Data Cleaning
Data cleaning is the process of fixing or removing incorrect, duplicate, or incomplete data within a dataset. It improves data quality, ensuring accurate and reliable information for decision-making. Learn why data cleaning is necessary and the essential reasons to clean your data.
4 views • 35 slides
How to Consolidate EasyChair Accounts
Learn how to merge two EasyChair accounts and consolidate them into one for the AMS Annual & WMC Conferences. Follow the steps outlined to ensure a smooth transition and avoid having duplicate accounts. Images included for visual guidance.
0 views • 8 slides
Employer Ambassador presentation slide deck
Elevate your presentation game with our Employer Ambassador slide deck. Crafted to impress, persuade, and inform, this dynamic resource is your key to delivering impactful presentations that resonate with your audience. From compelling visuals to strategic content, this deck is designed to help you
5 views • 19 slides
Understanding Hash Maps: A Common Data Structure
In this module, learn about Hash Maps, a common data structure used in various programming languages like Java, C#, C++, Python, and PHP. Hash Maps allow you to store key-value pairs without duplicate keys, making it efficient for mapping relationships between data elements. Explore how to declare,
6 views • 16 slides
Lubbock Retail Integration Task Force – LRITF
The Lubbock Retail Integration Task Force (LRITF) discussed various topics including customer choice enrollment, Winter Storm Uri securitization, distribution loss factors, and updates on duplicate addresses and various other updates. The completed action items Q&A provided insight into transitionin
0 views • 11 slides
Understanding Java ArrayList in Amity School of Engineering & Technology
Java ArrayList in Amity School of Engineering & Technology is a dynamic array used for storing elements without a size limit. It offers flexibility by allowing element addition and removal at any time. This type of array is part of the java.util package, similar to the Vector in C++. The ArrayList c
0 views • 18 slides
Efficient Record-Keeping System for Needle Stick Injuries
Streamline your needle stick and sharp object injury reporting process with EPINET for Microsoft Access. Learn how to enter new incident records, avoid duplicate IDs, input dates accurately, and utilize handy tips for efficient data entry. Ensure completeness of information to enhance infection prev
0 views • 35 slides
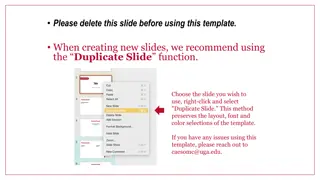
Efficient Slide Presentation Tips & Resource Utilization
Utilize the Duplicate Slide function when starting a new presentation instead of editing existing templates directly. Refer to the proper process for seamless layout and design preservation. For any inquiries, contact caesomc@uga.edu.
0 views • 13 slides
Customize Your PAC Handbook for an Effective Parent Advisory Council
Customize this template PAC Handbook for your school by saving a duplicate copy, renaming it, and tailoring it to your PAC's needs. The handbook includes guidance on where to find existing PAC information and specific details on school operations. Explore various sections to streamline your role wit
0 views • 18 slides
Understanding Dictionaries in Python
Dictionaries in Python allow you to store elements with keys of any type and values of any type. They can contain any and different types of elements, have unique keys but can have duplicate values, cannot be concatenated or repeated, can be nested, and are mutable like lists. Dictionaries can be it
0 views • 13 slides
Understanding Slowly Changing Dimension Type 2 (SCD2) by Dr. Girija Narasimhan
Dive into the concept of Slowly Changing Dimension Type 2 (SCD2) explained by Dr. Girija Narasimhan. Discover how this type helps maintain historical data in a target system by creating duplicate records with necessary changes, without disrupting the existing history. Learn how to create tables, ins
0 views • 17 slides
Implementing Provisions of Agriculture Improvement Act of 2018: National Accuracy Clearinghouse Efforts
Efforts are underway to implement sections of the 2018 Agriculture Improvement Act related to the National Accuracy Clearinghouse (NAC) to prevent duplicate issuance of SNAP benefits across states. The NAC rule requires states to report recipient information, screen applicants against the NAC, and t
0 views • 8 slides
Sample Slide Format for COI Disclosure at Academic Meetings
This presentation provides a sample slide format for disclosing conflicts of interest (COI) at academic meetings. It includes guidelines for using Form 1-A when no conflicts exist and for using Form 1-A when conflicts need to be disclosed. The format also covers details about financial interests and
0 views • 5 slides
Efficient Residency Verification Program Implementation in California
California's residency verification program entails information exchange among states to prevent duplicate public assistance, benefiting from shared data outside of PARIS. Details include selecting input records, sending files, receiving output files, and working on match results, with a focus on Ca
0 views • 8 slides
Understanding Record Linkage Concepts
