Conjunctive Searchable Symmetric Encryption From Hard Lattices
Discusses outsourcing storage and computing, encrypted data computing, and searchable symmetric encryption for data security in cloud environments. It touches on topics like data confidentiality, user revocation, and performance-oriented implementations.
2 views • 30 slides
Clean Heat Skills and Supply Chains
The Clean Heat Skills and Supply Chains initiative in Scotland aims to transition to clean heating systems by the end of 2045, focusing on energy efficiency improvements and statutory targets. The consultation seeks views on proposals to improve energy efficiency and end the use of polluting heating
0 views • 7 slides
Discover Your Signature Style at King Ice's Chains Store
Welcome to King Ice's chains store, your ultimate destination for stylish and statement-making chains. Whether you're searching for a classic Cuban link chain, a bold cross chain, or a unique Buddha chain, our store has everything you need to elevate your look and express your individuality. With a
8 views • 5 slides
Understanding Rotations and Kinematic Chains in Virtual Human Modeling
Exploring the concept of rotations in transformations and the use of kinematic chains in modeling human motion. Topics covered include kinematic parameterization, optimization of rigid body motions, and building virtual human models through kinematic chains. Understanding rotations as linear transfo
5 views • 78 slides
Shine Bright in Gold: Discover Our Gold Plated Chains
Elevate your style with the luxurious shine of our Gold Plated Chains collection. Crafted in gleaming gold and finished with impeccable detail, these chains add a touch of sophistication to any ensemble. Whether worn alone for a subtle glow or layered with other pieces for a bold statement, our Gold
3 views • 5 slides
Shine Bright with King Ice Gold Tennis Chains
Elevate your style with King Ice's Gold Tennis Chains, the ultimate symbol of sophistication and luxury. Crafted with precision and perfect for any occasion, these chains feature a sleek design that seamlessly blends classic elegance with modern allure. Whether you're looking to make a statement at
2 views • 5 slides
Key Management and Distribution Techniques in Cryptography
In the realm of cryptography, effective key management and distribution are crucial for secure data exchange. This involves methods such as symmetric key distribution using symmetric or asymmetric encryption, as well as the distribution of public keys. The process typically includes establishing uni
1 views • 27 slides
Understanding Matrices: Types, Definitions, and Operations
Matrices are ordered arrays used to express linear equations. Learn about types, definition, equality, and operations like addition, subtraction, and multiplication. Discover matrix equality and the transpose of a matrix, including symmetric and skew-symmetric matrices.
1 views • 17 slides
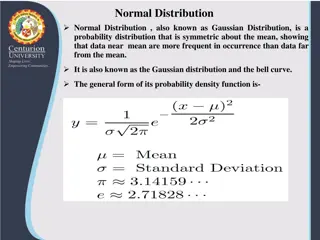
Understanding Normal Distribution and Its Business Applications
Normal distribution, also known as Gaussian distribution, is a symmetric probability distribution where data near the mean are more common. It is crucial in statistics as it fits various natural phenomena. This distribution is symmetric around the mean, with equal mean, median, and mode, and denser
1 views • 8 slides
Understanding Markov Chains and Their Applications in Networks
Andrej Markov and his contributions to the development of Markov chains are explored, highlighting the principles, algorithms, and rules associated with these probabilistic models. The concept of a Markov chain, where transitions between states depend only on the current state, is explained using we
19 views • 21 slides
Understanding Ecosystem Dynamics: The Food Web Explained
An ecosystem comprises various organisms living together in a community. Energy flow through food chains depicts how organisms obtain energy and nutrients from one another. Food chains show the sequence of feeding relationships, while a food web illustrates interconnected chains within a community.
1 views • 13 slides
Understanding the Intricacies of Food Chains in Ecosystems
Food chains play a crucial role in the transfer of energy within ecosystems. They consist of various trophic levels where organisms either consume or are consumed by others. Different types of food chains like grazing, detritus, predator, and parasitic chains interact to maintain the balance of ener
0 views • 15 slides
Understanding Food Chains, Trophic Levels, and Biomass Pyramids on Rangelands
Explore the intricate dynamics of food chains, trophic levels, and biomass pyramids on rangelands through informative visuals and explanations. Learn how energy flows through different levels, the concept of biomass pyramids, and the impact of vegetarianism on food chains and energy efficiency.
