Non Coronary Vascular Stents
Safe scanning of patients with non-coronary vascular stents (NCVS) in MRI settings in NHS Scotland. It covers key questions regarding the safety of patients with NCVS, including risks associated with MRI at different strengths, timing of MRI post-stent implantation, and the safety of various stent m
1 views • 9 slides
Evolution of CT Scan Technology and Terminology
The development of CT scanning technology revolutionized medical imaging. Godfrey Hounsfield introduced computerized axial transverse scanning in 1972, with Allan Cormack's mathematical contributions. Dr. Robert Ledley created the first whole-body CT scanner in 1974. Dr. Willi Kalender further advan
1 views • 121 slides
Enhancing Cybersecurity with Bluedog VAPT Services
Bluedog Security Monitoring offers essential cybersecurity services, including Vulnerability Assessment and Penetration Testing (VAPT). Their automated VAPT combines External Vulnerability Scanning and WebApp Scanning to provide comprehensive testing solutions that help businesses prioritize risks,
0 views • 16 slides
Environmental Scanning Techniques for Business Adaptation
Businesses are integral parts of society and must stay abreast of surrounding changes to thrive. Environmental scanning is crucial for businesses to adapt and evolve effectively.
0 views • 9 slides
Improve Your Reading Skills: Scanning and Skimming Techniques
Enhance your reading skills by mastering the art of scanning and skimming. Learn how to efficiently search for specific information without reading every word. Discover tips for scanning different types of texts and practice answering questions based on scanned content.
9 views • 12 slides
Explore the World of Computer Graphics in CSE452
Dive into the fascinating realm of computer graphics with CSE452. Learn about modeling, rendering, animation, and its various applications in entertainment, design, education, and more. Discover the techniques of computer-aided design, 3D scanning, procedural modeling, and rendering for photorealist
12 views • 24 slides
Advances in Particle Therapy: Slow Extraction and Dose Delivery at Medical Facilities
Medical facilities, like Heidelberg University Hospital, utilize advanced techniques such as slow extraction and raster scanning for precise dose delivery in particle therapy. The demands on these facilities include safe and precise beam parameters, uninterrupted therapy sessions, and fast irradiati
2 views • 23 slides
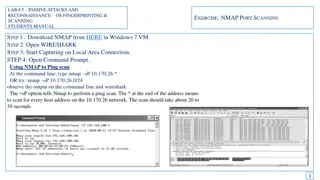
Passive Attacks and Reconnaissance using NMAP for Network Scanning
Learn how to use NMAP for passive attacks and reconnaissance through port scanning techniques like ping scan, TCP port scan, and stealth scan. Understand how to analyze the output in Wireshark to identify open ports and version numbers on target systems.
2 views • 7 slides
Passive Attacks and Reconnaissance in Network Security
Passive attacks involve monitoring target systems through port scanning or other means to locate vulnerabilities. Scanning is the first active action taken against a target network based on information gathered through footprinting, allowing deeper penetration. It includes scanning ports and service
0 views • 24 slides
Network Traffic Analysis with Wireshark: Examples and Techniques
Explore the world of network traffic analysis using Wireshark through examples and practical techniques. Learn how tools like Nmap and Wireshark can be used for network scanning and detecting suspicious activities. Dive into real examples, including identifying attackers through HTTP web traffic ana
1 views • 10 slides
Environmental Scanning Tool for Strategic Workforce Planning Cycle
In the Compare stage of strategic workforce planning, utilizing the Environmental Scanning Tool can assist in identifying work and workforce scenarios to achieve organizational goals. The tool consists of three templates including Choosing the Right Type of Data, Environmental Scanning Template, and
1 views • 9 slides
Techniques for Monitoring Asbestos Fiber Concentration in Ambient and Indoor Air using SEM
Explore the methods and results of an international proficiency testing (PT) scheme for measuring asbestos fibers in indoor and ambient air. The use of Scanning Electron Microscope (SEM) based techniques, including ISO 14966 and VDI 3492 guidelines, is discussed. The importance of PT schemes in ensu
0 views • 27 slides
Effective Reading Strategies: Skimming and Scanning Techniques
Develop your reading skills with skimming and scanning techniques. Skimming helps you quickly grasp the main ideas of a text, while scanning allows you to find specific information efficiently. Learn how to differentiate between the two methods and when to use each effectively.
