Understanding the Role of Security Champions in Organizations
Security Champions play a vital role in decision-making concerning security engagement, acting as a core element in security assurance processes within a team. They foster a security culture, reduce dependency on the CISO, and promote responsible autonomy and continuous security education in the org
3 views • 13 slides
Matrimonial Profiles - Seeking Companionship in Diverse Backgrounds
Explore a diverse range of matrimonial profiles featuring individuals of different Hindu backgrounds and citizenships, all seeking compatible partners. From medical professionals to teachers, these profiles showcase individuals with varied interests and aspirations for a happy union. Discover potent
1 views • 29 slides
Roughtime: Securing time for IoT devices
Accurate time is crucial for security protocols like DNSSEC and TLS in IoT devices. Roughtime protocol, with improved accuracy and security features, provides a solution for securing time in resource-constrained environments. The protocol addresses the bootstrapping problem and allows for microsecon
1 views • 8 slides
Colorado State Epidemiological Profiles - Substance Abuse Trends & Response Task Force
The Colorado State Epidemiological Profiles provide a state-level overview of data from various surveillance sources for prevention, intervention planning, monitoring, and evaluation. The profiles cover demographics, alcohol, marijuana, opioids, sustainability, and next steps. Updated every 2 years,
0 views • 12 slides
Understanding Epidemiological Profiles in Public Health Practice
Epidemiological profiles play a crucial role in substance abuse and mental health planning, helping professionals prioritize issues and raise awareness. The profiles include quantitative and qualitative data to analyze behavioral risk factors, consumption patterns, and clinical outcomes, sourced fro
1 views • 13 slides
Efficient Staffing Strategies for Nursing Units
Implementing effective staffing templates, self-scheduling options, and allowable overstaffing on specialized profiles can enhance data reporting accuracy and ensure adequate nurse coverage. Additional tips for accurate staffing numbers include adjusting profiles, managing floaters, and handling sta
0 views • 5 slides
Understanding PeopleSoft Security: A Comprehensive Guide
Explore the intricacies of PeopleSoft security, including user profiles, roles, permission lists, and the importance of business process-based role design. Discover how security safeguards Personally Identifiable Information (PII) data, the significance of ZC/ZZ/ZD roles, and the role of SACR securi
4 views • 41 slides
Understanding the Roles of a Security Partner
Learn about the roles and responsibilities of a Security Partner, including requesting changes to security roles, approving security requests, and initiating access requests. Explore the overview of Workday Security, the security access request process, and the pre-request process flow. Discover how
1 views • 17 slides
Utilizing PARE Platform for Student Placements in Leeds
The PARE platform is a cloud-based system used in Leeds for managing student placements. Practice Supervisors, Assessors, and Educators play key roles in supporting students through PARE by maintaining profiles, accessing training, and ensuring accurate records. Practice Education Leads are responsi
0 views • 8 slides
Enhancing Eduroam Security with New Standards and Practices
Explore the foundations of eduroam and the challenges with RADIUS, along with recommendations for improving security. Learn why moving away from RADIUS/UDP and adopting shared secrets of 16 characters is essential. Discover the issues with transitioning from UDP to RADIUS/TLS, and the new standards
0 views • 12 slides
Modernizing Network Security with nQUIC Noise-Based Packet Protection
Explore the evolution of network security mechanisms through nQUIC Noise protocol, comparing it against traditional HTTPS stack. Delve into the secure transmission aspects of TCP/IP, TLS, and the innovative approaches of QUIC protocol, emphasizing the significance of securing protocols with TLS in m
2 views • 119 slides
Comprehensive Overview of EAL Profiles and Strategies for Language Skills Assessment
EAL Profiles offer a versatile tool for assessing pupils' language skills and setting targets. They can replace Form 1 documents, aid in transition planning, update progress profiles, and inform teaching strategies. These profiles include sections for pupil information, progress overview, review tab
0 views • 10 slides
Understanding TLS v1.3: Enhancing Round-Trip Times and SSL Configuration
Delve into the intricacies of TLS v1.3 updates, exploring the significance of round-trip times in pre-TLS v1.3, the integration of 0-RTT and 1-RTT in TLS v1.3. Discover key configurations like SSL_CTX_set_max_early_data and SSL_CTX_set_options, as well as the implementation nuances in SSL.
