Apache MINA: High-performance Network Applications Framework
Apache MINA is a robust framework for building high-performance network applications. With features like non-blocking I/O, event-driven architecture, and enhanced scalability, MINA provides a reliable platform for developing multipurpose infrastructure and networked applications. Its strengths lie i
3 views • 13 slides
Modeling and Generation of Realistic Network Activity Using Non-Negative Matrix Factorization
The GHOST project focuses on the challenges of modeling, analyzing, and generating patterns of network activity. By utilizing Non-Negative Matrix Factorization (NMF), realistic network activity patterns can be created and injected into live wireless networks. Understanding and predicting user behavi
4 views • 28 slides
Automated Anomaly Detection Tool for Network Performance Optimization
Anomaly Detection Tool (ADT) aims to automate the detection of network degradation in a mobile communications network, reducing the time and effort required significantly. By utilizing statistical and machine learning models, ADT can generate anomaly reports efficiently across a large circle network
8 views • 7 slides
Buy 145 ENGINE WELDER GENERATOR Online - marcosengines.com
The Lincoln Outback 145 Engine Welder Generator built for the outdoors. It is a good option for service trucks, fence contractors, farmers, ranchers, maintenance crews, and anyone else who needs portable DC stick welding and AC generator power. Phone: (929) 376\u20137413 Email: info@marcosengines.co
3 views • 3 slides
Revolutionizing Network Management with Intent-Based Networking
Explore the concept and benefits of Intent-Based Networking (IBN) in simplifying network configuration and enhancing efficiency. Learn how IBN automates network operations, aligns with business objectives, improves security, and ensures scalability and reliability. Discover the potential of IBN tool
0 views • 14 slides
Proposed Enhancements for Generator Interconnection Process
Enhancements proposed for the generator interconnection process include creating a distinction between large and small generators, establishing tracking processes for small generators, and modifying existing sub-sections to incorporate small and large generators in Sections 5 and 6. The goal is to s
1 views • 12 slides
Network Compression Techniques: Overview and Practical Issues
Various network compression techniques such as network pruning, knowledge distillation, and parameter quantization are discussed in this content. The importance of pruning redundant weights and neurons in over-parameterized networks is highlighted. Practical issues like weight pruning and neuron pru
0 views • 37 slides
Network Slicing with OAI 5G CN Workshop Overview
Overview of Network Slicing with OAI 5G CN workshop focusing on the crucial role of network slicing in realizing the service-oriented 5G vision. This workshop covers topics like multiple logical networks creation on shared infrastructure, different types of network slices, preparation and instantiat
1 views • 6 slides
Network Design Challenges and Solutions in Business Data Communications
Issues in designing a Local Area Network (LAN) include needs analysis, technological design, and cost assessment. The traditional approach involves structured systems analysis, but faces challenges due to rapidly changing technology and increasing network traffic. The Building Blocks Approach recomm
1 views • 20 slides
Understanding 5G RAN Network Slicing and Architecture
Explore the intricate world of 5G Radio Access Network (RAN) and Network Slicing, delving into concepts such as SO Service Orchestrator, SDN-C Service Design, and Core Network Elements. Discover the significance of managing and designing mobile slice services, including eMBB, Massive IoT, and Missio
0 views • 26 slides
Understanding Snort: An Open-Source Network Intrusion Detection System
Snort is an open-source Network Intrusion Detection System (NIDS) developed by Cisco, capable of analyzing network packets to identify suspicious activities. It can function as a packet sniffer, packet logger, or a full-fledged intrusion prevention system. By monitoring and matching network activity
0 views • 23 slides
Updates on Generator Interconnection Procedures and Agreements Reform
ISO-NE is implementing further compliance reforms in response to FERC Order No. 845 regarding Generator Interconnection Procedures and Agreements. This includes proposed tariff language updates and discussions on surplus interconnection services. The changes aim to enhance the efficiency and effecti
0 views • 14 slides
Data Flows and Network Challenges in Particle Physics Infrastructure
This overview delves into the data flows and network challenges faced in particle physics infrastructure, focusing on the JUNO project. It discusses the process of data reception, storage, and replication across various data centers, highlighting the bidirectional nature of data flows. Additionally,
0 views • 24 slides
Enhancing Generator Telemetry Transparency for ERCOT
This document discusses telemetry issues, recommendations for generator systems, and a proposed solution (NPRR 1085) to improve ERCOT's system health transparency. It highlights the need for better communication of uncertainty in telemetry, clarity in updating telemetry, and mechanisms to align gene
0 views • 14 slides
Progress of Network Architecture Work in FG IMT-2020
In the Network Architecture Group led by Namseok Ko, significant progress has been made in defining the IMT-2020 architecture. The work has involved gap analysis, draft recommendations, and setting framework and requirements. Phase 1 focused on identifying 19 architectural gaps, such as demands for
1 views • 11 slides
Modeling Water Leak into Sodium in BN-600 Steam Generator
This paper discusses the modeling of a water leak into sodium in the BN-600 steam generator during a specific incident in 1982. It compares calculated data with leak detection system indications and analyzes hydrodynamic parameters in the second sodium circuit. The study utilized SLEAK and LLEAK-3C.
