NCI Data Collections BARPA & BARRA2 Overview
NCI Data Collections BARPA & BARRA2 serve as critical enablers of big data science and analytics in Australia, offering a vast research collection of climate, weather, earth systems, environmental, satellite, and geophysics data. These collections include around 8PB of regional climate simulations a
6 views • 22 slides
2022 Thales Access Management Index
Thales Access Management Index highlights the current landscape of access security, revealing insights on multi-factor authentication adoption, remote and privileged user access management, VPN usage trends, challenges faced, and preferences towards third-party access management. The report emphasiz
2 views • 9 slides
Revolutionizing with NLP Based Data Pipeline Tool
The integration of NLP into data pipelines represents a paradigm shift in data engineering, offering companies a powerful tool to reinvent their data workflows and unlock the full potential of their data. By automating data processing tasks, handling diverse data sources, and fostering a data-driven
9 views • 2 slides
Revolutionizing with NLP Based Data Pipeline Tool
The integration of NLP into data pipelines represents a paradigm shift in data engineering, offering companies a powerful tool to reinvent their data workflows and unlock the full potential of their data. By automating data processing tasks, handling diverse data sources, and fostering a data-driven
7 views • 2 slides
Understanding Cloud-Optimized HDF5 Files for Efficient Data Access
Explore the benefits and features of Cloud-Optimized HDF5 files, such as minimal reformatting, fast content scanning, and efficient data access for both cloud-native and conventional applications. Learn about chunk sizes, variable-length datatypes, internal file metadata, and best practices for opti
3 views • 25 slides
Ask On Data for Efficient Data Wrangling in Data Engineering
In today's data-driven world, organizations rely on robust data engineering pipelines to collect, process, and analyze vast amounts of data efficiently. At the heart of these pipelines lies data wrangling, a critical process that involves cleaning, transforming, and preparing raw data for analysis.
2 views • 2 slides
Data Wrangling like Ask On Data Provides Accurate and Reliable Business Intelligence
In current data world, businesses thrive on their ability to harness and interpret vast amounts of data. This data, however, often comes in raw, unstructured forms, riddled with inconsistencies and errors. To transform this chaotic data into meaningful insights, organizations need robust data wrangl
0 views • 2 slides
The Role of Data Migration Tool in Big Data with Ask On Data
Data migration tools are indispensable for organizations looking to transform their big data into actionable insights. Ask On Data exemplifies how these tools can streamline the migration process, ensuring data integrity, scalability, and security. By leveraging Ask On Data, organizations can achiev
0 views • 2 slides
Know Streamlining Data Migration with Ask On Data
In today's data-driven world, the ability to seamlessly migrate and manage data is essential for businesses striving to stay competitive and agile. Data migration, the process of transferring data from one system to another, can often be a daunting task fraught with challenges such as data loss, com
1 views • 2 slides
Ask On Data Empowering Organization’s Success through Data Migration Tool like Ask On Data
In today's data-driven world, successful organizations recognize the paramount importance of efficient data management. Among the myriad challenges they face, data migration stands out as a critical process, often determining the success or failure of digital transformation initiatives. As organizat
1 views • 2 slides
Personnel Safety Systems and Access Control at CERN Facilities
Personnel Safety Systems at CERN include ODH detection, fire safety measures, and access control to protect personnel from hazards. Various access control layers are implemented to regulate entry to different parts of the facility, ensuring only trained personnel access underground areas. Biometric
0 views • 19 slides
Introduction to Database Management System Explained
This presentation covers the basics of database management systems, including definitions of data, types of data, structured and unstructured data, storing data in computers using file systems and database systems, and issues with file systems like data redundancy, inconsistency, difficult data acce
1 views • 18 slides
Streamlining Data Access and Reporting with JCPS DataDash System
JCPS DataDash is a comprehensive tool that provides fast and efficient access to vital student data, allowing educators to monitor performance, track trends, and focus on areas for improvement. By leveraging the system, users can easily request and access detailed reports on student vital signs, dem
0 views • 8 slides
Port of Stockton Restricted Area Access Control and ID Card Policy