0 views • 7 slides
Disaster Recovery and Incident Response Concepts
This content covers the essential concepts of disaster recovery, incident response, penetration testing, vulnerability scanning, and business continuity planning in the context of cybersecurity. It explains the goals and steps involved in penetration testing, vulnerability scanning tasks, business c
2 views • 15 slides
Network Monitoring and Vulnerability Scanning Overview
Kashif Mohammad from the Department of Physics at the University of Oxford provides insights into their setup involving ZEEK, ELK Monitoring, and OpenVas for network monitoring and vulnerability scanning. The team aims to enhance network security through structured classification of nodes based on t
1 views • 10 slides
Understanding Scanning in Thin Clients, RDP, and Citrix Environments
Learn about the difference between Fat Clients and Thin Clients, various types of Thin Clients, reasons for using Thin Clients, how programs are accessed on servers, and issues with scanning in RDP connections in this informative guide. Discover why Thin Clients are preferred for centralized softwar
1 views • 16 slides
Understanding Functional Skills: Text Analysis and Application
This instructional text guides learners through the purpose of functional skills in analyzing different types of text, such as skimming and scanning, and understanding the features of various text genres. It includes activities to practice skimming, scanning, and detailed reading, with a focus on de
0 views • 13 slides
Implementing Barcode Scanning to Reduce Dispensing Errors in Pharmacy
Implementation of barcode scanning in pharmacy departments has been shown to significantly reduce dispensing errors, ensuring greater accuracy in medication dispensation. Despite the generally low error rate among pharmacists, high volumes of dispensing can still lead to a substantial number of erro
1 views • 20 slides
Understanding the Array Scanning Method in Electromagnetics
Exploring the Array Scanning Method (ASM) for analyzing the field of a single source near an infinite periodic structure. The notes cover the geometry, analysis, phasing, and field calculations involved in an infinite 2D periodic array of metal patches excited by dipole sources, providing insights i
0 views • 25 slides
Essential Skills for Safe Biking
Develop crucial skills to enhance safety while biking, such as scanning behind, communicating with other road users, being predictable, mastering straight line riding, and balancing to avoid hazards without swerving into traffic. Gain insights on crash avoidance techniques, interaction with drivers,
3 views • 8 slides
What Are the 5 Benefits of Choosing an Advanced MRI Scanning Centre in Panchkula for Accurate Diagnosis
early diagnosis is equally important in treatment. If you are in Panchkula or the places nearby, it is a very wise decision to opt for a modern MRI scanning centre, for example, Kior Healthcare.
1 views • 3 slides
Understanding Breast Ultrasound: Anatomy, Patient Preparation, and Scanning Protocol
This informative content delves into breast ultrasound, covering topics such as breast anatomy, patient preparation and positioning, scanning protocol, required images, and normal sonographic appearances. It provides valuable insights into the structure and composition of the breast, guidelines for
0 views • 8 slides
Comprehensive Guide to Intelligence Gathering and Penetration Testing Stages
Understanding the importance of intelligence gathering in security and the stages of penetration testing - information gathering, scanning, exploitation, and reporting. Delve into tools like nslookup for server information and leverage Google Dorks for database vulnerabilities. Safeguard your system
0 views • 4 slides
Understanding the Impact of New Diagnostic Technology in Insurance
Explore the latest advancements in diagnostic technology for predicting and diagnosing cardiac conditions like CHD. Learn about new techniques such as high-tech scanning, biomarker identification, and predictive testing, and understand how these innovations can influence insurance products and risk
0 views • 15 slides
Effective Reading and Listening Strategies in Language Teaching
Explore the various purposes and tasks involved in communicative language teaching, focusing on reading and listening skills development. Understand the importance of activating schemata, developing reading strategies, and language production activities such as speaking and writing. Delve into diffe
0 views • 39 slides
Mastering Reading Techniques: Skimming, Scanning, and Business Insights
Enhance your reading skills with a focus on skimming, scanning, and understanding business concepts such as commercial vs. retail, B2B vs. B2C, and online shopping trends. Dive into the specifics of general vs. specific information retrieval and learn about dual pricing strategies in the retail sect
0 views • 20 slides
Different Reading Techniques: Skimming and Scanning Explained
