Revolutionizing Financial Systems with Aquo Protocol
Aquo aims to integrate global financial systems into a unified protocol, addressing issues like limited liquidity, high costs, and restricted access to diverse assets. By tokenizing Real World Assets and offering innovative solutions, Aquo empowers investors with enhanced liquidity, global access, a
2 views • 10 slides
Enhancing Access to Medicines and Health Products through Innovative Approaches
Global Health Centre experts discuss how building access into innovation can ensure better access to medicines, vaccines, and health products. Key ideas include planting seeds for access early in innovation, exploring alternative innovation models, and rethinking the relationship between innovation
4 views • 20 slides
2022 Thales Access Management Index
Thales Access Management Index highlights the current landscape of access security, revealing insights on multi-factor authentication adoption, remote and privileged user access management, VPN usage trends, challenges faced, and preferences towards third-party access management. The report emphasiz
2 views • 9 slides
Guidelines for Expanded Access to Investigational Drugs and Devices
Providing guidance on types of Expanded Access for drugs, biologics, and devices, this content explains the concept of Expanded Access and the criteria that must be met. It covers different types of Expanded Access for drugs and devices, emphasizing the importance of patient safety and benefit. The
0 views • 10 slides
Personnel Safety Systems and Access Control at CERN Facilities
Personnel Safety Systems at CERN include ODH detection, fire safety measures, and access control to protect personnel from hazards. Various access control layers are implemented to regulate entry to different parts of the facility, ensuring only trained personnel access underground areas. Biometric
0 views • 19 slides
Effective Coordinating Structures for Response Operations
Operational coordination involves actions and activities to enable decision-makers to determine appropriate courses of action for various incidents, including homeland security operations. Coordinating structures help organize response efforts to address mission requirements, improve access to resou
3 views • 19 slides
Understanding Data Structures in CSC 207 with Dr. Olatunji K. A.
This course covers the objectives, learning outcomes, and contents related to data structures in CSC 207. Students will learn about data type specifications, representation techniques, algorithm analysis, recursive methods, and practical applications of data structures. The course delves into basic
1 views • 22 slides
Port of Stockton Restricted Area Access Control and ID Card Policy
Access to restricted areas at the Port of Stockton facilities requires possession of a TWIC (Transportation Worker Identification Credential). Only authorized personnel, such as employees, contractors, and those with regular access, may receive a Port Access Card after approval by the Facility Secur
0 views • 6 slides
Understanding Control Structures in Programming
Control structures in programming allow programmers to manage the flow of execution with selection/decision and repetition/loop structures. This chapter explores different types of selection control structures like if, if-else, nested if-else, and switch-case statements, providing examples and exerc
2 views • 30 slides
Exploring Trees Data Structures Using C - Second Edition
Learn about trees data structures in the context of programming using the C language. This comprehensive guide covers topics such as types of trees, tree creation, traversal, basic terminologies, and different tree structures like binary trees and binary search trees. Dive into the world of trees da
2 views • 54 slides
Introduction to Database Security and Countermeasures
Database security is essential to protect data integrity, availability, and confidentiality. Countermeasures such as access control, inference control, flow control, and encryption can safeguard databases against threats. Access control restricts user access, inference control manages statistical da
0 views • 26 slides
O3 Access Control Solution Overview
O3 Access Control Solution offers unique selling points like single-seat management software, role-based permissions, customizable user information, and more. The system includes a compact controller with multi-format reader support and BACnet Access objects. It integrates with other O3 modules for
0 views • 10 slides
Understanding Data Structures: A Comprehensive Overview
Data structures are schemes for organizing data in a computer's memory, influencing program performance. Common structures like queues and binary trees are outlined, illustrating their organization and use cases. The choice of data structures impacts task efficiency, with programmers analyzing data
0 views • 20 slides
Design of Head Works and Canal Structures - Learning Objectives and Evaluation
