High School Civil Rights Movement Escape Room
Engage high school students in an interactive escape room activity focused on key events and figures of the Civil Rights Movement. From segregation to landmark court cases and iconic protests, students will delve into the history through reading materials, questions, ciphers, and sorting tasks. This
2 views • 38 slides
The Shift from Government to Governance
This presentation discusses the transition from government to governance in public administration, exploring the concepts of public governance and the shift in decision-making processes. It covers the definition of public governance, the key differences between government and governance, and the imp
0 views • 8 slides
Understanding RC Phase Shift Oscillators
Dive into the world of RC phase shift oscillators, exploring the concepts of phase and phase shift in electronic circuits. Learn how cascading RC networks can achieve specific phase shifts, the role of impedance, and the practical applications of RC feedback networks in oscillator circuits. Discover
0 views • 18 slides
Pedagogical Shift in Physical Science: Constructing Knowledge Through Learner-Centered Experiences
There is a significant pedagogical shift in physical science education from viewing science as a fixed body of knowledge to emphasizing the process of constructing knowledge. Learners are now placed at the center stage, engaging in inquiry-based learning, critical thinking, and collaborative interac
3 views • 21 slides
Engaging Paper-Based Problem Solving for Computational Thinking Skills
Implementing paper-based problem-solving activities using puzzles, riddles, and pattern recognition can effectively introduce computational thinking without the need for complex technology or terminology. Through real-life scenarios like transporting a fox, chicken, and corn across a river or encodi
0 views • 23 slides
Introduction to RSA Cryptography and Public Key Encryption
Explore the fundamentals of RSA cryptography and public key encryption, including shift ciphers and affine ciphers. Learn how public key encryption solves the challenges of implementing secure communication on a large scale. Discover the key components of RSA, its development history, and the mathem
2 views • 37 slides
Columnar Transposition Cipher: Data Encryption Techniques at Mustansiriyah University Engineering College
Transposition ciphers, particularly the columnar transposition technique, are explored in the course "Data Encryption" at Mustansiriyah University Engineering College. The cipher involves rearranging message elements without changing their identities, making it crucial in modern block cipher designs
0 views • 4 slides
Shift of the Church: Eastward Expansion Through History
The Asian Church is witnessing a significant shift in influence from the West to the Majority World, marking a transformative phase in modern mission movements. With historical milestones like the Roman Catholic presence established in 1493 and the Protestant movement beginning in 1705 through figur
0 views • 12 slides
Understanding Shift Registers in Digital Electronics
Shift registers are a fundamental concept in digital electronics where binary numbers are shifted from one flip-flop to the next. They come in various types like SISO, SIPO, PISO, and PIPO, serving different purposes such as delay lines, data converters, sequential memory, and ring counters. The ope
0 views • 10 slides
Overview of Cryptography Techniques and Algorithms
Exploring the diverse realm of cryptography, this chapter delves into both nonmathematical and mathematical encryption methods. It covers substitution and transposition ciphers, steganography, hybrid systems, hashing, symmetric algorithms like DES and AES, as well as asymmetric algorithms utilizing
7 views • 21 slides
Benefits of Vocantas Mobile App and Online Portal
Explore the benefits of using the Vocantas Mobile App and Online Portal, including easy installation on mobile devices, managing notifications, shift filtering, bidding on future shifts, receiving notifications on shift awards, adding shifts to your calendar, and more. The Online Portal offers featu
0 views • 9 slides
Transposition Cipher Techniques in Modern Block Ciphers
Transposition ciphers, specifically columnar and double columnar transpositions, are explored in the context of data encryption and computer engineering at Mustansiriyah University Engineering College. These techniques involve rearranging message elements without changing their identities, providing
0 views • 4 slides
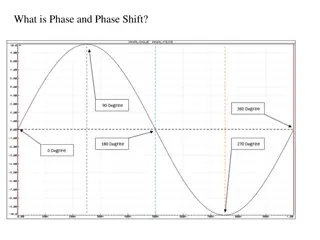
Understanding Phase Difference and Phase Shift in Sinusoidal Waveforms
Phase difference and phase shift describe the angular displacement of sinusoidal waveforms in degrees or radians. These concepts are crucial in analyzing the relationship between alternating quantities such as voltage and current. The phase angle determines the shift of a waveform along the horizont
1 views • 26 slides
Neural Shift-Reduce Dependency Parsing in Natural Language Processing
