RAZER LAPTOP REPAIR
Razer laptops, renowned for their high-performance gaming capabilities, are subject to various repair needs, ranging from hardware malfunctions to software issues. Common repair tasks include replacing damaged screens, keyboards, or batteries, addressing overheating problems by cleaning or replacing
2 views • 3 slides
Understanding Alinity i STAT High Sensitivity Troponin-I for Cardiovascular Diagnosis
Alinity i STAT High Sensitivity Troponin-I is a proprietary assay used in diagnosing myocardial infarction (MI) by quantitatively measuring cardiac troponin I in human plasma. This chemiluminescent microparticle immunoassay (CMIA) aids in the detection of MI, a significant aspect in managing heart d
2 views • 30 slides
Service Unit Cookie Training
Explore the exclusive 2024 Girl Scout Cookie training program, nutritional details, vegan ingredient varieties, and essential program basics. Learn about the program dates, pricing, cookie lineup, and important guidelines for troops and participants. Dive into the world of delicious cookies and empo
0 views • 40 slides
How BI Software Tools Secure Sensitive Business Information
Protecting sensitive business information is more important than ever. BI software tools play a crucial role in securing data through advanced security features such as data encryption, user access controls, real-time monitoring, audit trails, and data anonymization. These tools not only safeguard f
1 views • 6 slides
Unlocking Educational Synergy with DIKSHA & Google Classroom
Explore the proprietary and confidential collaboration between DIKSHA and Google Classroom to enhance educational synergy. Learn how to access, create, organize, and share content seamlessly, empowering educators and students alike. Dive into self-assessment tools, math lab activities, and more for
0 views • 27 slides
Understanding Different Types of Specifications in Estimation and Costing
In the field of estimation and costing, four main methods of specifying are used: Descriptive, Performance, Reference Standard, and Proprietary. Descriptive specifications provide detailed descriptions without using proprietary names, allowing for tight control over specified work. Performance speci
1 views • 9 slides
Understanding AARCH64 Linux Kernel Memory Management
Explore the confidential and proprietary details of AARCH64 Linux kernel memory mapping, virtual memory layout, variable configurations, DDR memory layout, and memory allocation techniques. Get insights into the allocation of physically contiguous memory using Continuous Memory Allocator (CMA) integ
0 views • 18 slides
Rocket Trades - Innovative Trading Strategy for Enhanced Accuracy
Rocket Trades is a Bengaluru-based firm established in 2016, offering a proprietary trading strategy focused on futures swing and directional trading in various financial instruments. Their unique approach combines technical data, fundamental analysis, and macro sentiment to capture market movements
0 views • 23 slides
Request for Intervention from Standing Committee on Finance in Matters Involving MMI and PIC
Matome Maponya Investment (MMI) Proprietary Limited, along with related entities and the Public Investment Corporation (PIC), seek intervention from the Standing Committee on Finance. MMI, a company founded in 1995 focusing on investment, agro-business, retail, property, and lifestyle offerings, is
0 views • 32 slides
Financial Management in Proprietary Funds and Water Utility Fund Transactions
This content covers topics related to proprietary funds, specifically addressing closure and post-closure care costs of a landfill in Montgomery County and transactions in the Water Utility Fund of the Town of Weston. It includes calculations, trial balances, accrued expenses, billings, liabilities,
0 views • 57 slides
Understanding System Management Mode (SMM) in x86 Processors
System Management Mode (SMM) is a highly privileged mode in x86 processors that provides an isolated environment for critical system operations like power management and hardware control. When the processor enters SMM, it suspends all other tasks and runs proprietary OEM code. Protecting SMM is cruc
1 views • 26 slides
Manage Student Assessment System Overview
This system allows users to set up assessment weightages for subjects, catering to school exam secretaries, subject teachers, and class teachers. It facilitates managing assessment activities like setting weightage percentages, exam types, entering marks, and providing comments for students. The sys
1 views • 88 slides
IEEE 802.11-19/1517r0 TDD Beamforming Configuration Overview
IEEE 802.11-19/1517r0 discusses TDD beamforming operations related to Beam Measurement in the standard. Before Draft 4.0, these operations were primarily initiated by SME, causing limitations due to proprietary network controllers. The document reviews gaps and improvements in TDD beamforming, aimin
0 views • 10 slides
Fund Accounting Overview and Types of Funds in Governmental Accounting
