Non Coronary Vascular Stents
Safe scanning of patients with non-coronary vascular stents (NCVS) in MRI settings in NHS Scotland. It covers key questions regarding the safety of patients with NCVS, including risks associated with MRI at different strengths, timing of MRI post-stent implantation, and the safety of various stent m
1 views • 9 slides
Evolution of CT Scan Technology and Terminology
The development of CT scanning technology revolutionized medical imaging. Godfrey Hounsfield introduced computerized axial transverse scanning in 1972, with Allan Cormack's mathematical contributions. Dr. Robert Ledley created the first whole-body CT scanner in 1974. Dr. Willi Kalender further advan
1 views • 121 slides
Enhancing Cybersecurity with Bluedog VAPT Services
Bluedog Security Monitoring offers essential cybersecurity services, including Vulnerability Assessment and Penetration Testing (VAPT). Their automated VAPT combines External Vulnerability Scanning and WebApp Scanning to provide comprehensive testing solutions that help businesses prioritize risks,
0 views • 16 slides
Environmental Scanning Techniques for Business Adaptation
Businesses are integral parts of society and must stay abreast of surrounding changes to thrive. Environmental scanning is crucial for businesses to adapt and evolve effectively.
0 views • 9 slides
Phased Array Antenna Design for Smart Intersection Radar Using Analog Devices ADAR-1000
Designing a phased array antenna system for a smart intersection radar project utilizing the Analog Devices ADAR-1000 beamformer. The system involves 4 independent phased arrays covering key directions in the intersection, with considerations for beam steering, beamwidth, and array configuration. Ke
0 views • 9 slides
Improve Your Reading Skills: Scanning and Skimming Techniques
Enhance your reading skills by mastering the art of scanning and skimming. Learn how to efficiently search for specific information without reading every word. Discover tips for scanning different types of texts and practice answering questions based on scanned content.
9 views • 12 slides
Understanding Java ArrayList in Amity School of Engineering & Technology
Java ArrayList in Amity School of Engineering & Technology is a dynamic array used for storing elements without a size limit. It offers flexibility by allowing element addition and removal at any time. This type of array is part of the java.util package, similar to the Vector in C++. The ArrayList c
0 views • 18 slides
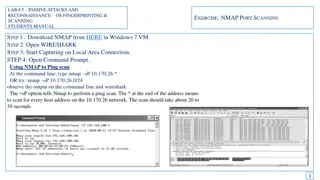
Passive Attacks and Reconnaissance using NMAP for Network Scanning
Learn how to use NMAP for passive attacks and reconnaissance through port scanning techniques like ping scan, TCP port scan, and stealth scan. Understand how to analyze the output in Wireshark to identify open ports and version numbers on target systems.
2 views • 7 slides
Passive Attacks and Reconnaissance in Network Security
Passive attacks involve monitoring target systems through port scanning or other means to locate vulnerabilities. Scanning is the first active action taken against a target network based on information gathered through footprinting, allowing deeper penetration. It includes scanning ports and service
0 views • 24 slides
Environmental Scanning Tool for Strategic Workforce Planning Cycle
In the Compare stage of strategic workforce planning, utilizing the Environmental Scanning Tool can assist in identifying work and workforce scenarios to achieve organizational goals. The tool consists of three templates including Choosing the Right Type of Data, Environmental Scanning Template, and
1 views • 9 slides
Effective Reading Strategies: Skimming and Scanning Techniques
Develop your reading skills with skimming and scanning techniques. Skimming helps you quickly grasp the main ideas of a text, while scanning allows you to find specific information efficiently. Learn how to differentiate between the two methods and when to use each effectively.