0 views • 11 slides
Exploring Ecosystem Dynamics: Food Chains, Energy Pyramids, and Trophic Levels
An exploration of key concepts in ecosystem dynamics, including food chains, energy pyramids, secondary consumers, and trophic levels. Discover the interconnected relationships between organisms in an ecosystem and the vital role of key species. Dive into the differences between food chains and food
0 views • 16 slides
Quantum Query Complexity Measures for Symmetric Functions
Explore the relationships between query complexity measures, including quantum query complexity, adversary bounds, and spectral sensitivity, in the context of symmetric functions. Analysis includes sensitivity graphs, the quantum query model, and approximate counting methods. Results cover spectral
0 views • 19 slides
Understanding Symmetric Key Block Ciphers - Overview and Implementation
Delve into the world of symmetric key block ciphers through a detailed exploration of classical ciphers like substitution and transposition, modern cryptography advancements, DES encryption, Simplified DES, key scheduling, expansion functions, S-Box usage, and more. Discover the intricacies of encry
0 views • 40 slides
Simplified Linear Transformation for N Application Rates in Corn and Wheat
Dr. Brenda Ortiz and Dr. Bill Raun led an investigation on predicting grain yield using optical sensors in corn and wheat. The challenges with the symmetric sigmoid model for yield prediction led to the development of a simplified linear transformation approach. Assumptions were made to create a mod
0 views • 28 slides
Understanding Eigenvalues in Quantum Information
Explore the eigenvalues of sums of non-commuting random symmetric matrices in the context of quantum information. Delve into the complexities of eigenvalue distributions in various scenarios, including random diagonals, orthogonal matrices, and symmetric matrix sums. Gain insights into classical and
0 views • 24 slides
Understanding Habitats, Adaptations, and Food Chains in Ecosystems
Explore the concepts of habitats, adaptations, and food chains in ecosystems. Learn how different environments support diverse organisms, how adaptations aid survival, the impact of competition for resources, and the flow of matter and energy through food chains. Discover the interdependence of plan
0 views • 51 slides
Development of Quantum Statistics in Quantum Mechanics
The development of quantum statistics plays a crucial role in understanding systems with a large number of identical particles. Symmetric and anti-symmetric wave functions are key concepts in quantum statistics, leading to the formulation of Bose-Einstein Statistics for bosons and Fermi-Dirac Statis
1 views • 15 slides
Understanding Hash Joins and Symmetric Hash Joins in Database Queries
Hash joins and symmetric hash joins are key techniques used in database queries to efficiently access and combine data from multiple tables. Hash joins load candidate records into hash tables for quick probing, while symmetric hash joins maintain two hash tables with two hash functions. Despite thei
0 views • 8 slides
Key Distribution and Management in Cryptography
This presentation discusses key distribution and management in cryptography, covering symmetric and asymmetric key cryptography, methods for sharing symmetric and public keys, as well as key distribution techniques such as manual delivery, initial key distributions, and the use of trusted third part
0 views • 30 slides
Advanced Techniques in Online and Bandit Algorithms Beyond Norms
Delve into the realm of online and bandit algorithms beyond traditional norms as discussed by Sahil Singla from Georgia Tech in collaboration with Thomas Kesselheim and Marco Molinaro. The presentation explores the design and optimization of algorithms for online settings, shedding light on load bal
0 views • 21 slides
Enhancing Pig Value Chains Through Innovation and Intervention
Conduct research to identify innovative solutions in gender, nutrition, environmental sustainability, and value chain upgrading/transformation. Utilize systems analysis to design integrated intervention packages for pig value chains. Learn from outcomes to adapt operations and activities, focusing o
0 views • 10 slides
Exploring Global Food Chains for 7-11 Year Olds
Embark on an educational journey delving into the complexities of global food supply chains through engaging slideshows and thought-provoking discussions. Understand the stages food products undergo from cultivation to consumption, ponder over fairness in supply chains, and even simulate the movemen
0 views • 15 slides
CO2 Emissions and Global Value Chains: Trends in Decoupling and Regional Impacts
The discussion focuses on the relationship between CO2 emissions and Global Value Chains (GVCs) from 1990 to 2015, exploring how GVC participation can aid in decoupling. It covers the environmental implications of GVCs, such as the effects on CO2 footprints, trade patterns, and emission intensities
0 views • 19 slides
Understanding Cryptography Basics and Toolbox