This content explores the concept of Shift-Reduce Dependency Parsing in the context of Natural Language Processing. It describes how a Shift-Reduce Parser incrementally builds a parse without backtracking, maintaining a buffer of input words and a stack of constructed constituents. The process invol
0 views • 34 slides
Understanding Shift Registers in Sequential Logic Circuits
Shift registers are sequential logic circuits used for storing digital data. They consist of interconnected flip-flops that shift data in a controlled manner. This article explores different types of shift registers such as Serial In - Serial Out, Serial In - Parallel Out, Parallel In - Serial Out,
2 views • 9 slides
Enhancing Resident Observations with Shift Cards in Outpatient Clinic
Explore the utility of Shift Cards in providing real-time feedback to residents in the outpatient clinic setting. Learn how to observe, provide feedback, and engage with the Clinical Competency Committee effectively using this innovative tool. Discover the benefits, learning objectives, and audience
0 views • 16 slides
Simplifying Residency Shift Scheduling with Mathematical Programming Techniques
This project, led by Professor Amy Cohn and William Pozehl, aims to demonstrate how mathematical programming techniques can simplify the complex task of residency shift scheduling. The Residency Shift Scheduling Game highlights the challenges of manual scheduling and the ease of using mathematical p
1 views • 37 slides
The Great Vowel Shift: A Linguistic Evolution
The Great Vowel Shift was a significant phonological transformation in the English language during the 15th to 17th centuries that altered the pronunciation of long vowel sounds. This shift, marked by a movement of vowel sounds to higher and more forward positions in the mouth, shaped the transition
3 views • 11 slides
Managing Fatigue and Shift Work: Impact on Safety and Wellbeing
Understanding the legal requirements, effects of fatigue and shift work, and ways to manage fatigue is crucial for ensuring workplace safety and employee wellbeing. Fatigue, a state of reduced performance capability, can result from various factors, including sleep loss and workload. Shift work pose
6 views • 19 slides
Pure Shift NMR Workshop: Advancements and Insights
Explore the latest developments and insights in Pure Shift NMR spectroscopy through presentations on acquisition methods, implementations, and the quest for spectral purity. Discover the evolution of magnet development and the potential of high-temperature superconductivity in NMR technology. Delve
2 views • 27 slides
Discussion on UL 7.5kHz Frequency Shift for n34 and n39 in 3GPP TSG-RAN WG4 Meeting #100-e
The approval document for Working Group on Dual-Site Selection (DSS) for n34 and n39 in CMCC, discussed in the 3GPP TSG-RAN WG4 Meeting #100-e, addresses the UL 7.5kHz shift agreements for different releases. The document outlines the mandatory nature of the shift for n34 and n39 in later releases,
3 views • 4 slides
Design and Implementation of Shifters in ALU for Single-Cycle Processors
The detailed discussion covers the construction of a multifunction Arithmetic Logic Unit (ALU) for computer processors, specifically focusing on the design and implementation of shifters. Shift operations such as SLL, SRL, SRA, and ROR are explained, with insights into shifting processes and data ex
0 views • 5 slides
Supporting Heroes in Mental Health Foundational Training (SHIFT)
SHIFT is a foundational training program funded by the Department of Justice, OJJDP, aimed at addressing the long-term effects of chronic exposure to traumatic material. The program focuses on supporting, educating, and empowering individuals in the mental health field to mitigate negative effects a
8 views • 5 slides
Understanding Block Ciphers in Cryptography
Explore the principles of block ciphers in modern cryptography, focusing on the Data Encryption Standard (DES) and its design principles. Learn about block cipher encryption, Feistel block cipher structure, n-bit block ciphers, ideal block ciphers, key length considerations, and challenges with idea
0 views • 44 slides
Understanding Symmetric Key Block Ciphers - Overview and Implementation
Delve into the world of symmetric key block ciphers through a detailed exploration of classical ciphers like substitution and transposition, modern cryptography advancements, DES encryption, Simplified DES, key scheduling, expansion functions, S-Box usage, and more. Discover the intricacies of encry
0 views • 40 slides
Understanding Encryption Techniques: From Transposition Ciphers to Rail Fence Ciphers
Explore the world of encryption techniques, diving into transposition ciphers and rail fence ciphers. Learn about encryption, decryption, plaintext, ciphertext, keys, and the art of secret writing. Discover how transposition ciphers reorder letters without changing their values and how rail fence ci
0 views • 26 slides
Understanding Cryptography: Basics of Encryption and Padding
Cryptography is essential for secure communication between parties, ensuring confidentiality and integrity of data. This overview covers basic math concepts, block ciphers, encryption modes like ECB and CBC, and the importance of padding in securing plaintext data.