0 views • 7 slides
Understanding Roots of Equations in Engineering: Methods and Techniques
Roots of equations are values of x where f(x) = 0. This chapter explores various techniques to find roots, such as graphical methods, bisection method, false position method, fixed-point iteration, Newton-Raphson method, and secant method. Graphical techniques provide rough estimates, while numerica
0 views • 13 slides
Disaster Recovery and Incident Response Concepts
This content covers the essential concepts of disaster recovery, incident response, penetration testing, vulnerability scanning, and business continuity planning in the context of cybersecurity. It explains the goals and steps involved in penetration testing, vulnerability scanning tasks, business c
2 views • 15 slides
Network Monitoring and Vulnerability Scanning Overview
Kashif Mohammad from the Department of Physics at the University of Oxford provides insights into their setup involving ZEEK, ELK Monitoring, and OpenVas for network monitoring and vulnerability scanning. The team aims to enhance network security through structured classification of nodes based on t
1 views • 10 slides
Understanding Scanning in Thin Clients, RDP, and Citrix Environments
Learn about the difference between Fat Clients and Thin Clients, various types of Thin Clients, reasons for using Thin Clients, how programs are accessed on servers, and issues with scanning in RDP connections in this informative guide. Discover why Thin Clients are preferred for centralized softwar
1 views • 16 slides
Pixel Array Status and Drawing Rules for High-Resistivity Epi Design
This collection of images and descriptions provides an overview of the pixel array status as of April 26, 2019, along with drawing rules for high-resistivity epi design. The pixel array features various components such as Pixel_S1, Pixel_S3, and the overall array structure. Drawing rules highlight t
4 views • 9 slides
Understanding Functional Skills: Text Analysis and Application
This instructional text guides learners through the purpose of functional skills in analyzing different types of text, such as skimming and scanning, and understanding the features of various text genres. It includes activities to practice skimming, scanning, and detailed reading, with a focus on de
0 views • 13 slides
Implementing Barcode Scanning to Reduce Dispensing Errors in Pharmacy
Implementation of barcode scanning in pharmacy departments has been shown to significantly reduce dispensing errors, ensuring greater accuracy in medication dispensation. Despite the generally low error rate among pharmacists, high volumes of dispensing can still lead to a substantial number of erro
1 views • 20 slides
Introduction to Microphone Array Beamforming: MATLAB Tutorial Series
Explore microphone array beamforming techniques in this MATLAB tutorial series by Pouyan Ebrahimbabaie from the Laboratory for Signal and Image Exploitation at the University of Liège, Belgium. Learn about acoustic array geometry, signal processing, time-delay beamforming, and more to enhance audio
0 views • 27 slides
Understanding the Array Scanning Method in Electromagnetics
Exploring the Array Scanning Method (ASM) for analyzing the field of a single source near an infinite periodic structure. The notes cover the geometry, analysis, phasing, and field calculations involved in an infinite 2D periodic array of metal patches excited by dipole sources, providing insights i
0 views • 25 slides
Array Indices: Starting at 0 or 1?
The debate over whether array indices should start at 0 or 1 continues. A compromise of 0.5 was rejected, leading to discussions on JavaScript syntax, function definitions, and iterator implementations in programming. Explore the intricacies of array indexing and programming practices.
1 views • 19 slides
Leading Axis Theory and Practice in Array Kingdom 2023
Exploring the concept of Leading Axis Theory and Practice in the Array Kingdom of Elsinore 2023. The discussion covers essential keys like Rank and Dyadic Transpose, Make Functions apply to whole arrays, and Theory Arrays of various ranks. The images provide insights into major cells, leading axes,
0 views • 32 slides
What Are the 5 Benefits of Choosing an Advanced MRI Scanning Centre in Panchkula for Accurate Diagnosis
early diagnosis is equally important in treatment. If you are in Panchkula or the places nearby, it is a very wise decision to opt for a modern MRI scanning centre, for example, Kior Healthcare.
1 views • 3 slides
Different Reading Techniques: Skimming and Scanning Explained
Reading involves the process of gaining meaning from text using eyes and brain. Skimming and scanning are two specific types of reading techniques that help readers to quickly grasp the main idea or find specific information in a text. Skimming is like gist reading, where you get a general idea of t
0 views • 17 slides
Understanding Array Indexing and Representation
Visual guide explaining how arrays are indexed and stored in memory, including defining upper and lower bounds, determining array length, and denoting array elements. Example illustrations provided for easy comprehension of array concepts.
0 views • 124 slides
Exploring MongoDB: Array Operations, Data Modeling, and NoSQL Concepts
Delve into MongoDB array operations such as accessing array elements with $slice, data modeling concepts, and the absence of joins in NoSQL systems. Learn how MongoDB handles relationships, querying nested data, and the nuances of data modeling in comparison to relational databases.
