Matrimonial Profiles - Seeking Companionship in Diverse Backgrounds
Explore a diverse range of matrimonial profiles featuring individuals of different Hindu backgrounds and citizenships, all seeking compatible partners. From medical professionals to teachers, these profiles showcase individuals with varied interests and aspirations for a happy union. Discover potent
1 views • 29 slides
Colorado State Epidemiological Profiles - Substance Abuse Trends & Response Task Force
The Colorado State Epidemiological Profiles provide a state-level overview of data from various surveillance sources for prevention, intervention planning, monitoring, and evaluation. The profiles cover demographics, alcohol, marijuana, opioids, sustainability, and next steps. Updated every 2 years,
0 views • 12 slides
Understanding Epidemiological Profiles in Public Health Practice
Epidemiological profiles play a crucial role in substance abuse and mental health planning, helping professionals prioritize issues and raise awareness. The profiles include quantitative and qualitative data to analyze behavioral risk factors, consumption patterns, and clinical outcomes, sourced fro
1 views • 13 slides
Efficient Staffing Strategies for Nursing Units
Implementing effective staffing templates, self-scheduling options, and allowable overstaffing on specialized profiles can enhance data reporting accuracy and ensure adequate nurse coverage. Additional tips for accurate staffing numbers include adjusting profiles, managing floaters, and handling sta
0 views • 5 slides
Utilizing PARE Platform for Student Placements in Leeds
The PARE platform is a cloud-based system used in Leeds for managing student placements. Practice Supervisors, Assessors, and Educators play key roles in supporting students through PARE by maintaining profiles, accessing training, and ensuring accurate records. Practice Education Leads are responsi
0 views • 8 slides
Comprehensive Overview of EAL Profiles and Strategies for Language Skills Assessment
EAL Profiles offer a versatile tool for assessing pupils' language skills and setting targets. They can replace Form 1 documents, aid in transition planning, update progress profiles, and inform teaching strategies. These profiles include sections for pupil information, progress overview, review tab
0 views • 10 slides
Deception Game on Decoy Systems and Honeypots
Deception Game on Decoy Systems and Honeypots explores the use of deception technologies in computer security, focusing on decoy systems like honeypots. It delves into how attackers are lured into fake objects and the monitoring of their behavior to mitigate intrusion. The concept of fake honeypots,
4 views • 25 slides
Exploring Att&ck Matrix: Engage Ludicrous Speed
Dive into the world of the Mitre Att&ck Matrix, where crazy ampersands and Trebuchet Font cues you in on how to engage Ludicrous Speed and understand the basics of attacker/adversary tactics, techniques, and common use cases. Explore matrices, prevent attacks, and work programmatically with Att&ck u
0 views • 26 slides
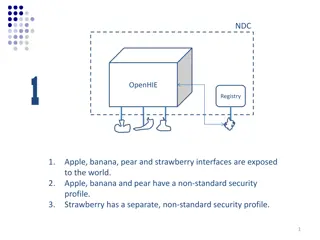
Comparison of Security Profiles in OpenHIE Registries
OpenHIE exposes interfaces with varying security profiles - non-standard in Scenario 1, standards-based in Scenarios 2 and 3. Scenario 1 requires managing multiple non-standard profiles, whereas Scenarios 2 and 3 facilitate plug-and-play with standard security protocols. Implications include ease of
4 views • 6 slides
Understanding Soil Profiles in Agricultural Science
Soil profiles are essential for classifying soils, with main profiles being Brown Earth, Podzol, and Gley. It's crucial to draw these profiles accurately for exams, considering horizons like O Horizon, A Horizon, B Horizon, and Bedrock. Brown Earth has a thick O horizon with uniform brown color, Pod
1 views • 8 slides
Understanding Network Security: Hijacking, Denial of Service, and IDS
This content delves into the concepts of spying and hijacking in network security, covering topics such as eavesdropping on packets, injecting packets into streams, denial of service attacks, and defense mechanisms like firewalls and IDS. It explores low-level attacks and defenses, including ARP cac
1 views • 81 slides
Attacks on Fully Random 64QAM Sounding Signal in IEEE 802.11-20/0964r0
Presentation by Intel demonstrates vulnerabilities in fully random QPSK and 64QAM sounding signals in IEEE 802.11-20/0964r0. Proposed attack methods, including Viterbi equalizer attacks, and solutions such as Secure LTF mechanism and windowed FFT are discussed to enhance security in ranging. The pre
0 views • 31 slides
Adversarial Risk Analysis for Urban Security
Adversarial Risk Analysis for Urban Security is a framework aimed at managing risks from the actions of intelligent adversaries in urban security scenarios. The framework employs a Defend-Attack-Defend model where two intelligent players, a Defender and an Attacker, engage in sequential moves, with
1 views • 26 slides
Efficient User Management System for Health Facilities
