Comparison of Security Profiles in OpenHIE Registries
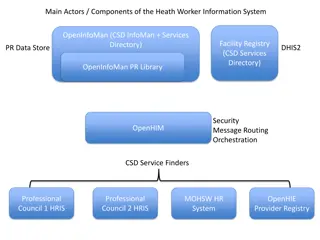
OpenHIE exposes interfaces with varying security profiles - non-standard in Scenario 1, standards-based in Scenarios 2 and 3. Scenario 1 requires managing multiple non-standard profiles, whereas Scenarios 2 and 3 facilitate plug-and-play with standard security protocols. Implications include ease of integration with other technologies and replacing OpenHIE elements seamlessly.
Download Presentation

Please find below an Image/Link to download the presentation.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.If you encounter any issues during the download, it is possible that the publisher has removed the file from their server.
You are allowed to download the files provided on this website for personal or commercial use, subject to the condition that they are used lawfully. All files are the property of their respective owners.
The content on the website is provided AS IS for your information and personal use only. It may not be sold, licensed, or shared on other websites without obtaining consent from the author.
E N D
Presentation Transcript
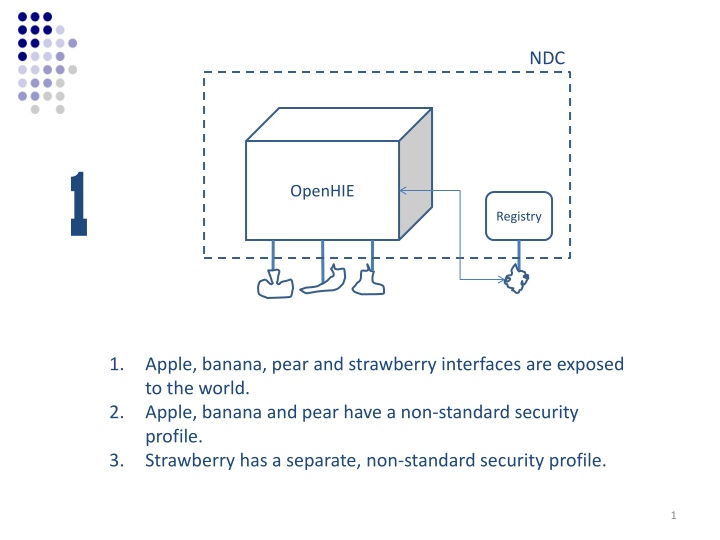
NDC 1 OpenHIE Registry 1. Apple, banana, pear and strawberry interfaces are exposed to the world. Apple, banana and pear have a non-standard security profile. Strawberry has a separate, non-standard security profile. 2. 3. 1
Implications of Scenario 1 OpenHIE is in the standards-development business Each client application will have multiple, non- standard security and access profiles to manage Developers must hand-code to our specs MOHs must trust them We are not plug-and-play with the world We are not plug-and-play within the NDC 2
NDC Registry 2 OpenHIE 1. Standards-based interfaces with standards-based security profiles are exposed to the world. Inside the datacentre, the FR is accessed via the strawberry interface; it is a trusted connection. 2. 3
Implications of Scenario 2 OpenHIE exposes standards-based interfaces Each client application will have a single set of standard security and access profiles to manage We are plug-and-play with the world OpenHIE could be replaced with another technology stack that is also based on the same standards We are not plug-and-play within the NDC 4
NDC Registry 3 OpenHIE 1. Standards-based interfaces with standards-based security profiles are exposed to the world. Inside the datacentre, the FR is accessed via a standards- based interface; it is a trusted connection. 2. 5
Implications of Scenario 3 OpenHIE is standards-based Each client application will have a single set of standard security and access profiles to manage We are plug-and-play with the world We are plug-and-play within the NDC Individual OpenHIE elements could be replaced with other elements that are also based on the same standards 6