Reservoir Storage-Yield Analyses Using HEC-ResSim Lecture #2
This lecture covers the theory of storage-yield analyses, focusing on understanding yield, types of yield like firm yield, methods to calculate yield, and the importance of storing water for re-distribution. It delves into within-year and over-year reservoir storage concepts, illustrating the minimu
11 views • 47 slides
Overview of Physical Hydrology and Hydroclimatology
Physical Hydrology and Hydroclimatology, a science focusing on water properties, distribution, and circulation, covers topics such as mass balance, watershed transfer functions, reservoir sizing, storage-yield analysis, and optimal yield calculations. The concept of optimal yield highlights the impo
12 views • 10 slides
Importance of Timely Verification in Care After Death
Understanding the verification process and importance of timely verification in care after death is crucial for improving the experience of death and dying for families. This session covers the definitions, process, and care after death, emphasizing the significance of timely verification in end-of-
6 views • 15 slides
Electors Verification Programme Overview
The Electors Verification Programme (EVP) is a campaign initiative encouraging citizens to verify and authenticate electoral details, including family members. Various methods such as NVSP, Mobile App, and 1950 helpline are utilized for verification. Citizens can also submit details through BLOs to
3 views • 25 slides
Criticisms and Defenses of Verification and Falsification Principles
Explore the criticisms and defenses of the Verification and Falsification Principles in religious language. Understand how believers defend the use of religious language and analyze challenges posed to the Verification Principle by notable thinkers like Swinburne, Hare, and Mitchell. Delve into resp
4 views • 15 slides
GLP.BBBEE.(PTY).LTD - Your Trusted BEE Verification Agency
GLP.BBBEE.(PTY).LTD is a level 3 SANAS accredited BEE verification agency with 9 years of experience specializing in complex ownership structures. They offer professional BEE verification services with a team of technical signatories ensuring fair ratings for clients across various sectors. Their ef
2 views • 7 slides
Integrated Verification and Repair in Control Plane
Modern networks face challenges from incorrect configurations affecting millions of users. This presentation discusses the integration of verification and repair processes into the control plane, aiming for consistent and policy-compliant network operations. It explores the complexities of network c
4 views • 16 slides
Formal Verification and Automata Abstraction in Esterel
This content delves into the applications of formal verification and automata abstraction in Esterel, focusing on techniques such as verification by abstraction of automata, boolean verification using BDDs, bounded model checking in SAT/SMT, and more. The work of Gérard Berry at the Collège de Fra
0 views • 38 slides
Program Verification via an Intermediate Verification Language
Dive into the world of program verification through an intermediate verification language with a focus on static program verification, reasoning about programs, and separation of concerns. Explore tools like Dafny and verification architectures like Boogie and Why3, along with key concepts including
3 views • 36 slides
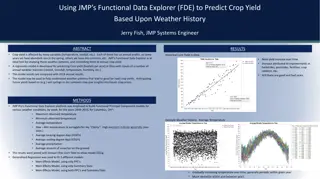
Predicting Crop Yield Using JMP's Functional Data Explorer
Crop yield prediction based on historical weather data in Ohio using JMP's Functional Data Explorer. A regression model is developed to forecast corn yield, correlating weather variables like temperature, rainfall, humidity, etc. Results show insights into weather patterns affecting crop yields, pot
2 views • 5 slides
Software Bugs and Formal Verification in Critical Systems
Software bugs have caused catastrophic events like radiation overdoses and rocket explosions, emphasizing the importance of formal verification in ensuring software correctness. Formal verification uses mathematical models to prove software correctness, offering higher assurance, especially in safet
1 views • 26 slides
Formal Verification of Cyberphysical Systems and Future Certification Methods
Explore the formal verification techniques and tools used in cyberphysical systems, including KeYMaera verification tool, applications in distributed car control and adaptive cruise control, and the formal verification of ACC algorithms. The future work section highlights considerations for sensor d
3 views • 17 slides
Comprehensive Solution for EU Digital COVID Certificate Verification
This solution offers face recognition, temperature monitoring, and verification of EU Digital COVID Certificates for personnel. It includes products like DHI-ASI7213X-V1-T1 and ASF172X-T1, with various unlocking modes and support for certificate verification. The system allows for accurate and fast
1 views • 7 slides
Automated Static Verification of Higher-order Functional Programs