1 views • 13 slides
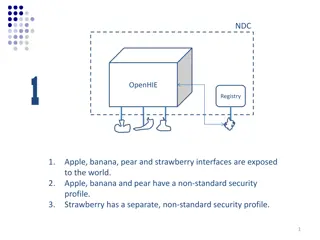
Comparison of Security Profiles in OpenHIE Registries
OpenHIE exposes interfaces with varying security profiles - non-standard in Scenario 1, standards-based in Scenarios 2 and 3. Scenario 1 requires managing multiple non-standard profiles, whereas Scenarios 2 and 3 facilitate plug-and-play with standard security protocols. Implications include ease of
4 views • 6 slides
Understanding Transport Layer Security (TLS)
The lecture discusses key security properties essential for secure communication in computer networks, such as confidentiality, integrity, authentication, and non-repudiation. It elaborates on cryptographic mechanisms for achieving these properties and emphasizes modularity and reusability in implem
1 views • 26 slides
Enhancing Security with Hardware Attestation in TLS
The hardware attestation in TLS presentation explores the theory and practice of remote attestation, emphasizing the need to improve workload authentication beyond software-bound trust. It delves into the use cases, remote attestation data flow, and the significance of Transport Layer Security (TLS)
0 views • 29 slides
Understanding Soil Profiles in Agricultural Science
Soil profiles are essential for classifying soils, with main profiles being Brown Earth, Podzol, and Gley. It's crucial to draw these profiles accurately for exams, considering horizons like O Horizon, A Horizon, B Horizon, and Bedrock. Brown Earth has a thick O horizon with uniform brown color, Pod
1 views • 8 slides
A New Approach to TLS Inspection
This article explores a new approach called IA2-TLS for inspecting Transport Layer Security (TLS) anytime and anywhere. It discusses the primary goals of TLS, the increasing importance of data encryption over networks, and the need for TLS inspection to enhance security controls. The challenges of i
1 views • 46 slides
Exploring DANE, DNSSEC, and TLS in Go6Lab
Delve into the implementation of DANE, DNSSEC, and TLS protocols at Go6Lab, a testing facility affiliated with ISOC/Go6 Institute in Slovenia. The setup includes DNSSEC implementation with PowerDNS and OpenDNSSEC, DANE experimentation with Postfix servers, and verification processes for TLS certific
0 views • 36 slides
Efficient User Management System for Health Facilities
Record and manage user details effectively with the new Version 2.0 User Management feature. RNTCP has now registered over 35,000 PHIs, 140,000 Private Health Facilities, 15,000 Private Labs, 31,000 Private Chemists, across 700 Districts and 8,000 TUs in Nikshay. Enhance operations by editing TU pro
0 views • 26 slides
Learn about Rainforest Animals and Create Animal Profiles
In this activity, students will explore the characteristics of animals found in the rainforest such as the parrot, leopard, orangutan, toucan, and more. They will create animal profiles with their partner using German sentences. The profiles will include information on the animals' body parts, respi
0 views • 10 slides
EPA Oil and Gas VOC Speciation Improvement Efforts
EPA's VOC Speciation transforms inventory species into Air Quality model species to support chemistry, ozone, and aerosol chemistry. The Speciate4.5 update in 2016 added oil and gas profiles, including location-specific uncontrolled profiles and WRAP profiles for various basins. The Uinta TMSR profi
2 views • 10 slides
Understanding TLS/SSL: Security, Attacks, and TLS 1.3
Learn about the world of TLS/SSL security, attacks, and the latest TLS 1.3 protocol. Explore how TLS ensures confidentiality and authenticity of communications, the client-server scenario in online shopping, a bit of history from SSL to TLS, and insights into different TLS versions and their securit
0 views • 37 slides
Understanding Transport Layer Security (TLS) and Secure Sockets Layer (SSL)
This content delves into the concepts of Transport Layer Security (TLS) and Secure Sockets Layer (SSL), exploring their origins, application in web security, and protocol stack integration. It covers the TLS/SSL handshake process, key derivation, data transfer mechanisms, and the significance of the
0 views • 26 slides
TLS Freight Forwarding Pvt Ltd: Your Business Partner for Complete Logistics & Supply Chain Solutions
TLS Freight Forwarding Pvt Ltd is a leading third-party logistics service provider operational in major cities of Pakistan, offering logistics, supply chain, and brokerage services. With a mission to exceed customer expectations, TLS provides global reach, multi-modal services, IT solutions for real
0 views • 13 slides
Inspection Profiles of Largest Children's Homes Providers - August 2018
Explore the inspection profiles of the largest private and voluntary providers of children's homes as of August 2018. Gain insights into ownership and inspection outcomes of over 500 homes, highlighting key organizations and national comparisons. Dive into the varying inspection profiles and outcome
0 views • 5 slides
Understanding Wind Profiles and Aerodynamic Roughness Length