0 views • 21 slides
Overview of Modern Cryptography and Data Encryption Standard (DES)
Exploring modern cryptography including symmetric key block ciphers, public key ciphers, stream ciphers, and post-quantum ciphers. Focus on Data Encryption Standard (DES), Simplified DES, Feistel cipher, key schedule, expansion function, S-Box, DES encryption, and decryption processes.
0 views • 37 slides
Understanding Public Key Cryptography in Network Security
Explore the concepts of public key cryptography, key distribution challenges, solutions to secret key schemes, and the importance of secure communication in network security. Learn about cryptology, cryptography, cryptanalysis, block ciphers, stream ciphers, and more in this informative content.
0 views • 21 slides
Crack the Code: A Journey into Transposition Ciphers
Mathematicians play a crucial role in industries like telecommunications and internet companies by condensing data and ensuring error detection. Transposition ciphers, like the Scytale used by Romans, offer a challenging way to encrypt messages. Test your skills with code-breaking challenges and exp
0 views • 4 slides
Understanding Secure PRFs and PRPs in Cryptography
Dive into the world of secure Pseudo-Random Functions (PRFs) and Pseudo-Random Permutations (PRPs) in cryptography. Learn about the definitions, security criteria, and examples of secure PRFs and PRPs such as 3DES and AES. Explore the concepts of secure block ciphers and key principles behind these
0 views • 54 slides
Beavers Code Cracking Mystery - Detective Agency and Kidnapping Case!
In this thrilling mystery, Boo the beaver has been kidnapped, leaving behind coded messages to uncover the suspect. The Detective Agency seeks your help to crack the codes and rescue Boo. Dive into letter-number ciphers, Morse code, and a list of intriguing suspects to unravel the mystery and bring
0 views • 24 slides
Lightweight Cryptography: Key-Reduced Variants and Beyond-Birthday-Bound Security
Lightweight cryptography has emerged as a hot research topic in the past two decades, with over 60 ciphers proposed. This includes examples like PRESENT, GIFT, SIMON/SPECK, and more. Authenticated encryption through CAESAR and NIST LWC plays a vital role, with ASCON and ACORN leading the lightweight
0 views • 25 slides
Introduction to Cryptology in Algebra 2 Classroom
Engage students in a high school Algebra 2 class by exploring cryptology concepts such as coding, hexadecimal systems, substitution ciphers, and the Vigenere cipher. The lesson plan includes activities like solving puzzles, introducing binary systems, converting to hexadecimal, and writing messages
0 views • 16 slides
Pure Shift Implementation by Dr. Adolfo Botana - JEOL Image Gallery
Explore a collection of images showcasing the Pure Shift Implementation by Dr. Adolfo Botana at JEOL. Dive into the basics, experiment submissions, proton vs. pure shift comparisons, processing techniques, pulse sequence coding, and more. Witness innovative processing methods and cutting-edge techno
0 views • 17 slides
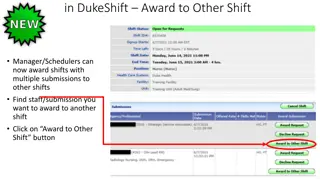
Efficient Shift Award Management in DukeShift System
DukeShift system allows Shift Managers/Schedulers to award shifts to staff members across different shifts. The process involves selecting staff submissions, choosing alternative shifts, ensuring correct dates, adding notes, and completing the award. For any questions, contact APIResourceGroup@duke.
0 views • 11 slides
Introduction to Traditional Ciphers: Columnar Transpositions
Traditional ciphers such as Columnar Transpositions involve rearranging plaintext letters based on a fixed number of columns. This technique enhances security by incorporating a keyword for encryption and decryption. Learn about the process and examples of implementing Columnar Transpositions in thi
0 views • 8 slides
Unlock the Challenges in Cipher Cove: A STEM Adventure
Explore Cipher Cove and tackle five cryptographic challenges involving different ciphers such as Caesar Shift, Pigpen, Transposition, Substitution, and Periodic Table. Put your problem-solving skills to the test by deciphering hidden clues and codes to progress through each challenge and ultimately
0 views • 6 slides
Understanding Block Ciphers in Cryptography
Explore the world of block ciphers in cryptography through topics such as distinguishing attacks, key-recovery attacks, designing paradigms like Substitution-Permutation Networks (SPNs) and Feistel networks, concrete security considerations, confusion/diffusion principles, attack models, and more.
0 views • 27 slides
Comprehensive Overview of Encryption Techniques and Algorithms
Explore the world of encryption with insights into symmetric and public key encryption, certificate authorities, secure sockets layer, substitution ciphers, block ciphers, AES, and public key cryptography. Delve into the intricacies of encryption keys and algorithms, including the AES process, Diffi
0 views • 31 slides