Explore the automated static verification of higher-order functional programs, focusing on Haskell code. Learn about denotational semantics, program assertions, and tools like GHC for verification. Discover the emphasis on simplicity and structural properties for easy proofs. Consider utilizing exis
3 views • 22 slides
Gradual Program Verification and its Techniques
Gradual Program Verification introduces a method where static verification is combined with dynamic verification to ensure program correctness gradually. This approach allows for partial specifications and runtime checks to be gradually applied, reducing the risk of errors and overhead in software d
4 views • 18 slides
Bond Valuation Models and Yield Relationship
Explore the fundamentals of bond valuation, including the present value model and the yield model, to understand how bond prices are determined based on factors like market price, coupon payments, and yield to maturity. Learn about the price-yield curve, convexity, and how to calculate expected yiel
5 views • 25 slides
Enhancing Crop Yield Mapping Through Novel Sensing Approach
Case IH, a leader in farm equipment, aims to boost the resolution of yield maps generated during harvest. Current methods provide only average yield data, missing crucial details. By introducing a novel sensing approach utilizing crop height detection technology, a more precise and detailed resoluti
2 views • 11 slides
Warning Verification and Scoring Guidelines in Weather Forecasting Workshop
Learn about the verification of warnings, classical contingency scoring, false alarm ratio, hits, false alarms, missed alarms balance, threshold-based warning verification, and impact-based warning verification discussed in the IMS Warning workshop at KNMI Block III. Understand the importance of mai
0 views • 13 slides
Verification Modulo Versions: Towards Usable Verification
Explore the challenges and solutions in compile-time verification with CodeContracts in Visual Studio. Delve into addressing warnings, improving analysis precision, and managing syntactic baselines for a more reliable verification process.
2 views • 33 slides
Plastic Anisotropy and Yield Surfaces in Material Mechanics
This lecture introduces the concept of yield surfaces in material mechanics, focusing on both single crystal and polycrystal levels. It covers topics such as defining yield surfaces, common yield functions like Tresca and von Mises, construction methods for single slip systems, and the influence of
1 views • 53 slides
SKA1 Low Assembly Integration & Verification Plan
The SKA1 Low Assembly, Integration, and Verification (AIV) Plan outlines the responsibilities of the AIV Consortium, consortium partners, and the roll-out plan for the SKA1 Low telescope. The plan encompasses user requirements validation, system verification, operational concepts, and more. It detai
3 views • 12 slides
ICAO Strategic Objective: Economic Development of Air Transport Verification and Validation Overview
This content provides an in-depth analysis of the ICAO Strategic Objective focusing on the economic development of air transport through verification and validation processes for air carriers. It includes details on forms verification, economic analysis, and policy considerations discussed at the IC
4 views • 22 slides
Overview of Program Verification Tools and Techniques
Explore the pillars of program verification, early mechanical verification systems, software quality assurance, and a spectrum of verification tools used for ensuring functional correctness, safety-critical systems, and more. Discover the role of proof assistants and automatic decision procedures in
1 views • 21 slides
Introduction to UVM: Verification Methodologies Overview
Explore the Universal Verification Methodology (UVM) for writing modular, scalable, and reusable testbenches. Learn about UVM's key technical highlights, its support for migration towards Coverage Driven Verification (CDV), and the advantages of Constrained Random Verification (CRV) in functional ha
4 views • 20 slides
DeepFace: Advancements in Face Verification Technology
DeepFace by Yaniv Taigman, Ming Yang, Marc Aurelio Ranzato, and Lior Wolf from Facebook AI Group and Tel Aviv University presents a breakthrough in face verification technology. The system achieves human-level performance by utilizing deep neural networks for face recognition, detection, alignment,
1 views • 12 slides
Linear Programming
Water resources planning and management involve utilizing linear programming models to optimize decision-making for water allocation, storage, and yield. This involves constraints such as maximizing or minimizing objectives subject to linear equations. Firm yield and storage capacity play critical r
0 views • 36 slides
Basic Hardware Verification Flow
This content delves into the significance of verification in hardware design, emphasizing the need for meticulous code review, skilled engineers, and comprehensive testing practices. It explores the Universal Verification Methodology (UVM) and various effective protocols for ensuring robust verifica