This course covers the design concepts, principles, methods, and procedures related to the design of irrigation head works and canal structures. Topics include irrigation network layout, diversion head works design, seepage analysis methods, protection works, canal profile design, canal head regulat
0 views • 4 slides
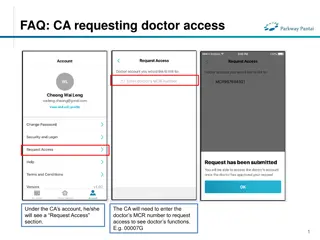
FAQs for Doctor and Clinical Assistant (CA) Account Access Management
Learn how CAs can request access to doctors' functions by entering the MCR number, how doctors can grant or remove CA access, and how CAs can manage access to multiple doctors. The process includes requesting, approving, and unlinking accounts, ensuring efficient and secure access management in a cl
0 views • 4 slides
Understanding x86-64 Procedures and Data Structures
This content provides insights into x86-64 programming, covering topics such as procedures, integer registers, stack frames, locals in the red zone, interesting features of stack frames, arrays, multi-dimensional structures, and more. It dives into the usage conventions of integer registers, the all
0 views • 44 slides
EventsHQ Virtual Event Registration: User Access and Setup Guide
This comprehensive guide provides step-by-step instructions on setting up virtual event registration using EventsHQ. It covers how users can access event details, join the event, and includes best practices for sharing access links. Learn how to utilize the Virtual Event Details feature, send remind
1 views • 19 slides
Innovative Resistive Layers and Structures for Particle Detection at CERN
Explore the latest advancements in resistive layers and structures designed for particle detection at CERN. The research covers various types of resistive structures, including GEM and BULK Micromegas, and delves into topics such as spark protection, energy levels, and material vaporization. Detaile
0 views • 39 slides
Understanding Looping Structures in PHP
Looping structures are essential in programming for writing iteration logics. This article delves into the importance of looping structures, different types in PHP, and creating basic logic using loops like for, while, for each, and do-while. Learn the syntax, parameters, examples, and flow charts t
0 views • 23 slides
Mix and Match Data Structures for Efficient Algorithms
Discover how to combine basic data structures like arrays, linked lists, and trees to create specialized data structures for various applications. Explore the concept of mix-and-match data structures with multiple organizations to implement efficient algorithms like adjacency lists and matrices for
0 views • 12 slides
Accessible Voting System for Californians with Disabilities
Learn about the Remote Accessible Vote-by-Mail System in California, designed to empower voters with disabilities to securely access, mark, and return their ballots from any computer with internet access. Find out who is eligible to use the system, how to access and return the ballot, and the steps
0 views • 23 slides
Dell Networking Solutions for BYOD and Guest Access Projects
Dell offers end-to-end solutions for Bring-Your-Own-Device (BYOD) and guest access projects, enabling secure employee access and controlled connectivity for visitors. The framework includes mobility business models, device security, network protection, and scalability. Dell supports customers in imp
0 views • 11 slides
Comparison between Array and Linked List Data Structures
Linked lists and arrays are commonly used data structures in programming. Linked lists offer flexibility in size changes and efficient rearrangement of elements, while arrays provide direct access to elements based on their index. Linked lists involve pointers connecting elements, allowing for dynam
0 views • 24 slides
Role-based Access Control Policies and Security Properties Overview
This content provides an overview of Role-based Access Control (RBAC) policies, Administrative RBAC (ARBAC) systems, and security properties in the context of access control in large organizations. It discusses the implementation of RBAC in various software systems, the assignment and revocation of
0 views • 18 slides
Open Access at Charles University: Opportunities and Challenges
Charles University is navigating the landscape of open access following the implementation of the Czech National Open Access Strategy. The university is working towards making all research articles and proceeding papers open access, monitoring article processing charges, and promoting open access as
0 views • 24 slides
Understanding Filesystem Security Principles and Access Control
Learn about filesystem security, general principles, discretionary access control (DAC), closed vs. open policy, closed policy with negative authorizations, and access control entries and lists. Discover how files and folders are managed, the role of access control lists (ACLs), and the different le
1 views • 56 slides
Understanding Ethernet and Multiple Access Protocols in Computer Networks
Exploring the fundamentals of Ethernet and multiple access protocols in computer networks, this content discusses the two primary categories of multiple access protocols - contention access and controlled access. It delves into topics such as CSMA/CD, LANs, performance of multiple access schemes, ad
