Academic Representation at Royal Holloway University
Academic representation at Royal Holloway University plays a crucial role in enhancing the educational experience for students. The system involves various levels of representation with specific responsibilities to ensure effective communication among students, Course Reps, and academic staff. Recen
3 views • 28 slides
Exploring micro:bit - The Next Gen Technocamps Partnership
Discover the collaboration between Technocamps and the micro:bit Foundation in Wales, bringing the new phase of micro:bit projects to students. Dive into what micro:bit can do, explore coding with Makecode, engage in fun activities like Emotion Badge coding, and learn how to use button events to con
0 views • 30 slides
Understanding 4-Bit Parallel Adder/Subtractor IC7483
Explore the concept of 4-bit parallel adder/subtractor using IC7483, which is a digital circuit capable of performing arithmetic operations on binary numbers greater than one bit in length. Learn about the structure, operation, and implementation of parallel adders with cascaded full adders. Discove
8 views • 11 slides
Daily current affairs 2024(presentation)
\u25ba Check this page for wide range of online courses: http:\/\/bit.ly\/kd-courses\n\nDo you want to get a Government job online course? Here are best govt job preparation courses :\n\n\ud83d\udc49 SSC Courses - \/\/bit.ly\/3Ft9FrY\n\n\ud83d\udc49 UPSC Courses - \/\/bit.ly\/3Diszjr\n\n\ud83d\udc49
2 views • 22 slides
SSC CHSL CPO 2024 (presentation)
\u25ba Check this page for wide range of online courses: http:\/\/bit.ly\/kd-courses\n\nDo you want to get a Government job online course? Here are best govt job preparation courses :\n\n\ud83d\udc49 SSC Courses - \/\/bit.ly\/3Ft9FrY\n\n\ud83d\udc49 UPSC Courses - \/\/bit.ly\/3Diszjr\n\n\ud83d\udc49
1 views • 9 slides
Analysis of Indicators 9 & 10 in Special Education Representation
The indicators 9 and 10 focus on the disproportionate representation of racial and ethnic groups in special education programs. Specifically, Indicator 9 looks at the overall disproportionate representation of groups eligible for special education, while Indicator 10 examines the disproportions with
1 views • 8 slides
Understanding Character Sets in Computer Science
Alphanumeric characters, special symbols, and control characters play crucial roles in representing data through character sets like ASCII and Unicode in computer science. ASCII, with its 7-bit binary codes, represents 128 characters, while Extended ASCII allows for 256 characters. Unicode covers a
1 views • 12 slides
Create a Flood Warning System with Micro:bit and Moisture Sensor
A design brief for constructing a flood warning system using micro:bit to detect rising water levels and alert homeowners, aiming to mitigate damage caused by flooding. The project involves selecting suitable input sensors, such as a moisture sensor, and programming the micro:bit to trigger a warnin
3 views • 9 slides
Evolution of Microprocessors: A Historical Overview
The history of microprocessors traces back to Fairchild Semiconductors in 1959, leading to the founding of Intel in 1968. The evolution from 4-bit to 64-bit microprocessors by Intel revolutionized computing. Key milestones include the Intel 4004 and 4040 (4-bit), 8008, 8080, and 8085 (8-bit), and th
2 views • 44 slides
Understanding the Right to Representation in Consumer Protection
The Right to Representation in consumer rights allows consumers to be heard and ensures their interests are considered in various forums. In India, the Consumer Protection Act of 1986 recognized this right and established Consumer Protection Councils at different levels. These councils play a crucia
0 views • 13 slides
Memory Design Overview: SRAM Cell and Bit Slice Organization
This content provides an overview of SRAM (Static Random Access Memory) cell and bit slice organization, explaining the design elements such as SRAM cell augment, D latch tristated output, multiple enable signals, row and bit selection, data input and output, addressing, and memory expansion with mu
0 views • 25 slides
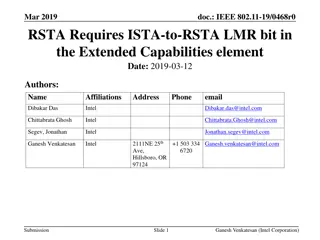
IEEE 802.11-19/0468r0 RSTA Requires ISTA-to-RSTA LMR Bit
This document proposes adding a bit in the Extended Capabilities element to indicate if ISTA needs information from RSTA for 11az negotiation initiation. It suggests RSTA advertise its expectation for ISTA to share the Location Measurement Report. By setting the RSTA requires ISTA-to-RSTA LMR bit, R
2 views • 11 slides
The Life and Personality of Two-Bit Matthews in "The Outsiders
Two-Bit Matthews, a key character in "The Outsiders," is described as the wisecracker of the gang with a humorous and loyal personality. Standing at six feet tall, with gray eyes and a wide grin, he is known for his optimistic nature, love for jokes, and loyalty to his Greaser friends. Despite his s
0 views • 5 slides
Understanding Confusion Matrix and Performance Measurement Metrics
