reduction, its environmental and health benefits, commuter trends, and the impact of COVID-19 on transit rid
0 views • 11 slides
Migration Matters Scotland Project Overview
The Migration Matters Scotland Project, co-financed by the European Fund for the Integration of Third Country Nationals, focuses on understanding and supporting the needs of migrants while building the capacity of local authorities. Key aims include facilitating migrant participation in policy formu
0 views • 12 slides
Unleashing Creativity: The Power of Storytelling Toolkits
Dive into the world of storytelling toolkits and learn how they can spark creativity, lead your narrative in unexpected directions, and infuse your writing with uniqueness and flair. Discover the art of rewriting a wizard's description using innovative techniques like Dadwavers to break traditional
0 views • 9 slides
Role-based Access Control Policies and Security Properties Overview
This content provides an overview of Role-based Access Control (RBAC) policies, Administrative RBAC (ARBAC) systems, and security properties in the context of access control in large organizations. It discusses the implementation of RBAC in various software systems, the assignment and revocation of
0 views • 18 slides
Active Learning Community for Upskilling Technicians and Engineers Program
This program, under ERASMUS+ Key Activity 2, aims to address skill gaps in the workforce impacted by Industry 4.0. It focuses on transversal, technological, and adaptive skills through active, problem-based, blended learning methods. The main outcomes include surveys on skills deficits, toolkits on
0 views • 9 slides
Open Access at Charles University: Opportunities and Challenges
Charles University is navigating the landscape of open access following the implementation of the Czech National Open Access Strategy. The university is working towards making all research articles and proceeding papers open access, monitoring article processing charges, and promoting open access as
0 views • 24 slides
Advancing Recognition of Prior Learning for Artisan Trade Workers
Artisan RPL Presentation highlights the socio-economic rationale behind the Artisan RPL program to provide formal recognition for semi-skilled trade workers. The project aims to address past imbalances, establish a clear pathway to trade tests, and standardize ARPL practices across sectors. Various
0 views • 9 slides
Understanding the Victorian Regulatory Change Measurement (RCM)
The Victorian Regulatory Change Measurement (RCM) methodology introduced in June 2010 aims to measure reductions in regulatory burden through different categories such as administrative costs, substantive compliance costs, delay costs, and more. The RCM formula helps in calculating the total regulat
0 views • 63 slides
Exploring Arts Integration in Education
Learn about the significance of intentional integration of arts into academic subjects, understand the difference between integration and hitching, explore sample project ideas incorporating arts instruction, and discover tools for successful integration in education. Dive into resources, toolkits,
0 views • 29 slides
Understanding Filesystem Security Principles and Access Control
Learn about filesystem security, general principles, discretionary access control (DAC), closed vs. open policy, closed policy with negative authorizations, and access control entries and lists. Discover how files and folders are managed, the role of access control lists (ACLs), and the different le
1 views • 56 slides
Understanding Ethernet and Multiple Access Protocols in Computer Networks
Exploring the fundamentals of Ethernet and multiple access protocols in computer networks, this content discusses the two primary categories of multiple access protocols - contention access and controlled access. It delves into topics such as CSMA/CD, LANs, performance of multiple access schemes, ad
0 views • 7 slides
Recruitment and Retention of Remote and Rural Health Care Staff in Scotland: Business Case
The Scottish Local Implementation Committee proposes a project focusing on recruitment and retention of non-medical staff in rural areas to tackle workforce challenges. The aim is to develop community-based solutions and toolkits to enhance staff recruitment and retention, addressing the specific ne
0 views • 14 slides
Enhancing Helicopter Safety Through IHST Initiatives
The International Helicopter Safety Team (IHST) is dedicated to reducing global helicopter accident rates through collaborative efforts between government and industry stakeholders. By analyzing data and developing safety toolkits, IHST aims to achieve an 80% reduction in accidents by 2016. Key focu
0 views • 11 slides
Building Collaborative Workplace Models for Managing Disabilities in a Unionized Environment
This workplace model focuses on managing physical and psychological disabilities in a unionized setting, emphasizing cooperation between management, labor, and health professionals. Success lies in early rehabilitation, joint disability management, and return-to-work programs. Programs like the Heal
0 views • 22 slides
Harvard Chan School 2021 Yearly Access Review Process
The Harvard Chan School conducts its annual Yearly Access Review (YAR) process to review user access to various financial systems. The process involves assessing permissions, levels of access, and organizational details for each team member. Instructions are provided on reviewing worksheets, adding
0 views • 19 slides
Understanding Security Access in PeopleSoft Finance
Explore the various levels of security access in PeopleSoft Finance, from basic entry access to transaction entry, approvals, and procurement processes. Learn how to request individual and department security access and find relevant forms on the financial services website. Discover the different ty
0 views • 11 slides
Application Log Processing Methodologies in Service-Oriented Architecture
Understanding the methodologies for processing application logs in a service-oriented architecture, including data collection, purpose, programming language toolkits, centralized log collection, non-discardable logs collection, event/enterprise bus integration, cloud platform data collection, and Ku
0 views • 13 slides
Reinforcement Learning for Long-Horizon Tasks and Markov Decision Processes
Delve into the world of reinforcement learning, where tasks are accomplished by generating policies in a Markov Decision Process (MDP) environment. Understand the concepts of MDP, transition probabilities, and generating optimal policies in unknown and known environments. Explore algorithms and tool
0 views • 11 slides
Mastering Writing for Publication: Strategies and Toolkits
Enhance your writing skills with practical strategies and essential toolkits for publication. Learn how to select a research program, develop your writing style, and understand the writing process effectively. Dive into the world of writing with guidance from experts in the field.
0 views • 18 slides