Explore the fundamentals of record linkage, also known as matching or merging, which involves combining data from different sources for the same individual. Learn about the importance of efficient and accurate duplicate detection, deterministic matching, and the challenges of variations in data betw
3 views • 20 slides
Encrypted Deduplication for Secure Cloud Storage
Encrypted deduplication enhances data storage efficiency by eliminating duplicate chunks and encrypting outsourced data to protect against cloud service providers. This approach uses message-locked encryption and metadata management to store unique data and key mappings securely. By leveraging encry
0 views • 24 slides
Distance-Based Suspicion Score for Audit Selection
Nuriddin Tojiboyev presented a method for audit selection based on distance measures, risk filtering, and exception sorting. The approach involves selecting representative samples from a population of records, using risk-based filtering to prioritize records for review. Various filters and exception
0 views • 19 slides
Explore Pretzel Time: A Movie Forum for Real Opinions
Pretzel Time is a unique movie forum platform where everyday individuals can share their honest opinions without the influence of critics or professional reviews. Users can freely post comments or discussions, with limits on duplicate movie posts and user comments. The platform offers a refreshing t
0 views • 4 slides
ESTRO 2024 PowerPoint Template
Access the ESTRO 2024 PowerPoint template designed for professional use. Customize your presentation by choosing between slide 2 or slide 3 and remove the instruction slide. Additionally, you can include your name, institute, and presentation title for a personalized touch. Please be mindful of the
0 views • 5 slides
Understanding Epistasis: Genetic Interactions and Their Implications
Epistasis is a phenomenon where the phenotypic expression of one gene is influenced by interactions with another gene. This concept, first introduced in 1909, plays a crucial role in genetics, affecting various traits and evolutionary processes. The difference between dominance and epistasis lies in
0 views • 41 slides
Monthly Slide Presentation Summary
In this monthly slide presentation, each slide represents a different month of the year from January to July. Each slide includes a calendar layout with days of the week and dates, accompanied by a visual representation. The slides provide a quick overview of each month, making it easy to track impo
0 views • 13 slides
Understanding Similarity and Distance in Data Mining
Exploring the concepts of similarity and distance in data mining is crucial for tasks like finding similar items, grouping customers, and detecting near-duplicate documents. Metrics like Jaccard similarity help quantify similarities between sets of data objects, enabling effective analysis and decis
0 views • 46 slides
Audit of Pre-Transfusion Sampling Process in Healthcare
An audit was conducted on the pre-transfusion sampling process within a healthcare board, revealing issues such as unnecessary duplicate samples, misidentification of patients, and delays in obtaining confirmatory samples. The audit highlighted the importance of secure electronic patient identificat
0 views • 12 slides
Importing and Loading ASSIST Data into Banner - CISOA/3CBG Conference 2014
Overview of the process involved in importing XML transcripts and loading ASSIST data into Banner for the CISOA/3CBG Conference 2014. The presentation covers two technologies used, Banner setup, XML XSL translation, data source details from eTranscriptCA (California Transcript Exchange), loading ASS
0 views • 25 slides
Effective Acquisitions Strategies for Libraries
Explore key insights from a meeting at the Fox River Valley Public Library District, focusing on handling duplicate records, potential causes of duplicates, vendor interactions, and fiscal year rollovers in libraries. Understand best practices for merging duplicates without disrupting acquisitions p
0 views • 15 slides
Vital Statistics and Civil Registration Challenges in Palau
Palau faces challenges in ensuring complete birth and death registrations, with issues such as delayed registrations, reliance on family members for form completion, and lack of proactive information gathering. The country uses a web-based database system for e-registry and digitization, with effort
0 views • 8 slides
Efficient String Similarity Search: A Cross Pivotal Approach in Computer Science and Engineering
Explore the importance of string similarity search in handling dirty data, with applications in duplicate detection, spelling correction, and bioinformatics. Learn about similarity measurement using edit distance and the challenge of time complexity in validation. Discover the filter-and-verificatio
0 views • 30 slides
Streamlining File Deduplication Process for Efficient Data Storage
Break down data into chunks, calculate signatures, and check for duplicates to optimize storage space. Deduplication method replaces duplicate chunks with pointers, improving write-heavy loads like backup and archival systems. Learn about the challenges and solutions for efficient file storage.