Wind profiles are crucial in understanding how wind speed changes with height in the boundary layer. The logarithmic and power law profiles depict this relationship, influenced by surface characteristics and obstacles. The aerodynamic roughness length, defining where wind speed becomes zero, remains
0 views • 14 slides
Evolution of Collisionless Plasma Bounded by Absorbing Walls
Study on the evolution of collisionless plasma between absorbing walls, analyzing rarefaction waves, density profiles, and plasma potential decay. Kinetic simulations reveal gas dynamics-like behavior with flat density profiles and linear velocity profiles leading to asymptotic decay. The influence
0 views • 15 slides
Understanding Traffic Light Profiles for Special Educational Provision
Traffic Light Profiles are tools used to support children with special educational needs by setting termly targets and strategies to help them reach their potential. These profiles are created in consultation with the SENDCO and class teacher, with a focus on addressing the child's needs and trackin
0 views • 6 slides
Network Security Course Overview - INFSCI 1075 by Amir Masoumzadeh
Network Security Course INFSCI 1075 by Amir Masoumzadeh focuses on security issues in networks, covering common attacks, prevention, detection, protocols like IPSec and SSL/TLS, cryptographic protocols, and more. The course prerequisites include knowledge of TCP/IP, algebra, digital logic, and basic
0 views • 16 slides
Evolution of TLS Security Profiles and Best Practices
TLS security profiles have evolved with the introduction of new profiles, retirement of old ones, and emphasis on non-downgrading best practices. Motivated by changes in security threats and cryptographic methods, the IETF has issued recommendations to ensure secure connections using TLS 1.2. The ne
0 views • 5 slides
Understanding Lawson Security: Basics, Hierarchy, and Administration Tools
This comprehensive guide covers essential aspects of Lawson Security, including an overview of security components, user roles, secured objects, and implementation methodology. Learn about the hierarchy structure, what can be secured, rules, and the tools available for security administrators and RM
0 views • 28 slides
REST Interface for HORUS.AI Platform - Tutorial Highlights
This tutorial delves into creating profiles and users using the ProfileManager service in the HORUS.AI platform. It covers steps like creating new profiles, adding users to profiles, and setting rules. The focus is on providing a REST interface for seamless interaction with the HORUS.AI system. The
0 views • 15 slides
Insights from Discussions with Admissions Officials on School Profiles, Grading Scales, and Admissions Criteria
Discussions with university officials shed light on the importance of school profiles, grading scale variations, and admissions criteria. Insights include the significance of school profiles, diversity in grading scales, and the role of NHS in the admissions process. Admissions offices consider fact
0 views • 25 slides
International Protection Needs Profiles in the Caribbean
Identified international protection needs profiles for asylum seekers in the Caribbean region, highlighting main countries of origin such as Cuba, Haiti, Jamaica, and Venezuela. Details include specific profiles and protection needs per country, along with recommended actions when encountering indiv
0 views • 10 slides
Colorado Epidemiological Profiles 2021 - Substance Use Data and Analysis
The 2021 Colorado Epidemiological Profiles provide in-depth data and analysis on substance use patterns, impacts, and demographics in Colorado. The profiles cover alcohol, marijuana, opioids, and tobacco, along with special considerations for populations like LGBTQ, veterans, tribal communities, unh
0 views • 19 slides
Weak Keys Detection in Network Devices
TLS and SSH rely on RSA and DSA for security, but weaknesses in random number generation can lead to widespread weak keys among hosts on the Internet. This paper uncovers the prevalence of repeated keys and easily inferred private keys, emphasizing the importance of entropy pools in key generation.
0 views • 28 slides
Comprehensive DevOps Security Training Overview
This Certified DevOps Security Practitioner course provides a deep dive into implementing DevSecOps, integrating security into the DevOps processes. Covering topics like security testing, Docker security, automation, and more, the training aims to equip participants with the necessary skills to embe
0 views • 5 slides
Creating User Profiles for Product or Service Development
Engage in an exercise outlined on page 130 to craft user profiles for a product or service using a partner, pen, paper, and internet resources. Follow the provided template to document your findings and focus on your design problem or the Designing Space Travel brief. Utilize existing data or genera
0 views • 10 slides
Benefits of Free SSL with Let's Encrypt for Website Security
Explore the advantages of implementing free SSL with Let's Encrypt for your website security needs. Discover why SSL/TLS encryption is essential to prevent insecure warnings in browsers, enhance search engine rankings, and comply with Apple's secure app requirements. Learn about the pain points asso
0 views • 25 slides