Addressing 5G Signaling Protocol Vulnerabilities
The 8th meeting of the Communications Security, Reliability, and Interoperability Council to discuss and address security vulnerabilities in the newly adopted 5G signaling protocol, HTTP/2. Learn about potential risks, recommended safeguards, and the prevention of these vulnerabilities in the upcomi
3 views • 85 slides
In-Depth Look at Breaking HTTP Servers, Proxies, and Load Balancers
Explore the world of disrupting HTTP technology with authors Ben Kallus and Prashant Anantharaman. Delve into vulnerabilities, DARPA-funded projects, and the interesting exploits in HTTP implementations. Witness the journey that involves discovering multiple vulnerabilities, receiving grants for res
2 views • 51 slides
Understanding Malicious Attacks, Threats, and Vulnerabilities in IT Security
Malicious attacks, threats, and vulnerabilities in IT systems pose significant risks and damages. This chapter explores the types of attacks, tools used, security breaches, and measures to protect against cyber threats. Learn how security professionals safeguard organizations from malicious attacks
0 views • 24 slides
Innovations and Vulnerabilities in ISO/IEC 18013 mDL Standard
Explore innovations and vulnerabilities in the ISO/IEC 18013 mDL (mobile Driver's License) standard in this presentation by Francisco Corella. Covering architecture, data elements, authentication methods, security innovations, and privacy goals, the talk delves into the nuances of mDL technology and
3 views • 42 slides
Understanding Complex Needs of Children in Justice System
Children with complex needs in the justice system often face high risks and vulnerabilities due to experiences such as adverse childhood events and trauma. This cohort of children has unmet, multi-layered needs and struggles with social disadvantages, secure attachments, and accessing timely service
0 views • 18 slides
Self-Supervised Learning of Pretext-Invariant Representations
This presentation discusses a novel approach in self-supervised learning (SSL) called Pretext-Invariant Representations Learning (PIRL). Traditional SSL methods yield covariant representations, but PIRL aims to learn invariant representations using pretext tasks that make representations similar for
0 views • 8 slides
How to Resolve QuickBooks Payroll Error Code 15223_ A Comprehensive Guide
Struggling with QuickBooks Payroll Error Code 15223? This guide provides a step-by-step approach to resolve it efficiently. Start by ensuring your QuickBooks software is updated to the latest version. Check your Internet Explorer settings, ensuring both SSL 2.0 and SSL 3.0 are enabled. Clear tempora
1 views • 5 slides
Understanding Vulnerabilities of Individuals with Autism in Disciplinary Hearings and Employment Tribunals
People with autism may face vulnerabilities in disciplinary proceedings and employment tribunals due to impaired theory of mind, communication difficulties, insistence on sameness, stereotyped behaviors, and sensory sensitivities. These challenges can lead to misunderstandings, difficulties in copin
0 views • 10 slides
Leveraging Artifact Dependency Graphs for Software Vulnerability Detection
Explore how LLVM-GitBOM utilizes artifact dependency graphs to detect vulnerabilities in software dependencies. The presentation covers the overview of GitBOM, CVE detection, supply chain vulnerabilities, and the importance of precise build tools in vulnerability scanning. Learn about utilizing gito
0 views • 34 slides
Understanding Global Economic Convergence Trends: Insights from Jeffrey Frankel’s Keynote at G20 Global Financial Stability Conference 2021
Jeffrey Frankel discussed the potential impact of the pandemic on global economic convergence at the G20 Global Financial Stability Conference 2021. Despite a resilient world economy in the first half of 2021, downside risks persist due to monetary and fiscal stimuli. The divergence between Emerging
1 views • 17 slides
Impact of COVID-19 on Older Adults: Vulnerabilities and Management
Older adults face higher risks from COVID-19, with individuals aged 65+ and 85+ suffering the most severe outcomes. Vulnerabilities in aging immune systems and unique transmission characteristics contribute to the pandemic's spread. Recognizing clinical symptoms and signs early is crucial for managi
0 views • 13 slides
HotFuzz: Discovering Algorithmic Denial-of-Service Vulnerabilities
A detailed exploration of algorithmic complexity bugs and insight into distributed micro-fuzzing methods. The study uncovers vulnerabilities through guided micro-fuzzing approaches, emphasizing the importance of AC bug detection and fuzz testing techniques such as seed inputs, fuzz observations, and
0 views • 14 slides
Understanding TLS v1.3: Enhancing Round-Trip Times and SSL Configuration
Delve into the intricacies of TLS v1.3 updates, exploring the significance of round-trip times in pre-TLS v1.3, the integration of 0-RTT and 1-RTT in TLS v1.3. Discover key configurations like SSL_CTX_set_max_early_data and SSL_CTX_set_options, as well as the implementation nuances in SSL.
