Overview of HEC API Scripting Part 1 and 2: DSS Files, DataContainer, HecTime, HecMath
This report delves into the HEC API scripting involving DSS files, DataContainer, HecTime, and HecMath. It covers important classes, accessing files, and the distinction between DataContainers and HecMath objects. Additionally, it compares Python and Java, highlighting their differences in interpret
2 views • 28 slides
What to Do When QuickBooks POS Client Cannot Connect to Server_ A Comprehensive Guide
Struggling with QuickBooks POS client connectivity issues? Our comprehensive guide offers detailed steps to resolve problems when QuickBooks POS client cannot connect to the server. Learn how to check network connections, configure firewall settings, and verify server configurations to restore seaml
1 views • 3 slides
Algorithms and Issues in Client Software Design
Explore the fundamentals of client software design, including the underlying algorithms, client architecture, and methods for identifying server locations. Learn how applications become clients, interact with TCP/IP protocols, and simplify client-side operations compared to server software.
5 views • 49 slides
New Accounts Rules and Client Money Safeguarding Overview
Explore the latest SRA Accounts Rules introduced on 25th November, emphasizing clearer standards, a revised definition of client money, and requirements for safeguarding and managing client funds. Understand the obligations and key considerations in handling client money to ensure compliance and fin
1 views • 26 slides
Understanding Client-Server Architecture
Client-server architecture is a computing model where a central server hosts and manages resources and services for client computers over a network. There are different types of clients and servers, each with unique characteristics and roles. This architecture offers various advantages and disadvant
3 views • 15 slides
Introduction to Linux Shell Scripting
Dive into the world of Linux shell scripting with a focus on the bash shell. Explore the basics of programming versus scripting, different shells available in Linux, common scripting errors, and the essential elements of writing shell scripts in Linux.
0 views • 26 slides
Simplifying Client-Side Scripting with jQuery
jQuery is a popular JavaScript library known for its fast and lightweight nature, designed to simplify client-side scripting of HTML. It provides a simplified way to navigate, manipulate, and interact with HTML documents, offering developers the ability to perform tasks like event handling, animatio
1 views • 11 slides
Understanding the Process of Social Case Work in Social Work Practice
Social case work involves a systematic process where a client seeks professional help through a case worker. This process begins with intake, where the client's needs and problems are assessed, followed by a psycho-social study to understand the client's adaptation to stress. The case worker probes
1 views • 24 slides
Understanding Social Case Work: Elements and Process
Social case work, as defined by H.H. Perlman, is a process used by human welfare agencies to assist individuals in coping with problems in social functioning. The fundamental elements include the person/client, problem, agency, process, and professional representative (social worker). The client, wh
0 views • 14 slides
Principles of Effective Client-Worker Relationship in Social Work
Understanding the principles of acceptance, communication, individualization, participation, confidentiality, self-awareness, and self-discipline is vital in establishing a positive client-worker relationship in social work. The initial interaction between the client and worker sets the tone for mut
0 views • 11 slides
Understanding Shell Variables and Scripting in Bash
Explore the realm of shell variables and scripting in the context of bash programming. Learn about variable manipulation, exporting, arithmetic operations, for loops, and common pitfalls in long shell scripts. Gain insights into the significance of variables in scripting and their impact on shell op
4 views • 13 slides
Investigating Add-On Cross Site Scripting Attacks: Abusing Browser Address Bar
This presentation delves into the realm of add-on cross site scripting attacks, exploring real-world examples and effects on popular social media platforms like Facebook and Twitter. The experiments conducted shed light on malicious behaviors, deceptive techniques, and potential severe consequences
0 views • 27 slides
A Dive into GDB Scripting Hidden Gems with Albert Lee
Delve into the world of GDB scripting hidden gems with Albert Lee on November 15, 2018. Explore essential features like debugging, register inspection, low-level memory views, and source-level code analysis. Understand techniques to enhance your debugging skills through the exploration of assembly c
0 views • 22 slides
Understanding Triangle Congruence Properties
Delve into the principles of congruent triangles by exploring the properties of side-side-side (SSS), side-angle-side (SAS), angle-side-angle (ASA), and right-angle-hypotenuse-side (RHS) congruence. Visual explanations help clarify how these properties determine if triangles are congruent.