Fund accounting in governmental organizations involves segregating financial resources into self-balancing accounts to facilitate specific activities and objectives. This practice ensures compliance with regulations and restrictions, such as GAAP and state laws. Various types of funds, including gov
0 views • 41 slides
Revolutionizing Communication with ENUMER: A Decentralized Approach
Traditional telephone systems rely on a chain of PSTN providers for call routing, leading to issues such as multiple re-codings and extra fees. ENUMER, a decentralized version of ENUM, offers a faster, more reliable, and cost-effective solution by allowing direct paths from buyer's PBX to seller, by
0 views • 12 slides
Managing Student Progression Tool for Academic Programs
This tool enables school student registrars to progress students within the same academic program seamlessly. Users need to run the Attendance Statistics Calculation process before advancing students. The tool allows verifying student progress, manually editing wrong progression, and retaining stude
0 views • 46 slides
Texas Association For Home Care & Hospice Regulatory Updates July 2023
HHSC has announced regulatory updates for Electronic Visit Verification (EVV) requirements for Medicaid services in Texas starting January 1, 2024. Providers must transition to the new vendor system, HHAeXchange, by October 1, 2023. The updates also cover the application process for becoming an HHSC
0 views • 11 slides
Exploring Computer Ethics and Privacy Principles
Computer ethics and privacy principles are essential in the evolving technology landscape. This content delves into different perspectives on computer ethics, views on privacy protection, and the implications of human enhancements. It highlights the importance of respecting proprietary rights, shari
0 views • 9 slides
Colorado Broadband Data Collection Update and Infrastructure Enhancements
Updating the Colorado broadband data collection process with legislature funding for staff and GIS data coordination. Focus on nuanced data collection for various potential uses such as DOLA grants, broadband planning, and provider marketing. Statewide broadband mapping shows improved speeds for hou
1 views • 26 slides
Rochester Public Utilities Presentation on True-up of Attachment O Transmission Revenue Requirements
Rochester Public Utilities (RPU) holds annual meetings to discuss and provide information on the calculation of the True-up of RPU's 2016 Annual Transmission Revenue Requirements. The presentation also covers the True-up Adjustment applied to the 2018 Forward-Looking Rate. RPU uses a FERC-approved F
0 views • 14 slides
Game Engines & GPUs: Current & Future Intersection with Graphics Hardware
Explore the current and future landscape of graphics hardware in relation to game engines and GPUs. Delve into the use cases, implications, and advancements in areas such as shaders, texturing, ray tracing, and GPU compute. Learn about Frostbite, DICE's proprietary engine, and its focus on large out
0 views • 45 slides
Nose Landing Gear PN 162A1100-9 SN MAL00720Y1576 Information
This document contains technical data and summary information related to Nose Landing Gear with Part Number 162A1100-9 and Serial Number MAL00720Y1576, including details on total time, cycles, overhaul, associated aircraft model, and next overhaul date. Additionally, it provides access to non-incide
0 views • 7 slides
Understanding ETPL Requirements and Approval Process
The North Carolina ETPL (Eligible Training Provider List) is a crucial resource that lists all approved WIOA training programs and providers. To be eligible for WIOA funds, providers must go through a two-step approval process involving the state agency and local workforce development boards. The ET
0 views • 15 slides
Understanding Sovereign Immunity and Contracts in Legal Context
Explore the intricacies of sovereign immunity and contracts in legal settings, including waivers, elements of immunity waiver, contractual implications, and the distinction between proprietary and governmental functions of local governmental entities. Delve into the key aspects that govern these leg
0 views • 14 slides
The Impact of Open Source Library Automation Systems
Marshall Breeding discusses the rise of open source library automation systems globally, comparing them to proprietary alternatives. He explores the adoption of open source products in the US and their coverage in international library reports, highlighting how libraries of different budgets utilize
0 views • 38 slides
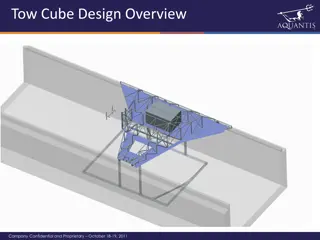
Tow Cube Design Overview - Company Confidential and Proprietary
Tow Cube Design Overview images showcasing various aspects of the design project conducted on October 18-19, 2011. Includes details on attachment plates, preliminary stress analysis, and displacement analysis. The images provide insights into the dimensions and features of the design, illustrating t
0 views • 8 slides
Zillow Kaggle Competition Overview and Incentives