Access to restricted areas at the Port of Stockton facilities requires possession of a TWIC (Transportation Worker Identification Credential). Only authorized personnel, such as employees, contractors, and those with regular access, may receive a Port Access Card after approval by the Facility Secur
0 views • 6 slides
Introduction to Database Security and Countermeasures
Database security is essential to protect data integrity, availability, and confidentiality. Countermeasures such as access control, inference control, flow control, and encryption can safeguard databases against threats. Access control restricts user access, inference control manages statistical da
0 views • 26 slides
Understanding Data Governance and Data Analytics in Information Management
Data Governance and Data Analytics play crucial roles in transforming data into knowledge and insights for generating positive impacts on various operational systems. They help bring together disparate datasets to glean valuable insights and wisdom to drive informed decision-making. Managing data ma
0 views • 8 slides
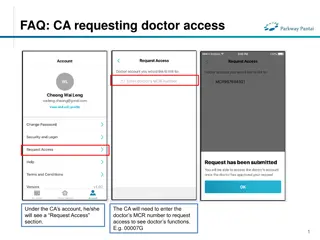
FAQs for Doctor and Clinical Assistant (CA) Account Access Management
Learn how CAs can request access to doctors' functions by entering the MCR number, how doctors can grant or remove CA access, and how CAs can manage access to multiple doctors. The process includes requesting, approving, and unlinking accounts, ensuring efficient and secure access management in a cl
0 views • 4 slides
Importance of Data Preparation in Data Mining
Data preparation, also known as data pre-processing, is a crucial step in the data mining process. It involves transforming raw data into a clean, structured format that is optimal for analysis. Proper data preparation ensures that the data is accurate, complete, and free of errors, allowing mining
1 views • 37 slides
Understanding Data Collection and Analysis for Businesses
Explore the impact and role of data utilization in organizations through the investigation of data collection methods, data quality, decision-making processes, reliability of collection methods, factors affecting data quality, and privacy considerations. Two scenarios are presented: data collection
1 views • 24 slides
Understanding Data Link Layer in Computer Networking
The Data Link Layer (DLL) is the second layer of the OSI model, responsible for error detection and correction, framing, addressing, synchronization, flow control, and multi-access protocols. It deals with logical link control and media access control, addressing destination hardware, avoiding data
0 views • 49 slides
Qualtrics Data Security and Access Protocol
Qualtrics ensures secure data management and access control for surveys created under the University of Windsor account. Data resides on servers in Canada with backups in Canada and Ireland. Access to individual surveys is restricted, and data can be anonymized. Respondent restrictions and study wit
0 views • 7 slides
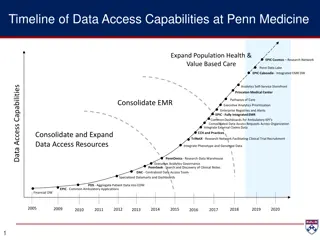
Evolution of Data Access Capabilities at Penn Medicine
Penn Medicine has expanded its data access capabilities over the years through various initiatives like EPIC Cosmos Research Network, Penn Data Lake, DAC, and more. The Data Analytics/Access Center (DAC) plays a crucial role in managing enterprise resources, data architecture, development, reporting
0 views • 23 slides
Enhancing Data Management in INDEPTH Network with iSHARE2 & CiB
INDEPTH Network emphasizes the importance of iSHARE2 & CiB to enhance data sharing and management among member centers. iSHARE2 aims to streamline data provision in a standardized manner, while CiB provides a comprehensive data management solution. The objectives of iSHARE2 include facilitating data
0 views • 17 slides
Achieving Secure and Scalable Data Access Control in Cloud Computing
Cloud computing enables remote data storage and application utilization without local hardware and software management. This paper addresses challenges related to data security and access control in cloud environments, emphasizing the need for fine-grained data access control. It discusses the compl
0 views • 32 slides
Accessing NC Fast Subsidized Child Care Data in Data Warehouse
Learn how to log in and access NC Fast Subsidized Child Care data through the Data Warehouse portal. Access to the data warehouse requires a login and password, which can be obtained by contacting your LME or Institution Security Officer. The metadata available includes descriptions, table names, pr
0 views • 15 slides
Comparison between Array and Linked List Data Structures
Linked lists and arrays are commonly used data structures in programming. Linked lists offer flexibility in size changes and efficient rearrangement of elements, while arrays provide direct access to elements based on their index. Linked lists involve pointers connecting elements, allowing for dynam
0 views • 24 slides
Open Access at Charles University: Opportunities and Challenges
Charles University is navigating the landscape of open access following the implementation of the Czech National Open Access Strategy. The university is working towards making all research articles and proceeding papers open access, monitoring article processing charges, and promoting open access as