Record and manage user details effectively with the new Version 2.0 User Management feature. RNTCP has now registered over 35,000 PHIs, 140,000 Private Health Facilities, 15,000 Private Labs, 31,000 Private Chemists, across 700 Districts and 8,000 TUs in Nikshay. Enhance operations by editing TU pro
0 views • 26 slides
Learn about Rainforest Animals and Create Animal Profiles
In this activity, students will explore the characteristics of animals found in the rainforest such as the parrot, leopard, orangutan, toucan, and more. They will create animal profiles with their partner using German sentences. The profiles will include information on the animals' body parts, respi
0 views • 10 slides
EPA Oil and Gas VOC Speciation Improvement Efforts
EPA's VOC Speciation transforms inventory species into Air Quality model species to support chemistry, ozone, and aerosol chemistry. The Speciate4.5 update in 2016 added oil and gas profiles, including location-specific uncontrolled profiles and WRAP profiles for various basins. The Uinta TMSR profi
2 views • 10 slides
Introduction to Network Security Course
This network security course by Professor Christo Wilson covers fundamental security principles applicable to all systems, designing secure networked systems, understanding attacker mindsets, and respecting ethical boundaries in security research. The course aims to equip students with the ability t
0 views • 26 slides
Understanding Blending Attacks on Mixes by Meng Tang
Explore the effectiveness of blending attacks on mixes, including steps of a blending attack, attack models, factors affecting the attack, defense strategies, and insights from the attacker's viewpoint.
0 views • 25 slides
Understanding BIOS Flash and System Management Mode Internals
Dive into the intricacies of BIOS flash and system management mode internals, exploring SPI flash technology, attacker persistence strategies, Copernicus vulnerability scanning results, BIOS flash locations, and boot BIOS flash configurations. Uncover the significance of hardware pins in determining
0 views • 28 slides
Cybersecurity News and Insights
Explore the latest cybersecurity news and insights on hacking incidents, data breaches, vulnerabilities, and attacker strategies discussed in the context of MIS. Stay informed about ongoing cyber threats and how attackers operate once inside a system.
0 views • 31 slides
Understanding Security Threats and Vulnerabilities in Computer Systems
In computer security, threats exploit vulnerabilities to breach security and cause harm. Vulnerabilities arise from system weaknesses, attacker access, and capability. Threats include spoofing, data tampering, repudiation, information disclosure, denial of service, and elevation of privilege. Catego
0 views • 13 slides
Inspection Profiles of Largest Children's Homes Providers - August 2018
Explore the inspection profiles of the largest private and voluntary providers of children's homes as of August 2018. Gain insights into ownership and inspection outcomes of over 500 homes, highlighting key organizations and national comparisons. Dive into the varying inspection profiles and outcome
0 views • 5 slides
Understanding Wind Profiles and Aerodynamic Roughness Length
Wind profiles are crucial in understanding how wind speed changes with height in the boundary layer. The logarithmic and power law profiles depict this relationship, influenced by surface characteristics and obstacles. The aerodynamic roughness length, defining where wind speed becomes zero, remains
0 views • 14 slides
Evolution of Collisionless Plasma Bounded by Absorbing Walls
Study on the evolution of collisionless plasma between absorbing walls, analyzing rarefaction waves, density profiles, and plasma potential decay. Kinetic simulations reveal gas dynamics-like behavior with flat density profiles and linear velocity profiles leading to asymptotic decay. The influence
0 views • 15 slides
Insights from Northwick Park Emergency Department & Young Harrow Foundation Workshop
Explore statistics and insights from the Northwick Park Emergency Department and Young Harrow Foundation workshop, focusing on emergency medicine, mental health, youth violence, trauma patients, and demographic distribution in the NW London sector. Discover trends in ED attendances related to youth
0 views • 15 slides
PacketGuardian: A Tool for Static Detection of Packet Injection Vulnerabilities
This research paper introduces PacketGuardian, an effective static analysis tool designed to evaluate the robustness of protocol implementations against packet injection attacks. This tool supports precise context, flow, field-sensitive taint analysis, implicit flow analysis, and employs a summary-b
0 views • 23 slides
Understanding Traffic Light Profiles for Special Educational Provision
Traffic Light Profiles are tools used to support children with special educational needs by setting termly targets and strategies to help them reach their potential. These profiles are created in consultation with the SENDCO and class teacher, with a focus on addressing the child's needs and trackin
