Why You Need to Buy LinkedIn Connections
In the competitive landscape of professional networking, LinkedIn stands out as the premier platform for building meaningful connections, fostering professional relationships, and expanding your career opportunities. With millions of users worldwide, LinkedIn offers a vast network of professionals a
4 views • 2 slides
Efficient Remote Work Strategies for Optimal Productivity
Learn best practices for remote work to navigate slow VPN connections, offline mode usage, browser settings for better performance, and effective data synchronization. Discover ways to enhance productivity and avoid network-related challenges while working remotely.
5 views • 8 slides
2022 Thales Access Management Index
Thales Access Management Index highlights the current landscape of access security, revealing insights on multi-factor authentication adoption, remote and privileged user access management, VPN usage trends, challenges faced, and preferences towards third-party access management. The report emphasiz
2 views • 9 slides
Credentialing Process for Adjuncts and GTAs Created by Felipe Vargas
This process overview details the steps and requirements for credentialing adjuncts and Graduate Teaching Assistants (GTAs). It covers accessing the Wizard program, submitting necessary documents, and the workflow from department to Provost. Various credentialing avenues are explained based on degre
0 views • 20 slides
Best New Connections in Ravensdale
Are you looking for the Best New Connections in Ravensdale? Then contact Charlton Power Pty Ltd. They specialise in providing top-notch electrical solutions for residential, commercial, and industrial clients. From switchboard upgrades and private pole installation to new connections their skilled t
0 views • 6 slides
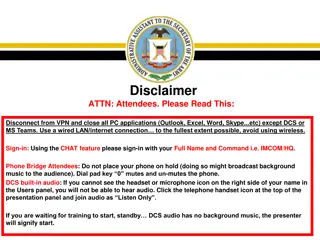
Army Records Management Virtual Symposium
Army Records Management-FOIA-Privacy-Civil Liberties Virtual Symposium will cover topics such as ARCIS, records retention schedules, record transfers, and accessing ARCIS accounts. Attendees are required to disconnect from VPN, use wired LAN, and follow specific guidelines for audio and phone usage
0 views • 21 slides
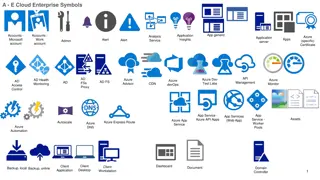
Symbolic Representation of Azure Cloud Enterprise Services
The images depict a variety of symbols representing different Azure cloud enterprise services, including application insights, analysis, monitoring, security, storage, virtual networks, and more. Each symbol represents a specific aspect or component of Azure services, such as VPN gateways, firewalls
0 views • 6 slides
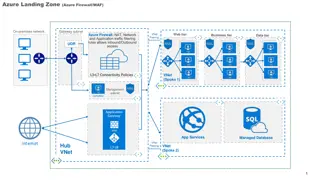
Azure Network Architecture Deployment Overview
An in-depth look at Azure network architectures, including landing zone configurations with Azure Firewall and WAF, deployment to primary Azure regions, hub and spoke models, network virtual appliances (NVAs), VPN tunnels, DMZ setups, and more. This comprehensive guide covers various network compone
6 views • 7 slides
Secure Networking Best Practices for Municipalities
Explore the implementation of secure networking practices for municipalities, including dedicated circuits, VPN connections, VLAN segmentation, and VoIP considerations. Learn about maintaining network integrity and protecting sensitive information in compliance with CJIS policies.
0 views • 9 slides
Syntactic Notions of the First Level in Linguistics
In this lecture, the syntactic notions of the first level in linguistics are discussed, focusing on word groups, simple sentences, and the essential features of actual division. The different types of syntagmatic groupings of words, such as notional words, functional words, and their combinations, a
1 views • 19 slides
DIT Demo Remote Access Guidelines for Working from Home
Explore the remote access guidelines for working from home provided by DIT Demo, covering essential aspects such as multi-factor authentication, virtual private network (VPN), virtual desktop infrastructure (VDI), conferencing options, and more. Learn about the necessary steps to access these resour
0 views • 11 slides
Modern Culvert Design Innovations in Tennessee's Transportation Infrastructure
Explore the evolution of culvert design in Tennessee, from the shift from moment connections to shear connections, adoption of AASHTO standards for federal funding compliance, and the utilization of pinned connections for efficient design and modeling in Opis and Excel spreadsheets.