0 views • 18 slides
Essentials of Penetration Testing: Expectations and Performance
This presentation delves into the realm of penetration testing, outlining the basic expectations and performance aspects. It emphasizes the importance of clear planning, client-side and auditor-side negotiations, and commencing the audit process diligently. With insights into the types of audits, sc
0 views • 32 slides
Essential Rules and Syntax for Naming and Using Variables in Bash Scripting
Learn the fundamental rules for naming variables in Bash scripting, understand the syntax for defining user-defined variables, and discover key considerations for assigning values and working with case-sensitive variables. Make the most of your scripting by following these guidelines closely.
0 views • 27 slides
Review of Basic Perl and Perl Regular Expressions
A thorough review of Perl and Perl Regular Expressions covering topics such as the importance of regular expressions in Perl, the benefits and drawbacks of using Perl for scripting, a simple Perl example, understanding Perl syntax, and how to run a Perl program. The review emphasizes Perl's strength
0 views • 60 slides
Client-Side Tips & Tricks for RadControls for ASP.NET AJAX
Discover the client-side functionality offered by RadControls for ASP.NET AJAX, empowering developers to create high-performing web applications. Learn about client-side basics, common features, events, data binding, jQuery integration, and more.
0 views • 25 slides
Shell Scripting Basics: A Comprehensive Guide
Learn the fundamentals of shell scripting through a detailed exploration of writing scripts, working with variables, understanding positional parameters, managing environment variables, utilizing variables and processes, and more in this informative guide featuring insights from Dr. Robert Siegfried
0 views • 36 slides
Understanding Client-Server Communication with Flask in Python
Explore the basics of implementing a client-server architecture using Flask in Python. Learn how to set up a server, create APIs, and interact with a client application. The process involves handling API calls, directing requests, and returning data to the client through the server.
0 views • 10 slides
Mitigating Client Frame Tracking in IEEE 802.11 Networks
Unencrypted and predictable frame fields in IEEE 802.11 networks can lead to client frame tracking, compromising user privacy. The Client Frame Tracking Countermeasures (CFTC) proposal aims to prevent tracking across epoch boundaries by obfuscating critical fields like PN, SN, and AID. Each epoch, l
0 views • 17 slides
Tips and Tricks for JSL Scripting in JMP - Enhance Your Data Analysis Skills
Explore helpful links, starting points, and tips for JSL scripting in JMP. Learn how to annotate errors, streamline your workflow, and handle complex data tasks effectively. Whether you're a beginner or looking to advance your skills, this guide has something for everyone.
0 views • 9 slides
PHP Scripting Essentials: From Basics to Advanced Concepts
Explore the comprehensive syllabus covering PHP scripting fundamentals, from variables and constants to decision-making statements, iterative loops, functions, and arrays. Understand the history of PHP, its evolution, and how it plays a crucial role in web development today.
0 views • 30 slides
Overview of Web Libraries, Tools, and Frameworks for Building Web Apps
Explore various client-side and server-side web libraries, tools, and frameworks such as Angular, Ember, Rails, Express, jQuery, d3, and more. Learn about the importance of web app frameworks, the challenges they solve, and considerations for choosing between server-side and client-side implementati
0 views • 57 slides
Understanding Client/Server Computing Architecture
Client/Server Computing architecture separates clients and servers over a network, allowing for file sharing, resource allocation, and service requests. Clients initiate services from servers, with transparent server locations and message-passing transactions. Systems with C/S architecture include f
0 views • 18 slides
Online Procurement Auctions for Resource Pooling in Client-Assisted Cloud Storage Systems
This study explores the use of online procurement auctions in client-assisted cloud storage systems to improve resource pooling and manage cloud outages. It discusses the benefits of client assistance, cloud storage services, common cloud outages, and potential solutions like Cloud Federation and Cl
0 views • 27 slides
Understanding Sessions and Cookies in Web Development
Sessions and cookies play a vital role in web development. Sessions represent a series of HTTP requests between a web browser and server, while cookies store data on the client side. PHP allows for managing sessions and cookies effectively, including setting, expiring, and deleting them. Sessions ar
0 views • 12 slides
Introduction to PHP Scripting Language and Operators
This content provides an overview of PHP, a server-side scripting language used to create dynamic and interactive web pages. It covers the basics of PHP scripting blocks, variable usage, operators, and their examples. Additionally, it explains common PHP operations like addition, subtraction, multip
0 views • 60 slides
Bash Control Structures Overview: Functions, Variables, Boolean Logic, and If Statements
This lecture covers essential topics in Bash scripting, including control structures such as functions, variable scope, boolean logic, and if statements. Understand how to declare functions, manage variable scope, use boolean operators for logic operations, and create conditional if statements for d
0 views • 11 slides
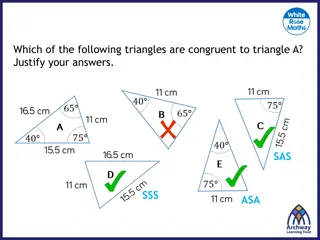
Understanding Triangle Congruence by SSS and SAS Postulates
Explore the Side-Side-Side (SSS) and Side-Angle-Side (SAS) postulates to prove triangle congruence. Learn how to use corresponding sides and included angles to establish congruence between triangles. Practice identifying congruent triangles and whether to use SSS or SAS for proof.
