How to Protect Your On-Demand App from Cyberattacks and Data Breaches
On-demand app development solutions provide convenient services but also carry cybersecurity risks like hacking, malware, and data breaches. This comprehensive guide explores best practices to secure on-demand apps and protect sensitive user data. Learn how encryption, multifactor authentication, ac
0 views • 4 slides
Phishing and Social Media Scam Protection | Scam Killnet Switch
The best online parental control tool is Scam Killnet Switch; protect your family against phishing and social media scams. Watch out for your family members while they play around on the internet. Your online interactions are kept safe by our cutting-edge technology, which recognises and stops harmf
3 views • 2 slides
Overcoming the UX Challenges Faced by FIDO Credentials in the Faced by FIDO Credentials in the Consumer Space
Many websites are vulnerable to phishing attacks due to traditional authentication methods. To address this, the utilization of cryptographic authentication, such as key pairs, is recommended to enhance security and prevent MITM attacks.
0 views • 17 slides
State of Oregon Phishing Awareness Program Implementation Overview
The State of Oregon has launched a comprehensive Phishing Awareness Program to educate and protect employees against phishing attacks. The program includes phishing simulations, security culture surveys, and clear steps for handling suspicious emails. Various phases have been implemented to ensure a
0 views • 10 slides
Oregon Phishing Awareness Program: Implementation and Strategy
The State of Oregon's Phishing Awareness Program involves a structured approach to combat phishing attacks. It includes various phases such as pilot programs, monthly phishing simulations, and employee engagement strategies. The program aims to educate staff at all levels on identifying and reportin
1 views • 10 slides
Understanding Cybersecurity Threats and Facebook Security
In today's digital landscape, cybersecurity threats are ever-present, ranging from phishing to ransomware. This presentation by Paul Haithcock sheds light on protecting networks and data. It also emphasizes the importance of securing Facebook accounts amidst the prevalence of cybercriminal activitie
1 views • 15 slides
Recognizing Online Scams and Seeking Support
Understanding the nature of online scams and learning how to identify them is crucial in protecting oneself from cyber threats. This lesson covers the tactics used by scammers such as phishing, smishing, and vishing, along with ways to spot scam emails or messages. It also emphasizes the importance
0 views • 30 slides
Enhanced Chapter Management Tools and Security Protocols for ASSP Region I
Explore the latest updates in ARVP technology communication, efficient chapter document storage, role-specific chapter email accounts, surveys using Crowdsignal, survey result analysis, newsletter creation via Real Magnet/Higher Logic, and guidelines to safeguard your chapter from spear-phishing att
1 views • 16 slides
Phriendly Phishing Training Solutions Overview
Phriendly Phishing offers security awareness and phishing simulation training solutions to organizations in Australia and New Zealand. Their training covers topics like phishing, spear-phishing, ransomware, malware, and scams, focusing on empowering employees to detect and prevent cyber threats effe
6 views • 42 slides
Understanding Modern Phishing Techniques and Evilginx Framework
Explore the evolution of phishing from its inception to modern-day strategies like Evilginx, a man-in-the-middle attack framework. Learn about the effectiveness of phishing, its impact on financial losses, and how Evilginx bypasses multi-factor authentication to capture sensitive information. Dive i
7 views • 30 slides
John Deere AB11 AB12 AB13 AB14 AB15 AB18 AP12 AP13 Pallet Fork & Bale Spear Loader Attachments Operator’s Manual Instant Download (Publication No.5MP76313)
Please open the website below to get the complete manual\n\n\/\/
0 views • 13 slides
Understanding Phishing Attacks: Risks, Prevention, and Awareness
Phishing attacks are prevalent cybercrimes where attackers deceive individuals into divulging sensitive information or engaging in harmful actions. These attacks can happen through various channels such as emails, texts, or websites. The perpetrators aim to manipulate emotions like curiosity, greed,
1 views • 47 slides
Scams Awareness Week 2021: Real or Fake Scam Radar Activity
This post discusses Scams Awareness Week 2021 and presents an interactive activity to test your scam radar. It includes images where you have to distinguish between real and scam content. Additionally, it highlights the role of Scamwatch in combating scams, recent scam trends like phishing and inves
1 views • 26 slides
Protect Yourself from Phishing Scams: Essential Tips to Stay Safe Online
Phishing is a serious threat that can lead to identity theft and financial loss. Learn what phishing is, how it works, and crucial tips to prevent falling victim to such scams. Stay informed about the latest phishing techniques, think before clicking on unfamiliar links, use anti-phishing tools, ver
