Good Laboratory Practices Study Protocols for Effective Research Management
Supplemental materials providing detailed protocols for implementing Good Laboratory Practices (GLP) in research settings. The protocols cover GLP requirements, experimental design, reading regulatory sections, approval processes, amendments, circulation lists, and study plans. These materials aim t
0 views • 22 slides
Update on SWAG Protocols and New NICE TA Progress Report
Kate Gregory leads the SWAG Protocols update for March 2024, with advancements in new protocols and NICE TA updates. A comparison of activities from Oct 2023 to Mar 2024 shows progress in issuing, reviewing, and drafting protocols. The latest NICE TA additions include treatments for advanced cancers
5 views • 13 slides
Understanding Consistency Protocols in Distributed Systems
Today's lecture covers consistency protocols in distributed systems, focusing on primary-based protocols and replicated-write protocols. These protocols play a crucial role in ensuring consistency across multiple replicas. One example discussed is the Remote-Write Protocol, which enforces strict con
0 views • 35 slides
Oklahoma School Safety Protocols Overview
Overview of the school safety protocols in Oklahoma, which define requirements based on COVID-19 alert levels per capita in each county. The protocols include instructions for different alert levels, mask recommendations, visitor limitations, and activity guidelines. Schools are expected to offer in
0 views • 9 slides
Work Protocols and Safety Measures for Employees Returning to Work
In the wake of the COVID-19 pandemic, these work protocols emphasize roles, responsibilities, and mental wellbeing of employees. Pre-work precautions at home, personal measures, testing procedures, increasing awareness, and safe travel guidelines are highlighted to ensure a secure work environment.
0 views • 16 slides
MAAP Protocol Overview in IEEE 1722: Address Acquisition and Message Format
The MAAP (Multicast Address Acquisition Protocol) is defined in IEEE 1722 for time-sensitive applications in bridged local area networks. It involves acquiring multicast addresses through claiming, probing, and defending messages. MAAP enables dynamic allocation of addresses and defending against co
1 views • 8 slides
Understanding Emergency Conditions in ERCOT Protocols
ERCOT has defined various levels and communication protocols for Emergency Conditions within the electrical grid system. This includes Emergency Notices, Energy Emergency Alerts, operating plans, outage coordination, and requirements related to voltage support for ensuring system safety and reliabil
6 views • 18 slides
Distributed Computation in Node-Capacitated Networks
Exploration of communication primitives and algorithms in node-capacitated networks, including Node-Capacitated Clique Model, communication on butterfly networks, orientation using Boruvka's algorithm, computing O(a)-orientation, and solving graph problems like BFS trees, maximal independent set, ma
0 views • 7 slides
Understanding Lock-Based Protocols in Database Concurrency Control
Lock-based protocols are essential mechanisms for controlling concurrent access to data items in a database system. This involves granting locks in exclusive (X) or shared (S) modes to ensure data integrity and prevent conflicts. Lock compatibility matrices and locking protocols play a crucial role
2 views • 69 slides
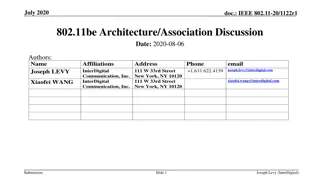
IEEE 802.11be MLD Architecture Discussion
The document discusses the architecture of MLD (Multicast and Local Delivery) within the IEEE 802.11be framework. It highlights how MLD will align with existing 802.11 basic architecture, emphasizing the management of access to PHY and media for both AP and non-AP devices. The goal is to integrate M
0 views • 9 slides
Laboratory Safety Protocols and Pathogen Classification
Scientist must adhere to lab safety protocols including wearing safety gear, proper waste disposal, and handling chemicals carefully. The classification of pathogens varies by country based on WHO guidelines into four risk groups. Understanding these protocols and classifications is crucial for a sa
0 views • 17 slides
SRYA Clinic Soccer Fall 2021 Updates and Protocols
Stay updated on the latest news and protocols for the SRYA Clinic Soccer Fall 2021 season. Learn about volunteer positions, contacts, fun facts about the program, COVID-19 updates, and general protocols from Rec & Parks. Ensure the safety and well-being of players, coaches, and families while enjoyi
0 views • 23 slides
State Transportation Department's Stormwater Monitoring Program Overview
This document presents findings and protocols from the National Cooperative Highway Research Program related to stormwater monitoring goals, objectives, and protocols for state departments of transportation. The project team, objectives, and report organization are outlined, aiming to provide guidan
0 views • 32 slides
Secure Composition of Key Exchange Protocols