1 views • 13 slides
Addressing Mental Health Challenges in Older Adults
Understanding the mental health challenges faced by older adults is crucial as they navigate through different stages of aging. Issues, vulnerabilities, and risk factors associated with aging can impact their well-being. From age-related vulnerabilities to under-identified and under-treated conditio
4 views • 36 slides
SSL for Local Development: Tools and Techniques
Understanding the importance of using SSL in local development, this article discusses reasons for SSL usage, setting up localhost and self-signed CAs, and tools like mkcert and Caddy to facilitate the process. It highlights the benefits and potential drawbacks of each tool, offering insights on imp
0 views • 9 slides
Exploring Web Application Vulnerabilities and JavaScript Worms
Web applications face pervasive vulnerabilities, with Cross-site Scripting (XSS) leading the threats. The domination of XSS and buffer overruns has enabled the propagation of JavaScript worms, exemplified by infamous cases like Samy's MySpace outbreak. These exploits, marked by obfuscation and polym
1 views • 20 slides
Understanding Buffer Overflow Vulnerabilities in Programming
Buffer overflow vulnerabilities pose serious security threats by allowing attackers to execute arbitrary code on victim machines. This issue arises from overwriting memory in a way that manipulates the program's behavior. Learn about the dangers of buffer overflow bugs, how they can be exploited, an
2 views • 33 slides
Software Security Principles and Practices: Enhancing Program Code Security
Understanding and addressing critical web application security flaws like unvalidated input, cross-site scripting, buffer overflow, injection flaws, and improper error handling is crucial in enhancing the security of program code. The NIST report NISTIR 8151 provides valuable recommendations to redu
2 views • 44 slides
Understanding Computer Security and Software Vulnerabilities
Computer security, also known as cybersecurity or IT security, encompasses the protection of information systems from theft and damage. This overview delves into software security, control-flow attacks, memory vulnerabilities, and the historical impact of events like the Morris Worm. Various aspects
0 views • 53 slides
Overview of Global Farmed Salmon and Organic Production
The data showcases the production figures for global farmed salmon across various countries, with Norway leading the production, followed by Chile, Scotland, and others. Additionally, insights into the growing organic salmon production, vulnerabilities in the sector, and details on organic mussels p
0 views • 9 slides
Analysis of file:// Vulnerabilities in Android Browser Apps
The study delves into file:// vulnerabilities in Android browser apps, uncovering risks posed by the file:// URI scheme. It highlights how file:// requests can breach app data isolation, potentially compromising sensitive files. The research presents a unified attack model, FileCross automated testi
0 views • 22 slides
Automated Detection of SSL Vulnerabilities in Applications
This research introduces SSLint, a systematic approach and automated tool for detecting incorrect SSL API usage vulnerabilities in applications. By analyzing millions of lines of code, the tool discovered previously unknown SSL/TLS vulnerable apps. The study addresses the motivation, problem stateme
0 views • 29 slides
Server-Side Technologies and Security Vulnerabilities in Mobile Services
This content delves into server-side technologies such as SQL, SOAP, JSON, and ReST used in mobile services, highlighting vulnerabilities that expose sensitive data. It emphasizes the importance of general web service security guidelines and discusses attacks against XML-based web services, outlinin
0 views • 52 slides
Understanding Blockchain Vulnerabilities to Quantum Attacks
Explore the vulnerabilities of blockchains to quantum attacks and the potential impact of quantum devices on blockchain technologies. Learn about key concepts such as blockchain basics, proof-of-work, quantum computing, quantum computing algorithms, and vulnerabilities like ECDSA and peer-to-peer ne
0 views • 23 slides
Understanding TLS/SSL: Security, Attacks, and TLS 1.3
Learn about the world of TLS/SSL security, attacks, and the latest TLS 1.3 protocol. Explore how TLS ensures confidentiality and authenticity of communications, the client-server scenario in online shopping, a bit of history from SSL to TLS, and insights into different TLS versions and their securit
0 views • 37 slides
Understanding Security Threats and Vulnerabilities in Computer Systems
In computer security, threats exploit vulnerabilities to breach security and cause harm. Vulnerabilities arise from system weaknesses, attacker access, and capability. Threats include spoofing, data tampering, repudiation, information disclosure, denial of service, and elevation of privilege. Catego
0 views • 13 slides
Understanding Authentication Mechanisms and Security Vulnerabilities
Authentication lies at the core of application security, serving as the primary defense against malicious attacks. This article explores various authentication technologies, including HTML forms-based authentication, multi-factor mechanisms, client SSL certificates, and more. It delves into common d