Explore the concept of confusion matrix, a crucial tool in evaluating the performance of classifiers. Learn about True Positive, False Negative, False Positive, and True Negative classifications. Dive into performance evaluation metrics like Accuracy, True Positive Rate, False Positive Rate, False N
3 views • 13 slides
Micro:bit Robot Entry Tutorial - Lesson on Tracking with YahBoom
Explore the world of robotics with this comprehensive tutorial series focused on tracking using YahBoom in micro:bit. Learn about black line tracking, infrared sensor principles, hardware setup, and block programming to enhance your robotics skills. Follow step-by-step instructions to create a fun a
0 views • 12 slides
Micro:bit Robot Entry Tutorial with YahBoom - Buzzer Singing Lesson
In this engaging tutorial series, you will learn how to program a micro:bit robot to sing "Happy Birthday" using a buzzer. Follow step-by-step instructions to set up your micro:bit, connect it to your computer, search for coding blocks, and combine them to create a musical robot. Powered by YahBoom,
2 views • 8 slides
Understanding the Congruence between Elites and Citizens in Representation
The relationship between elites and citizens in representative democracy is explored, tracing historical antecedents, the marriage between representation and democracy, modern representation models, and the roles of representatives. Key themes include responsiveness, responsibility, formalistic, des
0 views • 9 slides
Improved Encryption Technique for Phase Change Memory (PCM)
Bit flips in Phase Change Memory (PCM) can adversely impact performance, power consumption, and system lifespan. To address this, a write-efficient encryption scheme called DEUCE was developed, which reduced bit flips by 50% and improved speed by 27%. By re-encrypting only modified data, the scheme
0 views • 41 slides
Understanding Exchange Rate Behavior with Negative Interest Rates: Early Observations by Andrew K. Rose
In this study, Andrew K. Rose examines the exchange rate behavior in economies with negative nominal interest rates, focusing on the impact and implications of such rates on exchange rates. The findings suggest limited observable consequences on exchange rate behavior, with similarities in shocks dr
0 views • 42 slides
Enhancements in Gender Identity Representation in Healthcare
This content discusses the updates and additions to DICOM attributes and CID code lists related to patient gender identity representation. It addresses the use of sex and gender identity data in healthcare settings, focusing on cases like transgender patients undergoing hormone transition. The HL7 G
0 views • 12 slides
Understanding Pro Se Assistance and Pro Bono Representation
This material delves into the considerations, course outlines, justifications, and constitutional basis for assisting pro se litigants and encouraging pro bono representation. It covers the need for self-representation, limitations to the right, the increase in pro se litigants, and the constitution
0 views • 51 slides
Guide to Giving Negative Commands in Spanish
Learn how to effectively communicate what not to do in Spanish with negative commands. Understand the different forms of negative commands for -AR, -ER/-IR verbs, irregular verbs, direct object pronouns, stem-changing verbs, and verb forms ending in -CAR, -GAR, -ZAR. Master the rules and exceptions
0 views • 12 slides
Understanding Negative -T Commands in Spanish
Negative -T commands in Spanish are used to tell someone what not to do. These commands are often directed at friends or familiar individuals. Forming negative -T commands involves starting with the YO form in the present tense, dropping the O for -ER/-IR verbs, adding -ES for -AR verbs, and includi
0 views • 50 slides
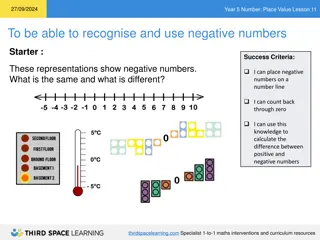
Exploring Negative Numbers in Year 5 Mathematics Lesson
In this Year 5 mathematics lesson on negative numbers, students learn to recognize and use negative numbers through various activities such as placing them on a number line, counting back through zero, and calculating the differences between positive and negative numbers. The lesson also prompts stu
0 views • 23 slides
Exploring the Possibility of People with Negative Height
This article delves into the theoretical concept of people with negative height, discussing the probabilities based on normal distribution models and empirical rules. It explores the likelihood of encountering individuals with negative height in today's population, throughout history, and the number
0 views • 10 slides
Understanding Bit Masking and Bitwise Operations for Efficient Bit Manipulation
Bit masking is a powerful technique in programming to selectively access or modify specific bits without affecting others. By creating a byte with bits set at desired positions using a bit mask, bitwise operators like OR (|) and AND (&) can be leveraged to efficiently set or clear specific bits. Thi
0 views • 11 slides
Understanding Negative Bit Representation in Computer Science
Dive into the world of negative bit representation in computer science, exploring the need for representing negativity in integers, methods like Two's Complement, disadvantages of Sign-Value and One's Complement, range of Two's Complement values, overflow, underflow, and more. Discover the significa
