Enhancing Security with Two-Factor Authentication in Funding & Tenders Portal
Increase in cybersecurity threats necessitates the use of two-factor authentication in the Funding & Tenders Portal to safeguard valuable information. Users are encouraged to adopt this secure login method, which will soon become mandatory. Methods such as mobile devices, SMS, and security keys are
1 views • 31 slides
Understanding Algorithms and Programming Fundamentals
Learn about algorithms, programming, and abstraction in computing. Explore the definition and properties of algorithms, the relationship between algorithms and programming, and the concept of abstraction. Discover how algorithms are like recipes and how abstraction simplifies complex tasks in comput
1 views • 17 slides
Near-Optimal Quantum Algorithms for String Problems - Summary and Insights
Near-Optimal Quantum Algorithms for String Problems by Ce Jin and Shyan Akmal presents groundbreaking research on string problem solutions using quantum algorithms. The study delves into various key topics such as Combinatorial Pattern Matching, Basic String Problems, Quantum Black-box Model, and mo
0 views • 25 slides
Understanding Approximation Algorithms: Types, Terminology, and Performance Ratios
Approximation algorithms aim to find near-optimal solutions for optimization problems, with the performance ratio indicating how close the algorithm's solution is to the optimal solution. The terminology used in approximation algorithms includes P (optimization problem), C (approximation algorithm),
2 views • 10 slides
Guide to Setting Up EU Login and Two-Factor Authentication
Learn how to create your EU Login account and add two-factor authentication for accessing Europass and other EU services. Follow step-by-step instructions to register, verify your email, and set up a secure password. Ensure a seamless process by understanding the difference between Europass and EU L
3 views • 18 slides
Two-Step Authentication Implementation for Enhanced Security
Learn about the implementation of two-step authentication at a university to combat phishing attacks and enhance security. Discover how Duo Security was used to provide a seamless two-step authentication solution, the challenges faced during the enrollment tool setup, and the successful implementati
0 views • 10 slides
Combining Graph Algorithms with Data Structures and Algorithms in CSE 373 by Kasey Champion
In this lecture, Kasey Champion covers a wide range of topics including graph algorithms, data structures, coding projects, and important midterm topics for CSE 373. The lecture emphasizes understanding ADTs, data structures, asymptotic analysis, sorting algorithms, memory management, P vs. NP, heap
0 views • 38 slides
Implementing 2FA for UW Azure AD: Best Practices and Options
Explore the implementation of two-factor authentication (2FA) for UW Azure Active Directory (AD) based on key decisions and options outlined in the provided slides. Understand the strategies for enforcing MFA, handling legacy authentication, and transitioning to cloud-based authentication. Discover
0 views • 19 slides
Security and Authentication in Electronic Filing Systems: Arkansas Subcommittee Report
Explore the subcommittee report on security and authentication in electronic filing systems for campaign and finance reports in Arkansas. Learn about user authentication, risks, mitigation strategies, and approaches used in other states. Discover the filing processes in both paper and electronic for
0 views • 24 slides
Understanding Randomized Algorithms: A Deep Dive into Las Vegas and Monte Carlo Algorithms
Randomized algorithms incorporate randomness into computations, with Las Vegas algorithms always providing the correct answer but varying in time, while Monte Carlo algorithms occasionally give wrong answers. Quick Sort is a classic Las Vegas algorithm that involves pivoting elements for sorting. Ch
4 views • 21 slides
Understanding Security Goals and Cryptographic Algorithms
Introduction to security goals such as privacy, data integrity, authentication, authorization, and availability, along with the usage of cryptographic algorithms like symmetric and asymmetric key algorithms, keyed hashing, and digital signatures for achieving different security objectives in communi
0 views • 13 slides
Understanding Algorithms and Programming: A Visual Introduction
Explore the fundamental concepts of algorithms and programming through visual representations and practical examples. Learn about algorithmic thinking, abstraction, recipe-like algorithms, and the importance of logical steps in accomplishing tasks. Discover how algorithms encapsulate data and instru
1 views • 17 slides
Distributed Algorithms for Leader Election in Anonymous Systems
Distributed algorithms play a crucial role in leader election within anonymous systems where nodes lack unique identifiers. The content discusses the challenges and impossibility results of deterministic leader election in such systems. It explains synchronous and asynchronous distributed algorithms
2 views • 11 slides
Mathematical Analysis of Algorithms in CMPE371 - Fall 2023-2024