4 views • 54 slides
Verification Job Aid
The Real Time Interface page in KEES allows users to track the status of their verification calls and view responses. Learn how to navigate the History List for call records and the Detail List for request and response details. Make sure to select the appropriate verification type before making requ
0 views • 23 slides
Enhancing Biogas Yield Through Post-Treatment of Residual Sludge
This report discusses the feasibility and benefits of increasing biogas yield through post-treatment of residual sludge. The study includes a detailed analysis of the process, findings from digestion tests, and conclusions drawn indicating a significant boost in biogas production. The post-treatment
18 views • 7 slides
Automatic Program Verifier and Boogie Language Overview
This content explores the concepts of automatic program verification through Separation of Concerns, Intermediate Verification Language, and Boogie language overview. It delves into the verification architecture using tools like Boogie and SymDiff, emphasizing the importance of structured verificati
2 views • 27 slides
End-to-End Crypto and Identity Verification Protocols at University College London
Explore topics such as end-to-end cryptography, anonymous communications, zero-knowledge data protection, and identity verification protocols at University College London through lectures and labs. Understand the procedures for non-interactive proof verification and the significance of identity as a
1 views • 33 slides
Religious Responses to the Verification Principle and Eschatological Verification
Explore how believers defend religious language against the Verification Principle, with a focus on responses to challenges and the concept of eschatological verification. Evaluations of the Verification Principle are discussed, highlighting the limitations and strengths in relation to religious tru
2 views • 16 slides
Effects of Micronutrients on Maize Grain Yield and Nutrient Uptake
Micronutrients are crucial for plant growth, influencing crop yield and quality. This study by Tafadzwa Chipangura aims to assess the impact of micronutrients, such as Cu, Fe, and Zn, on maize grain yield and macronutrient uptake. The experiment involved various treatments and analysis of maize grai
11 views • 15 slides
Forage Options and Yield Estimation for Drought-Stressed Corn
Explore forage options like silage and grazing for drought-stressed corn, along with methods to estimate yield based on grain yield, plant height, and actual measurements. Learn about nutrient content, conversion of silage to hay yield, and the value of normal corn silage in different scenarios.
4 views • 22 slides
Impact of Yield Level on Nitrogen Demand for Maize in the Midwest
Long-term trials at various locations in the Midwest explored the relationship between maize yield levels and nitrogen demand. Results from field experiments analyzed in the Central Great Plains emphasized the importance of optimal nitrogen rates for maximizing yield potential. Different sites and y
3 views • 17 slides
Modular Primal-Dual Fixpoint Logic Solving for Temporal Verification
Explore the innovative approach of solving temporal verification using modular primal-dual fixpoint logic to address non-safety verification challenges. Learn about constraint-based verification with constrained Horn clauses and extensions for non-safety verification in this cutting-edge research wo
1 views • 27 slides
DVCon Taiwan 2024 Design and Verification Contest - Authors, Design Scope, and Verification Plan
Explore the details of the DVCon Taiwan 2024 Design and Verification Contest, including information about authors, design scope, verification plan, methods, report, and conclusions. Get insights into the proposed verification strategy, integration process, evaluation metrics, and more.
9 views • 6 slides
Calculate Percent Yield in Chemistry Experiments
Learn how to calculate percent yield in chemistry experiments by understanding theoretical yield, actual yield, and efficiency. Practice problems provided for better understanding.
2 views • 5 slides
Understanding Care After Death and Verification Process
Learn about the importance of timely verification, the process of care after death, and the verification process. Discover why timely verification is crucial in end-of-life care and how to confirm death without a doctor. Explore expected deaths, verification criteria, and considerations for implanta
3 views • 15 slides
Understanding Automatic Program Verification with Dafny
Discover the world of automatic program verification using Dafny, a powerful tool for ensuring software correctness through mechanical verification techniques. Learn about program verification, Dafny's object-based language features, basic concepts, and practical exercises like reasoning about loops
0 views • 8 slides