Airport Security Market to be Worth $25.27 Billion by 2031
\u00ae, the airport security market is projected to reach $25.27 billion by 2031, at a CAGR of 8.6% from 2024 to 2031. Some of the major factors driving the growth of this market are stringent government regulations for airport security and the growing number of air passengers. In addition, increasi
6 views • 5 slides
KEERTHI SECURITY - Best Security Agencies In Bangalore
Keerthi Security is a security and facility management services provider in Bangalore. We are committed to offering top-notch security services for commercial and residential places. We aim to offer very secure and reliable security services to everyone. Our best-trained security guards are very sha
9 views • 11 slides
Sens Security Your Premier Personal Security Firm
In a world where personal safety cannot be taken for granted, Sens Security stands out as Melbourne's leading personal security firm. Our services are designed for those who demand the utmost in protection, whether you're a high-profile personality, a top executive, or an individual with unique secu
0 views • 6 slides
Sens Security Your Premier Personal Security Firm
In a world where personal safety cannot be taken for granted, Sens Security stands out as Melbourne's leading personal security firm. Our services are designed for those who demand the utmost in protection, whether you're a high-profile personality, a top executive, or an individual with unique secu
1 views • 6 slides
Sens Security Your Premier Personal Security Firm
In a world where personal safety cannot be taken for granted, Sens Security stands out as Melbourne's leading personal security firm. Our services are designed for those who demand the utmost in protection, whether you're a high-profile personality, a top executive, or an individual with unique secu
1 views • 6 slides
Understanding the Role of Security Champions in Organizations
Security Champions play a vital role in decision-making concerning security engagement, acting as a core element in security assurance processes within a team. They foster a security culture, reduce dependency on the CISO, and promote responsible autonomy and continuous security education in the org
3 views • 13 slides
Understanding Virtual Functions in C++
Learn about virtual functions in C++, their importance for achieving dynamic linkage and late binding, rules for defining virtual functions, differences between virtual and non-virtual functions, and examples illustrating their usage. Explore pure virtual functions and their role in creating abstrac
0 views • 7 slides
Important Guidelines for Virtual Care Services in Ontario
Virtual care services in Ontario effective December 01, 2022, require both patient and physician to be located in the province for insurance coverage. Specific codes for assessments and consultations have been updated, and services must follow defined criteria for eligibility. Initiating virtual car
0 views • 15 slides
Understanding the Roles of a Security Partner
Learn about the roles and responsibilities of a Security Partner, including requesting changes to security roles, approving security requests, and initiating access requests. Explore the overview of Workday Security, the security access request process, and the pre-request process flow. Discover how
1 views • 17 slides
Specialized Virtual Asset Services in Dubai | NH Management
NH Management is a leading virtual asset service provider in Dubai, offering specialized services to facilitate the opening of crypto virtual licenses in the UAE. Whether you\u2019re seeking a virtual license in Dubai or a Dubai virtual business lice
2 views • 8 slides
Requirements for Virtual/Online Teachers in the 2021-22 Academic Year
Legislation in Michigan impacts virtual and online courses, requiring districts to ensure proper teacher placement with valid certifications. Over 75% of sampled school districts had teachers lacking appropriate endorsements for virtual courses. The law mandates direct hire of qualified teachers and
1 views • 26 slides
Efficient Resource Management for Multi-Agent System Execution on Parallel Architectures with OpenCL
This research focuses on efficiently managing memory and computing resources for executing multi-agent systems on parallel architectures using OpenCL. The study presents a hybrid approach involving population-level molecular virtual chemistry and individual-level virtual cells. The work enhances a p
1 views • 33 slides
Understanding Virtual Reality: Types and Uses
Virtual Reality (VR) is a computer-generated environment that immerses users in realistic scenes and objects. This technology is widely used in entertainment, gaming, cinema, amusement parks, and social virtual worlds. There are three primary categories of VR simulations: non-immersive, semi-immersi
1 views • 10 slides
Exploring the Role of Learning and Development in Supporting Managers in Virtual Environments