4 views • 71 slides
Accessing and Utilizing CPCSSN Secure Research Environment (SRE)
Learn how to access the CPCSSN Secure Research Environment (SRE) for secure data analysis. Follow steps such as setting up VPN, accessing SQL databases, and establishing ODBC connections for statistical analysis using tools like SAS, R, SPSS, or Stata. Enhance your research capabilities within a sec
0 views • 12 slides
Overview of Loop Diagrams in Process Control Systems
Loop diagrams are essential documents in process control systems, providing schematic representations of hydraulic, electric, magnetic, or pneumatic circuits. They detail instrumentation arrangements, signal connections, power connections, and termination information. Guidelines and standards for cr
1 views • 5 slides
Business Continuity Planning in Times of Crisis
During challenging times like the current Covid-19 pandemic, it's crucial for businesses to develop a comprehensive business continuity plan. This plan should focus on maximizing productivity while minimizing risks to employees, clients, and vendors. Classify your employees into informational, hybri
0 views • 15 slides
What is NordVPN_ Is NordVPN safe and secure_
Share :\n \n \n \nA VPN, or Virtual Private Network, is a technology that creates a secure connection over a less secure network, such as the Internet. It allows users to send and receive data as if their devices were directly connected to a private
0 views • 12 slides
Network Deployment and Monitoring Overview
Explore key updates on network deployment for Pico2 testbed EOSC, including L3VPN deployment status, site connections, VPN management governance, and the importance of monitoring for cloud deployment. Gain insights into collaboration efforts between GEANT and RENATER, addressing challenges and advan
1 views • 7 slides
STM32WB BLE Secure Connections Overview
This detailed content provides insights into the secure connections in STM32WB BLE devices, covering aspects such as BLE security methods, encryption techniques, pairing processes, key distribution, and security modes and levels. It emphasizes the use of Long Term Keys (LTK), Diffie-Hellman key exch
0 views • 12 slides
Free Indian VPN for Tiktok
Access effortlessly with our Free Indian VPN for Tiktok, designed for fast speeds and secure browsing. Ideal for overcoming geo-restrictions and enjoying unrestricted content from India.
0 views • 5 slides
Free Indian VPN for Tiktok
Access effortlessly with our Free Indian VPN for Tiktok, designed for fast speeds and secure browsing. Ideal for overcoming geo-restrictions and enjoying unrestricted content from India.
0 views • 5 slides
Building Connections and Compiler Phases in College: Networking Strategies
Discover the benefits of building connections in college through networking strategies like reaching out to professors, TAs, and peers. Learn the importance of networking, ways to get involved on campus, and how to leverage your connections for personal and academic growth.
0 views • 39 slides
Building Friendships Where You Live: Pathways to Inclusive Connections
Understanding the importance of community connections for people with disabilities, this resource promotes friendship beyond typical relationships. It explores the benefits of friendships, strategies for meaningful connections, and the impact of support in fostering friendships regardless of locatio
0 views • 20 slides
Unix: Fundamentals and Connections
Explore the basics of Unix operating systems, terminology, types of Linux installations, and connecting to remote Linux machines. Learn about key concepts such as local vs. remote connections, SSH connections using passwords and keys, and tools like PuTTY for remote access.