0 views • 8 slides
Understanding Cyber Crime: Risks and Prevention Measures
Cyber crime, including hacking, phishing, and pharming, poses a significant threat in today's digital world. Learn about the types of hackers and how to tackle phishing and pharming attacks effectively. By following security measures such as avoiding sharing sensitive information and updating anti-p
4 views • 18 slides
Phishing Survival Guide: Educating Children and Parents
Empower children to identify and respond to phishing attacks with this comprehensive phishing survival guide. The guide includes learning outcomes, lesson notes, and instructions to create an engaging pocket guide for parents. Learn how to report suspicious emails, handle suspicious links, and prote
0 views • 4 slides
Understanding Phishing: Types, Risks, and Prevention Strategies
Phishing is a prevalent cyber threat that aims to deceive individuals into divulging sensitive information. This detailed guide covers different types of phishing attacks, their objectives, and effective prevention measures. It highlights how phishing emails target users through fear, urgency, rewar
0 views • 17 slides
How to Protect Your Cryptocurrencies from DeFi Phishing Scams
Learn how to protect your cryptocurrencies from DeFi phishing scams in this comprehensive guide. Understand the common tactics scammers use and discover practical strategies to safeguard your assets. From recognizing suspicious links to using secure
1 views • 4 slides
Phishing Survival Guide: How to Recognize and Respond to Suspicious Emails
Learn how to spot a phishing email and what steps to take if you receive one or fall victim to a phishing scam. Find out how to identify suspicious links, recognize phishing attempts, and protect yourself from giving out personal information or losing money. Stay informed and secure in the digital a
2 views • 5 slides
Essential Cybersecurity Practices for Safe Online Activities
Phishing attacks come in various forms such as common phishing, spear phishing, whaling, smishing, and vishing. It's crucial to be cautious when connecting to Wi-Fi networks, secure your passwords, and follow safe web browsing practices to protect your personal information online.
4 views • 5 slides
Staying Safe Online_ How to Avoid Phishing Scams?
Learn simple tips to protect yourself from phishing scams and keep your online accounts secure. Stay safe online today!\n
2 views • 5 slides
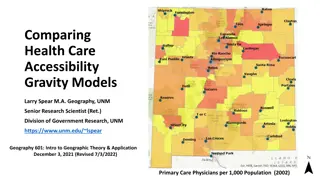
Comparing Health Care Accessibility Gravity Models in Geographic Theory
This study by Larry Spear, a Senior Research Scientist at UNM, delves into the concept of spatial interaction and the application of gravity models in analyzing health care accessibility. It discusses the development and comparison of one-step and two-step gravity models, addressing the issue of pat
3 views • 12 slides
Discoveries at M-231 Site: Artifacts and Findings
Features like cache pits and roasting pits, along with various artifacts, were unearthed at the M-231 site. Archaeologists identified items such as a knife, projectile points, and spear points. The collection of artifacts raises questions about their use across different time periods.
0 views • 51 slides
LEAP-Agri: Enhancing Food Security and Sustainable Agriculture
LEAP-Agri focuses on improving food security and sustainable agriculture through research and innovation collaborations between African and European teams. With a total budget of 28M and 30 partners from 18 countries, LEAP-Agri has funded 27 R&I projects, aiming to strengthen the EU-Africa partn
0 views • 12 slides
ReBIT Operational Excellence Webinar Series: Anti-Phishing Campaign
The ReBIT Operational Excellence Webinar Series features the Anti-Phishing Campaign, aiming to enhance cybersecurity postures in the industry through DMARC implementation and threat intelligence sharing. The webinar covers topics such as phishing mitigation strategies, DMARC technical details, and c
0 views • 10 slides
Understanding Phishing, Viruses, and Online Security
The internet can be a dangerous place with threats like viruses, worms, Trojan horses, and phishing scams. Learn how to protect yourself against these cyber threats and secure your personal information online. Be vigilant against email phishing schemes and follow tips to avoid falling victim to onli
0 views • 16 slides
Phonics Revisit: Digraphs and Tricky Words Practice
Explore digraphs and trigraphs in words like "growl," "frown," "spear," and practice sounding out tricky words such as "come," "they," and "when." Learn about the sounds "ei" and "eigh" making the "ay sound" and practice spelling words like "eight," "eighty," and "neighbour." Test your memory with a
0 views • 9 slides
Watch Out for Online Scams and Phishing Attempts
Be cautious of clickbait, loot boxes, and phishing schemes online. Stay alert for misleading titles and lookalike websites. Protect your accounts by avoiding suspicious links and always purchase from official websites. Remember: if it seems too good to be true, it probably is.