0 views • 6 slides
Understanding Threat Modeling and Offensive Security
Threat modeling in offensive security involves determining potential threat scenarios that could compromise a system, understanding the system from an attacker's perspective, and devising defensive strategies. It helps confirm security implementations, identify gaps, monitor shortcomings, vulnerabil
0 views • 31 slides
Understanding Web Security: Risks, Threats, and Safeguards
In the realm of web security, it is crucial to shift our mindset to anticipate malicious intent and potential vulnerabilities. Attackers can aim to access private data, manipulate information, disrupt services, or tarnish reputations. Familiarize yourself with common attacker goals, tools used, and
0 views • 18 slides
Evolution of TLS Security Profiles and Best Practices
TLS security profiles have evolved with the introduction of new profiles, retirement of old ones, and emphasis on non-downgrading best practices. Motivated by changes in security threats and cryptographic methods, the IETF has issued recommendations to ensure secure connections using TLS 1.2. The ne
0 views • 5 slides
Understanding Control Hijacking Attacks in Computer Systems
Explore the concept of control hijacking attacks in computer systems, including buffer overflows, format string vulnerabilities, and use-after-free exploits. Learn about the attacker's goal, examples of attacks, and the importance of understanding C functions, the stack, and the heap. Delve into sys
0 views • 39 slides
Network Security Fundamentals and Today's Security Challenges
Explore the basics of network security fundamentals and the current challenges in today's cyber landscape. Learn about security attacks, difficulties in defense, information security, key terminologies, cyberterrorism, attacker types, attack steps, and defense strategies. Understand the importance o
0 views • 17 slides
REST Interface for HORUS.AI Platform - Tutorial Highlights
This tutorial delves into creating profiles and users using the ProfileManager service in the HORUS.AI platform. It covers steps like creating new profiles, adding users to profiles, and setting rules. The focus is on providing a REST interface for seamless interaction with the HORUS.AI system. The
0 views • 15 slides
ConnectWise Incident Response Service: Expert Help for Security Incidents
ConnectWise Incident Response Service offers expert assistance 24/7 for handling worst-case security incidents. Gain direct access to incident response analysts, real-time management, recovery procedures, insights on attacker tactics, and post-incident monitoring. Choose from flexible service option
0 views • 13 slides
Insights from Discussions with Admissions Officials on School Profiles, Grading Scales, and Admissions Criteria
Discussions with university officials shed light on the importance of school profiles, grading scale variations, and admissions criteria. Insights include the significance of school profiles, diversity in grading scales, and the role of NHS in the admissions process. Admissions offices consider fact
0 views • 25 slides
International Protection Needs Profiles in the Caribbean
Identified international protection needs profiles for asylum seekers in the Caribbean region, highlighting main countries of origin such as Cuba, Haiti, Jamaica, and Venezuela. Details include specific profiles and protection needs per country, along with recommended actions when encountering indiv
0 views • 10 slides
Colorado Epidemiological Profiles 2021 - Substance Use Data and Analysis
The 2021 Colorado Epidemiological Profiles provide in-depth data and analysis on substance use patterns, impacts, and demographics in Colorado. The profiles cover alcohol, marijuana, opioids, and tobacco, along with special considerations for populations like LGBTQ, veterans, tribal communities, unh
0 views • 19 slides
Cryptology System Design Fundamentals: ARSA Cryptosystem Examination Solutions
The given content discusses the solution to an ARSA cryptosystem final examination design problem, involving the computation of public and secret keys for users A and B, encryption and signing of messages, and considerations for attacker interceptions and computations. The solution guides through th
0 views • 18 slides
Jamming-Resistant Encoding for Non-Uniformly Distributed Information
Protect systems against jamming with efficient encoding methods based on keystroke frequency distribution. Attacker profiles and assumptions analyzed. Approaches considered include algebraic manipulation detection codes and level-out codes. Initial results show promise in reducing error masking prob
0 views • 4 slides
Creating User Profiles for Product or Service Development
Engage in an exercise outlined on page 130 to craft user profiles for a product or service using a partner, pen, paper, and internet resources. Follow the provided template to document your findings and focus on your design problem or the Designing Space Travel brief. Utilize existing data or genera
0 views • 10 slides