0 views • 24 slides
Understanding Ethernet and Multiple Access Protocols in Computer Networks
Exploring the fundamentals of Ethernet and multiple access protocols in computer networks, this content discusses the two primary categories of multiple access protocols - contention access and controlled access. It delves into topics such as CSMA/CD, LANs, performance of multiple access schemes, ad
0 views • 7 slides
EU Data Access Rights: Maximizing Innovation and Fairness in Data Economy
The 2nd GRUR Expert Round Table discussed the importance of introducing new data access rights in the EU, aiming to create a Single Market for data while ensuring fairness and clarity in data usage. The Inception Impact Assessment highlighted the need for increased data access to benefit various act
0 views • 13 slides
Proposed MAP Channel Access Procedures in IEEE 802.11-24/72r0
In the May 2024 document IEEE 802.11-24/72r0, a uniform MAP coordination framework is discussed, involving procedures like M-AP discovery, coordinated transmissions, and channel access mechanisms. All APs in a coordination group can compete for channel access and share transmission opportunities. Th
0 views • 10 slides
Harvard Chan School 2021 Yearly Access Review Process
The Harvard Chan School conducts its annual Yearly Access Review (YAR) process to review user access to various financial systems. The process involves assessing permissions, levels of access, and organizational details for each team member. Instructions are provided on reviewing worksheets, adding
0 views • 19 slides
Understanding Security Access in PeopleSoft Finance
Explore the various levels of security access in PeopleSoft Finance, from basic entry access to transaction entry, approvals, and procurement processes. Learn how to request individual and department security access and find relevant forms on the financial services website. Discover the different ty
0 views • 11 slides
Proxy Access to Medications Implementation Stages
This document outlines the implementation stages for proxy access to medications. It covers agreements with healthcare providers, prerequisites including compliance and data sharing agreements, and systems configuration for access to medical records. The stages include setting up access for care pro
0 views • 7 slides
Overview of PaNOSC Workshop API Endpoints & Data Structures
This project discusses the API endpoints and data structures from the PaNOSC Workshop, focusing on reviewing use cases, required search results/data, actors involved, and the design of endpoints reflecting proposal/experiment processes. It covers detailed discussions on data models, instrument setup
0 views • 19 slides
Modernizing Data Ecosystem at Census Bureau
The Census Bureau is undergoing a transformation by integrating data-centric approaches, modernizing data collection processes, and leveraging third-party data to enhance the quality of statistical products. The focus now includes merging data science with traditional methods and diversifying data p
0 views • 7 slides
Understanding Data Protection Regulations and Definitions
Learn about the roles of Data Protection Officers (DPOs), the Data Protection Act (DPA) of 2004, key elements of the act, definitions of personal data, examples of personal data categories, and sensitive personal data classifications. Explore how the DPO enforces privacy rights and safeguards person
0 views • 33 slides
Understanding Data Awareness and Legal Considerations
This module delves into various types of data, the sensitivity of different data types, data access, legal aspects, and data classification. Explore aggregate data, microdata, methods of data collection, identifiable, pseudonymised, and anonymised data. Learn to differentiate between individual heal
0 views • 13 slides
Database Access Control & Privacy: A Common Ground Explored
Exploring the intersection of database access control and data privacy, this paper delves into the implications of data privacy concerns on Database Management Systems (DBMS). It discusses the need for more than just access control mechanisms and highlights the evolving landscape of data publishing,
0 views • 29 slides
Challenges and Importance of Government Access to Personal Data in Cross-Border Intelligence Oversight
Reflecting on the significance of the OECD Declaration on Government Access to Personal Data held by Private Sector Entities, this content delves into the drivers necessitating an OECD-type process, such as law enforcement needs, globalization of criminal evidence, and convergence of civilian commun
0 views • 8 slides
Benefits Data Trust - Improving Access to Essential Benefits
Benefits Data Trust (BDT) is a national nonprofit using data, technology, and policy to provide efficient access to assistance, enhancing health and financial security. Their vision includes connecting people to essential benefits with dignity and respect, aiming for lower healthcare costs and thriv
0 views • 15 slides