Cryptography serves the goals of managing who can view data, ensuring data integrity, and verifying the origin of data. It involves dramatis personae like Alice, Bob, Eve, and Oscar. The toolbox includes hash functions, symmetric encryption, and asymmetric encryption. Hash functions play a crucial r
0 views • 32 slides
Symmetric Chromatic Function for Voltage Graphs
Exploring the concept of a Symmetric Chromatic Function (SCF) for voltage graphs involves proper coloring conditions for edges and vertices, edge polarization functions, and decomposing voltage graphs into disconnected and connected squiggly graphs. The SCF allows for determining the number of ways
0 views • 7 slides
Understanding Construct Chains in Hebrew: A Visual Guide
Explore the concept of construct chains in Hebrew grammar through visual examples and explanations. Learn how to identify, read, and create construct chains using nouns and the word "of." Discover the importance of definite and indefinite status in construct chains with relevant biblical examples. C
0 views • 16 slides
Understanding Trade in Value-Added (TiVA) and Global Value Chains
Trade in Value-Added (TiVA) offers crucial insights into the complexities of global value chains and economic globalization. By shifting focus from gross trade statistics to value creation along supply chains, TiVA helps in formulating better policies and addressing systemic risks associated with ma
0 views • 22 slides
Nonstationary Configurations of a Spherically Symmetric Scalar Field
Action and stress-energy tensor, Einstein-Klein-Gordon equations, and method for constructing nonstationary configurations of a spherically symmetric scalar field are discussed in this study. The behavior of the characteristic function allows interpretations such as black holes, wormholes, or naked
0 views • 14 slides
Understanding Markov Chains and Applications
Markov chains are models used to describe the transition between states in a process, where the future state depends only on the current state. The concept was pioneered by Russian mathematician Andrey Markov and has applications in various fields such as weather forecasting, finance, and biology. T
1 views • 17 slides
Exploring Symmetric Chains and Hamilton Cycles in Graph Theory
Delve into the study of symmetric chains, Hamilton cycles, and Boolean lattices in graph theory. Discover the relationships between chain decompositions, Boolean lattices, and edge-disjoint symmetric chain decompositions, exploring construction methods and properties such as orthogonality. Uncover t
0 views • 15 slides
Understanding Cryptography and Symmetric Keys in Digital Communication
Cryptography, a vital part of digital communication, involves safeguarding messages from adversaries like eavesdroppers and impostors. Initially reliant on symmetric keys for encryption and decryption, the need to securely share keys posed a challenge. Technologies like DES and AES have advanced cry
0 views • 55 slides
Latest Update from Higgs Working Group Meeting - September 10th, 2010
Discussion highlights from the Higgs Working Group Meeting on September 10th, 2010, include menu approvals for data taking, introduction of new chains, issues with presampler noise affecting trigger rates, validation of jet chains, and optimization of tau chains. Updates on beam conditions, luminosi
1 views • 11 slides
Understanding Histogram Shapes and Distribution Patterns in Statistics
Explore the shapes of histograms and distribution patterns, including symmetric, skewed, bimodal, and uniform distributions. Learn to identify variables that are likely to be uniformly distributed, skewed right, skewed left, or symmetric in real-world data sets. Gain insights into key concepts like
0 views • 55 slides
Analysis of Symmetric Concrete Dam With and Without Sheet Pile
This analysis focuses on a symmetric concrete dam with and without a sheet pile, examining factors such as total pore water pressure, excess pore pressure, seepage velocities, and flow rates. By comparing scenarios with and without a sheet pile, insights into flow rate reductions and discharge varia
0 views • 13 slides
Reflecting on the Grace and Redemption in "Amazing Grace (My Chains are Gone)
Explore the profound message of redemption and freedom conveyed in the hymn "Amazing Grace (My Chains are Gone)", reflecting on the journey from being lost to being found, from blindness to sight, and from chains to freedom through the unending love and mercy of God.
0 views • 19 slides
Protecting Password Identifiers in IEEE 802.11-21
This submission addresses the need for safeguarding password identifiers in SAE to ensure privacy and prevent attackers from constructing personally identifiable information. The document presents two potential solutions, ultimately recommending the use of symmetric cryptography for efficient protec
0 views • 11 slides
Establishing Regional Value Chains in the Post-Epidemic Era: Opportunities for the Greater Tumen Region
Recent events, including escalating tensions between the US and China and the impact of COVID-19, have led multinational enterprises to seek new production centers. The Greater Tumen Region, encompassing Jilin, is positioned to become a key global production center with established regional value ch
0 views • 15 slides