The role of Learning and Development (L&D) in assisting managers with virtual learning is crucial in today's dynamic work landscape. This article delves into how managers prefer to learn, the impact of virtual working on their learning styles, barriers to optimizing virtual learning, and strategic s
0 views • 27 slides
Understanding Security in World Politics
Security studies delve into the intricate processes of defining and addressing security threats in global politics. It explores the contested nature of security definitions, emphasizes the political significance of security, and challenges the conventional boundaries of International Relations. The
0 views • 8 slides
OSBELTCA Board Meeting: September 20, 2023 - Virtual Attendees Guidelines
Attendees of the OSBELTCA Board Meeting on September 20, 2023, are instructed to mute their microphones unless directly addressed. The agenda includes call to order, mission statement review, approval of past meeting minutes, and discussion on granting licenses. The meeting will be recorded, and vir
0 views • 22 slides
Comprehensive Course Review: Security Research Cornerstones at Carnegie Mellon University
Dive into the essential topics of software security, network security, OS security, and cryptography in the course offered by Vyas Sekar at Carnegie Mellon University. Explore control flow hijacks, cryptography terminology, and the importance of network security in protecting data transmissions. Lea
0 views • 41 slides
Virtual Reality Software System at University of Illinois
The Virtual Reality Software System at University of Illinois leverages a Virtual World Generator to create alternative realities using synthetic models or real-world data. Tasks for the Virtual World Generator involve matched motion and user locomotion, while dealing with challenges like collision
0 views • 33 slides
Virtual Learning Update and Parental Meeting Information
Addressing virtual learning issues, the academy provides details on the schedule of virtual lessons for different year groups, contact information for support staff, and welfare calls for student well-being updates. A meeting is scheduled to discuss virtual learning matters. Parents are encouraged t
0 views • 7 slides
UIC Security Division Overview and International Activities
The UIC Security Division plays a crucial role in supporting the security platform of the International Union of Railways (UIC). Headed by Jacques Colliard, the division is based in Paris and consists of key personnel like Marie-Hélène Bonneau, Jos Pires, and Laetitia Granger. The division's activ
0 views • 12 slides
OSBELTCA Board Meeting - January 26, 2022 - Virtual Attendees Instructions
Virtual attendees of the OSBELTCA Board Meeting on January 26, 2022, are instructed to mute their microphones unless asked a direct question. The meeting will begin at 10:00 AM and will be recorded. The agenda includes various items such as Call to Order, Welcoming Remarks, Administering the Oath of
0 views • 15 slides
Guide to Effective Communication Skills for Virtual Meetings
Developing strong communication skills for virtual meetings is crucial for effective collaboration and productivity. Key tips include maintaining eye contact, active listening, and concise messaging. Overcome the challenges of virtual communication by utilizing proper etiquette and engaging particip
0 views • 6 slides
Understanding Virtual Memory Concepts and Benefits
Virtual Memory, instructed by Shmuel Wimer, separates logical memory from physical memory, enabling efficient utilization of memory resources. By using virtual memory, programs can run partially in memory, reducing constraints imposed by physical memory limitations. This also enhances CPU utilizatio
0 views • 41 slides
Understanding Virtual Worlds and Virtual Property
A virtual world is a computer-moderated environment separate from the physical world, enabling multiple individuals to interact simultaneously. Virtual property refers to objects within these worlds, having economic or sentimental value and deserving legal protection. Virtual crimes like theft occur
0 views • 9 slides
Automating Security Operations Using Phantom
Isabella Minca, an intern for 4 months in the Security Team at Adobe, presents an overview of automating security operations using Phantom. The presentation covers goals, security alerts, Phantom playbooks, handling security data, and the capabilities of Phantom in orchestrating security responses.
0 views • 28 slides
Smart Virtual Store Software Graduation Project Overview
Smart Virtual Store Software is a project developed in 2012 by Yaman A., Salman E., and Eman M. to simplify shopping through a virtual store concept. The project includes a QR code generator, QR reader, mobile application, server communication, and a website for easy ordering and purchasing of produ
0 views • 33 slides
Virtual Network Mapping: A Graph Pattern Matching Approach
Virtual Network Mapping (VNM) involves deploying virtual network requests in data center networks in response to real-time demands. It facilitates the deployment of virtual networks on physical machines by mapping virtual nodes and links onto substrate nodes and paths, ensuring constraints are met.
