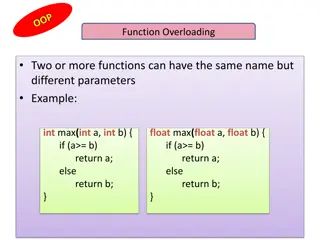
Code Pointer Integrity Team Overview
Code Pointer Integrity Team, consisting of Po-Jen Lai, Timmy Lin, Chun-Yu Hsiung, and Hung-Lin Wu, under the instruction of Scott Mahlke, is focused on understanding control flow hijack, memory control, and protection mechanisms. They explore new approaches to enhance code safety while minimizing overhead. The team also delves into threat models and safe regions versus regular regions for improved hardware-based isolation.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
Code-Pointer Integrity Team member: Po-Jen Lai, Timmy Lin, Chun-Yu Hsiung, Hung-Lin Wu Instructor: Scott Mahlke
What is Control flow hijack? 1. Attacker corrupts a data pointer 1. Overwrite the code pointer 1. Control-flow transferred to undesired code segment a. Attacker s shell code b. Gadgets (Undesired functions)
Memory Control flow hijack q char * buf = malloc(10) ... void * (func_ptr) (); char *q = buf + input1 func_ptr = &foo ... *q = input2 (*func_ptr)() buf func_ptr gadget
Control flow hijack protect (Softbound) Memory Metadata char * buf = malloc(10) buf_lo = p; buf_hi = p + 10; ... void * (func_ptr) (); char *q = buf + input1 q_lo = buf_lo; q_hi = buf_hi; func_ptr = &foo ... if ((q < q_lo) || (q >= q_hi)) abort() *q = input2 (*func_ptr)() q Propagate Metadata buf Check Metadata func_ptr gadget
Motivation Existing code safety methods are with high overhead. Memory safety method Overhead SoftBound 116% CCured 56% AddressSanitizer 73%
New approach 1. 2. Protect all data protect selected data 116 % overhead 2% - 8% overhead
Threat Model (Attackers capabilities) 1. 2. 3. Read / Write on process image (Memory) Read code but not write code No control over the program loading process
Safe Region vs Regular Region Protected vs unprotected Safe vs fast Hardware-based instruction-level isolation The mechanism for the isolation is architecture-dependent. Safe Memory Regular Memory Hardware-based isolation
Safe Region vs Regular Region Safe region Regular region Safe_ptr 2 Regular_ptr 2 Safe_ptr 1 Regular_ptr 1
Safe Region vs Regular Region Safe region Regular region Check! Safe_ptr 2 Regular_ptr 2 Safe_ptr 1 Regular_ptr 1
User modified data Safe Region vs Regular Region Safe region Regular region Check! Safe_ptr 2 Regular_ptr 2 Safe_ptr 1 Regular_ptr 1
Safe Stack Safely access local Guaranteed safe variables int foo(){ char buf[10]; int r = scanf( %s , buf); return r; } Safe Stack Regular Stack r return address buf
arrays or objects whose address is passed to other functions Safe Stack Safely access local Guaranteed safe variables int foo(){ char buf[10]; int r = scanf( %s , buf); return r; } Safe Stack Regular Stack r return address buf
arrays or objects whose address is passed to other functions Safe Stack Safely access local Guaranteed safe variables int foo(){ char buf[10]; int r = scanf( %s , buf); return r; } Anything might be corrupted Safe Stack Regular Stack r return address buf
Safe Stack All return instruction pointers are protected No ROP (return oriented programming) Zero performance overhead
Code-Pointer Integrity Sensitive pointer: code ptrs and ptrs that may later be used to access sensitive ptrs Only a small subset of all pointers are responsible for making control-flow transfers Enforcing memory safety only for control-sensitive data Over approximation at compile time
Instrumentation Ensure all sensitive pointers are stored in a safe region Create and propagate metadata at runtime Check the metadata on dereferences Metadata: bound, temporal ID Load/store CPI intrinsic instructions
Memory Layout Hardware-based instruction level isolation
Code-Pointer Separation (CPS) Simplified version of Code-Pointer Integrity Main Difference 1. Sensitive pointer = code pointer only 2. No need to store metadata 3. No runtime check Fewer security guarantees Lower performance overhead
Redirect object pointer Safe Memory Regular Memory obj1.pointer func_ptr2 Point_to_obj2 func_ptr1 obj2.pointer
Redirect object pointer Safe Memory Regular Memory obj1.pointer func_ptr2 Rewrite Point to obj1 func_ptr1 obj2.pointer
Security Guarantee Code-Pointer Integrity: formally guaranteed protection, 8.4% - 10.5% overhead (~6.5% of memory access) Code-Pointer Separation: strong protection in practice, 0.5% - 1.9% overhead (~2.5% of memory access) Safe Stack: Full ROP protection, negligible overhead
Current Status The latest version of LLVM only integrates Safe Stack Our proposed goals 1. CPS sensitive pointer detections 2. CPI sensitive pointer detections 3. Memory separation 4. Code generation