0 views • 43 slides
Cybersecurity Footprinting and Scanning Techniques
Learn about the techniques involved in cybersecurity footprinting and scanning to protect against information gathering, target acquisition, and unauthorized access. Explore topics such as network enumeration, DNS interrogation, and scanning methods to identify vulnerabilities and enhance security m
0 views • 8 slides
SKA1 Low Assembly Integration & Verification Plan
The SKA1 Low Assembly, Integration, and Verification (AIV) Plan outlines the responsibilities of the AIV Consortium, consortium partners, and the roll-out plan for the SKA1 Low telescope. The plan encompasses user requirements validation, system verification, operational concepts, and more. It detai
0 views • 12 slides
Conformal CPW Folded Slot Antenna Array on Kapton Substrate at North Dakota State University
The study conducted at North Dakota State University involves the design and analysis of a conformal CPW folded slot antenna array printed on a Kapton substrate. The research covers topics such as introduction, background, design guidelines, and measurement results. Various parameters of the antenna
0 views • 19 slides
Basics of Java Arrays and Array Manipulation
Learn about the fundamentals of Java arrays, including initialization, literals, indexing, and the special value of null. Explore how arrays function as reference types and how array cloning can be used to create shallow copies. Understand the implications of passing arrays to methods and how change
0 views • 44 slides
Broadband Array Processing of SH-wave Data Using Superarrays
Broadband array processing of SH-wave data using superarrays at High Lava Plains (HLP) with a flexible array of 118 broadband stations deployed between 2006-2009. The processing involves transverse component displacement seismograms aligned and normalized to unity on direct-S, and Vespagrams analysi
0 views • 15 slides
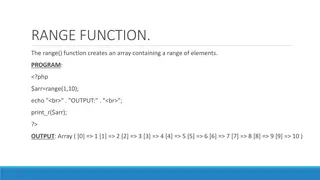
PHP Array Manipulation Functions Overview
The PHP code snippets demonstrate the use of various array manipulation functions like range(), min(), max(), array_slice(), adding/removing array elements, and array_unique(). These functions allow for creating ranges of elements, finding the minimum and maximum values in an array, extracting selec
0 views • 11 slides
Exploring Array-Oriented Solutions in APL by Richard Park
Array Programming Language (APL) offers a powerful approach to problem-solving through array-oriented solutions. Richard Park delves into the intricacies of APL, highlighting its tools of thought, language primitives, and problem-solving techniques. The webinar covers the significance of notation as
0 views • 40 slides
Exploring Atomic Dimensions: Scanning Probe Microscopy
Delve into the world of nanoscale imaging with Scanning Probe Microscopy (SPM) techniques like Scanning Tunneling Microscopy (STM) and Atomic Force Microscope (AFM). Unlike optical microscopes, SPM methods break the diffraction limit by relying on intermolecular forces and quantum tunneling for unpa
0 views • 26 slides
Understanding the Shoe Lace Method for Finding Polygon Areas
The Shoe Lace Method is a mathematical process used to determine the area of any polygon by employing coordinate geometry. By following specific steps, including organizing coordinates, multiplying diagonally, and adding columns in a certain manner, the method allows for a straightforward calculatio
0 views • 8 slides
The GP35 Experiment - Scintillator Array Preparatory Phase
Technical details of the GP35 experiment involving the assembly and testing of scintillator detectors for the Giant Radio Array for Neutrino Detection. It covers the setup, components, assembly, operation, maintenance, and test results of the detectors. Mistakes encountered during the process are hi
0 views • 13 slides
Linear Antenna Arrays: Theory and Applications
Introduction to linear antenna arrays, including the concept of distributing radiating elements, combining array elements for specific beam characteristics, and the theory behind linear antenna arrays. Exploring the benefits of linear arrays in obtaining narrow beams, fan beams, and scanning capabil
0 views • 20 slides
Understanding Arrays in PHP Programming
Arrays in PHP play a crucial role in storing and manipulating data efficiently. This snippet demonstrates the use of numerical and associative arrays, modifying elements, removing array elements, retrieving array size, handling nested arrays, and processing arrays with loops in PHP. Explore various
0 views • 9 slides
Effective Reading Techniques: Skimming, Scanning, and More
Explore different reading techniques like skimming, scanning, extensive reading, and intensive reading. Skimming helps to quickly grasp the main idea, while scanning is useful for finding specific information. Extensive reading is for pleasure, while intensive reading involves deep understanding and
0 views • 6 slides
Metamaterial-Based Series Connected Rectangular Patch Antenna Array for UHF RFID Readers
The metamaterial-based UHF RFID reader antenna array comprises features like rectangular patches, inter-digital capacitors, tuning stub, and a series fed array. The prototype dimensions and substrate details are provided along with resonant frequency observations. Test results include S-parameters o
0 views • 15 slides