0 views • 15 slides
Exploring Virtual Environments in Computing: An Overview
Virtual environments in computing encompass a range of technologies, from virtual memory to virtual machines and virtual execution environments. These environments allow software to run in a different setting than originally designed, minimizing complexities. Key components include virtual memory, m
0 views • 26 slides
Leveraging Social Media for Freemasonry Communication in West Lancashire
In response to the suspension of physical lodge meetings, Freemasonry in West Lancashire is utilizing social media platforms like Zoom, WhatsApp, and Skype for virtual communication. Although virtual meetings cannot replace regular gatherings, they help maintain fraternal relationships, conduct rehe
0 views • 7 slides
Maximize Virtual Learning with Maalinyai.Cloud.School
Dive into the world of cloud-based education with Maalinyai.Cloud.School. Explore the concept of learning in the cloud, virtual classrooms, and essential tips for virtual lessons. Discover how to make the most of online learning platforms like Zoom, engage students effectively, and create an interac
0 views • 12 slides
Understanding HTTP Security Headers for Web Apps
Explore the importance of HTTP security headers on web applications through a detailed breakdown of headers like HSTS, XFO, XSS, CSP, CTO, RH, and FP. Learn how these headers enhance security by instructing browsers on handling website content, preventing various attacks. Gain insights on configurin
0 views • 68 slides
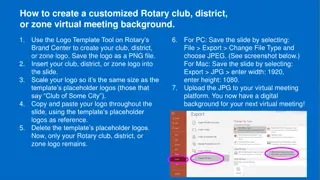
How to Create a Customized Rotary Club Virtual Meeting Background
Learn how to design a personalized Rotary club, district, or zone virtual meeting background using a step-by-step process. Save the logo template as a PNG file, insert it into the slide, and scale it to fit. Customize your virtual meeting background for a professional touch.
0 views • 9 slides
Virtual Meeting Security Best Practices
Ensure the security of your virtual meetings by following best practices to mitigate threats like teleconference hijacking. Consider tools like Zoom, Skype, Webex, and others to host secure meetings. Avoid making meetings public, manage screen-sharing options, use waiting rooms, validate participant
0 views • 23 slides
Understanding Linux Virtual Memory Management
The memory management subsystem in Linux ensures fair physical memory allocation for running processes, allowing them to share virtual memory when needed. Processes can have separate virtual address spaces or share memory through mechanisms like Unix System V shared memory IPC. Linux uses an abstrac
0 views • 230 slides
Stockton Unified School District SSC and ELAC Virtual Meeting Guidance for SY 2020-2021
Guidance for Stockton Unified School District SSC and ELAC virtual meetings includes protocols for meeting notices, planning steps, and preparation tips for virtual meetings. Emphasis on posting meeting notices, using mass notification systems, obtaining consensus for virtual meetings, and ensuring
0 views • 6 slides
Comprehensive Framework for Virtual Memory Research - Virtuoso
Virtuoso is an open-source, modular simulation framework designed for virtual memory research. The framework aims to address performance overheads caused by virtual memory by proposing solutions like improving the TLB subsystem, employing large pages, leveraging contiguity, rethinking page tables, r
0 views • 29 slides
Modular Security Analysis for Key Exchange and Authentication Protocols
Explore the modular security analysis approach used to examine the security of key exchange and authentication protocols, focusing on the universally composable authentication with a global Public Key Infrastructure. The analysis involves splitting the system into smaller components, separately anal
0 views • 15 slides
Revolutionizing Security Testing with BDD-Security
Explore the innovative approach of Continuous and Visible Security Testing with BDD-Security by Stephen de Vries. Gain insights into how security testing can be integrated seamlessly into modern development practices, shifting the focus from reactive to proactive measures. Learn about the importance
0 views • 33 slides
Comprehensive DevOps Security Training Overview
This Certified DevOps Security Practitioner course provides a deep dive into implementing DevSecOps, integrating security into the DevOps processes. Covering topics like security testing, Docker security, automation, and more, the training aims to equip participants with the necessary skills to embe
0 views • 5 slides
Understanding Security Testing and Architecture
Explore the fundamentals of security testing, computer security goals, software security approach, and security architecture. Learn about securing computer assets, verifying trustworthiness of security mechanisms, and validating security architecture through threat modeling. Enhance your knowledge o
0 views • 57 slides