Explore the mathematical analysis of algorithms in CMPE371 for Fall 2023-2024, focusing on non-recursive and recursive algorithms. Learn how to analyze non-recursive algorithms by deciding on input size parameters, identifying basic operations, and simplifying summations. Dive into recursive algorit
1 views • 31 slides
DAVA Drugs Authentication & Verification Application by National Informatics Centre
The DAVA Drugs Authentication & Verification Application, developed by the National Informatics Centre of the Government of India, enables authentication, tracking, and tracing of Indian drugs at different packaging levels. Manufacturers maintain Unique Serial Numbers for primary and secondary packa
2 views • 42 slides
Setting Up Two-Factor Authentication for HRMS Access
Learn how to enhance HR system security by setting up two-factor authentication for off-campus access. This tutorial covers the importance of two-factor authentication, using your phone as a second layer of security, initial setup procedures through Wyoweb, requesting permission for HR self-service
0 views • 9 slides
Pseudodeterministic Algorithms and Their Application in Search Problems
Pseudodeterministic algorithms provide a unique approach to the search problem associated with binary relations, offering an error reduction technique while sacrificing the ability to approximate the average value of a function. By introducing m-pseudodeterministic and pseudo-pseudodeterministic alg
1 views • 6 slides
Setting Up Multi-Factor Authentication at Moraine Park
Explore the options for setting up Multi-Factor Authentication (MFA) at Moraine Park, with Microsoft Authenticator as the recommended method. You can choose between using the Microsoft Authenticator app on a smartphone, receiving a text message, or a phone call for authentication. Detailed steps for
1 views • 16 slides
Understanding Authentication Mechanisms and Security Vulnerabilities
Authentication lies at the core of application security, serving as the primary defense against malicious attacks. This article explores various authentication technologies, including HTML forms-based authentication, multi-factor mechanisms, client SSL certificates, and more. It delves into common d
0 views • 70 slides
An Open-Source SPDM Implementation for Secure Device Communication
This article introduces an open-source SPDM (Secure Protocol and Data Model) implementation for secure device communication, developed by Jiewen Yao and Xiaoyu Ruan, Principal Engineers at Intel. SPDM aims to enhance device security through protocols for device authentication, session key establishm
0 views • 29 slides
Understanding STL Algorithms: A Practical Guide
Explore the world of STL algorithms through an insightful discussion on the definition of algorithms, the advantages of using STL algorithms over raw loops, and the different classes of STL algorithms available. Discover how these pre-built libraries can enhance your programming efficiency and code
1 views • 99 slides
Authentication and Authorization in Astronomy: A Deep Dive into ASTERICS
Explore the world of authentication and authorization in the field of astronomy through the lens of the ASTERICS project. Learn about the importance of verifying identities and granting access rights, the Virtual Observatory Approach, Single Sign-On standards, and Credential Delegation protocols. Di
0 views • 9 slides
Exploring the Role of Algorithms in Game Design
Delve into the world of algorithms in game design, from understanding the fundamental concept of algorithms to their pervasive presence in various aspects of gaming, such as military simulations, medical simulations, and gameplay mechanics. Explore how algorithms shape experiences in different types
0 views • 10 slides
Evolutionary Computation and Genetic Algorithms Overview
Explore the world of evolutionary computation and genetic algorithms through a presentation outlining the concepts of genetic algorithms, parallel genetic algorithms, genetic programming, evolution strategies, classifier systems, and evolution programming. Delve into scenarios in the forest where gi
0 views • 51 slides
Evolution of User Authentication Practices: Moving Beyond IP Filtering
The article explores the obsolescence of IP filtering in user authentication, highlighting the challenges posed by evolving technology and the limitations of IP-based authentication methods. It discusses the shift towards improving user experience and addressing security concerns by focusing on user
0 views • 22 slides
Online Advertising and Algorithms: Insights and Simplifications
Explore the world of online advertisements and algorithms through insightful discussions on online advertising, modern developments in online algorithms, and practical optimization strategies like budgeted allocation. Delve into topics such as decision-making under uncertainty, accessing algorithms,
1 views • 22 slides
Implementing Iterative Algorithms with SPARQL
This comprehensive guide explores the implementation of iterative algorithms with SPARQL, focusing on YarcData/Cray's approach to using these algorithms. It covers YarcData's interest in graphs, the Urika appliance, iterative algorithms in machine learning, implementation approach, and algorithms im