0 views • 19 slides
Improving Wireless Performance Through Content Overhearing Refactoring
Explore the concept of refactoring content overhearing to enhance wireless performance by focusing on throughput, leveraging overheard packets, suppressing duplicate data, and identifying sub-packet redundancy. Benefits of this approach include operating at finer granularity, redundancy elimination
0 views • 30 slides
TrustVare Email Duplicate Remover Software For OST, PST, MSG, EML, and MBOX.
Using the TrustVare Email Duplicate Remover Software, you can simultaneously remove numerous emails in various formats. Bulk duplicate emails from OST, PST, MSG, EML, EMLX, MBOX, and NSF files can be easily deleted with this software. A free trial ve
4 views • 8 slides
Navigating Workday Release Pitfalls: Essential Insights for Success
Avoid common pitfalls in Workday releases by understanding the challenges, key questions, safe harbor statements, and consulting services offered by Amethyst. Learn from Mack Baker, a seasoned Workday Practice Director, about the significance of a well-defined release process and the risks of a norm
0 views • 13 slides
Pyrethroid Pollinator Risk Assessment Proposal Overview
The Pyrethroid Working Group conducted a comprehensive investigation into existing pyrethroid study data to address EPA's request for a pollinator risk assessment. The proposal aims to bridge pollinator datasets across pyrethroids efficiently, avoiding duplicate data submissions. Key factors impacti
0 views • 14 slides
Identifying Redundancies in Fork-Based Development
Explore the challenges of redundant development in fork-based projects, such as duplicate pull requests, un-merged commits, and redundant feature implementations. Discover the impact of these redundancies on project maintenance, developer motivation, and overall efficiency. Learn about tools and str
0 views • 50 slides
Peoplesoft Procurement Training: Requisition Copying Process
Learn how to efficiently copy requisitions in Peoplesoft for procurement needs. Follow step-by-step instructions to duplicate and edit requisitions, manage requests, and submit them seamlessly through the system.
0 views • 12 slides
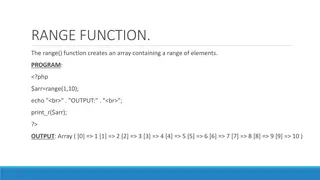
PHP Array Manipulation Functions Overview
The PHP code snippets demonstrate the use of various array manipulation functions like range(), min(), max(), array_slice(), adding/removing array elements, and array_unique(). These functions allow for creating ranges of elements, finding the minimum and maximum values in an array, extracting selec
0 views • 11 slides
Dealing with Generalization in Software Construction
Explore methods to address common code smells related to generalization in software development, such as dealing with duplicate code, inappropriate intimacy, and large classes. Learn how to apply techniques like Pull Up Field, Pull Up Method, and Extract Subclass to improve your code structure and m
0 views • 20 slides
Efficient and Effective Duplicate Detection in Hierarchical Data
This study explores the efficient and effective detection of duplicates in hierarchical data, focusing on fuzzy duplicates and hierarchical relationships in XML. It discusses the current and proposed systems, including the use of Bayesian networks for similarity computations. The methods involve vec
0 views • 25 slides
Advances in Big Data Integration and Cleaning Techniques
Explore the latest research on data cleaning and integration techniques in the era of big data. Topics cover similarity joins, real-world data challenges, similarity functions, and applications in near-duplicate object detection and collaborative filtering. Learn about essential operations for data
0 views • 36 slides
How To Merge Accounts In Salesforce
It\u2019s time to bring in the Salesforce expert who has already completed the Salesforce admin course to save your day. \n\nIn this article, we\u2019ve created a comprehensive and user-friendly guide on \n\nWhy do duplicate accounts appear in your Salesforce database?\nUseful tips to consider befor
0 views • 6 slides
Utilizing the Copy Tool in CAD: Techniques and Tips
Exploring the effective use of the Copy tool in CAD software to duplicate objects, navigate the command line prompts, and optimize workflow. Learn how to copy objects with precision, erase duplicates, and leverage multiple copy modes efficiently.
0 views • 8 slides