10 views • 9 slides
Design Overview of AC Bus Hybrid System Workshop
This content provides a walkthrough of the design decisions involved in an AC Bus Hybrid System Workshop, focusing on the use of a generator and PV array. It covers the scenario of a village using a diesel generator, customer requirements, site information, system arrangement, and more to help under
0 views • 51 slides
Understanding Interconnection Networks Topology
Exploring the topology of interconnection networks helps determine the arrangement of channels and nodes, impacting network cost, performance, latency, energy consumption, and complexity of implementation. Abstract metrics such as degree, hop count, and network diameter play crucial roles in evaluat
1 views • 56 slides
Transportation Network Modeling and Analysis with C.Coupled SE Platform
This content outlines the features and functionalities of the C.Coupled SE Platform (CSET Platform) developed by the Connetics Transportation Group. It covers aspects such as interface design, inputs merging, purposes, platform development using Cube, TAZs merging, and network attributes. The platfo
0 views • 11 slides
Human Disease Symptom Network: Understanding Disease Relationships Through Symptoms and Genes
The Human Disease Symptom Network (HSDN) is constructed using a large-scale medical bibliographic records database to form a network of human diseases based on symptom similarities. By integrating disease-gene associations and protein-protein interaction data, correlations between symptom similarity
0 views • 37 slides
Introduction to Network Analysis Using .NET
This presentation introduces the concept of network analysis using .NET in the humanities classroom. It provides a template for teaching and adapting network analysis tools for educational purposes. The guide explains the relevance of networks in processing and visualizing data, emphasizing the coll
0 views • 20 slides
Understanding Frame Pointer Attacks and Exploit Development with pwntools
Explore the concepts of frame pointer attacks, LD_PRELOAD usage, and exploit development with pwntools library. Discover how to spawn a shell using LD_PRELOAD or a constructor, along with the limitations and challenges associated with command-line exploitation.
0 views • 30 slides
Investigating Performance Bottlenecks in Smart Pointer Management
Investigation into performance issues caused by smart pointer manipulation, focusing on the use of boost
0 views • 8 slides
Meridian: An SDN Platform for Cloud Network Services
Meridian is an SDN platform developed by Mohammad Banikazemi, David Olshefski, Anees Shaikh, John Tracey, and GuohuiWang at IBM T. J. Watson Research Center. The platform focuses on providing cloud network services efficiently. It encompasses an architecture that enables faster and more convenient n
0 views • 21 slides
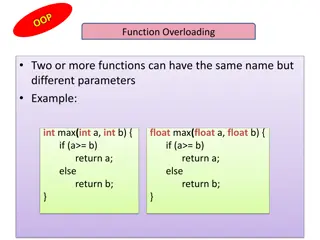
Understanding Function Overloading and this Pointer in C++
Explore the concept of function overloading in C++, allowing multiple functions with the same name but different parameters. Learn about the this pointer in object-oriented programming, which holds the memory address of the current object using a function. See examples of how to implement these conc
0 views • 13 slides
Enhancing Network Security with Software-Defined Snort and OpenFlow
Explore the implementation of Snort, Barnyard, and PulledPork within a Software-Defined Network framework using OpenFlow technology. Learn how these tools enhance network security through intrusion detection engines, rule management, and network traffic control mechanisms. Dive into the architecture
0 views • 15 slides
Effective S106 Process Management in Local Authority: Insights from Stephen Pointer, Harborough District Council
Explore the expertise of Stephen Pointer, Strategic Planning and Housing Manager at Harborough District Council, in managing an effective Section 106 (S106) process. Discover his role, responsibilities, and experiences in navigating the complexities of national and district contexts, community inter
0 views • 19 slides
Integrating Stochastic Weather Generator with Climate Change Projections for Water Resource Analysis
Exploring the use of a stochastic weather generator combined with downscaled General Circulation Models for climate change analysis in the California Department of Water Resources. The presentation outlines the motivation, weather-regime based generator description, scenario generation, and a case s
0 views • 20 slides