Reading involves the process of gaining meaning from text using eyes and brain. Skimming and scanning are two specific types of reading techniques that help readers to quickly grasp the main idea or find specific information in a text. Skimming is like gist reading, where you get a general idea of t
0 views • 17 slides
Understanding Unix/Linux Hacking Techniques
Explore Unix/Linux hacking techniques including footprinting, scanning, enumeration, vulnerability mapping, remote access, data-driven attacks, buffer overflow, input validation, and countermeasures. Discover methods to gain root access, exploit vulnerabilities, perform brute force attacks, and secu
0 views • 6 slides
Enhancing Network Security Through Multi-Core Packet Scattering and Deep Packet Inspection
Explore the use of multi-core systems to tackle performance bottlenecks in network intrusion detection systems, specifically focusing on deep packet inspection. Techniques such as load balancing and pattern subset scanning are discussed to optimize DPI processes and improve overall network security
0 views • 43 slides
Understanding Reconnaissance in Cybersecurity: Methods and Techniques
Reconnaissance is a crucial initial step in cyber attacks, involving gathering information about targets through active or passive methods. Active reconnaissance techniques include host discovery, port scanning, service version detection, and OS fingerprinting. This process aids in identifying vulne
0 views • 14 slides
Introduction to Algorithms and Sorting Techniques
Brute force and exhaustive search are fundamental problem-solving approaches in algorithm design, while selection sort and bubble sort are common sorting techniques. Brute force involves solving problems directly based on the problem statement, with the computer carrying out the computations. Select
0 views • 18 slides
Comprehensive Guide to Hacking Techniques & Intrusion Detection
Dive into the world of hacking techniques, intrusion detection, and network protocols with expert Ali Al-Shemery. Learn about host discovery, port scanning, packet crafting, and more using tools like Nmap. Explore the importance of network protocols like TCP, UDP, ICMP, and ARP. Discover the art of
0 views • 50 slides
Cybersecurity Footprinting and Scanning Techniques
Learn about the techniques involved in cybersecurity footprinting and scanning to protect against information gathering, target acquisition, and unauthorized access. Explore topics such as network enumeration, DNS interrogation, and scanning methods to identify vulnerabilities and enhance security m
0 views • 8 slides
Process of Launching an Enterprise: From Scanning Environment to Market Research
The process of launching an enterprise involves scanning the environment, locating business opportunities, converting opportunities into reality, conducting market research, developing a business plan, and managing the entrepreneur. It starts with analyzing the external and internal environment, fol
0 views • 8 slides
Understanding Scanning Electron Microscopes (SEM) and Electron Sources
Scanning Electron Microscopes (SEMs) utilize focused electron beams to produce high-resolution images by interacting with a sample's electrons. The electron source, such as the electron gun, plays a crucial role in forming fine electron beams for imaging purposes. Different types of electron sources
0 views • 12 slides
Exploring Atomic Dimensions: Scanning Probe Microscopy
Delve into the world of nanoscale imaging with Scanning Probe Microscopy (SPM) techniques like Scanning Tunneling Microscopy (STM) and Atomic Force Microscope (AFM). Unlike optical microscopes, SPM methods break the diffraction limit by relying on intermolecular forces and quantum tunneling for unpa
0 views • 26 slides
Exploring Confocal Microscopy: Adding the Third Dimension
Delve into the world of confocal microscopy with Lecture 07 of Principles of Modern Microscopy. Learn about optical sectioning, wide-field imaging, confocal laser scanning, and more to enhance fluorescence in microscopy. Understand the methods of optical sectioning such as deconvolution, multi-photo
0 views • 65 slides
Advantages of Scanning Lidars in Wind Resource Assessment
Scanning lidars offer a cost-effective and flexible solution for wind resource assessment compared to traditional met masts. They provide multi-point measurements without the need to relocate hardware, reducing uncertainties and risks in wind energy projects. This technology enhances the accuracy of
0 views • 10 slides
Effective Reading Techniques: Skimming, Scanning, and More
Explore different reading techniques like skimming, scanning, extensive reading, and intensive reading. Skimming helps to quickly grasp the main idea, while scanning is useful for finding specific information. Extensive reading is for pleasure, while intensive reading involves deep understanding and
0 views • 6 slides
Enhanced AC Coefficients Compression Techniques
Explore improved methods for compressing AC coefficients in JPEG coding, utilizing alternate adaptive scanning and multi-feature determined context arithmetic coding. The approach involves scanning order determination, entropy coding, and arithmetic coding techniques to enhance compression efficienc
0 views • 10 slides