0 views • 70 slides
Understanding Transport Layer Security (TLS) and Secure Sockets Layer (SSL)
This content delves into the concepts of Transport Layer Security (TLS) and Secure Sockets Layer (SSL), exploring their origins, application in web security, and protocol stack integration. It covers the TLS/SSL handshake process, key derivation, data transfer mechanisms, and the significance of the
0 views • 26 slides
Understanding the Importance of OWASP Dependency-Check Project
Explore the significance of OWASP Dependency-Check in managing software dependencies and mitigating known vulnerabilities in applications. Learn about the risks associated with using components with vulnerabilities and the challenges of patching programs. Discover how OWASP Dependency-Check provides
1 views • 26 slides
Data Disaggregation Taskforce: Assessment and Recommendations on Vulnerabilities
The Data Disaggregation Taskforce is conducting an assessment of current practices across sectors, assessing 10 sectors/clusters, 15 categories of affected populations, and identifying vulnerabilities in 17 categories. The Taskforce is working on harmonizing categories and finalizing recommendations
0 views • 6 slides
Understanding Spectre and Meltdown Security Vulnerabilities
Spectre and Meltdown are two critical security vulnerabilities that exploit microarchitectural features to gain unauthorized access to memory. These vulnerabilities enable attackers to read memory that should be inaccessible, targeting branch prediction and exception handling mechanisms. Side channe
0 views • 19 slides
Understanding Cloud Security Threats and Vulnerabilities
Explore the world of cloud security through the eyes of Dr. Liang Zhao, focusing on mobile security, WLAN security, and cloud threats. Learn about threat modeling, mitigating cloud vulnerabilities, and common threats such as data leakage, insecure interfaces, and more. Discover practical threat anal
0 views • 18 slides
Understanding Network Security Vulnerabilities and Attacks
Explore the world of network security vulnerabilities and attacks, including Denial-of-Service (DoS) and Distributed-Denial-of-Service (D-DoS), security flaws in the TCP/IP protocol suite, ICMP attacks, routing attacks, and TCP attacks. Learn about common security vulnerabilities such as address spo
0 views • 36 slides
Understanding Web Application Vulnerabilities in Information Warfare
Web application vulnerabilities such as Cross-Site Scripting, SQL Injection, and Broken Authentication pose significant risks in information warfare. Current solutions include Black-Box Security Testing and XSS Analyzers, but they have limitations like static verification and dependence on security
0 views • 21 slides
Understanding Programming Language Vulnerabilities and ISO/IEC/SC22/WG23
Explore the history and evolution of ISO/IEC/SC22/WG23 focusing on programming language vulnerabilities, led by Stephen Michell. Learn about the formation in 2006, publications, identified vulnerabilities, and the upcoming Edition 3 outlook with language-specific annexes. Discover comparisons with A
0 views • 15 slides
Basic Web Security Model for Secure Electronic Commerce
This presentation covers the basic web security model for secure electronic commerce, focusing on vulnerabilities such as XSS and SQL injection. It discusses the decline in web vulnerabilities since 2009 and explores reported web vulnerabilities. The course theme includes topics like web application
0 views • 38 slides
Understanding Spectre and Meltdown Security Flaws
Recent security vulnerabilities named Spectre and Meltdown have surfaced in the realm of computer architecture and hardware implementation. These flaws allow attackers to access sensitive data through covert channels utilizing speculative execution mechanisms. The vulnerabilities exploit the perform
0 views • 12 slides
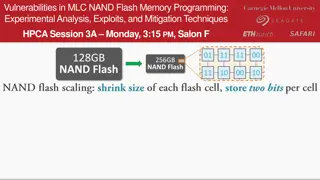
Experimental Analysis of Vulnerabilities in MLC NAND Flash Memory Programming
This session at HPCA explores the experimental analysis, exploits, and mitigation techniques related to vulnerabilities in MLC NAND flash memory programming. The presentation delves into the risks associated with NAND flash memory, such as data corruption and errors during read operations. It discus
0 views • 10 slides
Benefits of Free SSL with Let's Encrypt for Website Security
Explore the advantages of implementing free SSL with Let's Encrypt for your website security needs. Discover why SSL/TLS encryption is essential to prevent insecure warnings in browsers, enhance search engine rankings, and comply with Apple's secure app requirements. Learn about the pain points asso
0 views • 25 slides
Boosting Image Quality Assessment through Semi-Supervised and Positive-Unlabeled Learning
Incorporating Semi-Supervised and Positive-Unlabeled Learning methods enhances full-reference image quality assessment using less expensive unlabeled data and exclusion of negative samples. The framework involves PU learning with CE and NE losses, as well as SSL with MSE loss for labeled data and ps
0 views • 13 slides