1 views • 12 slides
Overview of Sorting Algorithms and Quadratic Sorting - CS 330 Lecture Notes
Sorting algorithms play a crucial role in computer science and computing tasks, consuming a significant portion of computing power. Various algorithms such as Bubble Sort, Selection Sort, and Insertion Sort are discussed for sorting a list of values efficiently. Quadratic sorting algorithms like Sel
0 views • 30 slides
Understanding Sublinear Algorithms and Graph Parameters in Centralized and Distributed Computing
Centralized sublinear algorithms and their relation to distributed computing are explored, emphasizing the efficiency of algorithms in processing large inputs in sublinear time. Examples of sublinear algorithms for various objects are provided, along with the computation and approximation of graph p
1 views • 34 slides
Understanding Kerberos Authentication in Network Security
Kerberos is a trusted authentication service for establishing secure communication between clients and servers in a distributed environment. Developed at MIT, it addresses threats like user impersonation and eavesdropping by providing centralized authentication. Kerberos relies on symmetric encrypti
0 views • 13 slides
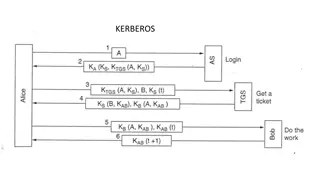
Understanding Kerberos Authentication Protocol
Kerberos is a secure authentication protocol developed at M.I.T. to allow workstation users to access network resources securely. It involves three servers: Authentication Server (AS), Ticket-Granting Server (TGS), and the server performing the requested tasks. The AS verifies users, TGS issues tick
0 views • 12 slides
CS260 Parallel Algorithms: Theory and Practice Review
This review covers essential topics from the CS260 Parallel Algorithms course by Yihan Sun, focusing on key concepts such as scheduler programs, cost models, reduce and scan techniques, PRAM models, atomic primitives, small algorithms, the master theorem, and sorting algorithms like Quicksort and Me
0 views • 25 slides
Understanding Strong Customer Authentication (SCA) for Online Payments in Ireland
The Irish Retail Payments Forum at the Central Bank of Ireland discusses the implementation of Strong Customer Authentication (SCA) under PSD2 regulations. SCA aims to enhance security by validating user identity through two-factor authentication. The deadline for full SCA migration is set for Decem
0 views • 13 slides
Secure Authentication Using ISO 15693 RFID Tags
The authentication process with ISO 15693 tags involves generating a signature using a hash of the tag UID and a private key. This signature, programmed during manufacturing, must match with the one generated by the reader for successful authentication. Advantages include enhanced security with priv
0 views • 7 slides
Uncovering Flaws in Authentication Solutions: A Privacy Concern
Delve into the potential privacy risks posed by design flaws in authentication solutions, as discussed by security consultant David Johansson. Explore scenarios where digital identities can be compromised, the implications of exposed electronic IDs, and the urgent need for software updates to safegu
0 views • 34 slides
Understanding Authentication and Authorization in Information Assurance
Explore the concepts of authentication and authorization in information assurance through a series of visuals and explanations provided by Adam Doup from Arizona State University. Learn about authentication terms, mechanisms, password systems, and UNIX standard hash functions. Gain insights into how
0 views • 26 slides
ASP.NET Web API Security and Authentication Overview
Explore the essential elements of ASP.NET Web API security, including HTTPS transport security, authentication filters, access to client identities, and OWIN middleware. Learn about securing your Web API with integrity protection, replay protection, and encryption for confidentiality. Dive into the
0 views • 29 slides
Exploring Stochastic Algorithms: Monte Carlo and Las Vegas Variations
Stochastic algorithms, including Monte Carlo and Las Vegas variations, leverage randomness to tackle complex tasks efficiently. While Monte Carlo algorithms prioritize speed with some margin of error, Las Vegas algorithms guarantee accuracy but with variable runtime. They play a vital role in primal
0 views • 13 slides
Modular Security Analysis for Key Exchange and Authentication Protocols
Explore the modular security analysis approach used to examine the security of key exchange and authentication protocols, focusing on the universally composable authentication with a global Public Key Infrastructure. The analysis involves splitting the system into smaller components, separately anal
0 views • 15 slides
Understanding Lock-Free and Wait-Free Algorithms in Concurrent Data Structures
Illustration of lock-free and wait-free algorithms compared to blocking algorithms, with insights on concurrent object execution, blocking vs. non-blocking algorithms, definitions, comparisons between locks, lock-free, and wait-free approaches, and explanations on making algorithms wait-free. Exampl
0 views • 23 slides