0 views • 11 slides
Exploring Triangle Similarity and Congruence
This content delves into understanding triangle congruence and similarity through various scenarios and visual representations. It discusses how to determine congruence using side-side-side, side-angle-side, and angle-side-angle criteria, and explores the concept of similarity in triangles based on
0 views • 21 slides
Analyzing Multimodality in Density Distributions Using JMP Scripting
Explore variability sources hidden in density distributions through JMP scripting. The analysis focuses on identifying and filtering distribution modes in semiconductor fab electrical measurements using kernel estimation and empirical rules. Antonio D'Angelo and Felice Russo from Lfoundry S.r.l. Ita
0 views • 6 slides
Intermediate Bash Scripting for Efficient Command Line Operations
Explore advanced Bash scripting techniques, including file redirection, file transfer methods, and script writing practices. Learn how to compress files, transfer data between local and remote hosts, and create executable Bash scripts for automated tasks in CSE 374.
0 views • 16 slides
Introduction to Scripting Techniques and Process
Explore the basics of scripting in this comprehensive example script that covers positional parameters, input handling, exit status testing, and various control statements like if, for, and while loops. Understand the importance of writing scripts, automation of tasks, and the use of special command
0 views • 45 slides
Introduction to Scripting Workshop Highlights
Explore the key points from the Introduction to Scripting Workshop held on October 15, 2015. Discover valuable resources, instructions for Windows and Mac access, and workshop setup details. Learn about shell scripting and practical examples like word counting in data science using the command line.
0 views • 59 slides
Enhancing Instructional Videos through Scripting: Insights from Elizabeth Sanders
Dive into the world of narrated instructional videos with Elizabeth Sanders as she shares her journey from unscripted to scripted content creation. Learn the importance of scripting, decision-making comparisons, and accessibility considerations. Discover tips and best practices to improve the qualit
0 views • 14 slides
Side by Side Refrigerator in Pakistan: Best Picks for Spacious and Stylish Kitch
A Side by Side Refrigerator can be an exciting addition to modern kitchens that combine design space, efficiency, and space all in one piece. \/\/kinkedpress.com\/side-by-side-refrigerator-in-pakistan-best-picks-for-spacious-and-stylish-kitchens\/
1 views • 1 slides
Understanding Cross-Site Scripting (XSS) Attacks and Prevention Measures
Cross-Site Scripting (XSS) is a prevalent security vulnerability in web applications that allows attackers to inject malicious scripts, potentially leading to unauthorized data access or manipulation. The content covers types of XSS attacks, finding vulnerable websites, testing exploits, and legal i
0 views • 10 slides
Understanding Cross-Site Scripting (XSS) Attacks
Learn about the dangers of Cross-Site Scripting (XSS) attacks, including Reflected and Persistent XSS types. This malicious practice allows attackers to inject harmful code into websites, potentially compromising user data and security measures. Discover how XSS attacks work, their impact on online
0 views • 38 slides
Understanding Client Expectations and Aligning with Business Goals
Effective strategies for understanding client/customer expectations and aligning them with business goals are crucial for success in IT-Design projects. By focusing on the client's needs and vision, IT professionals can elevate design value, improve timing and production processes, and aim for compr
0 views • 33 slides