0 views • 26 slides
Non-Negative Tensor Factorization with RESCAL
This article discusses non-negative tensor factorization with RESCAL, covering topics such as Non-Negative Matrix Factorization, Multiplicative Updates, RESCAL for Relational Learning, and Non-Negative Constraint for RESCAL. It explores how factorizing matrices/tensors into non-negative factors can
0 views • 11 slides
Understanding Non-Optimal Routing and 32-Bit ASN Compatibility
Explore the challenges caused by the incompatibility of 32-bit ASN with old router software, leading to non-optimal routing issues. Learn about Autonomous Systems, AS Numbers, BGP asymmetric routing, and the importance of routing software supporting 32-bit ASN. Discover how outdated software replace
0 views • 8 slides
Micro:bit Robot Entry Tutorial - Advanced Lesson on Breathing Lamp with YahBoom (80 characters)
In this tutorial, learn how to create an advanced breathing lamp effect using a micro:bit robot with YahBoom. Follow the steps to program the colorful lights on the dot matrix, change colors of the seven-color lamp, and connect the micro:bit to a computer for programming. This comprehensive guide in
0 views • 13 slides
Understanding MIPS Arithmetic Logic Unit (ALU)
The MIPS ALU is the heart of computer calculations, performing functions like add, and, or, and sub. This article delves into designing a full ALU, starting from a 1-bit full adder to a 32-bit ALU. It explores how operations like and, or, and addition are carried out within the ALU, and how to imple
0 views • 28 slides
Emerging Variable Precision Formats in Compiler Flow
Many applications rely on floating point numbers, but deciding on the right precision is crucial to avoid performance and energy waste. This work explores the impact of precision choices, including overkill and insufficient precision, on applications such as CNNs and GPU algorithms. It introduces a
0 views • 25 slides
Impact of Negative Nominal Interest Rates on Bank Performance
Negative nominal interest rates, implemented following the financial crisis, have had a limited effect on bank performance globally. While low rates reduce profitability, banks have shown resilience through adjustments in funding allocations and non-interest income sources. Studies suggest that resp
0 views • 34 slides
School Food Service Update and Financial Overview
Within the School Food Service update, information is provided on negative account balances, personal parent notifications, and payment options available to parents. The data includes details on total negative balances, number of families contacted, and payment methods. Challenges with negative bala
0 views • 5 slides
Electoral Systems and Minority Representation
Various electoral systems, including district and at-large voting, impact how minorities are represented in government. District systems can provide more proportional representation for minorities if they are geographically concentrated, while at-large systems often result in minority under-represen
0 views • 14 slides
Micro:bit Robot Ultrasonic Obstacle Avoidance Tutorial
Learn how to set up and program a micro:bit robot for ultrasonic obstacle avoidance. Follow the step-by-step guide to prepare hardware, connect the micro:bit to the computer, search for programming blocks, and test the ultrasonic sensor. Children can understand the concepts and experiment with obsta
0 views • 10 slides
Understanding Electoral Formulas and Proportional Representation
Electoral formulas play a crucial role in translating individual votes into legislative seats, with systems like Proportional Representation and Winner-Takes-All affecting government structure and representation. Proportional systems aim for fair seat allocation based on vote share, while non-propor
0 views • 13 slides
Universal Design for Learning (UDL) and Multiple Means of Representation
Explore the concepts of Universal Design for Learning (UDL) and Multiple Means of Representation in education. Learn about the importance of representation in learning, how to apply multiple means of representation, and practical strategies to enhance learning inclusivity. Engage in discussions and
0 views • 34 slides
Bellman-Ford Algorithm: Shortest Path with Negative Edge Length
The Bellman-Ford algorithm addresses the challenge of finding the shortest path in graphs with negative edge lengths, particularly useful in scenarios such as arbitrage in currency exchange rates. By utilizing dynamic programming and steps iteration, the algorithm efficiently detects negative cycles
2 views • 16 slides
Illustrated Design of a Simplified CPU with 16-bit RAM
Demonstrates the design of a basic CPU with 11 instructions and 4096 16-bit RAM, showcasing the assembly of a general-purpose computer using gates and registers. The CPU comprises 8 key registers for various functions, employing a sequential circuit for instruction execution. The machine language pr
0 views • 31 slides