1 views • 78 slides
Minimum Direct Connections to Achieve Simultaneous Access
In a computer science laboratory with 15 workstations and 10 servers, the minimum number of direct connections needed to ensure that any set of 10 or fewer workstations can simultaneously access different servers is determined using the Generalized Pigeonhole Principle. By strategically connecting w
0 views • 5 slides
MATLAB Remote Access Instructions for Off-Campus and BU Network Users
Access MATLAB remotely using VPN for off-campus and BU network users. Establish a VPN connection, control it via tray icon, and set up X-Win32 for SSH access. Download and install necessary software following step-by-step instructions provided. By following these steps, users can easily access MATLA
0 views • 11 slides
Implementing VPN for Secure Corporate Communication
A Virtual Private Network (VPN) offers a secure method for corporations with multiple sites to transfer data over the Internet while maintaining confidentiality. By encrypting data and using tunneling techniques, VPN software ensures that communications remain private, making it a cost-effective and
0 views • 10 slides
Asynchronous Transfer Mode (ATM) in Data and Computer Communications
Asynchronous Transfer Mode (ATM) is a packet transfer technology that supports multiple logical connections over a single physical interface. It uses fixed-sized packets called cells for data transfer. ATM bears similarities to packet switching and offers streamlined packet transfer with minimal err
0 views • 46 slides
Networking and Distributed Computing Systems Lab Setup Guide
Set up your lab environment for networking and distributed computing systems using Unix, Bash, and Emacs. Learn to access lab machines via SSH, use PuTTY and Terminal for communication, simulate Linux environment on Windows with Cygwin, run different OS on VMware Player, download and install Linux o
0 views • 14 slides
Troubleshooting Guide for SSLVPN Connection Issues
Learn how to troubleshoot common SSLVPN connection problems such as difficulties connecting to remote computers, network access device errors, conflicts with other programs, and issues with user privileges or certificates. Find solutions to resolve these issues and ensure a stable VPN connection.
0 views • 19 slides
Free Indian VPN for PUBG
Enhance your experience with our Free Indian VPN for PUBG, providing fast speeds and reliable connections. Perfect for bypassing geo-restrictions and accessing the game seamlessly from India.
0 views • 4 slides
Protect content from VPN requests
Safeguard your website's content by implementing measures to protect content from VPN requests and block. Enhance security and guard against possible abuse or illegal access by implementing sophisticated tools that examine incoming connections. In or
0 views • 4 slides
Protect content from VPN requests
Safeguard your website's content by implementing measures to protect content from VPN requests and block. Enhance security and guard against possible abuse or illegal access by implementing sophisticated tools that examine incoming connections. In or
0 views • 4 slides
Protect content from VPN requests
Safeguard your website's content by implementing measures to protect content from VPN requests and block. Enhance security and guard against possible abuse or illegal access by implementing sophisticated tools that examine incoming connections. In or
1 views • 4 slides
Best VPN for Tiktok
Discover the Best VPN for TikTok, offering high-speed connections and robust security to access and enjoy content without restrictions. Perfect for bypassing geo-blocks and enhancing your TikTok experience.
0 views • 4 slides
Risks of Unsecured Wireless Connections
Wireless connections are considered secured when users input a password following WPA or WPA2 standards. Unsecured connections lack encryption, leading to data interception, eavesdropping, and distribution of malware. Threats include data theft, cyber crimes, and misuse for illegal activities. Prote
0 views • 9 slides
MISSOURI CONNECTIONS
Unlock your potential with Erika Starr-Hunter, a dedicated international middle school counselor at Missouri Connections. Receive guidance and support to pave the way for your successful future. Trust in Erika's expertise to navigate the crucial transitional years of your education and personal grow
0 views • 9 slides
C2 Detection Techniques Part 1
In this comprehensive guide, explore C2 detection techniques, the importance of identifying persistent connections, and why starting with persistent connections is crucial. Learn about threats, methodologies, and the difference between bad actors and red teams. Get insights on where to start with pa
0 views • 30 slides
Extending Your Datacenter with Azure Site-to-Site VPN
Discover how to seamlessly integrate Microsoft Azure Network Site-to-Site VPN to extend your on-premise datacenter, showcasing common examples and key takeaways for setting up and managing the connection. Explore hybrid scenarios, capacity demands, remote site setups, and layered solutions for optim
0 views • 24 slides
ECCENTRIC CONNECTIONS IN STEEL STRUCTURES
This comprehensive overview delves into types of connections, eccentric connections, methods of analysis, and theoretical background in steel structures, covering seat connections, framed connections, bracket connections, and more.
0 views • 21 slides
Community Connections Implementation
Transforming Community Studies B into Community Connections, this initiative involves reviewing, refining, and implementing new subject offerings in various fields of study. Changes include updated learning requirements and assessment criteria, along with the introduction of new subject titles and a
0 views • 14 slides