Explore the game-based composition approach for key exchange protocols, focusing on ensuring security in compositions with arbitrary tasks and the universal composability of protocols. Delve into the Bellare-Rogaway security model and the details of security games in protocol analysis. Understand ke
0 views • 25 slides
Taming Adaptivity in YOSO Protocols: The Modular Way
Explore the concept of taming adaptivity in YOSO protocols through a modular approach. The research delves into the efficiency, adversary adaptivity, role assignments, and compiler models in synchronous YOSO protocols. The visual presentations illustrate the framework, challenges, and strategies in
0 views • 19 slides
Understanding Delegates in Unreal Engine
Delve into the world of delegates in Unreal Engine, from basic to dynamic and multicast types. Discover how delegates enable flexible function assignment and callback mechanisms within classes. Explore examples like player events and asset processing to grasp the power and versatility of delegates i
1 views • 18 slides
Framework for One-sided RDMA Multicast in Data Center Group Communications
This paper explores the implementation of one-sided RDMA multicast in data center group communications, highlighting the benefits of offloading network I/O from CPUs and unique connection parameters for efficient multicast operations. The research addresses the challenges of enabling one-sided RDMA
0 views • 11 slides
Understanding Project Calico: Networking Essentials and Future Trends
Explore the pivotal role of Project Calico in networking, focusing on its core concepts, including IP connectivity, multicast, and broadcast, along with a deep dive into the data path mechanisms. Discover the future prospects and use cases that highlight its provisioning and isolation capabilities w
0 views • 16 slides
Overview of Identification Protocols in CS255 by Dan Boneh
The lecture in CS255 covers various topics related to identification protocols, including signatures from trapdoor functions, certificates, revocation methods, certificate issuance problems, defense mechanisms like certificate transparency (CT), and moving on to protocols. The talk also explores the
0 views • 43 slides
Towards Practical Generic Zero-Knowledge Protocols
Exploring the evolution of zero-knowledge protocols, this presentation by Claudio Orlandi from Aarhus University delves into the concepts of Zero-Knowledge from Garbled Circuits, Privacy-Free Garbled Circuits, and more. The talk discusses efficient methods for proving statements and touches on relat
0 views • 29 slides
Basics of Networking Communication and Internet Structure
The content covers the basics of networking communication, including synchronous and asynchronous communication, broadcast, multicast, and point-to-point communication. It also discusses internet properties, client/server structure, and interactions in client/server relationships. The visuals provid
0 views • 39 slides
Wireless Sensor Networks: Medium Access Protocols Overview
This collection of images presents key concepts in wireless sensor networks, focusing on medium access protocols, the ISO/OSI reference model, types of conflict resolution, contention-free protocols, Bitmap protocol, ALOHA algorithm, and its analysis and efficiency. Various protocols and algorithms
0 views • 83 slides
Green Protocols for Greener Arbitrations
The Green Protocols introduced by AtLAS aim to guide the arbitration community in committing to environmentally sustainable practices. These protocols suggest ways to reduce carbon emissions, energy consumption, waste generation, and unnecessary travel by utilizing electronic communication, video co
0 views • 14 slides
Understanding Ethernet and Multiple Access Protocols in Computer Networks
Exploring the fundamentals of Ethernet and multiple access protocols in computer networks, this content discusses the two primary categories of multiple access protocols - contention access and controlled access. It delves into topics such as CSMA/CD, LANs, performance of multiple access schemes, ad
0 views • 7 slides
Understanding Computer Networking: Broadcast and Multicast Protocols
In this lecture on computer networking, we explore the concepts of broadcast and multicast protocols. The discussion covers topics such as BGP routing, IPv4 anycast hack, IP multicast, and the role of broadcast in small-to-moderate sized ad hoc networks. Learn about the differences between unicast,
0 views • 20 slides
Implementation and Validation of Multimedia Broadcast Multicast Service for LTE/LTE-Advanced
This study discusses the implementation and validation of a multimedia broadcast multicast service for LTE/LTE-Advanced using the OpenAirInterface platform. It explores the motivation behind enhancing multimedia capabilities in high-capacity mobile networks and the challenges related to previous res
0 views • 28 slides
Mechanized Model for CAN Protocols - FASE 2013
This research paper presents a mechanized model for Content Addressable Network (CAN) protocols, focusing on supporting RDF data storage in the Semantic Web. It discusses the general motivation, CAN principles, RDF queries, and challenges in handling queries over variables in large-scale settings. T