Zillow hosted a Kaggle competition with the objective of predicting log errors in their proprietary model. The competition involved feature engineering, unconventional methods, and a focus on neighborhood similarity. Scoring was based on Mean Absolute Error, with private scoring updates after the co
0 views • 47 slides
Recent Developments in English Law of Tracing & Unjust Enrichment
Recent decisions in English law show a shift in tracing & unjust enrichment practices. Cases like Brazil v. Durant and Bank of Cyprus v. Menelaou indicate a move towards a looser causal connection requirement. The discussion on backwards tracing and unjust enrichment has evolved from the Court of Ap
0 views • 18 slides
Selecting Transferable Gen Ed Courses for Ohio Public Institutions
Stakeholders preparing the Transferability Strategic Plan in Ohio emphasize the importance of selecting transferable General Education courses from proprietary to public institutions. This involves identifying widely taken Gen Ed courses and using enrollment data from Ohio public institutions to det
0 views • 17 slides
Overview of Antitrust Cases and Multistate Enforcement in U.S. Legal History
The content provides a historical overview of significant antitrust cases and multistate enforcement actions in the United States, including key court rulings and landmark legal proceedings involving state participation and enforcement of antitrust laws. It covers cases such as State of Georgia v. E
0 views • 18 slides
Rochester Public Utilities - Forward-Looking Transmission Revenue Update
Rochester Public Utilities (RPU) presents an update on the forward-looking transmission revenue requirements for calendar year 2021. The presentation covers the regulatory background, rate calculations, and adjustments for the upcoming year. Key topics include the FERC-approved formula rate, true-up
0 views • 13 slides
Fiscal Year 2016 Budget Presentation Overview
Budget Presentation for Fiscal Year 2016 covering Proprietary, Special Revenue, and Capital Funds. Includes a detailed timeline of financial activities, such as quarterly reviews, budget workshops, public hearings, and fund-specific analyses for Enterprise Funds like Solid Waste and Information Tech
0 views • 43 slides
Evolution of English Law: From Common Law to Equity and Beyond
The historical origins and development of English law are traced from the XIV century when Equity emerged as a supplement to Common Law, to the XVI and XVII centuries marked by conflicts between the King and Parliament, the establishment of the Star Chamber, and victory of Parliament over the King.
0 views • 22 slides
Tools for Automated Data Persistence and Quality Control in Financial Environment
The Schonfeld Environment, a registered investment firm, utilizes kdb+ for data management. Challenges involve persisting, automating, and ensuring quality control of proprietary data. The Persistence API facilitates secure and efficient management of derived datasets.
0 views • 13 slides
Understanding VLAN Trunking Protocol (VTP) in Networking
VLAN Trunking Protocol (VTP) is a Cisco proprietary protocol that simplifies the management of VLAN configurations across switches in a network. VTP allows for consistency in VLAN setup and reduces configuration errors by enabling changes to be propagated automatically. Different VTP modes control h
0 views • 18 slides
The Importance of Free and Open Instruction Sets in the Computer Industry
Explore the significance of free and open instruction sets in the realm of computing, emphasizing the benefits of innovation, market competition, transparency, and affordability in processor design. The discussion delves into the impact of proprietary ISAs, the role of industry standards, and the po
0 views • 27 slides
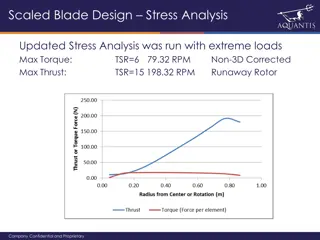
Scaled Blade Design and Rotor Progress Updates
This series of images showcases the stress analysis, extreme loads testing, loft and tooling progress, and hub design updates for a scaled blade design project. The stress analysis includes considerations for torque, thrust, and safety factors, with images detailing the results and adjustments made.
0 views • 6 slides
Future Vision for IEEE 802.11 in 5G Networks
This submission discusses the potential role of IEEE 802.11 as a component in future 5G networks, addressing challenges and opportunities. It presents insights on managing 802.11 within non-proprietary interfaces, emphasizing compatibility and defined functions for seamless integration in advanced n
0 views • 37 slides
Solutions for Demanding Business in South Eastern Europe Banking System
Explore how Asseco South Eastern Europe is responding to the challenges of the crisis in the banking system and economy. As a key player in the region, they offer tailored solutions, with a focus on proprietary software and services, for banks and the public sector. With a strong presence in multipl
0 views • 5 slides
Proprietary Trading_ A Strategy for Financial Excellence
Proprietary trading involves firms using their own capital to trade for profit, providing traders with firm funds, advanced tools, and profit-sharing opportunities. It\u2019s a dynamic route to financial growth.
0 views • 3 slides