0 views • 9 slides
Protect Yourself from Phishing Scams: Key Tips for Members
Phishing is a deceitful attempt by fraudsters to extract personal information from individuals, often through emails pretending to be from trusted sources like credit unions. The scammers aim to trick you into divulging sensitive details like passwords or account information. Learn how to recognize
0 views • 11 slides
Secure Online Behavior: Learn to Identify and Protect Against Cyber Threats
Enhance your knowledge on appropriate cyber behavior and how to identify phishing emails, handle phishing attempts, recognize phony phone calls, protect personal information, and more. Understand the risks and consequences of mishandling cyber threats to safeguard your online presence.
0 views • 4 slides
Protect Yourself from Online Scams: Tips and Examples
Learn about scams, identity theft, and phishing schemes, along with ways to safeguard your personal and financial information online. Discover common tricks used by scammers and how to spot and avoid falling victim to online fraud. Explore examples of phishing emails and strategies to protect yourse
0 views • 13 slides
Cyber Security Awareness and Best Practices
Enhance your cyber security knowledge with terminology like Social Engineering and Spear Phishing, and learn about common cybercrime activities such as phishing and ransomware attacks. Stay informed to protect yourself and your organization from malicious threats.
0 views • 26 slides
Cybersecurity Awareness: Phishing Investigations Practitioner Notes and Game Instructions
This content focuses on teaching children to identify phishing tactics used by individuals and organizations through activities and lesson notes. It emphasizes recognizing scam attempts, understanding safe online practices, and evaluating suspicious messages. The interactive game instructions instru
0 views • 4 slides
Learn How to Identify Genuine Emails and Avoid Phishing Attempts
Understanding how to spot phishing emails is crucial for maintaining email security. This activity presents various email examples for evaluation – distinguishing between genuine communications and potential phishing attempts. By honing this skill, individuals can protect themselves from online sc
0 views • 9 slides
Innovative Phishing-Resistant Cardholder Authentication and Payment Confirmation Method
Introducing a method for cardholder authentication and secure payment confirmation that is phishing-resistant, requires no interaction with the issuing bank at transaction time, and provides merchants with a non-repudiable cryptographic signature on transactions. This innovative approach leverages t
0 views • 8 slides
USCG Enterprise Architecture Realization Through Service-Oriented Approach
USCG Operations Systems Center (OSC) plays a vital role in developing, maintaining, and operating Coast Guard enterprise information systems. With a focus on service-oriented architecture (SOA), the center utilizes cloud computing, enterprise service bus, and modern technologies to support missions
0 views • 36 slides
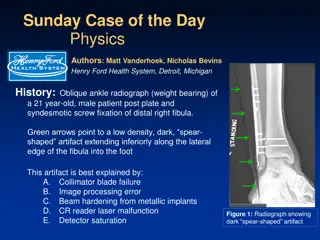
Understanding Image Processing Artifacts in Radiography
An oblique ankle radiograph of a patient showed a dark spear-shaped artifact extending from the leg to the foot, which was identified as an image processing error due to a black border imaging algorithm issue. The presence of metal in the leg caused the algorithm to fail, resulting in the artifact.
0 views • 4 slides
Understanding Atlatls: Ancient Spear-Throwing Devices
Atlatls, also known as spear-throwers, are ancient tools used for propelling spears with greater force and distance. They predate bows and arrows and were used for hunting large mammals. Modifications like adding weights and adjusting lengths impact the throwing distance. Factors like atlatl weight,
0 views • 11 slides
Protecting Your Data_ Tips for Preventing Phishing Attacks
Learn practical tips to protect your data and avoid phishing scams. Stay safe online with easy-to-follow advice to prevent cyber threats.
2 views • 7 slides
Understanding Network Breaches: Methods and Mitigation
Discover how networks are breached through phishing, exposed services, and publicly available exploits as explained by a security consultant. Learn about phishing techniques, externally exposed services vulnerabilities, and common exploits used to gain unauthorized access. Explore ways to mitigate t
0 views • 22 slides