0 views • 26 slides
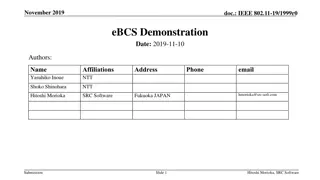
Implementation and Demonstration of eBCS Concept in IEEE 802.11-19/1999r0
This presentation showcases the implementation and demonstration of the eBCS concept, including the system architecture, utilization of eBCS AP and STA, web server functionality, and data transmission processes. It covers the use of LDPC-Staircase/Triangle for packet transmission, IP multicast for d
0 views • 9 slides
Broad Architectural Principles in System Design
The role of broad architectural principles in system design is crucial for creating large-scale systems. Researchers must define goals and assumptions while considering performance, elegance, and iterative design processes. Understanding critical-path driven processes helps optimize system efficienc
0 views • 50 slides
Local MAC Address Assignment Protocol (LAAP) and 802.1CQ
The Local MAC Address Assignment Protocol (LAAP) in conjunction with 802.1CQ specifies protocols and procedures for locally unique assignment of MAC addresses in IEEE 802 networks. LAAP operates in two modes - Server Mode and Peer-to-Peer Mode, ensuring efficient allocation of MAC addresses while av
0 views • 15 slides
Understanding Virtual Synchrony and Commit Protocols in Distributed Systems
Explore the concepts of virtual synchrony, commit protocols, and reliable multicasting in distributed systems. Learn about one-to-one communication, process groups, and virtually synchronous multicast, along with implementations in LAN environments. Discover how processes can handle failures and ens
0 views • 23 slides
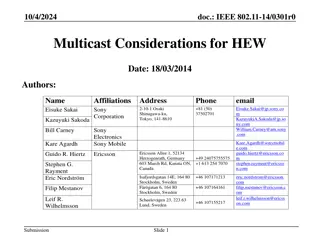
Multicast Considerations for High Efficiency Wireless (HEW) Networks
Discusses the unique characteristics and challenges of distributing the same content to a large number of devices in dense deployment scenarios, focusing on multicast communication. Emphasizes the need for efficient solutions in HEW to enhance multicast communication for scenarios such as video dist
0 views • 14 slides
Scalable Identity and Key Management for Publish-Subscribe Protocols
This research by Prashant Anantharaman from Dartmouth College focuses on scalable identity and key management for publish-subscribe protocols in Energy Delivery Systems. It discusses the architecture, goals, assumptions, and implementation results in the context of PKI vs. Macaroons protocols. The w
0 views • 37 slides
Interconnection Networks in Multiprocessing Systems Overview
Explore the intricacies of interconnection networks for multiprocessing systems in Embedded Computer Architecture, covering connecting processors, topologies, routing, deadlock, switching, and performance metrics like bandwidth and latency. Delve into various network types, such as on-chip networks
0 views • 33 slides
Comprehensive Examination Questions on Data Management Systems and Security Protocols
This content covers a range of topics related to data management systems, including two-phase locking and two-phase commit protocols, Bayou system with vector clocks and causality, digital signatures and certificates in protocols, and authentication protocols. Questions include scenarios and concept
0 views • 6 slides
Efficient Gossip and Bimodal Multicast Protocols in Distributed Systems
Gossip protocols are vital in spreading information efficiently in large systems, with log(N) time complexity for dissemination. Bimodal multicast uses IP multicast for message transmission, lacking reliability and flow control. The cost of IP multicast is low, but ensuring reliability can be achiev
0 views • 49 slides
IEEE 802.21 Joint Plenary Opening Report
The presentation discusses the objectives, work status, and task group activities of IEEE 802.21 related to handover services and interoperability between heterogeneous networks, focusing on multicast group management and revision projects. The report outlines the session schedule and future plans f
0 views • 7 slides
Improved Merlin-Arthur Protocols for Fine-Grained Complexity Problems
The text discusses Merlin-Arthur proof systems and protocols for central problems in fine-grained complexity, particularly focusing on the time complexity, completeness, and soundness of these protocols. It also touches on recent interest in these protocols and presents new results in areas such as
0 views • 16 slides
Quantum Distributed Proofs for Replicated Data
This research explores Quantum Distributed Computing protocols for tasks like leader election, Byzantine agreement, and more. It introduces Quantum dMA protocols for verifying equality of replicated data on a network without shared randomness. The study discusses the need for efficient protocols wit
0 views • 28 slides
Terrestrial File Transfer Concept: Design Goals and Protocols
This document discusses the concept of terrestrial file transfer as presented in a series of slides from an ESA event in Noordwijkerhout, The Netherlands. It covers the purpose, design goals, protocols, and transport protocols involved in exchanging files between agencies for mission design, operati
0 views • 20 slides