0 views • 7 slides
Understanding Shared Memory, Distributed Memory, and Hybrid Distributed-Shared Memory
Shared memory systems allow multiple processors to access the same memory resources, with changes made by one processor visible to all others. This concept is categorized into Uniform Memory Access (UMA) and Non-Uniform Memory Access (NUMA) architectures. UMA provides equal access times to memory, w
0 views • 22 slides
Performance Analysis of Synchronization Methods in Concurrent Data Structures
Explore the impact of synchronization methods on the performance and behavior of concurrent data structures in multithreaded applications. The study involves developing and implementing concurrent data structures, analyzing coarse-grain locking, fine-grain locking, lock-free mechanisms, and assessin
0 views • 25 slides
Understanding Structures and Unions in C Programming
Exploring the concept of structures and unions in the C programming language, this reference material covers their definition, initialization, assignment, members, arrays, and nested structures. Learn how structures aggregate data types and how unions can share memory locations. Gain insights into s
0 views • 20 slides
Exploring Single Layer Structures with Cube Conversations
Dive into the exploration of single-layer structures with Cube Conversations. Discover different perspectives on visualizing these structures and uncover various ways to analyze and think about them. Engage in critical thinking and problem-solving to understand the composition of unit cubes in the g
0 views • 5 slides
Understanding Access Changes and Community Relations at Fermilab
Access to Fermilab has become more complicated due to changing DOE guidance and security posture. Efforts are being made to streamline access while addressing security gaps. Public access to outdoor areas of the Fermilab campus is still encouraged, but communication regarding access changes needs im
0 views • 12 slides
Harvard Chan School 2021 Yearly Access Review Process
The Harvard Chan School conducts its annual Yearly Access Review (YAR) process to review user access to various financial systems. The process involves assessing permissions, levels of access, and organizational details for each team member. Instructions are provided on reviewing worksheets, adding
0 views • 19 slides
Understanding Security Access in PeopleSoft Finance
Explore the various levels of security access in PeopleSoft Finance, from basic entry access to transaction entry, approvals, and procurement processes. Learn how to request individual and department security access and find relevant forms on the financial services website. Discover the different ty
0 views • 11 slides
Overview of PaNOSC Workshop API Endpoints & Data Structures
This project discusses the API endpoints and data structures from the PaNOSC Workshop, focusing on reviewing use cases, required search results/data, actors involved, and the design of endpoints reflecting proposal/experiment processes. It covers detailed discussions on data models, instrument setup
0 views • 19 slides
Comprehensive Guide to Algorithms and Data Structures Course (CS211)
Explore the world of algorithms and data structures with the CS211 course instructed by Modhi AlSobeihy. Enhance problem-solving skills, implement algorithms, select appropriate data structures, and apply object-oriented concepts in application design. The course covers a range of topics from theory
0 views • 11 slides
Resonance Phenomena in Grating Structures and Applications
Resonance phenomena in grating structures, such as dielectric or metal gratings on substrates, offer sensitive elements for detecting biological and chemical agents. The sensitivity of these structures is described by equations relating to resonant wavelength changes and the refractive index of inve
0 views • 20 slides
Development of Fetal Head and Neck Structures in Week 12
The fetal head and neck structures in week 12 exhibit a complex formation process involving contributions from all three embryonic layers and the neural crest. Neural crest plays a significant role in developing jaw skeletal elements, connective tissues, and tendons. The pharynx, starting at the buc
0 views • 30 slides
Understanding Data Structures and Abstract Data Types in Computational Thinking
Data organization and abstraction play a crucial role in computational thinking. Data structures like fasteners exemplify how different types of operations are associated with distinct characteristics. Abstract Data Types (ADTs) serve as specifications for data structures, outlining their essential
0 views • 17 slides
Overview of Bloom Filters and Succinct Data Structures
Bloom filters and succinct data structures are efficient data structures used for set-membership tests and approximate queries. Bloom filters offer compact storage for set membership with a trade-off in accuracy, while succinct data structures aim to balance high performance, low space cost, and sup
0 views • 22 slides