Exploring Wind Energy Systems Without Gearbox - Research Findings
Investigating wind energy systems without a gearbox reveals insights on turbine performance and generator efficiency. The data generated highlights differences in output power, current, and RPM between ideal and actual setups. Higher RPM allows for a wider selection of generators, although the curre
0 views • 5 slides
Understanding Network Analysis: Whole Networks vs. Ego Networks
Explore the differences between Whole Networks and Ego Networks in social network analysis. Whole Networks provide comprehensive information about all nodes and links, enabling the computation of network-level statistics. On the other hand, Ego Networks focus on a sample of nodes, limiting the abili
0 views • 31 slides
Code Pointer Integrity Team Overview
Code Pointer Integrity Team, consisting of Po-Jen Lai, Timmy Lin, Chun-Yu Hsiung, and Hung-Lin Wu, under the instruction of Scott Mahlke, is focused on understanding control flow hijack, memory control, and protection mechanisms. They explore new approaches to enhance code safety while minimizing ov
0 views • 25 slides
Automatic Generation of Research Highlights from Scientific Abstracts
Huge growth in scientific publications has made it challenging for researchers to keep up with new research. This project focuses on automatically constructing research highlights from paper abstracts using deep learning models. The system employs sequence-to-sequence models with attention and point
0 views • 9 slides
Understanding Pointers in C: A Beginner's Guide
Delve into the world of pointers in C with this comprehensive guide covering topics such as the address operator, pass by copy versus pass by reference, pointer usage, NULL pointers, pointer allocation, and practical experiments to enhance your understanding. Learn about the fundamentals of pointers
0 views • 22 slides
Understanding Smart Pointers in C++ - Bonus Lecture CSE390c Spring 2022
Explore the concept and benefits of smart pointers in C++ as a solution to managing heap-allocated memory more effectively. Learn about avoiding memory leaks and errors when handling pointers through smart pointer implementation. Dive into a Toy Smart Pointer example using a custom class template.
0 views • 36 slides
Network Function Virtualization (NFV) Overview
Network Function Virtualization (NFV) focuses on virtualizing network functions to improve efficiency and reduce costs in network infrastructure. The lecture discusses key readings, devices that compose a network, specialization of devices, benefits of one-device-does-anything approach, and the goal
0 views • 21 slides
Enhancing Network Stability with Network Monitoring Systems
Network monitoring is crucial for efficient management and proactive issue detection in a network environment. Factors influencing an effective network system include choosing the best OEM, SLA agreements, and selecting a reliable System Integrator. Reactive monitoring can lead to financial losses a
0 views • 12 slides
Valuation of Adding a Generator Option to a Community
This study focuses on evaluating the option value of adding a generator to a community's network, specifically at bus 1. The valuation is conducted by analyzing how electricity demand evolves over time and utilizing tools like demand lattice to map out future probable demand scenarios. The aim is to
0 views • 26 slides
Comparison of Generator Governor Dead-band Settings in ERCOT Interconnection
This report compares the generator governor dead-band settings in the ERCOT Interconnection for the years 2008 and 2015 from January to November. It outlines the changes in the dead-band settings over the years, including the requirements for proportional response, improvements in primary frequency
0 views • 17 slides
Accelerating Systemic Change Network Inaugural Workshop Summary
The Accelerating Systemic Change Network held its inaugural workshop at Howard Hughes Medical Institute in July 2016 to address the lack of coordination in improving higher education. With a vision to become a professional hub for change researchers in STEM education, the network aims to enhance ind
0 views • 5 slides
University Network Section Overview July 2015 - March 2016
The presentation covers the network team structure, team members, objectives, goals, report outline, network statistics, accomplishments, and future plans of the university network section from July 2015 to March 2016. It highlights efforts to provide stable internet and intranet services, restructu
0 views • 16 slides